Auditing IT from the Inside Out – A Beginner's Guide
July 16, 2025

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026

Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026

Protect your data. Learn how cloud backup services for business ensure recovery, continuity, and security for your enterprise.
March 3, 2026
July 16, 2025
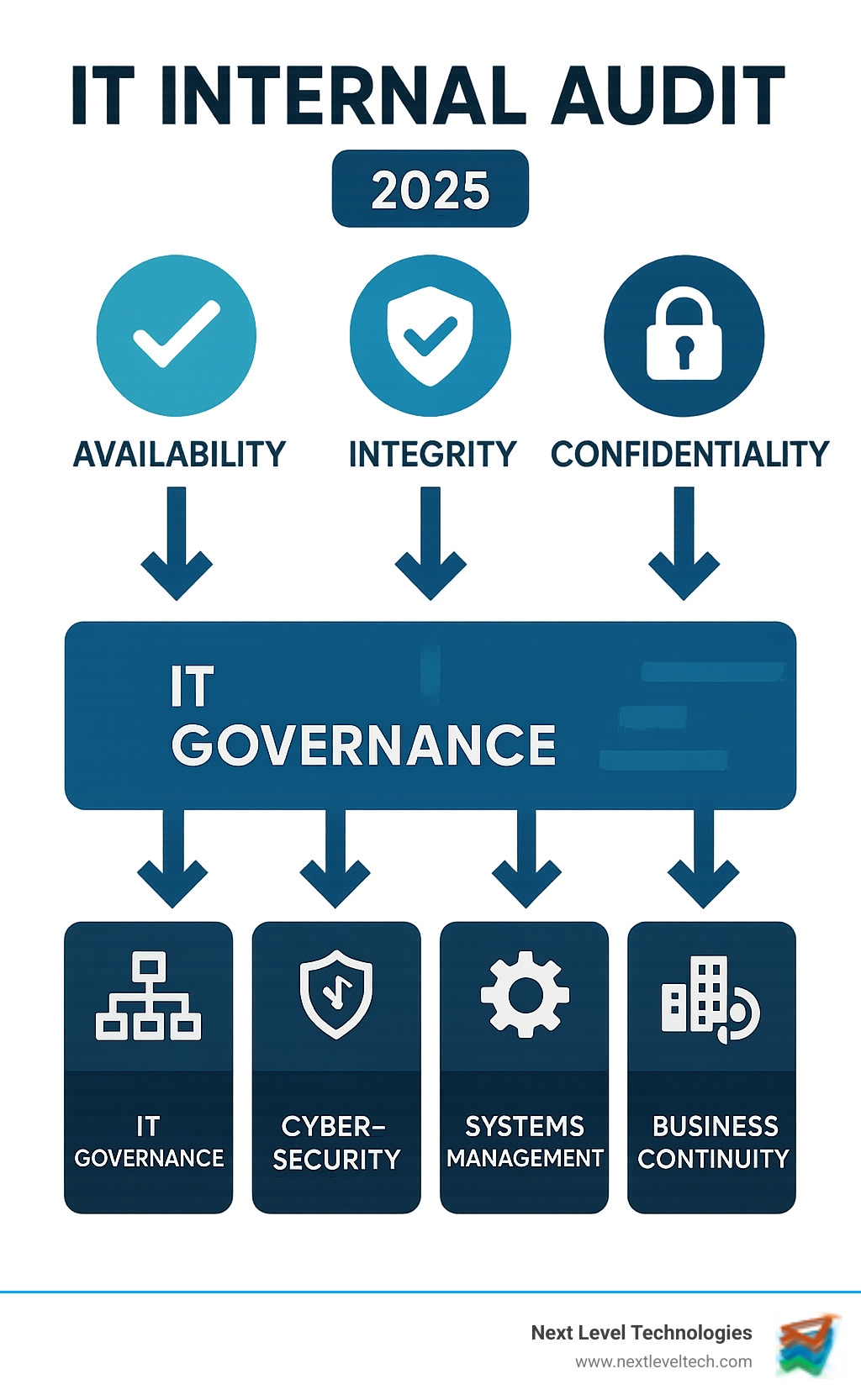
An IT internal audit is an independent, objective examination of your organization's technology infrastructure, policies, and procedures designed to improve operations and strengthen risk management. Unlike external audits performed by third parties for compliance purposes, IT internal audits are conducted by your organization (or trusted partners) to identify vulnerabilities, assess controls, and ensure your technology supports business objectives.
