The Unbreakable Core: A Deep Dive into IT Infrastructure Security
August 15, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
August 15, 2025
IT infrastructure and security form the foundation that keeps your business running. IT infrastructure includes all technology components your business relies on—servers, networks, software, and data centers—while IT security protects these assets from cyber threats and ensures business continuity.
Key components include hardware, software, networks, security layers like firewalls and encryption, and data protection measures like backups and disaster recovery.
The stakes are high. IT downtime can cost businesses up to $9,000 per minute, and cybercrime has surged dramatically. A significant number of infrastructure vulnerabilities remain unresolved, leaving businesses exposed to known attacks.
"It only takes a moment — a less-than-secure password, a single click on the wrong website — and your company's security can be compromised."
This makes a secure IT foundation critical for survival.
I'm Steve Payerle, President of Next Level Technologies. For over 15 years, I've helped businesses in Columbus, Ohio, and Charleston, WV, build robust IT infrastructure and security systems. My experience has shown me how the right approach can transform an organization's ability to compete and thrive.
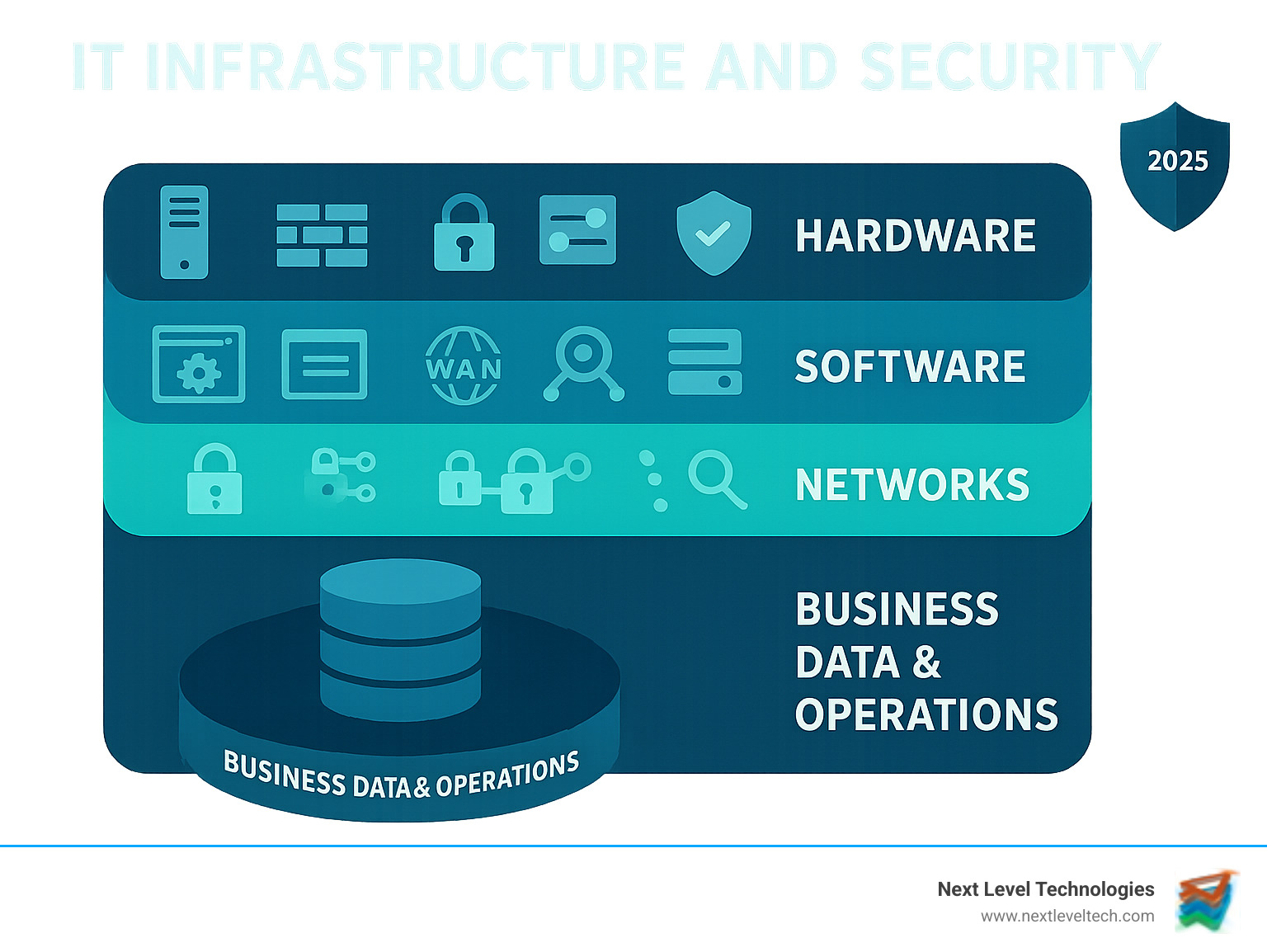
Common it infrastructure and security vocab:
Think of your IT infrastructure and security as the essential systems that keep a city running. It's the intricate web of technology components working together behind the scenes, including the physical equipment, the software that runs it, and the networks that connect everything.

These three pillars—hardware, software, and networks—are interdependent. Powerful hardware is useless without an operating system, and the best software falls flat without a network to connect users to their tools.
Hardware is the physical foundation of your IT infrastructure and security. These are the machines that store data and connect you to the digital world.
If hardware is the body, software is the brain. It transforms metal and silicon into tools that revolutionize your business.
Expert software deployment and management ensures all these components work together securely and efficiently.
Your network is the most critical component of your IT infrastructure and security, enabling collaboration and information sharing.
Our optimized network solutions for business ensure your data flows smoothly and securely, no matter where your team is working.
Imagine arriving at your office to find your systems down, your network compromised, and your business at a standstill. This nightmare scenario happens daily. In today's digital-first environment, robust IT infrastructure and security is the difference between thriving and barely surviving.
