Demystifying Network Hardware: The Building Blocks of Digital Communication
August 14, 2025

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026

Master your small business server setup with our comprehensive guide. Learn planning, installation, security, and maintenance for SMBs.
February 17, 2026
August 14, 2025
Computer hardware networking forms the invisible foundation that powers every digital interaction in your business. When you send an email, access cloud files, or process online payments, specialized physical devices work behind the scenes to make it all possible.
What is computer hardware networking?
Think of network hardware as the digital highways of your business. Just like roads need bridges, traffic lights, and maintenance crews to function properly, your network needs routers to direct traffic, switches to connect devices, and firewalls to maintain security.
The stakes are higher than many business owners realize. Research shows that hardware failures cause 38% of network downtime, with each minute of outage costing businesses an average of $5,600. For mid-sized companies already struggling with outdated technology and frequent system disruptions, understanding these building blocks becomes critical for operational stability.
I'm Steve Payerle, President of Next Level Technologies, and I've spent over a decade helping businesses in Columbus, Ohio and Charleston, WV build resilient computer hardware networking infrastructures. Through extensive cybersecurity training and hands-on experience with hundreds of network deployments, I've seen how the right hardware foundation can transform struggling IT operations into competitive advantages.
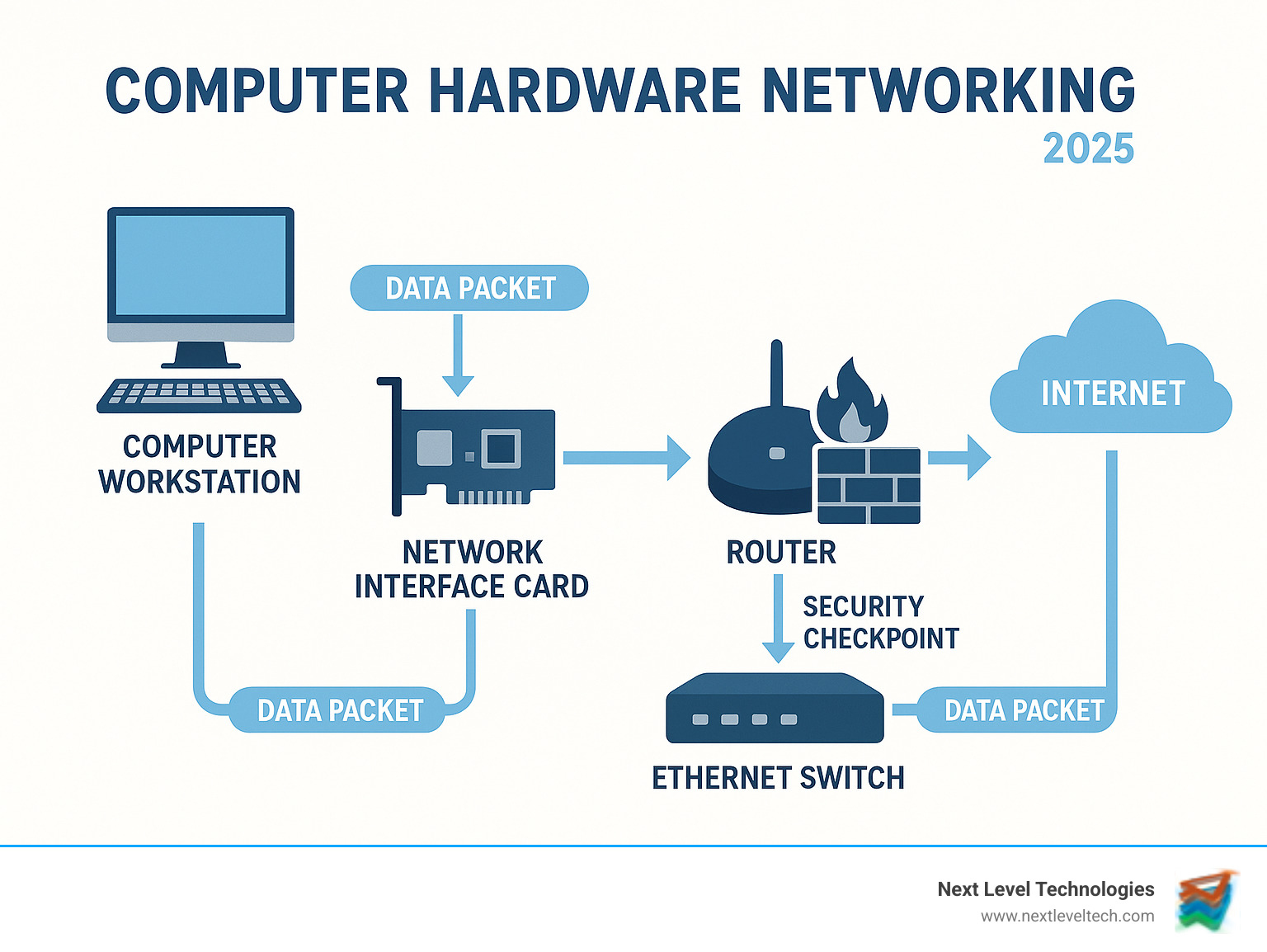
Learn more about computer hardware networking:
Picture this: you're trying to send an important file to a colleague across the office. Your computer has all the processing power it needs, but without the right network connection, that file isn't going anywhere. This perfectly illustrates why computer hardware networking brings together two essential but distinct elements that work hand-in-hand.

