Stay Compliant: Essential Cybersecurity Services for Your Business
July 2, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
July 2, 2025
Cybersecurity compliance services help protect your business from costly breaches, penalties, and lost trust. If you need a fast answer:
| What Are Cybersecurity Compliance Services? | Why Are They Important? | What Do You Get? |
|---|---|---|
| Expert support to meet legal and industry data rules | Avoid fines, lawsuits, and data leaks | Risk assessments, policy help, audits, staff training |
| Guided framework selection (PCI DSS, HIPAA, etc.) | Win customer trust and contracts | Continuous monitoring, penetration tests, quick reporting |
| Ongoing monitoring and evidence collection | Stay ahead of new threats and changing laws | Roadmap for ongoing improvement and certification |
In short:
Cybersecurity compliance services are expert solutions that keep your business aligned with required security laws and standards—helping you avoid penalties, protect data, and build customer trust.
More companies face bigger risks every year—from ransomware to strict new privacy laws. Regulatory pressure is rising fast for businesses of all sizes in Columbus, Charleston, and beyond. Staying compliant isn't just a checkbox; it's essential for business growth, reputation, and survival.
As Steve Payerle, I bring decades of experience leading teams in cybersecurity compliance services and managed IT for businesses across Ohio and West Virginia, ensuring that our clients protect their data and meet every industry standard.
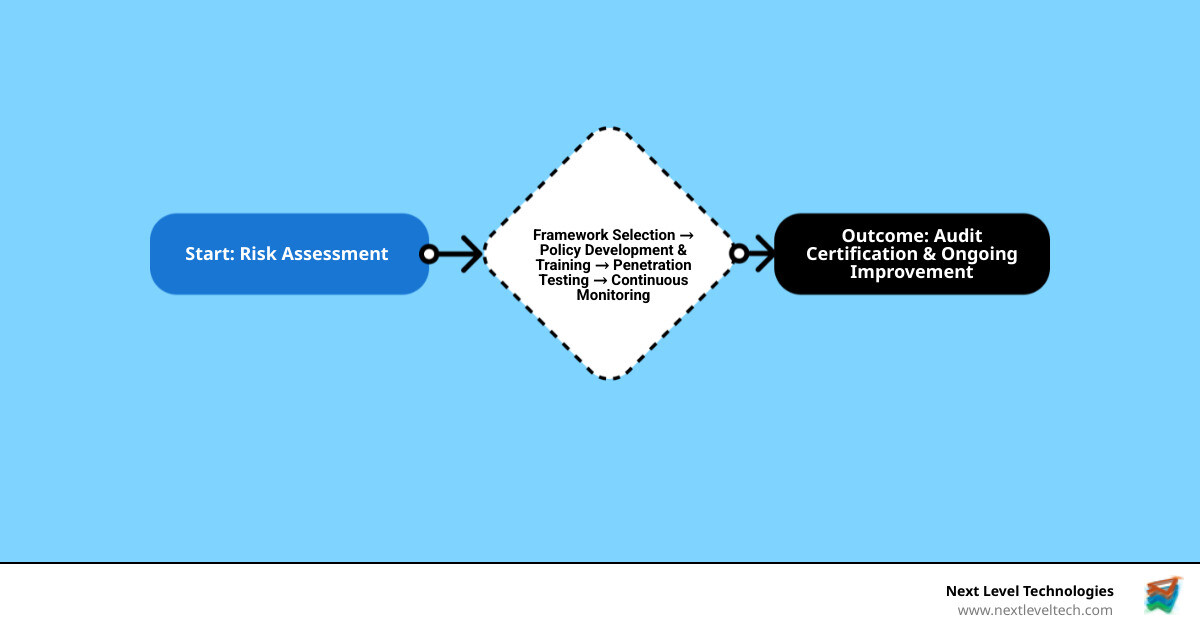
In this guide, we'll walk you through the essential cybersecurity compliance services every business needs:
By the end, you'll have a clear roadmap for protecting your business while meeting every regulatory requirement—without breaking your budget or overwhelming your team.
A solid risk assessment is the starting point for every effective cybersecurity compliance services program. Our engineers02 bring decades of hands-on experience in Columbus and Charleston, digging into servers, laptops, cloud apps257. Using trusted frameworks such as the NIST Cybersecurity Framework and CIS Controls, we trace every pathway attackers might use, then measure the potential business impact.
More info about IT Compliance Monitoring
Choosing the right framework determines how quickly you reach compliance goals. Next Level Technologiess certified team guides you through SOC2, PCI DSS, HIPAA, GDPR, ISO 27001, CMMC, HITRUST, and FedRAMP requirements without duplicate effort.
Most frameworks share building blocks access control, training, and incident response so we crossmap controls and cut cost.
We anchor our guidance to NIST guidelines and proven control families. Continuous cybersecurity training keeps our specialists current on every rule change.
Industry mandates, customer contracts, and growth plans point to the best framework. If you need more than one, our multiframework mapping approach lets you tackle overlapping controls once, then reuse evidence.
Learn more about IT Compliance

Great tools fail if people ignore them. Our cybersecurity compliance services team writes policies that match how your staff actually worksremote, mobile, or inofficeand then trains everyone with short videos, handson simulations, and quarterly phishing drills.
Documentation becomes your proof during audits and insurance reviews, so we automate recordkeeping of policies, signoffs, and refresh cycles.
Pen tests show whether controls really stop attackers. Our certified ethical hackers in Ohio and West Virginia run external, internal, and social engineering tests, plus ASV scans for PCI DSS.
