Unlocking Security: How Multi-Factor Authentication Protects You
September 5, 2025
Optimize IT spending & boost ROI with it cost management software. Gain visibility, cut waste, and drive strategic growth.
March 6, 2026

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026

Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026
September 5, 2025
Understanding how does multi factor authentication work is critical for any business in today's cyber threat landscape. MFA requires users to provide two or more verification factors before gaining access. The process is simple:
In a world of constant phishing attacks and data breaches, passwords alone are not enough. Research from Microsoft shows that MFA can prevent 99.9% of automated attacks, making accounts with it enabled significantly less likely to be compromised.
Think of MFA like securing your front door with both a deadbolt and a keypad. Even if a thief steals your key (password), they still can't get in without the code (second factor). This layered approach is what makes MFA so effective.
The stakes are particularly high for businesses handling sensitive data. A single breach can lead to devastating financial loss, regulatory penalties, and a damaged reputation.
As President of Next Level Technologies, I've seen how vital robust cybersecurity is. My team, with its extensive cybersecurity training, has helped countless businesses in Columbus, Ohio, and Charleston, WV, implement comprehensive MFA solutions. Understanding how does multi factor authentication work is the key difference between a secure business and a cyberattack victim.
Running a business with only password protection is like using a screen door to protect a bank vault. Multi-Factor Authentication (MFA) is a security system that requires two or more different types of proof to verify your identity, acting as a digital bodyguard against cybercriminals.
Why is MFA essential? Modern threats are sophisticated. Credential stuffing uses stolen login details from one breach to attack other sites, while phishing attacks trick employees into revealing their credentials. MFA creates multiple checkpoints that hackers must overcome, making it a critical component of any Identity and Access Management (IAM) strategy.
The benefits are clear: MFA provides increased security for your entire digital ecosystem and is especially valuable for remote workforce protection, ensuring consistent security standards everywhere. As business processes move online amid rapid digital change, MFA is essential for survival.
According to a Microsoft study on MFA effectiveness, implementing it can block 99.9% of automated account attacks—a game-changer for your security posture.
The uncomfortable truth of single-factor authentication risks is that a compromised password leaves your entire digital kingdom vulnerable. The data breach consequences can be devastating, including financial theft, business disruption, and loss of customer trust.