Let's start with computer hardware – the physical parts you can actually touch and see. Think of your computer's CPU as the brain, making all the decisions and calculations. The memory (RAM) acts like your desk workspace, holding information you're currently using. Storage devices like hard drives and SSDs are your filing cabinets, keeping everything safe for later. Then you have all the input and output devices – keyboards, mice, monitors – that let you interact with the system.
Without these tangible components, a computer is just an expensive paperweight.
Networking is the magic that connects everything together. It's all about information exchange and resource sharing between different devices. When your accounting team accesses files from the server, or when you check email from your phone, that's networking in action. The whole purpose is to break down the walls between individual computers and create a collaborative digital environment.
Here's where it gets interesting: computer hardware networking combines these two worlds. Your server (hardware) needs to talk to workstations (more hardware) through switches and routers (networking hardware). It's like having a conversation – you need both people and a way for them to communicate.
Through our extensive cybersecurity training and years of hands-on experience in Columbus and Charleston, we've seen how businesses struggle when they don't understand this relationship. The hardware might be powerful, but without proper networking, it's like having a sports car stuck in your garage.
Computer Hardware, Software, and Networking
While hardware and networking serve different purposes, they're more alike than you might think. Understanding both their differences and similarities helps you make smarter decisions for your business.
| Feature | Computer Hardware | Networking |
|---|---|---|
| Primary Purpose | Process data and run applications | Enable communication and resource sharing |
| Key Features | Processing speed, memory, storage capacity | Connection speed, scalability, security protocols |
| Maintenance Focus | Hardware updates, component replacement | Configuration, monitoring, troubleshooting |
| Performance Impact | Determines individual device capabilities | Affects how well devices work together |
The biggest difference? Hardware focuses inward – how fast can this computer process information, how much can it store, how reliable are its components. Networking focuses outward – how well can multiple devices share information, access resources, and stay connected.
But here's what they share: both require careful planning and ongoing maintenance. You can't just buy the fastest processor and expect it to work perfectly with an outdated network setup. Similarly, the most advanced networking equipment won't help if your computers can't keep up.
Both also have a direct impact on your business productivity. A failing hard drive can shut down one workstation, but a misconfigured router can bring down your entire office. They're truly interdependent – each relying on the other for optimal performance.
This is why our team emphasizes the importance of viewing computer hardware networking as a complete system, not separate pieces. When we design IT infrastructure for businesses in Ohio and West Virginia, we consider how every component works together to create a reliable, secure, and efficient network that grows with your business needs.
Think of computer hardware networking like the circulatory system of your business. Just as your body needs arteries, veins, and a heart to move blood efficiently, your network needs specific hardware components to move data where it needs to go. Each device has a specialized job, and when they work together properly, your business operations flow seamlessly.

These are the workhorses that get your devices talking to each other in the first place. Without them, you'd have a bunch of very expensive paperweights sitting on your desks.
Every device in your network starts with a Network Interface Card (NIC). This circuit board or chip is like a translator that allows your computer to speak "network language." Whether it's the Ethernet port on your desktop or the wireless adapter in your laptop, the NIC is what connects your device to the network. Its speed directly impacts how fast your data moves, so a slow NIC can bottleneck even the fastest network.
Switches are the traffic managers of your local network. Unlike the old-fashioned hubs that basically shouted everything to everyone (imagine trying to have a private conversation in a crowded restaurant), switches are smart. They learn which devices are connected to which ports and send data only where it needs to go. This creates dedicated pathways for each conversation, dramatically improving network efficiency.
