Don't Get Hacked: Simple Cybersecurity for Every Business
November 14, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
November 14, 2025
Cybersecurity for business isn't optional anymore—it's essential for survival. The numbers tell a sobering story: 73% of small and mid-sized businesses experienced a data breach or cyberattack in 2023. This isn't a distant threat; it's happening now.
Key Business Cybersecurity Essentials:
Cybercriminals don't care about your company size. They use automated tools 24/7 to find easy targets. Small businesses often assume they're "too small to be a target," but attackers see that as an advantage. Weak security means easy money.
A single breach can lead to financial losses, lost customer trust, system downtime, legal fines, and permanent reputation damage.
The good news? Most cyberattacks are preventable with basic security measures. You don't need a massive IT budget to protect your business—you just need to understand the fundamentals.
As Steve Payerle, President of Next Level Technologies, I've spent over 15 years helping businesses across Columbus, Ohio, and Charleston, WV build effective cybersecurity for business programs. This guide will show you how to protect your business using the same practical strategies we implement for our clients.

Let me be blunt: cybercriminals don't care if you're a Fortune 500 company or a local business with five employees. They run automated scans probing for weaknesses in any system they can find. Your business has something they want—customer data, financial information, or a computer to hijack. The misconception that "we're too small to be targeted" makes small businesses attractive targets because they often have weaker defenses. Understanding the real threats is the first step in building effective cybersecurity for business defenses.
A cyberattack's financial devastation extends far beyond the initial incident. Direct costs include forensic investigations, system restoration, and potential ransom payments. These can easily reach tens or hundreds of thousands of dollars.
Indirect costs are often worse. System downtime means lost revenue. Your team scrambles to manage the crisis instead of serving customers, causing missed deadlines and stalled projects. If customer data is compromised, you face potential lawsuits and regulatory fines from bodies like HIPAA or GDPR, which can be substantial.
The damage to your reputation might be the costliest consequence. When customers learn their sensitive information was exposed, trust evaporates. Rebuilding that loyalty can take years, if it's possible at all. This is why cyber insurance has become a critical part of risk management; it won't prevent an attack, but it can help you survive the financial aftermath.
The threat landscape changes, but certain attacks remain effective. Here are the ones our highly trained technical staff at Next Level Technologies sees targeting businesses daily.
Malware is any malicious software designed to damage or gain unauthorized access to your systems, including viruses, worms, and trojans.
Ransomware is the weapon of choice for cybercriminals. It encrypts your files and demands a ransom to restore access. With 63% of small businesses facing ransomware, it's a primary threat.
Phishing attacks exploit the human element with sophisticated emails, texts, or fake websites that look legitimate. The goal is to trick someone into revealing login credentials or other sensitive data.

Business Email Compromise (BEC) attacks are particularly devastating. Attackers impersonate executives to manipulate employees into making fraudulent wire transfers, costing businesses hundreds of thousands in a single transaction.
Insider threats come from within, whether intentional or accidental. A disgruntled employee might steal data, or a well-meaning team member could click a bad link.
Denial-of-Service (DoS) attacks flood your systems with traffic until they collapse, taking your website and email offline and cutting you off from customers.
Traditional security tools can't handle these evolving threats, which is why businesses need advanced threat protection solutions to stop sophisticated attacks.
Your biggest cybersecurity vulnerability isn't your firewall—it's your people. Research shows 88% of data breaches result from employee mistakes, as attackers are skilled at manipulating human psychology.
This is why employee training is essential. Your team must learn to recognize phishing, use strong passwords, handle sensitive data, and report suspicious activity without fear. Regular training keeps security top of mind.
Leadership buy-in makes all the difference. When executives champion cybersecurity, it becomes a business priority, not just an IT project. At Next Level Technologies, our extensively trained staff works with leadership in Columbus, Ohio, and Charleston, WV, to establish this security-first mindset and maintain IT security policy compliance.
