Multi Factor Magic – How Online Authentication Keeps You Safe
July 17, 2025

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026

Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026

Protect your data. Learn how cloud backup services for business ensure recovery, continuity, and security for your enterprise.
March 3, 2026
July 17, 2025
Online multi factor authentication is a security method that requires users to verify their identity using two or more different factors before accessing accounts or systems. Here's what you need to know:
What is Online Multi-Factor Authentication?
Why It's Essential:
How It Works:
The reality is stark: data breaches happen daily, and hackers constantly develop new ways to steal passwords. As one cybersecurity expert puts it, "relying on just usernames and passwords to secure your online accounts is no longer considered safe."
For mid-sized businesses, the stakes are even higher. A single compromised account can lead to ransomware attacks, data theft, and costly downtime that disrupts operations for weeks.
I'm Steve Payerle, President of Next Level Technologies, and I've been helping businesses in Columbus, Ohio and Charleston, WV strengthen their cybersecurity defenses since 2009. Our extensively trained cybersecurity staff has implemented online multi factor authentication solutions for hundreds of companies, dramatically reducing their risk of account takeovers and data breaches.
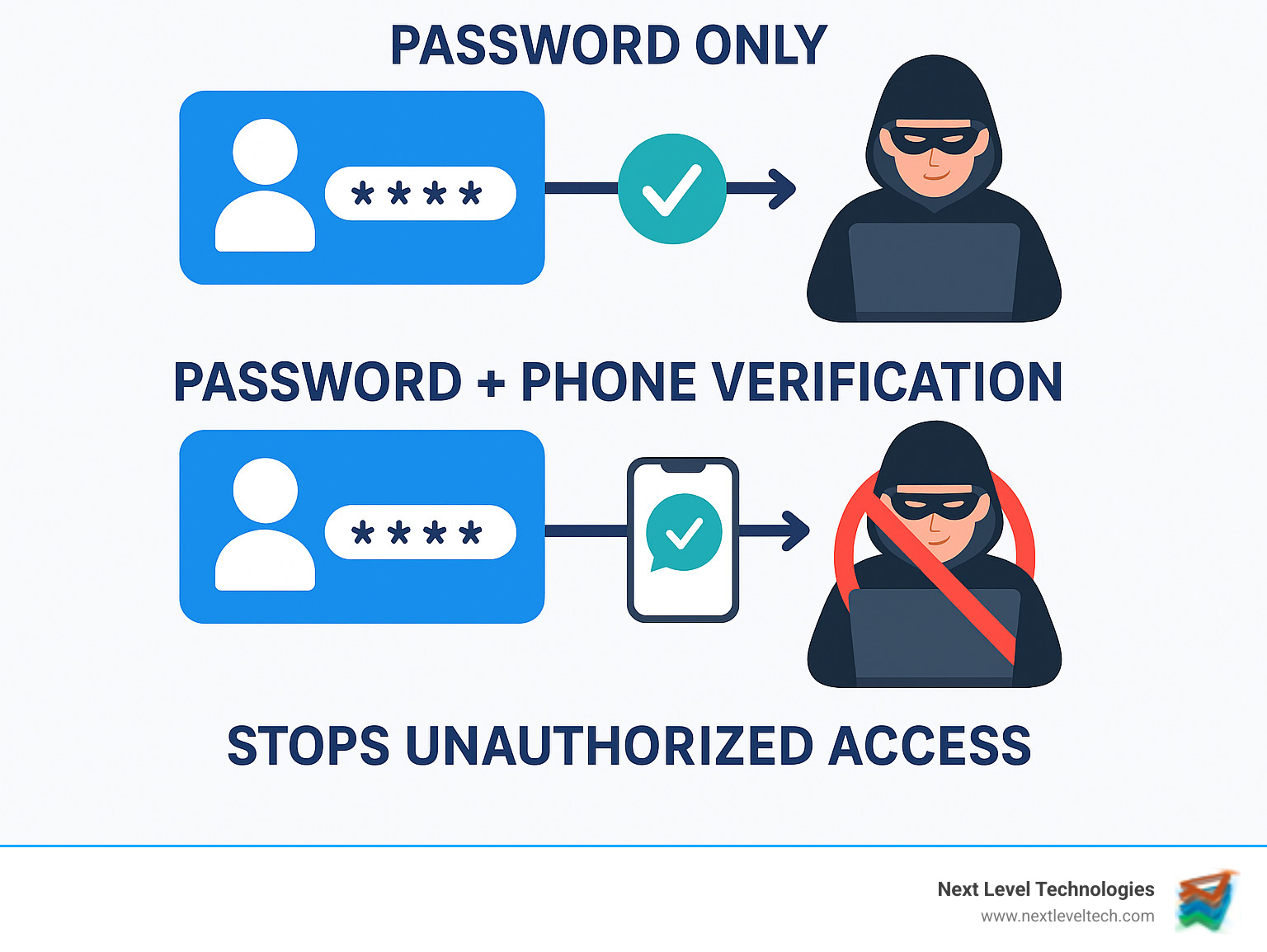
Picture this: you've got a strong password protecting your front door, but a determined burglar still manages to pick the lock. Now imagine if you had a second deadbolt that required a completely different key. That's essentially what online multi factor authentication does for your digital accounts – it adds that crucial second layer of protection.
