Protecting Your Perimeter: Endpoint Security for Remote Workers
October 16, 2025

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026

Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026

Protect your data. Learn how cloud backup services for business ensure recovery, continuity, and security for your enterprise.
March 3, 2026
October 16, 2025
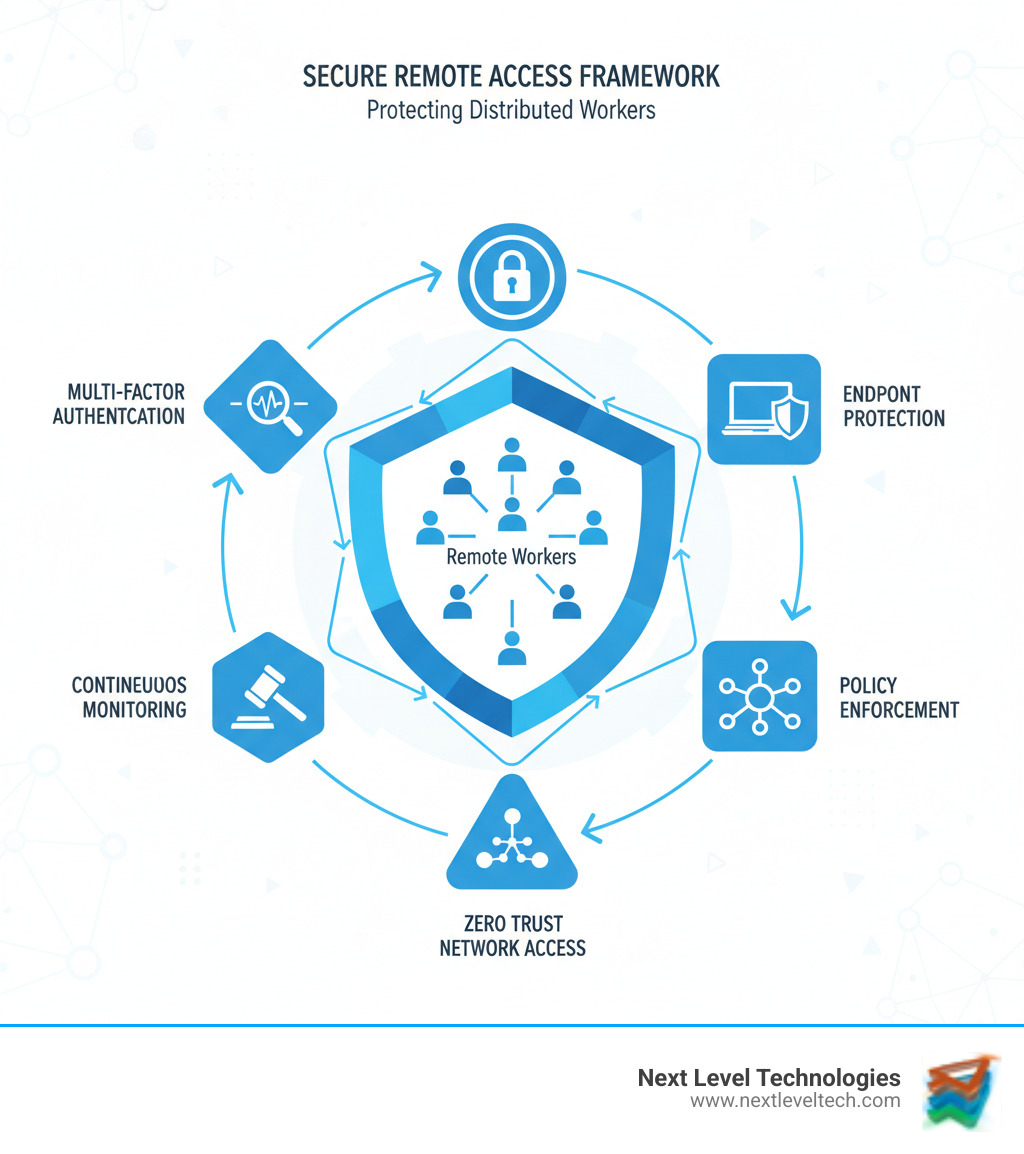
Secure remote access enables employees to connect safely to company resources from any location while maintaining enterprise-level security controls. With 77% of remote employees reporting higher productivity when working from home, businesses must balance flexibility with protection against an expanded attack surface.
Key Components of Secure Remote Access:
The shift to remote work is permanent, with 98% of workers wanting to continue remotely at least part-time. This flexibility shatters traditional security models that assumed a secure office perimeter, which no longer exists.
The numbers are stark: 36% of organizations have faced security incidents from unsecured remote workers. With cybercriminals sending 14.5 billion phishing emails daily, and over 90% of incidents tracing back to human error, the average successful attack costs a business $1.6 million.
The problem isn't remote work; it's outdated security. Traditional VPNs, designed for office-based work, grant broad network access, creating huge risks if a device or account is compromised.
I'm Steve Payerle, President of Next Level Technologies, and over the past 15 years, I've helped hundreds of businesses across Columbus, Ohio, and Charleston, West Virginia, implement secure remote access solutions that protect their data without sacrificing productivity. My team's extensive cybersecurity training has shown us that the most effective approach combines multiple security layers with Zero Trust principles.

