Compliance Without Tears – Cybersecurity Audit Solutions You'll Love
August 1, 2025

Secure your business future. Explore comprehensive security services it, from threat prevention to compliance, and find your ideal partner today.
February 4, 2026

Get top-tier IT Support Worthington OH. Boost efficiency, secure data, and grow your business with expert managed IT services.
February 3, 2026

Unlock innovation & cut costs with expert Open Source managed services. Boost security, efficiency, and compliance for your business.
February 2, 2026
August 1, 2025
Safeguarding your business means understanding cybersecurity audit and compliance solutions. These are systems and processes that help your business:
Cyber threats are growing fast. So are the rules about data. Not following these rules can lead to huge fines, legal trouble, and damage to your reputation. A data breach costs much more than being prepared.
I'm Steve Payerle, President of Next Level Technologies. My team and I have spent years helping businesses in Columbus, Ohio, and Charleston, WV, steer the complex world of cybersecurity audit and compliance solutions, ensuring they stay safe and productive.
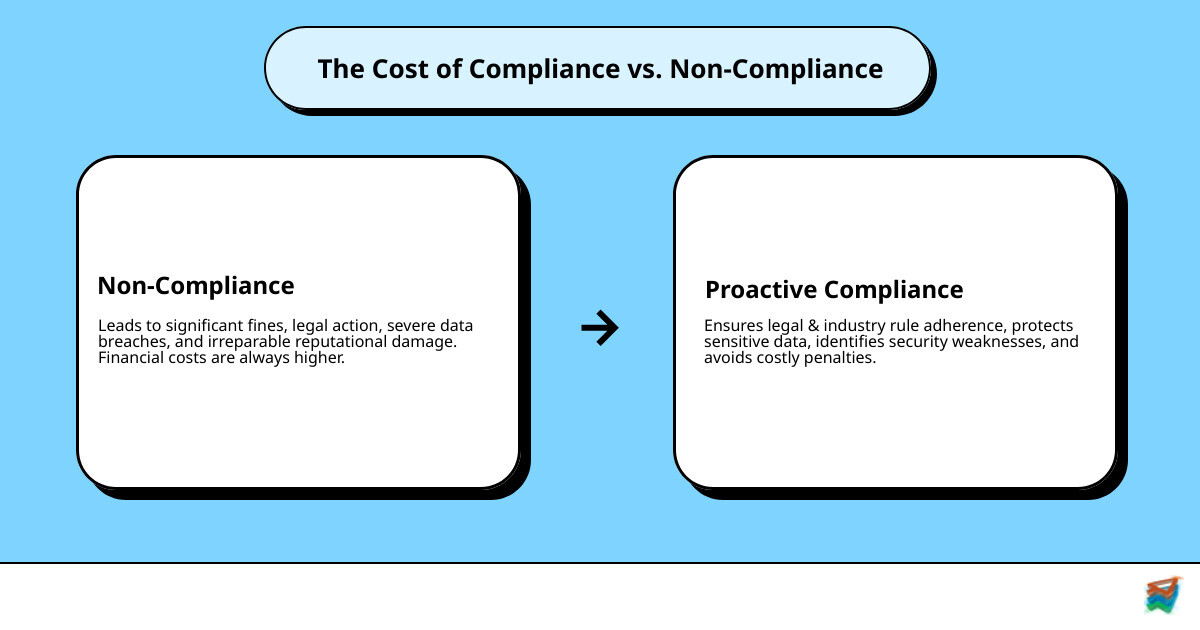
Think of cybersecurity compliance not as a chore, but as a core business strategy. The risks of non-compliance are serious, from huge fines to legal trouble and reputational damage. The financial cost of a proactive cybersecurity audit is always less than the fallout from a data breach. It's a clear choice: invest now to prevent disaster later.
Failing to keep up with cybersecurity regulations raises your risk of data breaches. As digital threats evolve, so do the rules. A rise in cyberattacks on government agencies and large organizations makes it clear: every business must take action to protect itself.
Embracing strong cybersecurity audit and compliance solutions brings significant benefits:
Want to dig a little deeper into the basics? You can learn more about Understanding the Basics of IT Compliance.
The world of cybersecurity compliance is filled with different standards, each designed for specific industries or data types. Here are some of the most common ones:

Achieving and maintaining cybersecurity compliance presents several common challenges:
These challenges show why a smart, well-supported approach to cybersecurity audit and compliance solutions is essential for your business to thrive.
Thankfully, you don't have to tackle these challenges alone. The market offers a robust array of cybersecurity audit and compliance solutions designed to simplify, automate, and manage your journey to compliance. These solutions typically fall into a few key categories: automation platforms, expert-led advisory services, and comprehensive managed compliance services. Choosing the right blend depends on your organization's size, complexity, and internal resources. For strategic insights, you might find value in resources like Shape your 2025 cyber GRC strategy with a complimentary Gartner report. We also offer comprehensive Cybersecurity Compliance Services custom to your needs.