Cybercriminals have become incredibly sophisticated. They're not just trying random passwords anymore. Instead, they're using advanced techniques like credential stuffing, where they take millions of stolen username and password combinations from data breaches and systematically try them across different websites. They're also employing brute force attacks that can crack weak passwords in minutes.
This is where online multi factor authentication becomes your digital superhero. At its core, MFA is a security method that requires users to provide two or more different types of verification before accessing an account or system. Think of it as your bouncer who checks both your ID and your invitation before letting you into the VIP section.
MFA is a cornerstone of modern Identity and Access Management (IAM) strategies. It dramatically reduces the risk of account takeover attempts, even when passwords have been compromised. Our cybersecurity team has seen how implementing MFA can transform a company's security posture – it's like upgrading from a screen door to a vault.
For businesses looking to strengthen their overall security framework, you can explore our comprehensive Cyber Security Services to see how we help companies build robust defenses.
Let's clear up some confusion that even tech-savvy folks sometimes have. You've probably heard the terms Multi-Factor Authentication (MFA), Two-Factor Authentication (2FA), and Two-Step Verification (2SV) thrown around interchangeably. While they're related, they're not exactly the same thing.
Multi-Factor Authentication (MFA) is the umbrella term. It requires users to provide two or more verification factors from different categories to prove their identity. These categories are based on something you know (like a password), something you have (like your phone), and something you are (like your fingerprint).
Two-Factor Authentication (2FA) is actually a specific type of MFA that uses exactly two different verification factors. For example, entering your password and then confirming a code sent to your phone. It's precise and effective.
Two-Step Verification (2SV) is the less secure cousin. While it requires two steps, both might come from the same category. For instance, entering your password and then answering a security question – both are things you know. It's better than just a password, but not as robust as true MFA.
Our extensively trained cybersecurity staff always recommends true MFA over 2SV because it provides stronger protection against sophisticated attacks.
Here's a sobering reality: password vulnerability is at an all-time high. Most people use passwords that are either too simple, reused across multiple accounts, or both. Hackers know this, and they're taking advantage of it every single day.
Online multi factor authentication serves as a powerful shield against the most common cyber threats that keep business owners awake at night. When hackers launch brute force attacks – essentially trying thousands of password combinations until they find the right one – MFA stops them cold. Even if they crack your password, they still can't get in without that second factor.
Phishing prevention is another area where MFA shines. We've all heard stories about employees who accidentally clicked on a malicious link and entered their credentials on a fake website. With MFA in place, even if someone falls for a phishing scam, the attacker still hits a wall when they try to access the account.
The CISA guide on phishing-resistant MFA provides excellent insights into how advanced MFA methods can protect against even the most sophisticated phishing attempts. This type of protection is becoming essential as cybercriminals develop more convincing fake websites and emails.
Perhaps most importantly, MFA provides crucial data breach mitigation. When major companies experience breaches and millions of passwords are stolen, MFA ensures that those compromised credentials alone aren't enough to access your systems. It's like having a backup plan for your backup plan.
Ransomware protection is another critical benefit. Many ransomware attacks begin with compromised credentials. By blocking unauthorized access at the login stage, MFA can prevent these devastating attacks from ever taking hold in your network.
The statistics speak for themselves – implementing a second authentication factor reduces the risk of unauthorized access by an impressive 99%. For businesses in Columbus, Ohio and Charleston, WV, this level of protection isn't just nice to have – it's essential for staying competitive and maintaining customer trust in today's digital marketplace.