When your network signals start getting weak over long distances, repeaters step in like digital megaphones. They amplify and refresh the signal, extending your network's reach beyond normal cable limitations. This is especially important in larger buildings where you need reliable connections across multiple floors.
Your modem is your gateway to the outside world. It translates the digital language your computers speak into the format your internet service provider understands, whether that's through cable lines, phone lines, or fiber optic cables. Think of it as your network's passport to the internet.
Wireless Access Points (WAPs) bring freedom to your network by creating Wi-Fi zones. They're essentially radio stations that let your mobile devices, laptops, and tablets connect without being tethered to cables. In our experience working with businesses across Columbus, Ohio and Charleston, WV, properly positioned access points can transform how teams collaborate.
Physical Components of Computer Network
Once your devices can connect, you need traffic controllers to make sure data gets to the right destination efficiently. These devices are like the air traffic controllers of your digital world.
Routers are perhaps the most critical components in modern networking. They connect different networks together (like linking your office network to the internet) and make intelligent decisions about the best path for each piece of data. Every data packet that travels between networks goes through a router that checks its destination and forwards it along the most efficient route. Without routers, the internet simply couldn't exist.
Bridges serve as connectors between different network segments, helping to reduce traffic congestion by filtering what crosses between them. They're particularly useful when you have older network equipment that needs to communicate with newer systems, or when you want to segment a large network into smaller, more manageable pieces.
Gateways act as translators between different types of networks or protocols. While people often use the term interchangeably with routers, gateways have a broader role – they can convert data formats and protocols, allowing networks that "speak different languages" to communicate effectively.
Moving data efficiently is only half the battle. You also need hardware dedicated to protecting your network and keeping it running smoothly, especially given the cybersecurity challenges we see daily in our managed IT services work.
Firewalls are your network's security guards. These devices (or sometimes software) create a protective barrier between your trusted internal network and the wild west of the internet. They examine every piece of data trying to enter or leave your network, blocking anything that doesn't meet your security rules. Given our extensive cybersecurity training, we've seen how proper firewall configuration can prevent devastating security breaches.
Proxy servers work as intermediaries, handling requests between your devices and external servers. They can hide your internal network structure from outside observers, cache frequently accessed content for faster loading, and filter out unwanted websites or content.
When your business grows and network traffic increases, load balancers become essential. These devices distribute incoming requests across multiple servers, preventing any single server from becoming overwhelmed. It's like having multiple checkout lines at a grocery store instead of forcing everyone through one register.
Content filters help maintain productivity and security by blocking access to inappropriate or dangerous websites. They're often built into firewalls or proxy servers, and they're particularly valuable for businesses that need to enforce acceptable use policies or protect against malware-laden websites.
IT Infrastructure for Small Business
Your computer hardware networking infrastructure isn't just about getting devices connected – it's the foundation that determines whether your business runs smoothly or struggles with constant slowdowns and security threats.
Picture this: you're trying to run a marathon in flip-flops. That's essentially what happens when you ask modern business applications to perform on outdated network hardware. The results are predictably frustrating.
The numbers tell a sobering story. Hardware failures cause 38% of network downtime, and each minute your network is down costs an average of $5,600. I've seen businesses in Columbus, Ohio lose thousands of dollars in a single afternoon because an aging switch finally gave up during a critical client presentation.
But hardware doesn't have to fail completely to hurt your business. Latency – those annoying delays when clicking a link or opening a file – often stems from overworked routers that can't handle your current data demands. Throughput issues create bottlenecks where information crawls through your network like rush hour traffic on a two-lane highway.
The reality is that network hardware has a lifecycle of 3-5 years. Beyond that point, devices become unreliable, energy-hungry, and unable to support the speeds your business needs. Our cybersecurity-trained team regularly helps Charleston, WV businesses avoid costly surprises by planning hardware refreshes before problems strike.
Think of it this way: you wouldn't run a delivery business with trucks from the 1990s. Your network deserves the same consideration.
Computer Hardware Problems and Solutions
Here's a statistic that should keep every business owner awake at night: 90% of businesses experienced a cyberattack in the past year. The good news? Properly configured network hardware forms your first and most critical line of defense.

A robust hardware firewall acts like a security guard at your building's entrance, examining every piece of data before it enters your network. Unlike software firewalls that run on individual computers, dedicated hardware firewalls provide enterprise-level protection that can't be disabled by malware or user error.
But here's where many businesses stumble: they buy great security hardware and then leave it with default passwords and open ports. It's like installing a high-tech security system and leaving the front door wide open. Every router, switch, and access point needs secure configuration and regular firmware updates to eliminate vulnerabilities that cybercriminals actively exploit.