Key Components of IT Internal Audit:
The process systematically evaluates three critical aspects of your information systems: availability (systems work when users need them), integrity (data is accurate and reliable), and confidentiality (information is protected from unauthorized access). This comprehensive approach helps organizations avoid costly downtimes, data breaches, and regulatory penalties while maximizing their technology investments.
As Steve Payerle, President of Next Level Technologies, I've guided countless businesses through IT internal audit preparations and implementations since founding our company in 2009. My team's extensive cybersecurity training and technical expertise help organizations in Columbus, Ohio, and Charleston, WV, transform their IT audit processes from compliance burdens into strategic advantages.
A sudden systems crash can halt operations and put customer data at risk. An IT internal audit is not just a bureaucratic checkbox; it's a strategic shield protecting your most valuable assets. Since every business interaction relies on technology, protecting your IT infrastructure is essential for survival and growth.
An IT internal audit acts as an early warning system, protecting priceless assets like data, intellectual property, and operational continuity. With the rise of cloud computing and mobile devices, cyber threats have more entry points than ever. An audit systematically evaluates your IT infrastructure to spot vulnerabilities before they can be exploited, acting as a comprehensive health check for your technology.
Navigating complex regulations like the General Data Protection Regulation (GDPR) is another major challenge. An IT internal audit ensures your systems meet all necessary standards, helping you avoid devastating penalties, legal battles, and reputation damage. Our Cybersecurity Compliance Services are designed to help businesses stay compliant without getting buried in paperwork.
Beyond protection, an audit aligns technology with business goals, changing IT from a cost center into a growth engine. It ensures every system and process supports your strategic objectives. It also helps manage the complexity of third-party relationships with cloud services and software vendors, assessing external dependencies to ensure you aren't inheriting unnecessary risks.
The bottom line impact is significant. By identifying inefficiencies and underused technology, audits often uncover cost savings and performance improvements. A well-executed IT internal audit is a strategic foundation for building trust with customers and stakeholders, allowing you to grow your business with confidence.
An IT internal audit is a clear, organized process designed to provide valuable insights and strengthen your technology. It's a systematic way to evaluate what's working and what can be improved.
An IT internal audit is incredibly versatile. It dives deep into different parts of your technology to make sure everything is running smoothly and safely. Think of it like a detailed map, where each section represents a vital area we explore.
Generally, IT audits focus on two main types of controls: IT General Controls (ITGC) and IT Application Controls (ITAC). ITGCs are the big-picture rules that apply to your entire IT setup. This includes things like who can access your systems or how changes are made. ITACs, on the other hand, are specific to individual software applications. They make sure data is correct when you type it in, for example.
Here are the main areas our team at Next Level Technologies typically examines during an IT internal audit:
This section looks at how IT is run and organized within your company. We want to be sure it truly supports your business goals.
We check if your IT strategy aligns with your overall business objectives. Are your technology investments actually helping your company move forward? We also review your IT policies and procedures. Are they clear? Are they followed? This includes rules for acceptable use, how long you keep data, and security guidelines.
We look at your organizational structure for IT. This means checking roles and responsibilities. We want to see clear authority and proper segregation of duties. This helps prevent problems like conflicts of interest. We also assess if your staff has the right skills and training. Are they up-to-date on security? Our team's deep cybersecurity training shows just how important this area is! Finally, we review your IT budgeting to ensure resources are used wisely and give you the best value.
