Why Identity Access Management is Critical for Modern Business Security
Identity Access Management (IAM) ensures that the right people access the right digital resources at the right time, for the right reasons. In simple terms, IAM is your organization's digital security guard—it verifies who someone is (authentication) and determines what they're allowed to do (authorization).
Quick Overview: What You Need to Know About IAM
- What it does: Controls user access to applications, systems, and data
- Core functions: Authentication (proving identity) and authorization (granting permissions)
- Key benefits: Reduced data breach risk, improved productivity, simplified compliance
- Essential features: Single Sign-On (SSO), Multi-Factor Authentication (MFA), automated user provisioning
- Why it matters now: Hybrid work models and cloud computing make traditional perimeter security obsolete
If you use multiple applications for work, you've likely experienced the frustration of managing different usernames and passwords for each system. Now imagine this complexity multiplied across an entire organization, with the added responsibility of protecting sensitive customer data, financial records, and intellectual property. That's the problem IAM solves.
According to industry research, 95% of data breaches are caused by human error. IAM systems dramatically reduce this risk by centralizing identity management, enforcing strong authentication, and ensuring employees only access what they need for their specific roles. For organizations navigating regulatory requirements like GDPR, HIPAA, or SOX, IAM provides the audit trails and access controls necessary to demonstrate compliance.
The stakes have never been higher. With employees working remotely and accessing company resources from personal devices, the traditional approach of trusting anyone "inside the network" no longer works. IAM brings structure to this chaos by verifying every access request, regardless of where it originates.
I'm Steve Payerle, President of Next Level Technologies, where we've helped businesses across Columbus, Ohio, and Charleston, WV, implement robust Identity Access Management systems that protect their digital assets while improving operational efficiency. Our cybersecurity team has extensive training in deploying IAM solutions that balance security with user experience, ensuring your employees stay productive while your data stays protected.
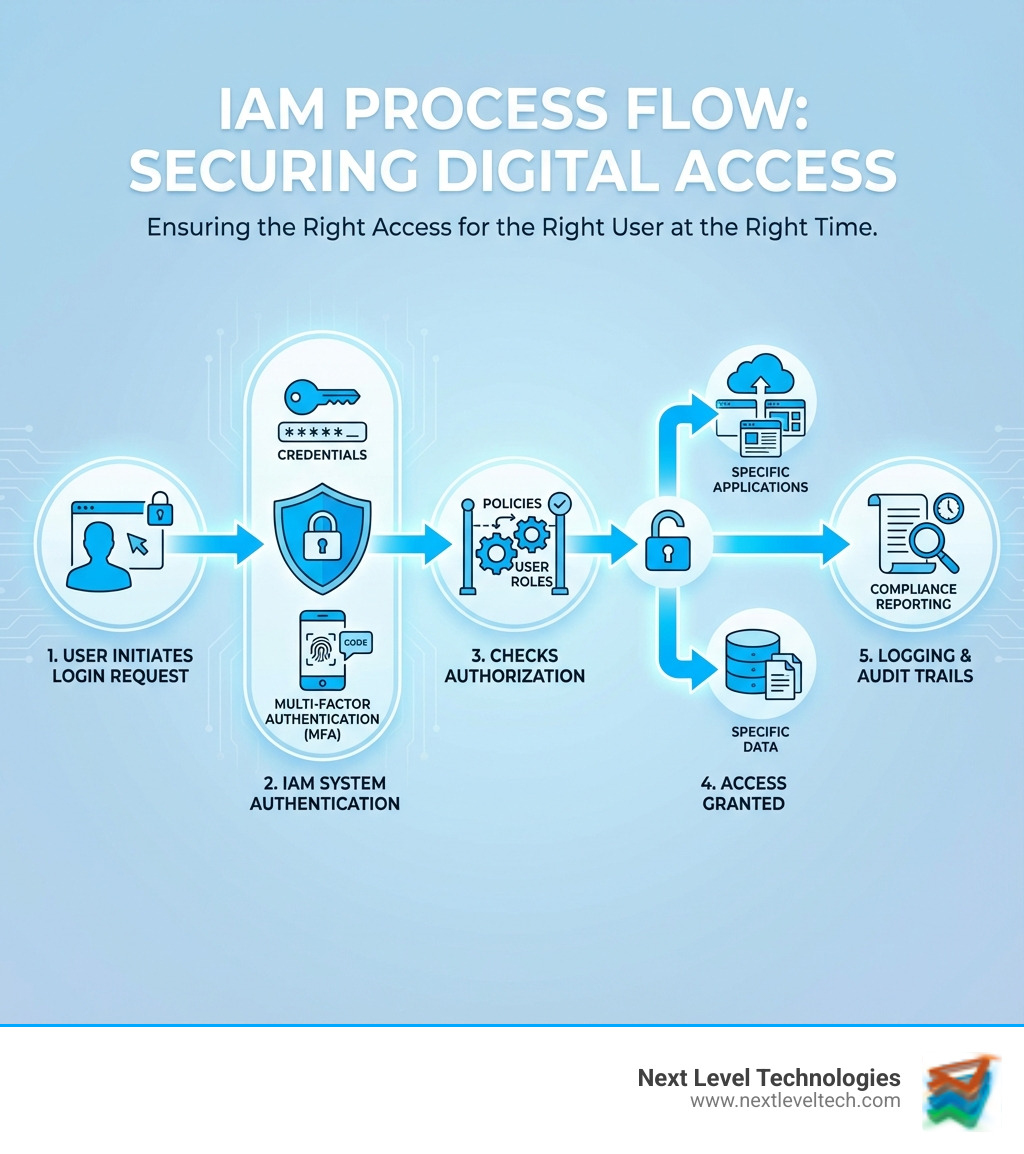
What is Identity and Access Management (IAM) and How Does It Work?
In today's digital landscape, where hybrid work models are the norm and cloud computing reigns supreme, securing our digital assets is paramount. This is precisely where Identity Access Management (IAM) steps in as a cornerstone of modern cybersecurity. IAM is a comprehensive framework of policies, processes, and technologies designed to manage and control who (or what) can access specific information and resources within an organization's IT environment. It's about making sure that every user, device, and application is verified and granted only the appropriate level of access.
