Secure Your Digital Life: The Top Benefits of Multi-Factor Authentication
September 16, 2025

Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026

Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026

Find the best Remote IT Support Business for your small business. Learn how to define needs, evaluate providers, and secure your tech.
February 6, 2026
September 16, 2025
Understanding the benefits of multi factor authentication is critical as cyber threats evolve. Here are the key advantages that make MFA a must-have security measure:
Top Benefits of Multi-Factor Authentication:
The statistics are clear: Microsoft research shows MFA blocks 99.9% of automated attacks, and the Verizon Data Breach Investigation Report links stolen credentials to 49% of all data breaches. With billions of credentials on the dark web, passwords alone are not enough.
Consider that over 80% of data breaches are due to compromised passwords, and the average breach cost reached $5.17 million in 2024. MFA is a smart financial investment.
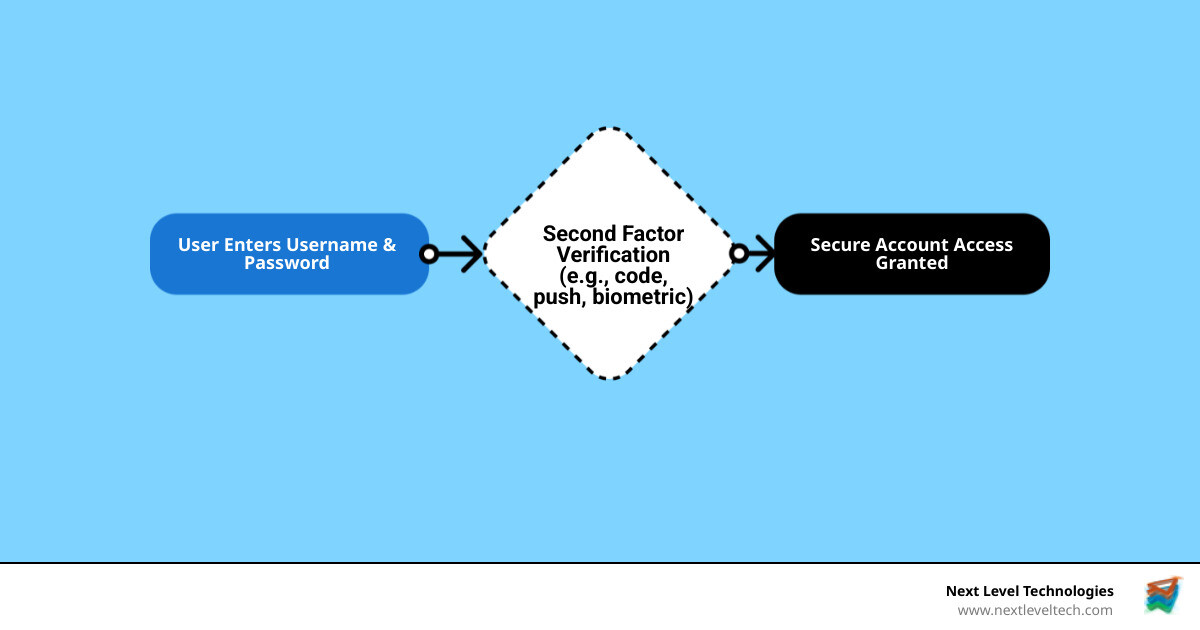
The core concept is simple yet powerful - MFA adds multiple layers of verification beyond just a username and password. Instead of relying on a single point of failure, users must provide two or more different types of evidence to prove their identity.
I'm Steve Payerle, President of Next Level Technologies. For 15 years, I've seen how the benefits of multi factor authentication transform security for businesses in Columbus, Ohio, and Charleston, WV. Our team's extensive cybersecurity training has helped hundreds of businesses implement MFA to protect against evolving threats.
Benefits of multi factor authentication word list:
Multi-factor authentication builds a formidable wall around your digital assets. A password is like a single lock on a door. MFA adds multiple locks, like a deadbolt and a keypad, stopping an intruder even if they get past the first one.