Because so many businesses work with outside IT companies, we also check your IT Vendor Risk Management Solutions. Are security rules in your contracts? Are you monitoring service agreements? Do vendors tell you about incidents that affect their other customers? These are all important questions.
This is often the most critical part of an audit. It focuses on keeping your systems and data safe from cyber threats.
We look closely at access controls. This means checking how user accounts are set up and if access levels match job roles. We make sure access is reviewed regularly and that strong password rules are in place. We also check if administrator activity is monitored. We verify if Multifactor Authentication Solutions are used, especially for remote access. This adds a vital extra layer of protection.
Our audit also covers network security. This includes checking your firewalls, intrusion detection systems, and secure virtual private networks (VPNs). We assess your vulnerability management and patch management programs. Are you regularly scanning for weaknesses? Are you updating your software and systems to fix known issues? For companies using cloud services, we look at Cloud IT Security. We make sure data is secure and compliant in the cloud.
We also examine physical security controls. This means checking things like locks, badge access, and even how your servers are cooled. We want to protect your hardware and data centers. And of course, we verify your anti-malware defenses, including antivirus software and gateway filters, to fight off malicious software.
This section focuses on the entire life of your IT systems and applications. It covers everything from how they are built to how they are maintained.
We assess if you have a structured Software Development Lifecycle (SDLC). This includes checking for secure coding practices and security testing for web applications. We also review your change management process. This ensures that any changes to IT systems are approved, tested, and documented. This helps prevent problems and risks.
We verify your IT Asset Inventory Management. Do you know all your hardware and software? Are unauthorized programs blocked? We also check data classification and protection. Is your data categorized? Is it encrypted when it's moving or stored? Are USB drives restricted? Is there a secure way to remove data from old storage devices? Finally, we make sure system performance monitoring is in place to keep everything running smoothly and spot any bottlenecks.
No one wants to think about a disaster, but being prepared is key to your business's survival. This area ensures your company can bounce back quickly from any major disruption.
We verify your backup and recovery procedures. Are your systems and data backed up regularly? Are these backups stored securely? Most importantly, are they tested to make sure they can actually be restored? We assess your IT Disaster Recovery Planning. Do you have a full plan to get IT operations back up after a big problem? Is it tested regularly?
We also check your Business Impact Analysis (BIA). Does your plan identify your most critical business functions? Do you know how quickly they need to be recovered? And we review your IT Security Incident Management plan. This ensures your organization can quickly find, respond to, and recover from security incidents. We even check if you're notified when your vendors have incidents.
By looking closely at all these areas, an IT internal audit gives you a complete picture of your IT environment. It highlights what you're doing well, where you can improve, and new opportunities.
The thought of an audit can sometimes feel like preparing for a pop quiz—unsettling! With the right proactive preparation, though, you can turn that nervous energy into confidence. A well-prepared IT internal audit isn't just smoother for everyone involved; it delivers better results for your business.
Getting ready for your IT internal audit doesn't have to be overwhelming. Many of the preparation steps will improve your day-to-day operations well before the auditors arrive.
Start with your IT asset inventory. Having a complete and accurate picture of all your hardware and software is foundational. This means knowing every server, workstation, network device, application, and license in your environment.
Next, review and update all your IT policies and procedures. Make sure your acceptable use policies, data retention guidelines, and incident response procedures are current and reflect how things really work. This alignment is crucial for IT Security Policy Compliance.
Conduct a self-assessment or gap analysis before the official audit begins. Identifying potential weaknesses in advance lets you address issues proactively rather than being surprised during the actual audit.
Communicate early and often. Notify all relevant internal departments and external partners about the upcoming audit, its purpose, and what information might be requested.
Gather documentation from previous audits if you've had them. These reports, findings, and evidence of remediation provide valuable context and show your commitment to continuous improvement.