Building a culture of security transforms your business. Employees become part of the defense, thinking about security before they act. This gives you a competitive advantage. Customers want to do business with companies they trust to protect their information. Demonstrating robust security practices differentiates you from competitors. Investing in cybersecurity for business isn't just about avoiding disaster; it's about building trust and protecting your reputation.
Think of cybersecurity for business like building a castle with multiple layers of defense. This layered security approach protects your business from multiple angles. The first step is a thorough risk assessment to identify vulnerabilities in your people, processes, and technology. Our highly trained technical staff at Next Level Technologies, serving businesses in Columbus, Ohio and Charleston, WV, brings years of cybersecurity expertise to these assessments, spotting weak points before attackers do. Understanding your IT infrastructure and security is the foundation of your defense.
Your laptops, desktops, and mobile devices are the front lines. If you're using legacy antivirus, you're fighting today's threats with yesterday's weapons. Traditional AV relies on recognizing known threats, but by the time a new threat is cataloged, it has already caused damage.
Next-Generation Antivirus (NGAV) is different. It uses machine learning and behavioral analysis to spot suspicious activity from both known and unknown threats.
| Feature | Legacy Antivirus (AV) | Next-Generation Antivirus (NGAV) |
|---|---|---|
| Detection Method | Signature-based | Machine Learning, AI, Behavioral Analysis |
| Threats Covered | Known threats only | Known and unknown (zero-day) threats |
| Prevention Capability | Limited, reactive | Proactive, predictive |
| Performance Impact | Can be heavy, often scans in batches | Lightweight, real-time |
| Management | Often complex, manual updates | Cloud-managed, automated |
Endpoint Detection and Response (EDR) adds another layer, acting like a security camera system that continuously monitors and alerts you to suspicious activity on your devices.
Your network also needs protection. A robust firewall acts as a gatekeeper for traffic. Your Wi-Fi must be locked down with WPA2 or WPA3 encryption and a strong, unique password. For remote employees, secure remote access solutions like Virtual Private Networks (VPNs) are essential. A VPN creates an encrypted tunnel for data, protecting it from prying eyes on insecure networks like public Wi-Fi. Warn your team about the risks of public Wi-Fi.
Not everyone needs access to everything. The principle of least privilege dictates that you give people only the permissions they need to do their jobs. This limits the damage if an account is compromised.
The single most powerful security measure you can implement is Multi-Factor Authentication (MFA). It requires users to prove their identity with two or more factors—something they know (a password) and something they have (a code from an app).

Even if a hacker steals a password, they can't get in without that second factor. We've seen MFA stop countless attacks for our clients. For a complete understanding, read our guide on Multi-Factor Authentication (MFA) explained.
Strong password policies are your next line of defense. Require at least 12 characters, use unique passwords for each account, and encourage password managers. Role-based access control (RBAC) ties permissions to job functions, simplifying access management.
Email is a top attack vector. Email authentication is critical to cybersecurity for business. Technologies like SPF, DKIM, and DMARC verify that emails claiming to be from your domain are legitimate, preventing scammers from impersonating you. Our extensively trained team can configure these protocols correctly to avoid blocking legitimate emails.
Your data needs protection at every stage. Data encryption should be applied both when data is stored (at rest) and transmitted (in transit), scrambling it so it's unreadable if intercepted.
A solid data backup strategy is your safety net. We recommend the 3-2-1 backup rule: keep three copies of your data on two different media types, with one copy offsite or in the cloud. Cloud backups are popular because they are accessible anywhere and protected from physical disasters. Crucially, you must regularly test your backups to ensure they are not corrupted. Don't wait for a ransomware attack to find your backups have failed. Our guide to data backup solutions for small business can help you build a reliable strategy.
Think of cybersecurity for business as a marathon, not a sprint. It's an ongoing process that requires a living, documented plan. When a cyberattack hits, the last thing you want is your team scrambling. A clear, written plan eliminates chaos. Our team at Next Level Technologies has guided countless businesses through creating and testing these plans, and preparation makes all the difference. Good IT security incident management is about having a roadmap ready before you need it.
You don't have to reinvent the wheel. The National Institute of Standards and Technology (NIST) created a free, practical Cybersecurity Framework (CSF) for businesses like yours.
