Assessing IT Compliance: Steps to Ensure Your Organization's Success
May 16, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
May 16, 2025
IT compliance assessments are systematic evaluations of how well your organization's IT systems and practices align with relevant regulations, standards, and internal policies. They help identify gaps in your compliance posture and provide actionable steps for remediation.
Quick Answer: What is an IT Compliance Assessment?
An IT compliance assessment is a structured review that:* Evaluates your adherence to regulatory requirements (HIPAA, GDPR, PCI-DSS, etc.)* Identifies security gaps and vulnerabilities in your IT systems* Verifies that controls are properly implemented and effective* Provides a roadmap for remediation and continuous improvement* Helps avoid penalties and protect your organization's reputation
In today's interconnected business landscape, IT compliance assessments have become essential rather than optional. With 98% of organizations worldwide connected to vendors that experienced breaches in the last two years, compliance failures can result in significant regulatory fines (up to 10 million Euros for GDPR violations), operational disruptions, and lasting reputational damage.
Many compliance teams feel stuck in a cycle of repetitive assessments that yield few meaningful benefits. This frustration often stems from treating compliance as a checkbox exercise rather than an opportunity to strengthen your security posture and business operations.
Regular assessments are particularly crucial as organizations adopt new technologies, expand operations, and face increasingly sophisticated cyber threats. The most common barrier to compliance success is manual processes, according to Clausematch's 2023 State of Compliance Technology report. This highlights the need for a more strategic, automated approach.
I'm Steve Payerle, President of Next Level Technologies, and I've guided numerous businesses through IT compliance assessments that transform regulatory obligations into strategic advantages, leveraging our team's extensive cybersecurity training and expertise across our Columbus, Ohio and Charleston, WV locations.

An IT compliance assessment is like a health checkup for your organization's technology systems. It's a thorough evaluation that shows how well your IT infrastructure, processes, and practices align with laws, industry standards, and your own internal policies. But these assessments are far more than technical box-ticking exercises – they're vital governance activities that help your business stay on the right side of regulations.
A recent Deloitte report highlighted something we see all the time: "Many organizations underestimate the complexity of linking compliance risk to enterprise-wide objectives." This gets to the heart of the matter – compliance isn't just about avoiding trouble; it's about creating real business value.
The consequences of non-compliance can be severe:
But here's the good news – when done right, IT compliance assessments deliver real benefits beyond just keeping you out of trouble. They improve your security posture by identifying vulnerabilities before they become problems. They often streamline operations as you refine processes to meet requirements. They can even give you a competitive edge, as more customers and partners look for businesses that take compliance seriously.
I've seen how strong compliance programs build investor and stakeholder confidence. At Next Level Technologies, we help businesses in Columbus, Ohio and Charleston, WV develop a culture of continuous compliance readiness rather than last-minute panic when audits loom.
Leadership commitment makes all the difference. When executives demonstrate that compliance matters, that attitude flows throughout the organization. Our team emphasizes this cultural aspect in all our client engagements.
Equally important is making sure your team understands why compliance matters. Research from the National Institute of Standards and Technology (NIST) confirms what we've always known – organizations with stronger compliance maturity invest significantly in staff education and awareness.
When our cybersecurity experts conduct IT compliance assessments, we focus on four critical objectives:
First, we ensure regulatory alignment – confirming your systems and processes meet all applicable laws and industry standards, whether that's HIPAA for healthcare organizations or PCI DSS for businesses that handle payment data.
Next comes control validation – because having policies on paper isn't enough. We verify that your security controls actually work as intended in real-world conditions.
We also focus on gap detection, identifying areas where your current measures don't quite meet requirements or best practices. These gaps represent potential risks to your business.
Finally, we help with risk prioritization because not all compliance issues are created equal. Our assessments help you understand which gaps pose the greatest risk, so you can tackle the most important issues first with your limited resources.
One healthcare client told us something that stuck with me: "Before working with Next Level Technologies, we viewed compliance as a necessary evil. Now we see how our IT compliance assessments actually improve our patient care by ensuring data integrity and availability."