At its heart, IAM is a vital part of modern IT. It functions as a sophisticated system to securely verify user identities and manage access rights across various systems, applications, and resources. Without a robust IAM solution, organizations risk unauthorized access, data breaches, and significant compliance headaches. IAM solutions are an excellent way to prevent and minimize the impact of attacks, bolstering cybersecurity by ensuring that only authorized users have access to sensitive resources. This is key to achieving Secure Data Access in any organization.

Defining the Core: Identity vs. Access Management
While often used interchangeably, "identity management" and "access management" refer to distinct, though closely related, aspects of the overall IAM framework. Think of it this way:
Identity Management focuses on verifying who someone is. It's the process of creating, maintaining, and managing digital identities for users (employees, customers, partners), as well as devices and applications. This includes storing attributes that help verify a user’s identity, such as their name, job title, email address, and the methods used for verification. Identity management also covers the entire user lifecycle, from provisioning (granting initial access) to deprovisioning (revoking access when roles change or employment ends). As the Identity Management Institute highlights, the IAM lifecycle manages the end-to-end process of granting and revoking access. Learn more about What is identity management (ID management)?.
Access Management determines what that verified individual, device, or application is allowed to do once their identity is confirmed. It governs their permissions and privileges—which applications they can open, which files they can view or edit, and what actions they can perform. Access management enforces policies based on roles, security clearance, and other attributes to ensure that users can only interact with the resources necessary for their tasks.
Essentially, identity management answers the question "Are you who you say you are?", while access management answers "Now that we know who you are, what are you allowed to do?". Both are crucial for a comprehensive Identity Access Management strategy.
The Mechanics: Authentication and Authorization Explained
These two processes are the engine room of IAM, working hand-in-hand to control access.
Authentication: This is the initial step where a user's identity is verified. It's like showing your ID to a bouncer at a club. Common authentication methods include:
- Passwords: The most traditional method, though increasingly vulnerable.
- Biometrics: Fingerprints, facial recognition, or voice patterns.
- Tokens: Physical devices or software-generated codes (like those from an authenticator app).
- Multi-Factor Authentication (MFA): A critical security layer that requires users to provide two or more verification factors to gain access to a resource. This significantly reduces the risk of credential compromise. We strongly recommend implementing robust Multi-Factor Authentication Solutions to protect your organization.
Authorization: Once authenticated, the system determines the user's access rights. This is where policies come into play, defining what resources an authenticated user can access and what actions they can perform.
- Role-Based Access Control (RBAC): A popular method where permissions are assigned to specific roles (e.g., "Marketing Manager," "Finance Analyst"), and users are then assigned to these roles. This simplifies management, as permissions are tied to the role, not individual users.