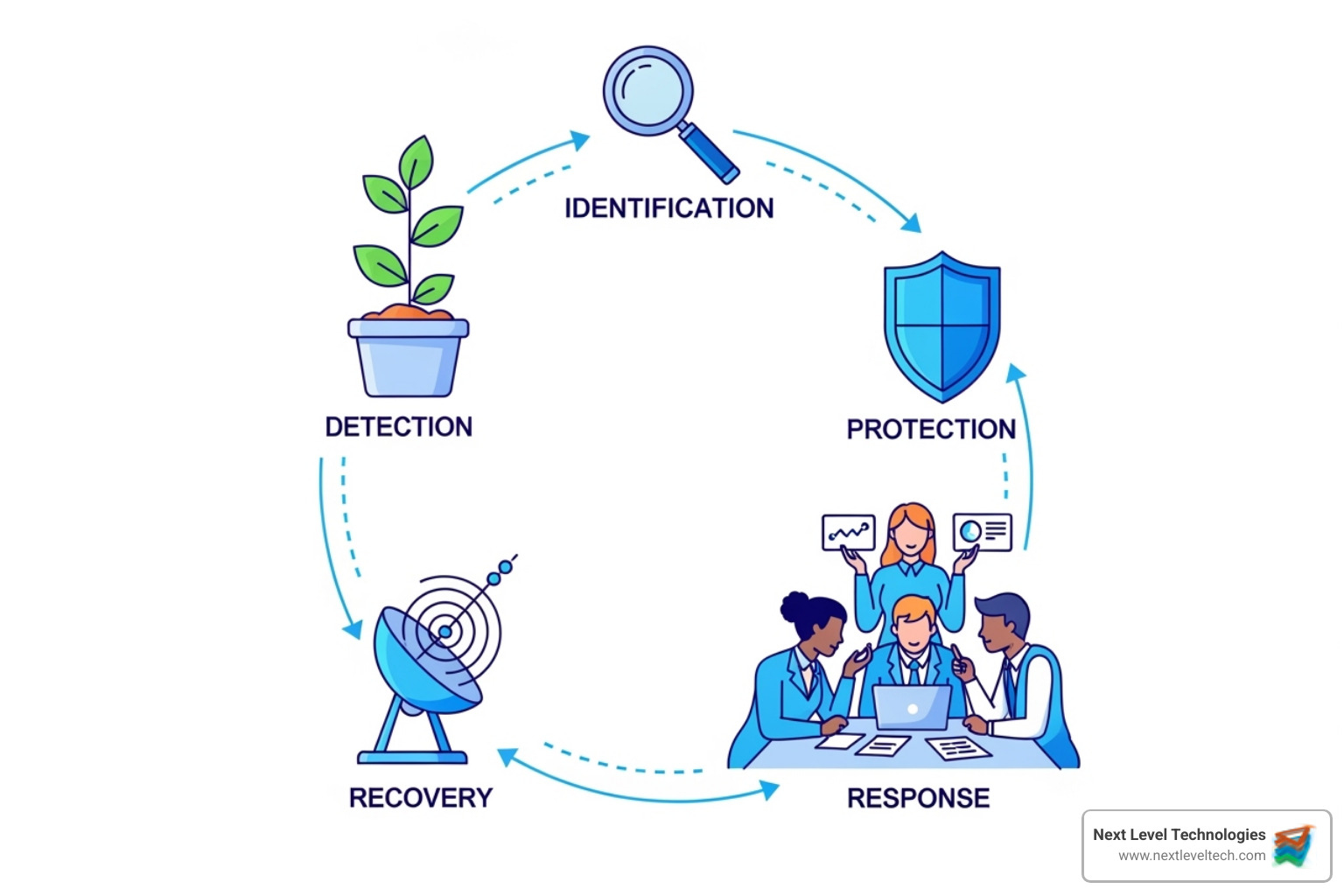
The framework breaks down cybersecurity into five core functions: Identify assets, Protect them, Detect threats, Respond to incidents, and Recover operations. The newest version, CSF 2.0, adds a Govern function, emphasizing that cybersecurity needs leadership support and clear policies from the start.