This is where a layered defense becomes your lifeline. MFA ensures that even if a password is stolen, attackers are still locked out without the second factor. Beyond protecting sensitive data, MFA helps businesses meet strict compliance requirements like HIPAA. It provides peace of mind, allowing you to focus on growth instead of worrying about the next cyber attack.
Let's clarify some common terms. While often used interchangeably, 2FA, two-step verification, and MFA have key differences.
The number of factors and security levels you implement should depend on your specific business needs and risk tolerance. Understanding these distinctions helps you make an informed decision.
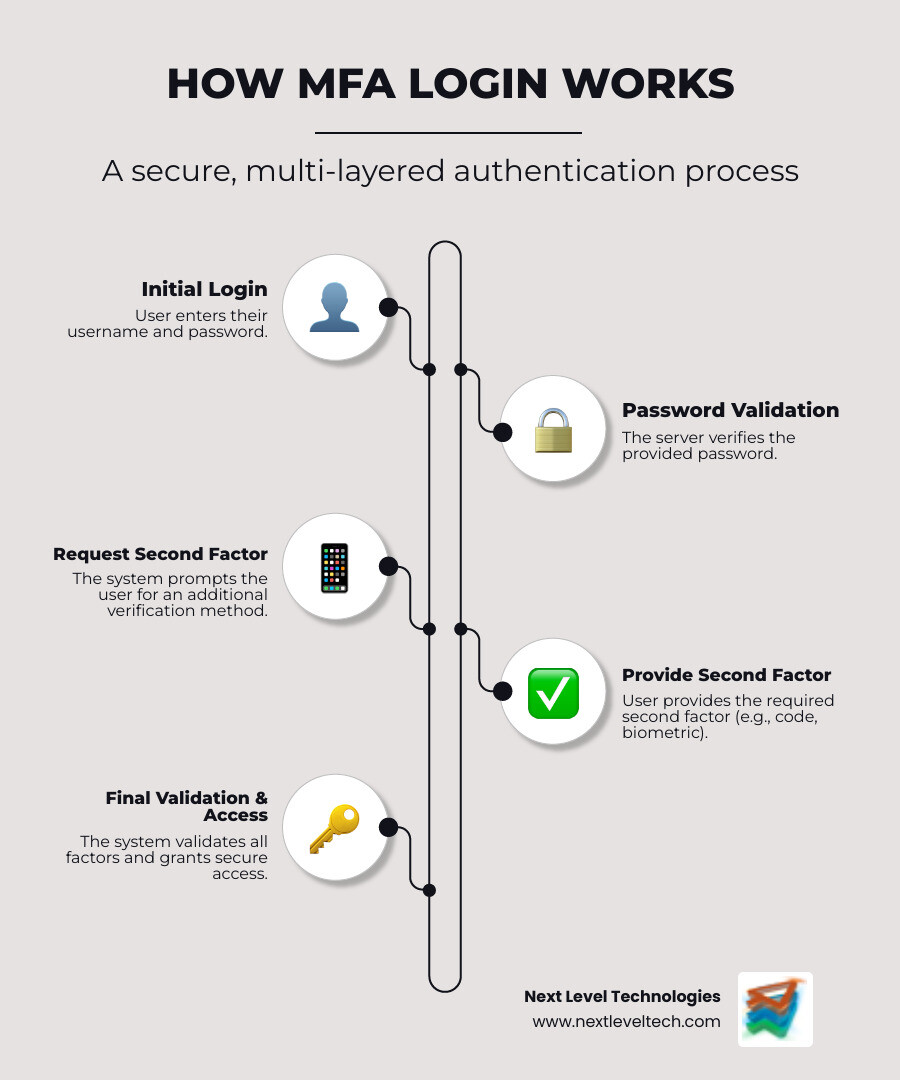
Now that we've covered the what and why, let's explore how does multi factor authentication work behind the scenes. The process involves a secure conversation between you and the server, with multiple rounds of user verification and server validation.

This multi-step authentication process establishes secure communication, ensuring that even someone with your password remains locked out without the additional factors. It's like a high-security building that requires both an ID card and a fingerprint scan to enter.
The user sign-in process is designed to be both thorough and user-friendly. Here’s a quick walkthrough:
In my experience helping businesses in Columbus, Ohio, and Charleston, WV, this process becomes second nature to users in just a few days. The extra few seconds it takes provides an exponential security boost.
Modern MFA is smarter than a simple, rigid system. It uses adaptive and cloud-based approaches to balance security with convenience.
Adaptive Multi-Factor Authentication uses risk-based authentication to adjust security requirements based on user context. If you log in from your usual office device during business hours, it might be seamless. But an attempt from an unrecognized location at 2 AM would trigger a request for more proof. It analyzes signals like geolocation and device trust to make intelligent decisions.
Cloud-Based Multi-Factor Authentication is essential for the modern workplace where data and apps live in the cloud. Unlike traditional on-premise solutions, cloud-based MFA integrates seamlessly with all your services, scaling effortlessly as your business grows. Our cybersecurity-trained team has implemented these systems for countless businesses, providing one comprehensive solution to protect everything, everywhere.
To truly grasp how does multi factor authentication work, you must understand its three foundational pillars. Each represents a different category of proof you can offer to verify your identity: something you know, something you have, and something you are.