Imagine compliance not as a mountain of paperwork but as a sleek, automated process. That's the promise of compliance automation software. These platforms streamline the entire compliance lifecycle, from evidence collection to continuous monitoring and audit preparation.
Key features include:
These solutions enable you to "do the work once" and apply it across multiple frameworks, making your IT Compliance Monitoring much more efficient.
While automation is a game-changer, the human touch remains indispensable. Expert-led audit and advisory services provide the specialized knowledge and strategic guidance that software alone cannot. These firms bring years of experience and deep technical expertise to the table.
What do they offer?
Our team at Next Level Technologies, with our extensive cybersecurity training and technical certifications, embodies this expert-led approach. Whether you're in Columbus, Ohio, or Charleston, WV, we bring that deep-seated knowledge to every engagement, helping you with IT Internal Audit and more.
For many businesses, especially SMBs, managing cybersecurity and compliance can feel overwhelming. This is where managed security and compliance services shine, offering a cost-effective way to outsource these critical functions to dedicated experts.
Key benefits include:
For businesses looking for comprehensive protection and compliance without the internal burden, exploring Managed Cybersecurity Services is a smart move.
Cybersecurity audit and compliance solutions are more than a checkbox exercise. A cybersecurity audit is a vital tool to reach security goals, reduce cyberattack risks, and build trust. As cyber threats grow, especially against large organizations and government agencies (as shown in this report on increasing cyberattacks), regular, thorough audits are non-negotiable. Audits also provide key insights for your Threat Modeling and Risk Analysis, helping you tackle the biggest weaknesses first.
Artificial intelligence (AI) is also shaking up compliance. An AI-powered approach, combined with human expertise, can help you achieve and maintain compliance at every stage of business growth. This turns governance, risk, and compliance (GRC) from a defensive chore into a proactive business driver. AI and automated workflows can handle repetitive tasks and spot gaps in compliance programs, offering predictive ways to prevent risks.
Automation is a must-have for modern cybersecurity audit and compliance solutions. It transforms the process by:
Even with automation, preparing for a cybersecurity audit requires a clear plan.
Here’s a look at how manual audit prep stacks up against automated solutions:
| Feature | Manual Audit Preparation Checklist | Automated Audit Preparation |
|---|---|---|
| Evidence Collection | Time-consuming, manual gathering from disparate sources, often incomplete. | Automated collection from integrated systems, continuous, comprehensive. |
| Control Monitoring | Periodic, snapshot checks, prone to human error, can miss ongoing issues. | Real-time, continuous monitoring, immediate alerts for deviations. |
| Policy Management | Stored in documents, difficult to track updates and dissemination. | Centralized, version-controlled, automated policy generation and distribution. |
| Risk Assessments | Infrequent, spreadsheet-based, often subjective. | Integrated, continuous risk identification, automated prioritization. |
| Issue Remediation | Manual tracking and follow-up, prone to delays and oversight. | Automated issue tracking, AI-powered remediation suggestions, workflow management. |
| Auditor Collaboration | Email, shared drives, ad-hoc meetings, can be disorganized. | Centralized platform for communication, evidence sharing, and query management. |
| Overall Time/Effort | High, significant drain on internal resources, stressful. | Significantly reduced, more efficient, less stressful. |
To ensure a successful audit, follow these key steps:
By following these steps, you can turn an audit from a dreaded event into a smooth, confidence-boosting experience. Our team at Next Level Technologies, with our deep technical experience and extensive cybersecurity training, is ready to help you with comprehensive IT Compliance Assessments to ensure you're fully prepared.
Navigating cybersecurity audit and compliance solutions can bring up many questions. Here are answers to some of the most common ones.
While related, these two functions are distinct.
A cybersecurity audit is a formal review to verify that your organization meets specific security regulations, standards, or policies. It asks, "Are we following the rules?" Its focus is on compliance.
A risk assessment is a process to identify and analyze potential threats to your data and systems. It asks, "What could go wrong, and what would the impact be?" Its focus is on preparedness. We can help you understand your specific dangers with a Cyber Insurance Risk Assessment.
In short, a risk assessment identifies dangers, while an audit verifies that your safeguards against those dangers are working and compliant.
The timeline to achieve compliance with a framework like SOC 2 varies, typically taking anywhere from 3 to 12 months. The exact duration depends on several factors:
Compliance is an ongoing commitment, not a one-time project.
Yes, absolutely. It's a common misconception that robust cybersecurity audit and compliance solutions are only for large enterprises. They are more accessible and affordable for small and medium-sized businesses (SMBs) than ever before.
Here's why:
Strong cybersecurity is attainable for businesses of all sizes. Learn more about How Managed IT Services Help Small Businesses With Regulatory Compliance.
Navigating the complex and ever-changing world of cybersecurity audit and compliance solutions doesn't have to be a source of constant stress. We've explored how challenging it can seem, with evolving regulations, manual processes, and skill gaps. But here’s the good news: you don't have to face these challenges alone! Imagine compliance becoming a smooth, manageable part of your business, not a constant worry.
That's exactly what we help businesses achieve at Next Level Technologies. We're your dedicated partner in navigating these waters. Whether you're in Columbus, Ohio, or Charleston, WV, our local team is ready to support you.
Our team isn't just experienced; they are highly trained and certified experts. They bring extensive cybersecurity training and technical certifications to every single project. This means you get top-tier advice and solutions, custom just for you. We understand the unique challenges businesses face, especially those in industries often overlooked.
We truly believe that strong cybersecurity audit and compliance solutions should empower your business. They shouldn't hold you back or add unnecessary burdens. Instead, they should be a strong foundation for growth, protecting your data and your reputation.
By partnering with us, you gain more than just a service provider. You get a strategic ally committed to keeping your operations secure. We simplify your compliance journey, letting you focus on what you do best.
Ready to leave compliance worries behind? Let's make compliance stress-free together. Reach out for a free consultation on our managed IT services and IT support today!
Get a free consultation on our managed IT services and IT support
Secure your business future. Explore comprehensive security services it, from threat prevention to compliance, and find your ideal partner today.
February 4, 2026
Get top-tier IT Support Worthington OH. Boost efficiency, secure data, and grow your business with expert managed IT services.
February 3, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