This layered approach improves identity verification by requiring more than just a password. It uses different authentication factors, making it much harder for unauthorized users to gain access, even with a stolen password. For a deeper dive, see the guidance from NIST on Back to Basics: What’s multi-factor authentication - and why should I care?.
The core principle of MFA relies on using at least two different types of authentication factors from three distinct categories:
An MFA verification process typically involves entering your password, then being prompted for a second factor from one of the other categories, like a code from your smartphone or a fingerprint scan.
Though often used interchangeably, Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) have a key difference.
Two-Factor Authentication (2FA) is a specific type of MFA requiring exactly two distinct factors (e.g., a password and a phone code).
Multi-Factor Authentication (MFA) is the broader term for any process requiring two or more factors. All 2FA is MFA, but MFA can include three or more factors for even higher security.
The benefits of multi factor authentication go beyond an extra login step; it's a security system that stops attackers before they do damage.
At Next Level Technologies, our cybersecurity-trained team in Columbus, Ohio, and Charleston, WV, has seen MFA transform security for businesses of all sizes. It's essential protection in today's threat landscape.
MFA's real power is its effectiveness against common attacks like phishing and credential stuffing, where hackers use stolen passwords. MFA makes these methods significantly harder.
Cybercriminals seek easy targets. An MFA-protected account requires more than a password, causing many attackers to simply move on.
For businesses, MFA strengthens data protection, helps with regulatory compliance, and builds user trust. It's also essential for remote work security, keeping distributed teams safe and productive.
Our team's extensive cybersecurity training and technical expertise confirm that MFA is no longer optional—it's essential infrastructure for any secure organization.
With cyberthreats multiplying daily, the security power of the benefits of multi factor authentication is clear. If a password is a basic lock, MFA is a full security system.
The numbers are incredible: MFA blocks 99.9% of automated attacks. This is a game-changing statistic offering real protection against common cybercriminal methods.
This is powerful because most attacks use credential stuffing (using stolen passwords from other breaches) and brute-force attacks (repeatedly guessing passwords). MFA stops these methods cold. Even with a stolen password, attackers hit a wall because they can't provide the second factor—a code, fingerprint, or token.
This defense-in-depth approach, which our team in Columbus and Charleston has implemented for countless businesses, creates multiple layers of protection. MFA also mitigates password reuse. If a reused password is stolen from one site, MFA prevents a domino effect by requiring a unique second factor for each account.
It also protects against keyloggers. Malware can steal your typed password, but it can't steal a code from your authenticator app or your fingerprint.
Crucially, MFA reduces the risk of human error. It provides a safety net for mistakes like clicking phishing links or using weak passwords. This protects business data and personal information alike. It's a rare security measure where a small effort yields massive protection.
If you're ready to strengthen your organization's defenses with this level of protection, consider exploring More info about our Managed Cybersecurity Services.
The benefits of multi factor authentication extend beyond security to regulatory compliance. MFA helps you meet strict data protection requirements that govern how businesses must protect sensitive data.
Regulators create rules to prevent data misuse. If your business handles sensitive data like health records, payment info, or personal details, you are subject to these regulations.
Compliance violations lead to massive fines, legal fees, and reputation damage. MFA helps you avoid these costs by demonstrating due diligence in protecting sensitive information.
Our team at Next Level Technologies has extensive cybersecurity training to help businesses in Columbus, Ohio, and Charleston, WV, steer these complex regulations. We implement MFA solutions that strengthen security and satisfy auditors. This proactive posture keeps regulators happy and your business protected. More info about our Cybersecurity Audit and Compliance Solutions.
The shift to remote work has been a game-changer for productivity but has also created new cybersecurity challenges. Team members now log in from various locations, often on less secure home networks or personal devices. This creates many new entry points that need protection.
This is where the benefits of multi factor authentication are critical. MFA acts as a digital bouncer, preventing access even if a password is compromised on an unsecured network.