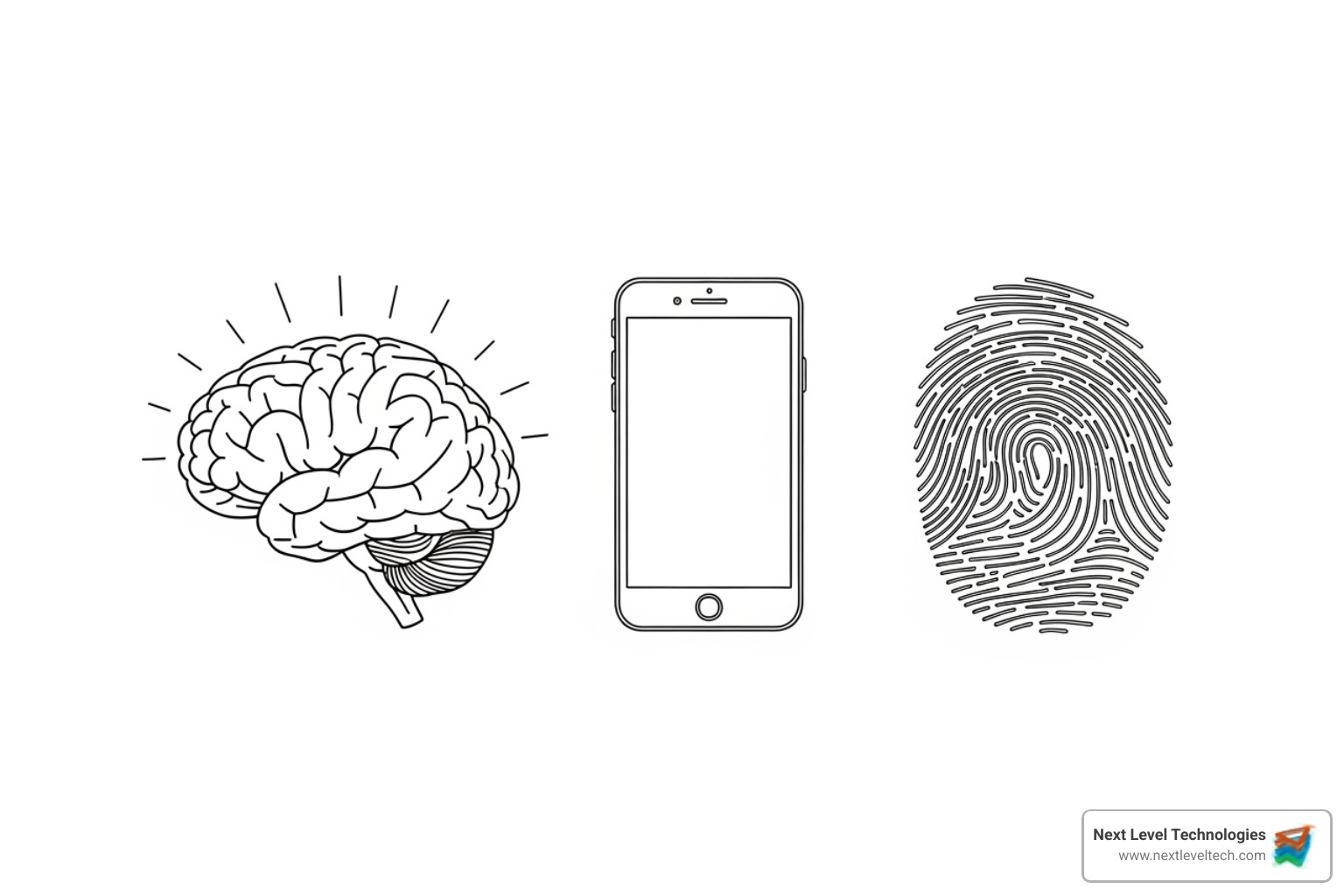
The strength of MFA comes from combining factors from at least two of these pillars. A cybercriminal might steal your password (knowledge), but they would still need your phone (possession) or fingerprint (inherence) to succeed.
This is the most common factor, but also the most vulnerable. It includes:
Knowledge factors alone are no longer sufficient due to their vulnerability to phishing and guessing.
This factor relies on a physical item in your possession.

We help clients implement comprehensive Online Multi-Factor Authentication strategies that account for these real-world options.
This pillar uses your unique biological and behavioral traits, which are very difficult for attackers to replicate.