Prepare your financial information related to IT expenditures, investments, and any reported losses due to IT incidents.
Finally, be prepared for the unexpected. Even with thorough preparation, audits sometimes uncover surprising findings. Approach them with an open mind; the goal is to identify and address areas for improvement.
Even well-intentioned organizations sometimes stumble during an IT internal audit. Learning from these common missteps can save time, stress, and money.
Poor risk assessment – Failing to identify and prioritize IT risks can cause the audit to miss critical areas. Conduct thorough, annual risk assessments that reflect your evolving threat landscape.
Inadequate scope – A scope that is too narrow may overlook significant vulnerabilities or compliance issues. Make sure the audit scope aligns with business objectives and regulatory requirements.
Communication breakdowns – Lack of clear dialogue between auditors and stakeholders leads to misunderstandings and delays. Foster open, continuous communication throughout the process.
Insufficient auditor skills – If the audit team lacks technical expertise in areas like cloud computing or AI, important details may be missed. Ensure your auditors maintain up-to-date certifications and cybersecurity training.
Treating the audit as a one-time event – An audit should feed an ongoing improvement process. Accept a continuous-improvement mindset and integrate recommendations into regular operations.
Failure to follow up on findings – Generating a report is only the beginning. Establish accountability for remediation and verify that issues are fully resolved.
By being proactive, communicating openly, and embracing continuous improvement, you can transform your IT internal audit into a powerful tool for strengthening your organization.

Technology evolves at break-neck speed, and the IT internal audit professional has evolved with it. Instead of acting solely as technical compliance checkers buried in server logs, today’s IT auditors serve as strategic advisors, ensuring that technology risks are understood in the context of business objectives.
Emerging tools such as Artificial Intelligence, Machine Learning, IoT, and multi-cloud deployments introduce complex risks that traditional methods can miss. Audit teams must therefore understand these technologies from both a technical and business-risk perspective. The Institute of Internal Auditors (IIA) notes that new technologies raise the likelihood of security breaches and data misuse.
To stay effective, modern IT auditors need a blend of skills:
Professional bodies such as The Institute of Internal Auditors (IIA) and ISACA’s CISA certification help auditors maintain the latest knowledge. At Next Level Technologies, our Columbus, OH, and Charleston, WV teams invest heavily in ongoing cybersecurity training to keep clients ahead of the curve.
The future of IT internal audit is proactive and deeply integrated into business operations—helping organizations not only comply with regulations but also harness technology safely for lasting success.
It's completely natural to have questions about something as vital as an IT internal audit! We hear a lot of common inquiries, and we're always happy to shed some light. Here are some of the questions we get asked most often, along with our straightforward answers:
Ah, the classic "how long is a piece of string?" question! The truth is, the timeline for an IT internal audit can vary quite a bit. It's not a one-size-fits-all situation, and several factors play a big role:
First, consider the scope of the audit. Are we diving deep into just one specific area, like your access controls, or are we taking a comprehensive look at your entire IT universe? A focused review will naturally be quicker than a full-scale assessment.
Then there's the complexity of your systems. An organization with many different, interconnected, or older systems might require more time to steer and understand than one with a simpler setup. And, of course, the size of your organization matters. A small business with a straightforward IT environment will likely have a much shorter audit than a large enterprise with thousands of users and intricate networks.
Finally, your team's preparedness can make a huge difference. If your policies, procedures, and documentation are well-organized and easy to access, the audit process tends to flow much more smoothly and quickly. Generally speaking, an IT internal audit could take anywhere from a few weeks for a targeted review to several months for a very extensive, enterprise-wide assessment. We always work closely with you during the planning phase to set clear, realistic timelines.
This is a fantastic question, and it highlights two very different, but equally important, aspects of IT security! Think of it like this: they're both crucial for protecting your digital assets, but they approach the task from different angles.