The NIST CSF helps you see where you are and where you need to go, showing you security gaps clearly. Our extensively trained staff uses this framework with clients in Columbus, Ohio, and Charleston, WV, to build security programs that fit their operations. You can learn more at the NIST Cybersecurity Framework (CSF) official site.
An Incident Response Plan is your playbook for a crisis. It tells everyone what to do, who is responsible, and in what order. An effective IRP has six phases:
The secret ingredient is regular practice. We recommend tabletop exercises—simulated attacks where your team walks through the plan. It's like a fire drill for IT security, revealing gaps and building confidence. Our cybersecurity team, with its extensive training in incident response, can help you design and test these plans. Businesses that practice their IRPs recover significantly faster.
Most small and mid-sized businesses lack a full-time, expert cybersecurity team. Partnering with a provider specializing in cybersecurity for business is a smart solution.
When evaluating partners, look for:
Proactive monitoring is key. It's the difference between installing smoke detectors and waiting for a fire. Working with managed cybersecurity services gives you enterprise-level expertise at a fraction of the cost, letting you focus on your business while experts handle the threats.
I hear this question all the time. The reality is: you can't afford not to invest in basic security. The good news is you don't need a Fortune 500 budget.
Start with fundamentals that deliver the biggest bang for your buck. Multi-Factor Authentication (MFA) is often free and stops most account compromises. Regular software updates and strong password policies cost nothing but time. Many cloud services also include robust, enterprise-grade security features.
The smartest financial decision is often partnering with a managed cybersecurity services provider. Hiring a single cybersecurity expert can cost over $100,000 per year. With a managed services partner, you get an entire team of highly trained cybersecurity professionals for a predictable monthly fee. This approach provides scalable expertise, 24/7 monitoring, and proactive threat detection without the high overhead of an in-house team.
If I could only recommend one measure, it would be Multi-Factor Authentication (MFA), hands down.
MFA is powerful because even if criminals steal your password, they still can't access your accounts without the second factor (like a code from your phone). It's like having a second, different lock on your door. MFA blocks over 99% of automated attacks—an incredible return for something so simple to implement.
Focus on protecting your most critical systems first: email, cloud applications, financial software, and administrative access. The few seconds it takes to enter an authentication code creates a barrier that stops most attackers cold. It's the most effective step you can take today to improve your cybersecurity for business posture.
Knowing where to report a cyberattack helps you respond quickly. Time is critical. After activating your Incident Response Plan, report the incident to these authorities:
Also, notify your cyber insurance provider immediately, as required by your policy, and contact any customers whose data may have been compromised. Our team at Next Level Technologies has extensive experience guiding businesses through these reporting processes and the recovery that follows. You don't have to steer it alone.
You've learned the essentials of cybersecurity for business: strong access controls, layered defenses, and incident response planning. But cybersecurity isn't a one-time setup; it's an ongoing commitment that requires constant attention as threats evolve. Your digital infrastructure deserves expert care.
That's where the right partner makes all the difference. At Next Level Technologies, we've spent years helping businesses in Columbus, Ohio, and Charleston, WV steer modern cybersecurity. Our team is passionate about protecting what you've built. With extensive cybersecurity training and real-world experience, our highly trained staff brings a depth of knowledge that most businesses can't maintain in-house.
We specialize in serving businesses of all sizes, especially those in industries often overlooked by larger IT providers. Your challenges aren't generic, so your solutions shouldn't be either.
Our comprehensive approach covers everything from implementing multi-factor authentication and endpoint protection to developing your incident response plan. We provide proactive, 24/7 monitoring, not just reactive fixes. Think of us as your dedicated IT security team, keeping threats at bay so you can focus on your business.
The cost of a cyberattack far exceeds the investment in proper protection. You've seen the risks. Now is the time to act. Don't gamble with your business's future.
Get expert Managed IT Services and IT Support and let's build the secure, resilient foundation your business deserves.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