Endpoint security becomes much more manageable when your network hardware supports centralized policy enforcement. This means you can ensure every device that connects to your network meets your security standards, whether it's a company laptop or a visitor's smartphone.
Our extensive cybersecurity training has shown us that hardware-based security isn't just about blocking bad guys – it's about creating a foundation where your other security tools can work effectively. When your network hardware is properly secured, you're not just protecting data; you're protecting your business's reputation and your customers' trust.
IT Support for Small Businesses
Even with the best computer hardware networking infrastructure in place, managing it effectively requires understanding common pitfalls and implementing proven strategies. Through our extensive technical experience serving businesses in Columbus, Ohio and Charleston, WV, we've seen how proactive management can transform network reliability.
Network hardware management presents unique challenges that can catch even experienced IT teams off guard. Malfunctioning devices top our list of frequent support calls – from power supply failures in critical servers to switch ports that suddenly stop working. These hardware failures often happen at the worst possible times, creating urgent situations that demand immediate attention.
Temperature issues and ventilation problems create silent threats to your network infrastructure. We regularly visit client sites where server rooms lack proper cooling or equipment cabinets are clogged with dust. Overheating doesn't just slow performance; it dramatically shortens hardware lifespan and can cause sudden, catastrophic failures.
Power-related challenges compound these problems. Power supply fluctuations can damage sensitive networking equipment, while battery degradation in uninterruptible power supplies (UPS) leaves networks vulnerable during outages. Many businesses find their backup power has failed only when they need it most.
Capacity overutilization represents another common challenge. As businesses grow, they often push aging hardware beyond its limits. Imagine trying to force highway traffic through a single-lane road – that's what happens when modern data demands meet outdated network infrastructure.
Even seemingly simple issues like DNS configuration problems and physical connectivity failures can paralyze operations. A loose cable or misconfigured router setting might seem minor, but these problems create frustrating intermittent disruptions that are surprisingly difficult to diagnose without proper expertise.
Successful computer hardware networking management starts with proactive monitoring and deeper visibility into your infrastructure. Rather than waiting for equipment to fail, smart businesses implement 24/7 monitoring tools that spot performance anomalies before they become major outages. Our team's extensive cybersecurity training helps us identify security-related hardware issues that many monitoring systems miss.
Regular maintenance schedules form the backbone of reliable network operations. This includes physical cleaning of equipment, systematic cable integrity checks, and maintaining proper environmental conditions for temperature and humidity. IT asset management provides the foundation for these efforts – maintaining detailed inventories of all hardware including purchase dates, warranty information, and configuration details.
Automation of routine tasks frees your team to focus on strategic initiatives rather than repetitive troubleshooting. Automated systems can handle basic diagnostics and maintenance tasks, ensuring consistent care for your network infrastructure.
Multi-vendor support agreements simplify management for businesses with diverse hardware ecosystems. Instead of juggling multiple support contracts, unified support streamlines troubleshooting and maintenance across different manufacturers.
Understanding hardware dependencies and processes prevents cascading failures when individual components experience problems. Our technical team maps these relationships for clients, creating clear documentation that guides rapid problem resolution.
When specific issues arise, proven troubleshooting approaches make the difference. Cable connectivity problems often require systematic testing and immediate replacement of faulty components. Port failures on switches or routers can be quickly resolved by reconfiguring connections to available ports. Traffic overload situations need careful analysis using network monitoring tools to identify bottlenecks and plan appropriate upgrades. Routing problems require verification that protocols and device configurations allow seamless data packet movement across your network.
For businesses in Columbus, OH and Charleston, WV, partnering with experienced professionals ensures your network infrastructure remains resilient, secure, and optimized for your specific business needs. Our team's extensive technical background and proactive management approach helps prevent problems before they impact your operations.
The Importance of IT Asset Management in Columbus Ohio
The world of computer hardware networking offers some of the most exciting and stable career opportunities in today's technology landscape. As businesses become increasingly dependent on digital infrastructure, the demand for skilled professionals who understand both the physical and logical aspects of networking continues to grow.
At Next Level Technologies, we've witnessed how rewarding careers in this field can be. Our team members in both Columbus, Ohio and Charleston, WV have built successful paths by combining technical expertise with continuous learning and hands-on experience.
The beauty of computer hardware networking is that it opens doors to diverse career paths, each with its own unique challenges and rewards.
Network Administrator roles form the backbone of most IT departments. These professionals handle the day-to-day operations of network infrastructure, installing and configuring routers and switches, maintaining network security, and troubleshooting connectivity issues. It's a role that requires both technical knowledge and problem-solving skills, as you'll often be the first person called when something goes wrong.