Think of online multi factor authentication as a security system that checks multiple forms of ID before letting someone into your digital accounts. Just like a high-security building might require both a keycard and a fingerprint scan, MFA requires different types of proof that you are who you claim to be.
These verification methods fall into three distinct categories, often called the "three pillars" of authentication. Each pillar represents a different way to prove your identity, and the real power of MFA comes from combining at least two of these pillars together.
To learn more about how these factors can be dynamically applied based on context and risk, check out our guide on Adaptive Multi-Factor Authentication.
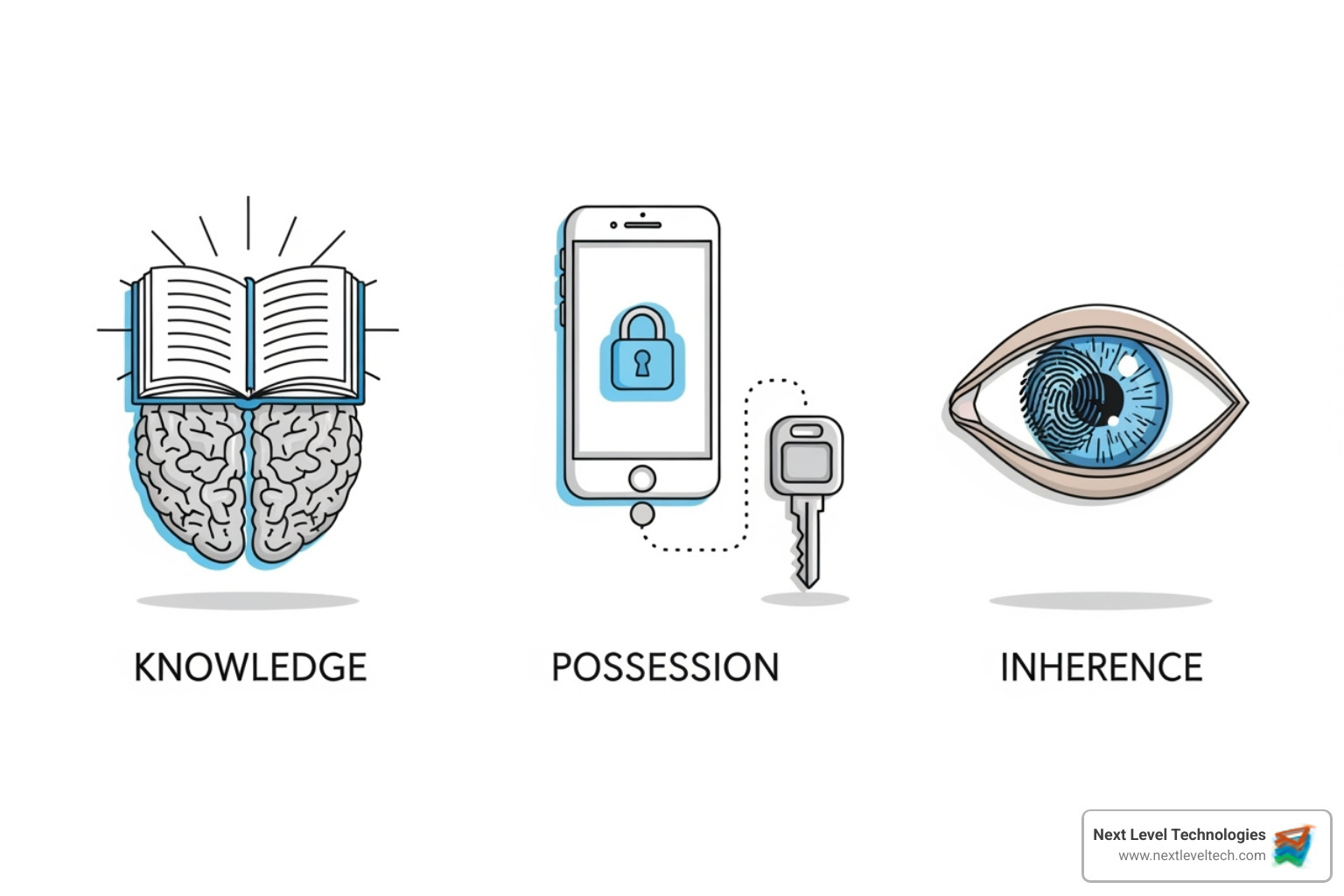
The three pillars of authentication work together to create a robust security framework:
Something you know is the most familiar authentication factor. This includes passwords, PINs, security questions, and passphrases. While these are easy to use and remember, they're also the most vulnerable to attacks. Passwords can be guessed, stolen in data breaches, or obtained through phishing scams. That's why our cybersecurity experts always recommend using strong, unique passwords (at least 12 characters or 4 words and 15 characters long) even when MFA is in place.