- Attribute-Based Access Control (ABAC): Offers more granular control by granting permissions based on a combination of user attributes (department, job function, location), resource attributes (sensitivity, owner), and environmental conditions (time of day, device type).
The Core of Identity Access Management: Functions and Benefits
Implementing a robust Identity Access Management system goes far beyond just security; it's a strategic move that fundamentally transforms how an organization operates. Our experience with businesses in Columbus, Ohio, and Charleston, WV, has shown us that IAM is a game-changer, improving everything from security posture and user experience to IT workload and overall data breach risk. For a deeper dive into overall security, check out our Cybersecurity for Business Complete Guide.
Modern IAM tools offer a suite of capabilities designed to automate, streamline, and secure access across complex IT environments. They are the digital Swiss Army knife for identity and access, helping us manage who can do what, where, and when.

Here are some of the core capabilities we look for in effective IAM tools:
- Centralized Identity Storage and Management: A single source of truth for all user identities (employees, contractors, customers) across the organization. This eliminates data silos and ensures consistency.
- Single Sign-On (SSO): Allows users to authenticate once and gain access to multiple applications and services without re-entering credentials. This dramatically improves user experience and reduces password fatigue.
- Multi-Factor Authentication (MFA): As discussed, MFA adds crucial layers of security beyond just a password. Modern IAM tools integrate various MFA methods like biometrics, push notifications, and hardware tokens.
- User Provisioning and Deprovisioning: Automates the creation of user accounts and assignment of roles/permissions upon onboarding, and the revocation of access upon offboarding. This is critical for security and efficiency.
- Access Request Workflows: Streamlines the process for users to request access to new resources, ensuring proper approvals and documentation.
- Auditing and Reporting: Provides detailed logs of all access attempts, changes to permissions, and user activities. This is invaluable for security analysis, incident response, and demonstrating compliance during audits.
- Self-Service Capabilities: Empowers users to manage their own passwords, update profile information, and request access to resources, reducing the burden on IT helpdesks.
- Contextual and Risk-Based Authentication: Analyzes various factors (device, location, time, behavior) during login to assess risk and dynamically request additional authentication if needed.
- API Security and IoT Identity Management: Extends IAM principles to secure interactions between APIs and manage identities for the growing number of IoT devices.
Why IAM is a Game-Changer for Your Organization
The benefits of implementing a comprehensive Identity Access Management system are profound and far-reaching, impacting every facet of your business.
- Improved Security and Reduced Data Breach Risk: This is perhaps the most obvious and critical benefit. By enforcing strong authentication, centralizing access controls, and implementing the principle of least privilege, IAM significantly reduces the attack surface. As noted in our research, IAM tools significantly reduce your risk of data breaches. With 95% of data breaches linked to human error, restricting what a compromised account can access limits potential damage.
- Improved Regulatory Compliance: Many compliance mandates, such as GDPR, HIPAA, and SOX, require strict controls over data access and privacy. IAM systems provide the necessary mechanisms to enforce these policies, track user activities, and maintain comprehensive audit trails. This allows organizations to demonstrate during audits that access to sensitive data is being governed properly, saving us from potential fines and reputational damage.
- Higher Employee Productivity and Better User Experience: Imagine your team no longer struggling with dozens of passwords or waiting for IT to manually grant access to new applications. SSO streamlines login processes, and self-service portals empower users. This translates directly to less frustration and more time spent on core tasks. Our team at Next Level Technologies has seen how a well-implemented IAM solution frees up employees to focus on what they do best. For more on this, explore our MFA Benefits Complete Guide.
- Streamlined IT Operations and Reduced Workload: IAM solutions automate and standardize many tasks related to identity, authentication, and authorization management. This includes onboarding new hires, modifying access rights, and deactivating accounts. Automated user provisioning and password resets free up IT staff from repetitive tasks, allowing our highly trained cybersecurity professionals to focus on more strategic initiatives and proactive security measures. This can significantly reduce the nearly 50% of helpdesk calls that are password or logon related.
- Agility and Innovation: By providing secure and efficient access to resources, IAM supports agility and innovation, especially in cloud environments. It allows businesses to scale workload and workforce access securely, enabling faster adoption of new technologies and services.
Implementing IAM: Best Practices and Common Problems
Implementing an Identity Access Management system is a significant undertaking, but one that yields immense security and operational dividends. It requires strategic planning, a phased approach, and often, the technical expertise that our team at Next Level Technologies brings to businesses in Columbus, Ohio, and Charleston, WV. We understand that this isn't just about software; it's about changing your security posture. For comprehensive support, consider our IT Security Services.