It's easy to confuse IT compliance assessments with risk assessments and internal audits, but they serve different purposes:
IT compliance assessments look specifically at how well you meet regulatory and contractual requirements. They evaluate your systems against specific external standards and typically align with regulatory deadlines or happen annually.
Risk assessments cast a wider net, examining broader business and operational risks. They identify potential threats to your business objectives and often happen quarterly or when significant changes occur.
Internal audits focus on testing how well your internal controls are designed and whether they're operating effectively. These usually follow a schedule set by your audit committee.
While there's some overlap, IT compliance assessments specifically examine your systems through a regulatory lens. They're more narrowly focused than enterprise risk assessments, which consider all potential business threats.
The most mature organizations find ways to integrate these activities using a common control framework. Our team at Next Level Technologies, with our extensive cybersecurity training and experience across Ohio and West Virginia, specializes in helping businesses create this kind of integrated approach that maximizes efficiency while ensuring comprehensive coverage.
Creating a structured approach to IT compliance assessments isn't just about checking boxes—it's about building a sustainable program that protects your business. At Next Level Technologies, we've developed and refined a practical seven-step framework based on real-world experience with businesses throughout Columbus, Ohio and Charleston, WV.

Every effective IT compliance assessment starts with proper scoping. This foundational step prevents you from wasting resources or leaving dangerous gaps in your compliance coverage.
When we work with clients, we begin by clearly identifying which systems need assessment—your critical applications, databases, and infrastructure components that handle sensitive information. We then determine what types of data you're processing, whether that's personal information, healthcare records, or payment details, as each comes with its own regulatory requirements.
Geographic considerations matter tremendously in today's global environment. A business operating in both Ohio and California faces different requirements than one solely based in West Virginia. Similarly, different departments within your organization may fall under different regulatory frameworks.
"I see so many businesses either trying to boil the ocean by assessing everything, or dangerously underscoping their compliance efforts," shares our compliance director. "Finding that sweet spot takes experience and regulatory knowledge."
For deeper insights into which requirements affect your specific industry, check out our guide on understanding IT compliance requirements for different industries.
Once you know what you're assessing and against which standards, it's time to identify where your risks actually lie. This isn't about theoretical problems—it's about understanding what could realistically impact your business.
Our cybersecurity experts work with you to model potential threats to your compliance posture. We pay special attention to your vendor relationships, since nearly all organizations (98%) connect with vendors that have experienced breaches in recent years.
We believe in combining qualitative and quantitative approaches to risk scoring. While simple High/Medium/Low ratings work well for initial assessments and smaller organizations, numerical scoring provides the precision needed for mature programs, especially in heavily regulated industries.
A manufacturing client in Columbus once told me, "When we put actual dollar figures on our compliance risks, suddenly our executive team started taking cybersecurity much more seriously." That's the power of proper risk quantification.
The control mapping phase is where IT compliance assessments start delivering real value. Here, we document everything you already have in place—your policies, technical safeguards, and administrative procedures—and map them to specific compliance requirements.
This mapping process often reveals something exciting: many controls satisfy multiple compliance requirements simultaneously. For example, a strong password policy might check boxes for HIPAA, PCI DSS, and your cyber insurance requirements all at once.
"The lightbulb moment for many of our clients comes when they realize they're already doing much of what's required—they just haven't documented it properly," notes our lead security consultant with over 15 years of cybersecurity training.
For more on creating effective security policies, see our comprehensive guide on IT Security Policy Compliance.
With preparation complete, it's time for the hands-on assessment work. Our team brings extensive cybersecurity training to this process, ensuring we uncover issues that automated tools might miss.
We conduct thorough stakeholder interviews with system owners and users to understand how things actually work in practice. Document reviews help us verify that policies match reality. Technical testing, vulnerability scanning, and in some cases penetration testing verify that your security controls actually work as intended.
"Tools are fantastic for efficiency, but there's no substitute for experienced human judgment," explains our senior security analyst. "Our team members in both Columbus and Charleston bring local knowledge along with technical expertise to every assessment."