Network Engineer positions take a more strategic approach to infrastructure. Engineers design complex network architectures, plan capacity upgrades, and implement advanced routing and switching solutions. This role often involves working with cutting-edge technology and requires deep understanding of network protocols and hardware capabilities.
The growing importance of cybersecurity has made Security Analyst roles increasingly vital. These professionals focus on protecting network infrastructure from threats, implementing firewall policies, monitoring for vulnerabilities, and responding to security incidents. Our staff's extensive cybersecurity training reflects how critical these skills have become in today's threat landscape.
IT Support Technician roles provide an excellent entry point into the field. Support technicians help users with hardware and software issues, including basic network connectivity problems. It's a role that builds strong foundational knowledge while developing customer service skills.
Systems Administrator positions often blend network management with server administration. These professionals ensure the overall health of IT infrastructure, managing everything from network hardware to operating systems and applications.
For experienced professionals, IT Consultant roles offer the opportunity to work with multiple businesses, providing expertise on network design, hardware selection, and infrastructure optimization. It's a path that rewards deep technical knowledge with variety and independence.
Building a successful career in computer hardware networking requires a thoughtful combination of formal education, industry certifications, and practical experience.

Formal education provides the theoretical foundation that supports practical skills. Many colleges and universities offer programs in Computer Systems and Networking, Information Technology, or Computer Science. These programs typically include hands-on lab work that mirrors real-world scenarios, giving students experience with actual network hardware before entering the workforce.
Industry certifications carry significant weight with employers because they validate specific, job-ready skills. Cisco certifications like CCNA and CCNP are globally recognized and highly valued, particularly since Cisco hardware powers much of the world's network infrastructure. The Cisco Networking Academy (NetAcad) offers structured learning paths that emphasize hands-on laboratory experience alongside theoretical knowledge.
CompTIA certifications provide vendor-neutral foundational knowledge that applies across different hardware brands and technologies. The A+ certification covers computer hardware fundamentals, Network+ focuses on networking concepts, and Security+ addresses cybersecurity basics. These certifications are excellent starting points for entry-level professionals.
Hands-on experience remains irreplaceable in this field. There's simply no substitute for actually configuring a router, troubleshooting a network outage, or setting up a server. Many educational programs emphasize practical labs, and creating a home lab environment can provide valuable learning opportunities outside of formal coursework.
Continuous learning is perhaps the most important aspect of a networking career. Technology evolves rapidly, new security threats emerge regularly, and hardware capabilities constantly improve. Successful professionals commit to staying current with industry trends, new technologies, and evolving best practices.
The networking field rewards those who combine technical expertise with problem-solving abilities and communication skills. Whether you're starting your career or looking to advance, the foundation of computer hardware networking knowledge opens doors to a stable, well-compensated, and intellectually rewarding professional path.
Introduction to Networking course
As we wrap up our journey through computer hardware networking, it's clear that these components are so much more than just gadgets sitting in a server room. They're the digital foundation that keeps your business humming along, connecting your team, protecting your data, and enabling everything from simple email exchanges to complex cloud operations.
Think about it: every time you send a file to a colleague, process a customer payment, or access your business applications, you're relying on this intricate web of routers, switches, firewalls, and other hardware working in perfect harmony. It's like a well-orchestrated symphony where each instrument has a crucial part to play.
The foundation of digital communication starts with understanding that hardware failures cause significant disruptions and costly downtime. But with proactive management and the right expertise, these challenges become manageable. We've seen how proper configuration, regular maintenance, and strategic planning can transform a struggling network into a competitive advantage.
Security remains paramount in today's threat landscape. The hardware-based protections we've discussed – from firewalls blocking malicious traffic to properly configured routers preventing unauthorized access – form the bedrock of any solid cybersecurity strategy. Our team's extensive cybersecurity training has shown us time and again that businesses with robust hardware security foundations are far better positioned to weather the storm of modern cyber threats.
For businesses in Columbus, Ohio and Charleston, WV, building this resilient infrastructure doesn't have to be a solo journey. At Next Level Technologies, we've spent years helping companies just like yours steer these complexities. Our technical experience spans everything from small office networks to complex multi-location infrastructures, and we understand that every business – regardless of industry – deserves reliable, secure computer hardware networking.
Whether you're dealing with aging equipment that's slowing down your operations, planning a network upgrade, or simply want the peace of mind that comes with expert monitoring and support, we're here to help you reach that next level of IT excellence.
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