Inherence factors are naturally phishing-resistant. Our extensively trained staff in Columbus, OH, and Charleston, WV, has deep experience implementing biometric solutions that provide both ironclad security and user-friendly convenience.
While MFA is a powerful security tool, it's not a silver bullet. Understanding the benefits and drawbacks of MFA is crucial. The benefits are clear—drastically reduced risk—but drawbacks can include initial setup time and a slight delay at login. A solid implementation strategy is key to maximizing security without harming the user experience.
Our highly trained staff in Columbus, Ohio, and Charleston, WV, leverages extensive cybersecurity training to find the sweet spot between ironclad security and seamless daily operations for your team.
Sophisticated attackers have developed ways to target MFA. Here’s what to watch for:
Successful MFA implementation requires a thoughtful strategy. Our team has perfected this process over years of experience.
Following these practices, as detailed in our Multi-Factor Authentication Solutions, transforms MFA into a resilient defense mechanism.
These are common questions we hear from business owners in Columbus, Ohio, and Charleston, WV. Our team's extensive cybersecurity training provides the answers.
How does multi factor authentication work with Microsoft 365 is seamless. It integrates directly into the sign-in process for apps like Outlook, SharePoint, and Teams.
Microsoft Entra ID (formerly Azure AD) is the authentication engine. When MFA is enabled, it supports methods like the Microsoft Authenticator app, codes, SMS, and phishing-resistant FIDO2 security keys. The real power lies in Conditional Access policies, which our highly trained staff helps configure. These smart rules can require MFA for risky sign-ins (e.g., from an unfamiliar location) but allow seamless access in low-risk scenarios. This protects your cloud resources without frustrating users. For technical details, see Microsoft's guide on Enabling MFA for Microsoft 365.
The honest answer: MFA is not foolproof, but it stops the vast majority of attacks and makes a successful breach dramatically harder. Most attackers will move on to easier targets.
Bypasses typically rely on social engineering, not technical hacking. In an MFA fatigue attack (like the 2022 Uber breach), criminals with a stolen password spam you with login requests, hoping you'll approve one. SIM swapping is another threat if you use SMS for authentication. Advanced phishing can also try to intercept codes, but phishing-resistant methods like FIDO2 security keys defeat this.
The key takeaway is that while sophisticated attacks exist, they require far more effort. User vigilance is crucial. Never approve an MFA request you didn't initiate.
Let's be honest: MFA adds an extra step that can take 5 to 30 seconds. However, this minor delay is insignificant compared to the weeks of disruption a security breach would cause.
Modern solutions greatly reduce the inconvenience. Adaptive MFA is smart, often skipping the second factor for routine, low-risk logins. User-friendly methods make the process fast:
Most users barely notice the process after a few weeks. The peace of mind from knowing your business is protected is well worth the small adjustment. Our cybersecurity expertise helps you strike the right balance between security and convenience.
Understanding how does multi factor authentication work is essential for protecting your digital assets. By requiring multiple forms of proof—something you know, have, and are—MFA creates a layered defense that is exponentially stronger than a password alone. Even if a password is stolen, attackers are still locked out.
MFA is a foundational security measure that enables your business to accept digital change, from supporting a remote workforce to migrating to the cloud. While no solution is perfect, MFA raises the security bar so high that most attackers will simply move on.
The peace of mind from proper MFA implementation is invaluable, allowing you to focus on running your business, not worrying about the next cyber threat.
At Next Level Technologies, we are built on proactive protection and expert IT support. Our highly trained staff brings extensive cybersecurity training and real-world experience to every MFA implementation. We specialize in helping businesses in Columbus, Ohio, and Charleston, WV, access enterprise-level security solutions.
Our team works with you to choose the right methods, train your employees, and create recovery plans that keep your business secure and productive. Don't wait for a security incident. The cost of implementing MFA is a fraction of the cost of a data breach.
Ready to take your security to the next level? Learn more about our Managed IT Services and IT Support and find how our expertise can protect your business with comprehensive, layered security.
Optimize IT spending & boost ROI with it cost management software. Gain visibility, cut waste, and drive strategic growth.
March 6, 2026
Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