This combination of automated and manual assessment provides the most complete picture of your compliance posture.
Finding gaps is only valuable if you have a practical plan to address them. Our approach to remediation planning is both comprehensive and realistic.
We categorize gaps based on risk level and implementation difficulty. Some fixes might be simple configuration changes that dramatically reduce risk—these "quick wins" go to the top of the list. Others might require longer-term projects with significant investment.
For each gap, we help you identify a clear owner, establish realistic timelines, and determine required resources. This isn't about creating an overwhelming to-do list; it's about building a manageable roadmap that steadily improves your compliance posture.
"Breaking remediation into manageable phases keeps teams from getting overwhelmed," shares our project manager. "We've found this approach leads to much higher completion rates for our clients in both Ohio and West Virginia."
Clear communication can make or break your compliance program. That's why we put special emphasis on creating reports that speak to different audiences within your organization.
For executives, we provide high-level summaries that connect compliance gaps to business risks and opportunities. For technical teams, we offer detailed findings with specific remediation steps. And for audit purposes, we help you maintain a comprehensive evidence repository that proves your compliance efforts.
Visual dashboards have proven particularly effective for our clients. These provide at-a-glance understanding of your compliance status across different requirements, helping everyone from the board to IT staff understand where you stand.
"The best compliance report I've ever seen actually led to increased IT budget approval," recalls a client from Charleston. "It was so clear and compelling that our leadership immediately understood the business case."
IT compliance assessments shouldn't be annual fire drills. The most successful organizations accept continuous monitoring and regular reassessment.
We help clients implement automated monitoring tools that verify control effectiveness year-round. We establish compliance KPIs so you can measure progress over time. And we set up alerts for compliance drift that notify you when controls fail or degrade.
"Compliance isn't a destination—it's an ongoing journey," explains our director of managed services. "The threat landscape and regulatory environment are constantly evolving, and your compliance program needs to evolve with them."
Our team's extensive cybersecurity training allows us to help you stay ahead of emerging requirements and threats. For more on building a sustainable monitoring program, see our detailed guide on IT Compliance Monitoring.
Navigating the maze of compliance requirements can feel overwhelming. As we help clients across Columbus, Ohio and Charleston, WV, we've found that understanding which regulations apply to your specific situation is the first critical step in any successful IT compliance assessment.

Let's break down the major frameworks you might need to address:
If your business interacts with EU citizens' data, GDPR should be on your radar. This comprehensive privacy regulation focuses on protecting personal data with stringent requirements around data subject rights, breach notification, and privacy by design. The stakes are high—violations can cost up to €20 million or 4% of global annual revenue. One client told us, "We had no idea our small Ohio business would be subject to European regulations until Next Level's assessment identified our international customer base."
Healthcare organizations or their business associates handling protected health information (PHI) must comply with HIPAA's Privacy Rule, Security Rule, and Breach Notification Rule. With penalties reaching $1.5 million per violation category annually, our cybersecurity experts often find that proper technical safeguards are in place while administrative controls need strengthening.
This internationally recognized standard provides a systematic approach to information security management. Rather than prescribing specific technologies, ISO 27001 focuses on risk assessment, security controls, and management review processes. Organizations seeking global recognition of their security practices often pursue certification, which requires passing a formal audit.
If you're providing services to other businesses, your customers may require SOC 2 compliance. This framework evaluates your controls related to security, availability, processing integrity, confidentiality, and privacy. SOC 2 reports come in two flavors: Type I (assessing design effectiveness at a point in time) and Type II (evaluating operational effectiveness over a period, usually 6-12 months).
"Credit card processing is the compliance requirement most businesses encounter first," notes our payment systems specialist. PCI DSS includes 12 requirements covering network security, data protection, and vulnerability management. Any organization that processes, stores, or transmits credit card data must comply, with requirements varying based on transaction volume.
Developed by the National Institute of Standards and Technology, this flexible, risk-based approach works for organizations of all sizes. The framework is organized around five key functions: Identify, Protect, Detect, Respond, and Recover. Our team with extensive cybersecurity training particularly appreciates NIST CSF's adaptability for businesses at different security maturity levels.