Your IT foundation is the invisible engine powering your business. When it runs smoothly, it's unnoticed. When it fails, everything stops. That's why professional IT services are essential—they keep your digital foundation solid while you focus on your core business.
The financial impact of inadequate IT infrastructure and security can be devastating. Consider these costs:

The question isn't whether you can afford to invest in proper IT infrastructure—it's whether you can afford not to.
Investing in strong IT infrastructure and security delivers returns that go far beyond disaster avoidance. It becomes a competitive advantage that drives growth.
At Next Level Technologies, our staff in Columbus and Charleston brings deep technical experience to help businesses realize these advantages. We've seen how adapting to modern IT needs transforms organizations. Robust IT infrastructure and security isn't an expense—it's an investment in your future.
The digital world has an underground economy working around the clock to exploit any weakness. Your IT infrastructure and security face constant, evolving threats from every direction.
Recent research shows a significant increase in unauthorized access incidents, often involving third parties. The threat landscape is growing more interconnected and unpredictable. At Next Level Technologies, our cybersecurity-trained staff in Columbus and Charleston constantly updates our defensive strategies to stay ahead of these emerging threats.
Threats from outside your organization are sophisticated and relentless.
Our team continuously monitors recent industry data and threat reports to keep clients protected.
Sometimes the biggest threats come from within, often unintentionally.
Government and industry advisories regularly highlight these supply chain risks.
Attacks on critical infrastructure—energy grids, financial systems, healthcare networks—affect entire communities.
Securing IT infrastructure and security is about protecting individual businesses and maintaining the stability of our entire digital ecosystem. Our experienced team in Columbus, Ohio, and Charleston, WV, helps businesses implement security that contributes to overall community resilience.
Protecting your IT infrastructure and security requires a multi-layered strategy, much like a medieval fortress with moats, walls, and guards. This approach, known as defense-in-depth, is the gold standard for cybersecurity. Industry best practices, such as those outlined in the NIST Cybersecurity Framework, reinforce why layering controls is essential for reducing risk.