Something you have refers to physical items that only you should possess. Your smartphone is the most common example, whether it's receiving SMS codes or running authenticator apps. Hardware security keys like YubiKeys, smart cards, and USB tokens also fall into this category. These physical factors are generally more secure than passwords because an attacker would need to physically steal your device to use them.
Something you are involves your unique biological characteristics. Fingerprints, facial recognition, voice patterns, and retina scans are all examples of biometric authentication. While incredibly convenient and unique to each person, even biometrics aren't foolproof – sophisticated attackers can sometimes find ways to mimic or copy these biological markers.
The magic happens when you combine at least two of these different factors. For example, entering your password (something you know) and then providing a code from your phone app (something you have) creates a much stronger security barrier than either factor alone.
When we implement online multi factor authentication solutions for businesses across Columbus, Ohio and Charleston, WV, we carefully evaluate the security, convenience, and potential vulnerabilities of each method. Here's how the most common approaches stack up:
| MFA Method | Security | Convenience | Vulnerabilities |
|---|---|---|---|
| SMS Codes | Lowest - Vulnerable to SIM swapping, phishing, and network interception | Very High - Almost everyone has a mobile phone | Highly susceptible to SIM swapping attacks where attackers gain control of your phone number, and phishing where users are tricked into giving up the code |
| Authenticator Apps (TOTP) | Medium - More secure than SMS but still vulnerable to phishing and MFA fatigue | High - Requires smartphone app | Susceptible to phishing if users enter codes on fake sites, or MFA fatigue if users approve malicious requests after being bombarded with notifications |
| Hardware Security Keys (FIDO/WebAuthn) | Highest - Resistant to phishing, man-in-the-middle attacks, and SIM swapping | Medium - Requires carrying a physical device | Can be lost or stolen (though often protected by a PIN), and require remembering to carry the device |
SMS codes are the most widely used method because they're simple and accessible. However, they're also the least secure option. Attackers can use SIM swapping to take control of your phone number, or simply intercept the messages through various technical means.
Authenticator apps like Google Authenticator, Microsoft Authenticator, and Authy generate time-based codes directly on your device. They're much more secure than SMS because they don't rely on the cellular network. However, users can still fall victim to phishing attacks or "MFA fatigue" – where constant notification prompts lead people to eventually approve a malicious request just to make them stop. To combat this, CISA provides guidance on implementing number matching in MFA applications, a technique that requires users to enter a specific number to approve a login, making it much harder to approve malicious requests by accident.
Hardware security keys represent the gold standard for MFA security. These physical devices use strong cryptographic methods and are resistant to most common attacks. The authentication happens directly between the key and the service, making it nearly impossible for attackers to intercept or replay. For businesses handling sensitive data, we often recommend this approach despite the slight inconvenience.
Modern online multi factor authentication systems go beyond simple two-factor setups. Risk-based authentication analyzes factors like your location, device health, and the time of your access attempt to determine how much additional verification is needed.
For example, if you're logging in from your usual office computer in Columbus during business hours, the system might only require your password and a simple push notification. But if someone tries to access your account from an unusual location at 3 AM, the system might demand additional verification steps.
Geolocation tracking, device health monitoring, and user behavior analytics all contribute to this intelligent approach. These systems learn your normal patterns and flag anything suspicious. This fits perfectly with the Zero Trust security model, where every access request is verified regardless of where it comes from.
Conditional Access policies can also trigger different authentication requirements based on what someone is trying to access. Viewing basic company information might require minimal verification, while accessing financial systems or customer data demands the strongest possible authentication.
Our extensively trained cybersecurity staff has seen how these advanced systems can dramatically improve security without making life difficult for users. The key is finding the right balance between protection and practicality for your specific business needs.
Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