Defense contractors and subcontractors must meet CMMC requirements to work with the Department of Defense. The model has three progressive levels of cybersecurity maturity, with increasing requirements at each stage. For manufacturing clients in Ohio and West Virginia working in the defense sector, early preparation for CMMC assessment is crucial.
Financial institutions operating in New York must comply with these cybersecurity regulations, which require a formal risk assessment, cybersecurity program, and appointment of a Chief Information Security Officer. Even if your main operations are in Columbus or Charleston, these requirements may apply if you serve New York customers.
"The biggest mistake we see is businesses trying to boil the ocean," explains our compliance lead. "Not every framework applies to every organization. Part of our value is helping you focus on what truly matters for your specific situation."
The secret to efficient IT compliance assessments is understanding how different requirements overlap. By developing a unified control framework, you can dramatically reduce duplication of effort:
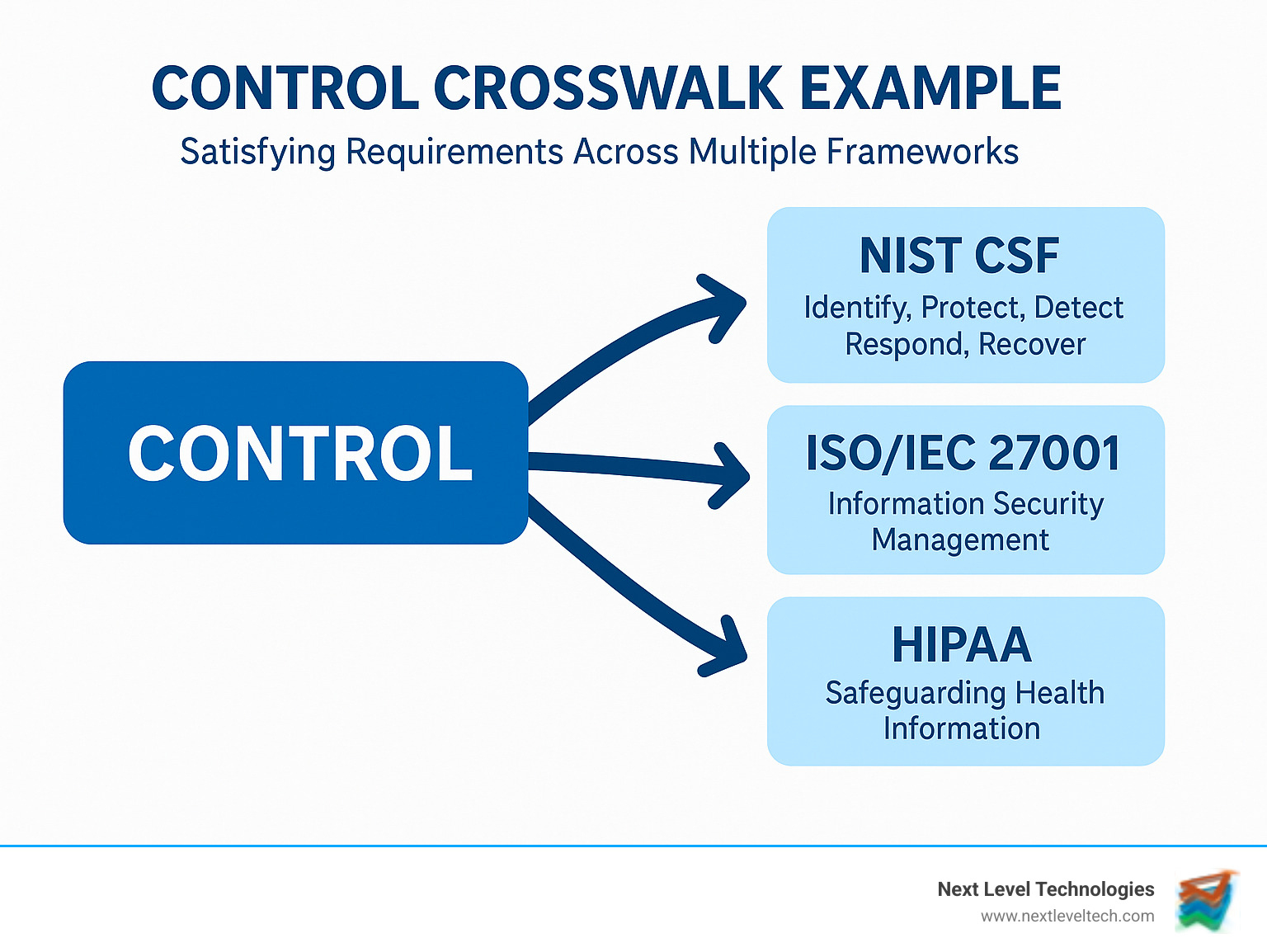
Creating a common control library lets you implement controls once while satisfying multiple frameworks. When you map controls to requirements, you can clearly see how each security measure addresses different regulatory obligations. This "implement once, comply many" approach not only saves time but ensures consistency across your compliance program.