No single security measure is perfect. By layering multiple controls, you create a fortress that is incredibly difficult to breach. At Next Level Technologies, our team's extensive cybersecurity training informs our approach, combining proactive measures with comprehensive risk assessment for businesses in Columbus, Ohio, and Charleston, WV.

Our consulting expertise helps businesses design these comprehensive strategies, ensuring every layer works together seamlessly.
| Feature | On-Premise (Traditional) Infrastructure | Cloud Infrastructure (e.g., AWS, Azure, Google Cloud) |
|---|---|---|
| Responsibility | You handle everything: physical security, hardware, networking, operating systems, applications, and data. | Shared Responsibility Model: Cloud provider secures the infrastructure; you secure your data, applications, and configurations. |
| Physical Security | You manage data centers, server rooms, and access control. | Cloud provider handles robust data center security. |
| Hardware Management | You buy, maintain, and upgrade all hardware. | Cloud provider manages the underlying hardware. |
| Network Security | You configure firewalls, network segmentation, and monitoring systems. | You configure virtual networks and security groups using cloud tools. |
| Patch Management | You patch everything – operating systems and applications. | Cloud provider patches infrastructure; you patch your applications. |
| Data Control | You have complete control over where data is stored. | Data lives in cloud provider facilities; location may vary. |
With cloud infrastructure, configuration management is critical. Many breaches occur due to misconfigured settings, not a failure of the cloud provider. While providers offer security of the cloud, securing your data in the cloud is your responsibility.
Your most sophisticated IT infrastructure and security system can be defeated by one employee clicking the wrong link. Your people are either your strongest defense or your weakest link.
Our team in Columbus, Ohio, and Charleston, WV, leverages its extensive cybersecurity training to not only implement technical solutions but also to train your employees, turning your workforce into a strong "human firewall."
Building a secure system requires the right tools. Here are the essentials:
At Next Level Technologies, our security solutions integrate these tools into a comprehensive defense system that we configure, monitor, and continuously optimize.
Your IT infrastructure and security requires constant care, like a garden. The digital landscape changes daily, with new threats and evolving regulations. Building a secure foundation is just the beginning; maintaining it requires continuous vigilance.
Cyber threats don't keep business hours, so your security can't either. Continuous monitoring is your 24/7 digital security guard.
This is why expert support is essential. Our team at Next Level Technologies provides 24/7 monitoring, leveraging our extensive cybersecurity training to act on issues before they impact your business.
Compliance isn't just paperwork; it's about following best practices that protect data and build customer trust. Ignoring industry regulations can lead to heavy fines and reputational damage.
Our team's technical experience and cybersecurity training in Columbus, Ohio, and Charleston, WV, allows us to provide comprehensive compliance support, navigating these complex standards to protect your business.
Even the best security can't prevent every disaster. A solid disaster recovery and business continuity plan is essential for survival.
A well-tested plan turns a potential catastrophe into a manageable setback.
Building an unbreakable IT infrastructure and security foundation is a strategic investment in your business's future. It's about understanding that your digital backbone is the heartbeat of everything you do.
We've explored the critical components, the high cost of failure, and the multi-layered strategies needed for effective protection. The reality is that cyber threats are relentless, but with the right approach and partnership, you can build a robust defense that adapts to whatever comes next.
This is where the technical expertise and extensive cybersecurity training of our team at Next Level Technologies makes the difference. Our staff in Columbus, Ohio, and Charleston, WV, doesn't just implement solutions—we understand them inside and out. We've seen how the right strategy transforms businesses.
You didn't start your business to become a cybersecurity expert. By partnering with a team of highly trained experts, you can ensure your digital core remains unbreakable, allowing you to focus on what you do best: growing your business.
Your IT infrastructure and security should empower your dreams, not cause sleepless nights. Let us handle the complexities, so you can focus on achievement.
Managed IT Services and IT Support from Next Level Technologies
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