Secure remote access is more manageable with MFA. Whether using a VPN or cloud apps, it ensures only authorized users get in, protecting corporate resources regardless of location—from a home office in Columbus, Ohio, to a hotel on a business trip.
Our team's extensive cybersecurity training has shown us that proper remote security improves enterprise mobility. Employees are more confident, and managers can rest assured their data is protected.
Modern, cloud-based MFA solutions are designed for flexible work, adapting to company or personal devices across multiple locations. This flexibility is essential for the hybrid work models we see in our service areas of Charleston, WV, and Columbus, Ohio.
If you're looking to strengthen your remote workforce security, our team can help you implement the right solution for your specific needs. Check out More info about Cloud-Based Multi-Factor Authentication to learn how we can help protect your distributed team.
One of the most surprising benefits of multi factor authentication is that it can simplify your workday. While it seems counterintuitive, pairing MFA with Single Sign-On (SSO) technology makes access easier.
MFA works hand-in-hand with SSO integration. This combination creates an "authenticate once, access everything" experience that is a game-changer for productivity. In a typical workday, you use many applications, each requiring a password. Without SSO, this means constant logins and password resets, wasting valuable time.
SSO integration changes this. You perform one MFA challenge at the start of your session. After this centralized authentication, you can access all connected apps without further logins.
This provides user convenience and robust security. Our clients in Columbus and Charleston report significant time savings, allowing employees to focus on their work instead of juggling passwords.
Reduced password fatigue is a real benefit. With fewer passwords to remember, users are less likely to use weak or insecure practices, improving overall security.
Improved productivity is measurable. Our cybersecurity training shows that an effective MFA and SSO combination can save employees 10-15 minutes daily on authentication tasks.
This system proves security and efficiency can coexist. A thoughtful MFA and SSO implementation creates a more secure and productive environment—a win-win for everyone.
Selecting the right MFA method isn't one-size-fits-all. The key is to balance security, user experience, and budget.
At Next Level Technologies, our cybersecurity-trained team helps businesses in Columbus, Ohio, and Charleston, WV, make these choices. Our technical experience shows the best MFA solution is one your team will use consistently. When evaluating options, consider the trade-offs between usability and security, implementation costs, and user adoption. Match the method to your risk level and user needs.

| Method | Pros | Cons | Best For |
|---|---|---|---|
| SMS/Email OTPs | Widely available, easy to use | Vulnerable to SIM swapping, phishing | Basic consumer accounts |
| Authenticator Apps | More secure than SMS, works offline | Requires app installation, device sync | Most business & personal use |
| Push Notifications | Very convenient, simple approval | Can lead to "MFA fatigue" attacks | Frequent, low-risk logins |
| Biometrics | Fast, convenient, hard to replicate | Device-dependent, potential for bypass | Securing personal devices |
| Hardware Tokens | Highest security, phishing-resistant | Cost, can be lost/stolen | High-security environments |
Not all MFA methods are equal against sophisticated phishing. With traditional methods like SMS, an attacker can trick you into entering your credentials on a fake site and then use them on the real one.
This is why experts, including CISA, champion phishing-resistant MFA. These methods are designed to stop attackers even if you fall for a fake website. This works through cryptographic authentication tied to your device and the legitimate website's domain. Your device performs a secret handshake with the real site that imposters can't intercept or replay.
FIDO2 and WebAuthn are the leading standards for this technology, using public-key cryptography to create unphishable authentication. This is found in hardware keys like YubiKey and built-in features like Windows Hello or Touch ID.
While any MFA is a huge security improvement, phishing-resistant options eliminate an entire category of attacks. Our team's extensive cybersecurity training confirms that investing in these solutions provides long-term dividends and peace of mind. If you're ready for enterprise-grade protection, explore our Multi-Factor Authentication Solutions.
While the benefits of multi factor authentication are clear, implementation can feel daunting due to concerns about user pushback, cost, and IT support. However, these challenges are manageable with the right approach.