Centralizing evidence collection in one repository further streamlines the process. As one banking client remarked, "Before working with Next Level Technologies, we were gathering the same evidence three different ways for three different audits. Now we do it once and map it everywhere it's needed."
Your security is only as strong as your weakest vendor—a sobering thought considering that 98% of organizations are connected to vendors that experienced breaches in the last two years. In 2022 alone, 63 attacks on vendors caused 298 third-party data breaches across companies.
"I like to remind clients that compliance doesn't stop at your company's borders," says our risk management specialist. "Your assessments must include your entire business ecosystem."
Effective vendor management starts with a comprehensive vendor inventory that catalogs all third parties with access to your systems or data. Once identified, apply risk-based classification to focus attention where it's most needed—vendors handling sensitive data require more scrutiny than those providing non-critical services.
Conduct thorough due diligence before engagement, include specific contractual requirements around security and compliance, and implement ongoing monitoring to ensure vendors maintain appropriate security postures over time.
One healthcare client in Charleston shared, "We were shocked to find our billing company wasn't HIPAA compliant. Next Level's vendor assessment process identified this critical gap before it became a reportable breach."
By taking a comprehensive approach to regulatory compliance that includes your vendors, you create a stronger security posture that protects your business, your customers, and your reputation.
Let me share something that might sound familiar: hours spent hunting down documents, endless email chains requesting evidence, and spreadsheets so complex they need their own user manual. Sound like your compliance process? You're not alone.
The most common barrier to compliance success is manual processes, according to Clausematch's 2023 State of Compliance Technology report. The good news? Automation isn't just possible—it's changing how forward-thinking organizations approach IT compliance assessments.

"With the right technology, you can run a full risk assessment in less than 30 days," explains our technology specialist at Next Level Technologies. "That's a dramatic improvement over traditional manual approaches that might take months and leave your team exhausted."
Modern tools that can breathe new life into your compliance program include GRC platforms that centralize your compliance activities in one place, AI-powered risk scoring that helps you focus on what matters most, and automated evidence collection that gathers documentation without endless follow-ups. Many of our clients have found particular value in real-time compliance dashboards that give executives instant visibility into compliance status and predictive analytics that help identify potential issues before they become problems.
At Next Level Technologies, we pride ourselves on staying ahead of these technological curves. Our team's extensive cybersecurity training enables us to implement these solutions effectively for clients across Columbus, Ohio and Charleston, WV. We've found that the blend of technological expertise in Columbus combined with the practical, relationship-focused approach common in Charleston creates a perfect balance for our clients.
When it comes to specific tools for IT compliance assessments, it's not just about buying software—it's about finding the right fit for your organization's unique needs.
Control mapping tools have been game-changers for many of our clients, especially those dealing with multiple regulatory frameworks. One healthcare client in Columbus told us, "We used to spend weeks mapping controls across HIPAA, SOC 2, and NIST. Now it's largely automated, and we can focus on actual improvements instead of documentation."