Best Practices for a Successful Identity Access Management Implementation
To ensure your IAM implementation is a resounding success, we recommend adhering to these best practices:
- Accept the Principle of Least Privilege (PoLP): This is arguably the most critical best practice. PoLP dictates that users, applications, and devices should only be granted the minimum access rights necessary to perform their specific tasks and nothing more. If an employee's account is compromised, limiting their access to non-sensitive files significantly reduces the potential damage. It also mitigates insider threats by ensuring employees only have access to information essential for their roles. This proactive approach is fundamental to increasing your organization's security posture. We encourage you to review our insights on Least Privilege Access for a deeper understanding.
- Automate the User Lifecycle: From onboarding to offboarding, automate the provisioning and deprovisioning of user accounts and their associated access rights. This ensures that new employees gain necessary access quickly and that access is promptly revoked for departing employees, minimizing security gaps.
- Enforce Strong Authentication (MFA is a Must): Make Multi-Factor Authentication (MFA) a mandatory requirement for all users accessing sensitive systems and data. Passwords alone are no longer sufficient. MFA adds a crucial layer of security that significantly reduces the risk of unauthorized access even if a password is stolen.
- Conduct Regular Access Reviews and Recertification: Periodically review user access rights to ensure they align with current job roles and responsibilities. Remove any unnecessary or excessive privileges. This helps maintain PoLP and identifies "privilege creep" over time.
- Implement Continuous Monitoring and Auditing: Actively monitor user activities and access logs for suspicious behavior or anomalies. Robust auditing capabilities are essential for detecting potential threats, ensuring compliance, and providing an undeniable record for forensic analysis.
- Centralize Identity Management: Consolidate all identity information into a single, authoritative directory. This simplifies management, improves consistency, and provides a unified view of all identities and their access entitlements.
- Plan for Scalability and Integration: Choose an IAM solution that can grow with your organization and integrate seamlessly with your existing applications, infrastructure, and cloud services. Our technical team ensures solutions are custom to your specific needs, whether you're a small business or a larger enterprise.
- Educate Users: Provide clear training and communication to employees about IAM policies, the importance of strong authentication, and how to use self-service features. User adoption is key to the success of any IAM system.
- Follow Industry Guidelines: Adhere to recognized standards and guidelines, such as the NIST Digital Identity Guidelines. These provide a robust framework for secure identity management.
For businesses supporting remote workers, these best practices are even more critical. Read our Secure Remote Access Best Practices for more insights.
Navigating Common Identity Access Management Challenges
While the benefits are clear, implementing Identity Access Management can present its share of problems. We've helped many businesses in Columbus, Ohio, and Charleston, WV, overcome these common challenges:
- Legacy System Integration: Many organizations operate with a mix of old and new systems. Integrating a modern IAM solution with legacy applications that weren't designed for such interoperability can be complex and time-consuming. It often requires custom connectors or API development.
- Managing a Hybrid Environment: With resources often split between on-premises servers and multiple cloud platforms, maintaining consistent IAM policies and controls across this hybrid landscape is a significant challenge. This requires a solution that can span different environments effectively.
- User Resistance and Adoption: Change can be hard, and new security measures, especially those affecting daily login routines, can sometimes be met with user resistance. A lack of understanding or perceived inconvenience can hinder adoption. Clear communication and user-friendly solutions are essential.
- Scalability Issues: As organizations grow, the number of users, applications, and devices requiring access management can explode. An IAM solution must be able to scale efficiently without becoming a bottleneck or compromising performance.
- Lack of Skilled Personnel: Implementing and managing a sophisticated IAM system requires specialized expertise in cybersecurity, identity protocols, and integration. Many organizations struggle to find or retain staff with the necessary skills, which is where a managed IT service provider like Next Level Technologies can step in. Our team has the deep technical experience to handle these complexities.
- Budget Constraints: IAM solutions, especially comprehensive enterprise-grade platforms, can represent a significant investment. Organizations must carefully weigh the costs against the substantial benefits in security, compliance, and efficiency.
- "Privilege Creep": Over time, users often accumulate more access rights than they truly need due to role changes or project-specific permissions that are never revoked. Managing and regularly reviewing these privileges to prevent "privilege creep" is an ongoing challenge.