At Next Level Technologies, we've guided hundreds of businesses in Columbus, Ohio, and Charleston, WV, through MFA implementation. Our extensive cybersecurity training and experience show that most problems stem from poor planning, not technical complexity.
The trickiest challenge is often integrating with legacy systems. While cloud apps are simple, older on-premise software may need extra work. Our technical experience allows us to integrate MFA with a wide range of systems. We offer specialized On-Premise Multi-Factor Authentication solutions for these cases.
Employee training is crucial but straightforward. Initial setup is quick, and self-registration options reduce the IT burden while empowering users.
A common pitfall is "MFA fatigue," where constant prompts lead to careless approvals or insecure workarounds, reducing overall security. The solution is Adaptive MFA (or risk-based authentication), which intelligently applies security based on context, working with your team's workflow.
For example, a login from a trusted device at a normal time and location might not require an MFA prompt. But an unusual login attempt, like from a different country at 3 AM, would trigger an immediate challenge. This approach considers factors like IP address, device trust, and login patterns to minimize friction for legitimate users while blocking attackers.
Policies can be fine-tuned to your organization's risk profile. The goal is to reduce unnecessary prompts while protecting against high-risk scenarios. Our Adaptive Multi-Factor Authentication solutions are customized to strike this balance.
A successful MFA rollout depends as much on people as technology. Success comes from clear communication and user buy-in. To ensure a smooth rollout, we recommend a strategy that includes:
This approach makes MFA a natural part of the daily routine.
Our team's extensive cybersecurity training has helped us address common questions about the benefits of multi factor authentication for businesses in Columbus, Ohio and Charleston, WV.
While MFA dramatically improves security, it's not completely foolproof. Bypassing it is exponentially harder than cracking a password but possible for determined attackers. Common bypass methods include social engineering (tricking users into giving up codes) and "MFA fatigue bombing" (spamming requests until one is approved).
SIM swapping is another risk for SMS-based MFA, where attackers take over your phone number. This is why our cybersecurity experts recommend more secure methods. The key takeaway is to use phishing-resistant MFA (like hardware tokens) and never approve an MFA request you didn't initiate.
MFA is more affordable than most expect. Compared to the average $5.17 million cost of a data breach, it's one of the smartest security investments a business can make.
Costs vary. Free options are often included with platforms like Microsoft 365. Advanced features may involve per-user licensing ($3-$15/user/month). Hardware tokens are a one-time cost. Setup and training costs depend on complexity, but the ROI from preventing a single breach is significant. The benefits of multi factor authentication in preventing costly breaches far outweigh the implementation investment.
The future of authentication is evolving toward greater security and convenience.
Our cybersecurity training keeps our team current, ensuring our clients in Columbus and Charleston benefit from the latest advancements toward more secure, seamless, and intelligent authentication.
Passwords alone are not enough. The benefits of multi factor authentication are clear: MFA is essential for protecting your business.
MFA blocks 99.9% of automated attacks, helps prevent data breaches, and ensures regulatory compliance. Considering the multi-million dollar cost of an average data breach, MFA is one of the smartest financial decisions you can make to protect your data, reputation, and bottom line.
Cyber threats are constantly evolving. A proactive security posture that includes robust MFA allows you to stay ahead of them, not just react.
At Next Level Technologies, we help businesses in Columbus, Ohio, and Charleston, WV, transform their security with expert MFA implementation. Our team's extensive cybersecurity training and deep technical expertise ensure a seamless integration, proper training, and ongoing support for your peace of mind.
We understand every business is unique. Whether you need cloud, on-premise, or adaptive MFA, our experience ensures we can tailor a solution that balances security and convenience for your specific needs.
Don't wait for a breach to force your hand. The benefits of multi factor authentication are available now, and expert implementation makes the transition smooth. Take action today to protect your business and your customers.
Ready to take the next step? Protect your business with our Managed IT Services and IT Support.
Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026
Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