Finding flaws is only step one. We help prioritize, patch, and verify fixes so reports turn into measurable risk reduction.
Automated evidence gathering feeds tickets into your service desk, linking vulnerabilities to remediation tasks. That traceability keeps you auditready yearround.
Risk assessments look wide; penetration tests dive deep. Using both, on different cadences, gives a full security picture without overspending.
Snapshots are outdated the moment theyre taken. We deploy SIEM and MDR platforms that watch your environment 247, then autocollect evidence for auditors.
Quarterly exports of log retention, access reviews, and backup tests mean no more lastminute scramble.
API integrations fold new cloud workloads into monitoring instantly, while AIdriven analytics cut false positives so small teams stay focused.
More info about IT Compliance Monitoring
Audit day should feel routine. We run mock audits, tidy evidence, and coach staff so external assessors glide through.
| Framework | Typical Timeline | Renewal |
|---|---|---|
| SOC 2 II | 612 mo | Annual |
| ISO 27001 | 618 mo | 3 yrs |
| HIPAA | 36 mo | Ongoing |
Using a PlanDoCheckAct cycle, we fold lessons back into the program and keep pace with new regulations.
Certifications open doors to government bids, larger clients, and stronger customer trustturning compliance spending into revenue growth.
Non-compliance can be costly in more ways than one. The penalties depend on which rules you're supposed to follow and how serious the violation is. GDPR fines can reach 4% of your annual global revenue, or €20 million, whichever is more. HIPAA fines range from $100 to $50,000 per incident, with annual caps that can hit $1.5 million. PCI DSS fines can reach $5,000 to $100,000 every single month—plus you might see your transaction fees go up.
But the pain isn't just financial. If customer data is exposed, you could face lawsuits or need to notify every affected person. Many states require public disclosure after a data breach, which can turn one incident into a full-blown PR nightmare. Reputational damage is often harder to fix than any technical problem.
Customers might lose confidence and take their business elsewhere. Insurance providers may deny coverage or hike your premiums. You could even lose out on important contracts if your cybersecurity compliance services aren't up to par. Compliance is about survival, not just red tape.
How often you need to check your compliance status depends on your industry, the frameworks you follow, and your unique risk profile. Most standards call for at least annual assessments. If you're under SOC 2 Type II, you'll be doing continuous monitoring over a 12-month window with a yearly review. ISO 27001 has annual audits, with a more in-depth recertification every three years. PCI DSS requires an annual full assessment, with quarterly vulnerability scans.
But don't wait for the calendar to tell you when to act. Major changes—like rolling out a new app, changing up your infrastructure, or onboarding key staff—are good reasons to review your compliance status right away. Regular checkups help you spot issues before they become big headaches.
Organizations at higher risk (like those handling sensitive healthcare or financial data) might benefit from quarterly reviews. Lower-risk businesses might be fine with one deep-dive per year, plus lighter check-ins after big changes. Our team at Next Level Technologies can tailor a schedule that fits your needs and keeps you ready for anything.
Absolutely—they can, and honestly, they must. The data shows that most small businesses don't survive long after a major cyberattack. Upfront investments in cybersecurity compliance services are almost always cheaper than trying to recover from a breach.
At Next Level Technologies, we specialize in scaling compliance to match your business size and budget. Our technical experts look for high-impact, cost-effective controls—think smart employee training, stronger passwords, and reliable backups. These steps can make a huge difference and don't always require a big spend.
Managed compliance services are especially helpful for smaller teams. Instead of hiring full-time IT and security staff, you get access to our extensive cybersecurity training and real-world experience. It's a fraction of the cost, and you only pay for what you need.
Many insurance companies offer discounts for businesses with solid security programs. Plus, more customers are asking for proof of compliance before they sign on. That means your investment can help you win contracts, save on insurance, and avoid the costs of a breach all at once.

At Next Level Technologies, our team in Columbus, Ohio and Charleston, WV is ready to guide you. We bring deep technical expertise and the latest cybersecurity training, helping you get—and stay—compliant, no matter your size or industry. If you have more questions or want to get started, learn more about our cybersecurity compliance services.
Cybersecurity compliance services aren't just about checking boxes or avoiding fines—they're about building a rock-solid foundation that lets your business grow with confidence. When you get compliance right, something amazing happens: your customers trust you more, new doors open, and you gain real competitive advantages that keep paying dividends.
The secret sauce? Treating compliance as part of your overall business strategy, not just a technical hurdle to jump over. When you weave together solid risk assessments, smart framework choices, clear policies, thorough testing, continuous monitoring, and expert audit support, you create something powerful—a security program that actually makes your business stronger.
Here at Next Level Technologies, we've walked this path with hundreds of businesses across Ohio and West Virginia. Our team brings years of hands-on experience and extensive cybersecurity training to every project. We're based in Columbus and Charleston, but more importantly, we understand the real challenges you face every day.
What sets us apart is how we approach each client's unique situation. No two businesses are exactly alike, and cookie-cutter solutions just don't work. Whether you're a small business taking your first steps into compliance or a growing company looking to strengthen what you already have, we meet you where you are.
We can guide your organization through every phase—from that initial risk assessment all the way through to the ongoing improvements that keep you ahead of new threats. Our comprehensive cybersecurity compliance services aren't just about keeping you safe and compliant—they're about giving you the peace of mind to focus on what you do best: growing your business.
Ready to turn cybersecurity from a worry into a competitive advantage? Let's talk about how we can help.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