An IT audit (or IT internal audit) is like a thorough health check of your entire IT system. It's a broad, systematic review designed to evaluate how well your IT controls, policies, and procedures are working. We're looking at things like: "Are your security policies robust enough?" "Are employees following the rules we've set?" "Are your backup systems actually ready if disaster strikes?" The main goal here is to assess your governance, risk management, and compliance. An IT internal audit tells you if your defenses are designed correctly and if they're being followed.
A penetration test, on the other hand, is like a simulated, targeted attack. Imagine a team of ethical hackers trying to break into your systems, just like a real cybercriminal would. Their goal is to find actual technical vulnerabilities that could be exploited. They'll ask questions like: "Can we bypass your firewall?" "Is there a weakness in this web application that lets us sneak in?" "Can we get to your sensitive data?" A pen test focuses on exploitable weaknesses and tells you if your defenses can be bypassed by a determined attacker.
While they're distinct activities, they're wonderfully complementary. An IT internal audit might reveal a need for a penetration test in a particular high-risk area, and the findings from a pen test can directly inform the scope of future IT internal audit efforts. Together, they form a powerful duo in a robust cybersecurity strategy.
Absolutely, 100%! While you often hear about large corporations needing IT internal audits due to regulations, a small business can gain immense, sometimes even greater, benefits from one. In fact, because small businesses often operate with leaner IT teams and rely so heavily on technology, an IT internal audit can be even more crucial.
Here's why it's a game-changer for smaller organizations:
First, it's about protecting your valuable data. Small businesses are unfortunately not immune to cyber threats. An IT internal audit helps you shield your customer data, financial records, and intellectual property from costly breaches.
Second, it ensures operational resilience. Imagine your systems going down unexpectedly. For a small business, downtime can be catastrophic. An audit helps make sure your systems are reliable and that you have solid plans in place to recover quickly from any disruptions.
Beyond protection, there's cost-effectiveness. By identifying inefficiencies or redundant systems, an audit can actually lead to significant cost savings in the long run. Plus, it helps ensure you're getting the most out of your existing IT investments.
Even small businesses have compliance requirements, whether it's related to data privacy or specific industry standards. An IT internal audit helps you understand and meet these obligations, keeping you out of hot water.
The beauty of it all is that an IT internal audit is highly scalable. You don't need a massive, overwhelming audit. A focused review on your most critical IT areas can provide incredible value and lay a strong foundation for secure and efficient IT operations. For more on navigating these waters, you might find our guide, Explaining IT Compliance Beginners Guide For Small Business Success, really helpful.
Phew! We've journeyed through the intricate, yet incredibly vital, world of the IT internal audit. We've seen how it's not just about ticking boxes, but about proactively safeguarding your precious data, ensuring you stay compliant with changing regulations, and making sure your technology truly supports your big-picture business goals. It's clear that an IT internal audit isn't just a chore; it's a critical, value-adding activity that makes your organization stronger from the inside out.
In today's digital landscape, where your IT systems are the very heartbeat of your operations, a proactive and thorough approach to IT auditing is absolutely essential. It's your secret weapon for resilience, your guide to efficiency, and a powerful way to maintain the trust of everyone who interacts with your business. It helps you anticipate potential risks before they become real problems, fine-tune your operations for peak performance, and ultimately, helps you thrive.
For businesses in Columbus, Ohio, or Charleston, WV, needing that expert hand to guide them through preparing their IT environment for audits, or to help implement those robust controls we've talked about, the team at Next Level Technologies is here for you. Our staff brings a wealth of deep technical experience and has undergone extensive cybersecurity training, meaning we're not just familiar with the challenges, we're equipped to solve them. We're particularly passionate about assisting organizations, including those in industries that are often overlooked, in navigating the complexities of IT risk and compliance. We don't just point out where things could be better; we partner with you to build lasting, effective solutions.
Ready to secure your digital future and truly strengthen your IT posture? Let's work together. Explore our comprehensive Managed IT Services And IT Support to see how we can help your business reach its Next Level.
Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