Addressing these challenges requires careful planning, technical proficiency, and a partner who understands both the technology and your business needs. Our expertise in IT Infrastructure and Security means we're well-equipped to guide you through these complexities.
The Bigger Picture: IAM's Role in Compliance and the Future
Identity Access Management is not a static solution; it's a dynamic and evolving field that continuously adapts to the regulatory landscape and technological advancements. Its role in ensuring IT Security Policy Compliance is only growing, and its future is being shaped by transformative technologies like cloud computing and Artificial Intelligence (AI).
IAM Standards and Regulatory Compliance
The digital world thrives on interoperability, and IAM is no exception. Standardized protocols are essential for different systems and organizations to securely exchange identity and access information.
Here are some key IAM standards that facilitate this interoperability:
| Standard | Purpose TABLE
| Standard | Description of its role in IAM |
|---|
| SAML | Security Assertion Markup Language. An XML-based standard for exchanging authentication and authorization data between an identity provider (IdP) and a service provider (SP). Primarily used for federated identity and enterprise applications. |
| OIDC | OpenID Connect. An identity layer built on top of the OAuth 2.0 protocol. It allows clients to verify the identity of the end-user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the end-user in an interoperable and REST-like manner. |
| SCIM | System for Cross-domain Identity Management. An open standard for automating the exchange of user identity information between identity domains and IT systems. It simplifies user provisioning, updating, and deprovisioning across multiple applications. |
Regulatory Compliance: Beyond interoperability, IAM is indispensable for meeting stringent regulatory requirements. Laws like the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Sarbanes-Oxley Act (SOX) demand meticulous control over who can access sensitive data. IAM solutions provide the framework to:
- Enforce Access Policies: Ensure that only authorized personnel can access data protected by these regulations.
- Track User Activities: Maintain detailed logs and audit trails of all access attempts and modifications, crucial for demonstrating accountability.
- Generate Audit-Ready Reports: IAM systems enable us to produce comprehensive reports that auditors require to verify compliance with data access governance. This ensures we can demonstrate that access to sensitive data is being governed properly.
These capabilities are vital for any business, particularly those in regulated industries. For more insights into these requirements, read our guide on Understanding the Basics of IT Compliance.
The Future of IAM: AI, Cloud, and Beyond
The landscape of Identity Access Management is continually evolving, driven by new technologies and an ever-shifting threat environment. We're seeing exciting developments that promise even more robust and intelligent security.
- Cloud-Native IAM (IDaaS): The shift to cloud computing means IAM solutions are increasingly cloud-based, offered as Identity as a Service (IDaaS). This provides scalability, flexibility, and reduced infrastructure overhead, allowing organizations to manage identities and access across distributed cloud environments more efficiently. This supports agility and innovation, especially in cloud environments, as businesses use IAM to manage and scale workload and workforce access securely.
- AI and Machine Learning in Threat Detection: AI is revolutionizing IAM by enabling systems to detect and respond to threats more intelligently. AI-enabled IAM can analyze user behavior patterns, identify anomalies (like a login from an unusual location or at an odd hour), and automatically trigger additional verification steps or block access. This proactive threat protection helps stop attacks before they escalate.
- Passwordless Authentication: Users are tired of passwords, and frankly, they're often a security weak point. The future of IAM is moving towards passwordless authentication methods, leveraging biometrics, magic links, FIDO2 security keys, and other innovative approaches. These methods are not only more convenient for users but also significantly more secure.
- Decentralized Identity: Emerging concepts like decentralized identity, often based on blockchain technology and Decentralized Identifiers (DIDs), aim to give individuals more control over their own digital identities and how their data is shared. While still nascent, this could fundamentally change how identities are managed in the future.
These advancements underscore the importance of staying current with IAM technologies. Our team is constantly monitoring these trends to ensure businesses in Columbus, Ohio, and Charleston, WV, are equipped with the most advanced and effective solutions. For more on securing your cloud resources, refer to our Cloud Security Best Practices.
Conclusion
Identity Access Management is more than just a cybersecurity tool; it's a foundational element of modern cybersecurity, a strategic framework for protecting digital assets. It improves security, boosts productivity, and ensures compliance. Implementing a robust IAM system requires expertise and a clear strategy. The highly trained cybersecurity teams at Next Level Technologies, serving businesses from our locations in Columbus, Ohio, and Charleston, WV, are equipped to guide you through every step, from planning to ongoing management. Secure your organization's future by mastering access control today. Learn more about our Managed IT Services and IT Support.