Workflow engines help automate the tedious parts of compliance—task assignments, approvals, and follow-ups. Document management systems ensure you never have to hunt for evidence again, while assessment automation tools streamline the evaluation process itself. For organizations with complex tech environments, connector libraries with pre-built integrations can save countless hours of custom development work.
"The right tools don't just make compliance faster—they make it more accurate and comprehensive," one of our solutions architects often reminds clients. "Manual processes inevitably lead to gaps and inconsistencies that create risk."
Despite all these technological advances, we still see organizations struggling with their IT compliance assessments. The challenges are often surprisingly similar regardless of company size or industry.
Manual processes continue to dominate many compliance programs, with critical information trapped in spreadsheets and shared drives. Regulatory change management remains difficult as requirements evolve faster than ever. Most organizations face resource constraints with limited budget and expertise for compliance activities. We frequently encounter siloed approaches where different departments handle compliance separately, creating duplication and gaps. Perhaps most challenging is building a true compliance culture where security and compliance become everyone's responsibility.
One manufacturing client in Charleston put it perfectly: "We had all the right tools, but they weren't making a difference because our team saw compliance as something separate from their 'real job'."
To overcome these challenges, we recommend investing in training programs that build compliance knowledge throughout your organization. Start with high-risk areas rather than trying to perfect everything at once. Document lessons learned from each assessment cycle to avoid repeating mistakes. Develop a maturity roadmap that shows how your compliance program will evolve over time. And don't forget to celebrate successes—compliance wins deserve recognition!
"Compliance isn't just about technology—it's about people and processes," our training coordinator often emphasizes. "The most successful programs balance all three elements."
Our team at Next Level Technologies brings this balanced approach to clients across Columbus and Charleston, combining our extensive cybersecurity training with practical, human-centered implementation strategies. We've found that the right mix of technology and expertise can transform compliance from a burden into a business advantage.
For more strategies on overcoming compliance challenges, check out our guide on Top Strategies IT Service Providers Use to Guarantee Your Data Privacy and Compliance.
Navigating the complex world of regulatory compliance doesn't have to be overwhelming. Effective IT compliance assessments aren't just checkboxes on a to-do list—they're powerful tools that protect your business while creating genuine competitive advantages.
Throughout this guide, we've walked through a practical framework that transforms compliance from a necessary burden into a strategic asset. The journey might seem daunting at first, but each step builds upon the last, creating a comprehensive approach that grows with your business.
Compliance isn't a one-time project with a finish line. It's an ongoing journey that evolves as regulations change, new threats emerge, and your business expands. The most successful organizations accept this reality, building flexible compliance programs that adapt through continuous assessment and improvement.
At Next Level Technologies, we understand these challenges intimately. Our team brings extensive cybersecurity training and real-world experience to organizations across Columbus, Ohio, Charleston, WV, and surrounding areas. We've helped businesses of all sizes develop compliance programs that not only satisfy regulatory requirements but actually strengthen their overall security posture and business operations.
"Compliance shouldn't just be about avoiding penalties," our lead compliance specialist often says. "It should be about building trust with your customers and partners while protecting what matters most to your business."
Whether you're taking your first steps toward formal compliance or looking to improve an established program, we're ready to help. Our approach combines technical expertise with practical business sense, ensuring your compliance efforts align with your broader strategic goals.
Don't wait for a compliance failure or data breach to prioritize this critical aspect of your business. The costs—both financial and reputational—are simply too high. Instead, take proactive steps today to build a compliance program that grows with your business and provides lasting peace of mind.
Learn more about how our Managed IT Services and IT Support can strengthen your compliance posture while supporting your broader business objectives. With Next Level Technologies as your partner, you'll gain not just a service provider but a trusted advisor committed to your long-term success.
Contact us today to discuss how our team in Columbus and Charleston can help you transform compliance challenges into business opportunities. After all, in today's digital landscape, strong compliance isn't just about avoiding problems—it's about building a foundation for sustainable growth.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