The cybersecurity landscape has shifted dramatically with the rise of remote work. In my experience helping businesses across Columbus and Charleston implement secure remote access solutions, I've witnessed how quickly the threat environment has evolved.
The challenge is that traditional security boundaries have dissolved. Instead of protecting one office, we now must secure hundreds of home offices, coffee shops, and mobile hotspots.
Unauthorized access is easier for criminals who steal credentials. With valid logins, they can enter your systems undetected, looking like any other remote employee.
Data breaches often follow. A single phishing attack costs an average of $1.6 million, and with 14.5 billion sent daily, the risk is high. These attacks are sophisticated, often mimicking trusted sources.
Malware infections spread faster in remote settings. Personal devices often lack office-level security, and an employee's home network with smart TVs and gaming consoles can provide entry points for attackers.
More than 90% of incidents trace back to human error, often due to inadequate support. In fact, 20% of remote workers reported their IT teams provided zero guidance on security when they started working from home.
Traditional VPNs create their own problems. They grant broad network access, giving a user a key to the entire digital building. This creates significant lateral movement risk: if an attacker compromises one VPN connection, they can move across your entire network.
Through our extensive cybersecurity training and real-world experience, we've learned that the old "castle-and-moat" security model simply doesn't work when your employees are scattered across different locations. The perimeter isn't your office building anymore—it's wherever your people and their devices are. This is why businesses need to rethink their approach to secure remote access, moving beyond simple VPNs toward comprehensive, identity-focused security strategies. For more insights, check out our guide on 5 Common Cybersecurity Threats to Small Businesses and How Managed IT Services Can Help.
Effective secure remote access is like home security. You don't rely on a single lock; you use deadbolts, a security system, and cameras. This same layered thinking, or defense-in-depth, applies to protecting your business network. At Next Level Technologies, our team's extensive cybersecurity training has shown that successful strategies combine several key components working together seamlessly. The foundation is policy enforcement: clear, actively enforced rules about who can access what, when, and how.
Your employees' devices are the new front door to your business, and each one is a potential entry point for attackers.
Device hardening is the bedrock. It involves configuring devices for maximum security from the start by disabling unnecessary services and locking down operating systems.
Full-disk encryption is non-negotiable. If a device is lost or stolen, encryption renders the data unreadable, preventing a devastating breach.
While up-to-date antivirus is important, modern threats require Endpoint Detection and Response (EDR). EDR continuously monitors for suspicious behavior, detecting sophisticated attacks that basic antivirus misses. It's like a 24/7 digital security guard.
Patch management is critical. Cybercriminals hunt for vulnerabilities in outdated software, so we ensure all systems and applications are patched promptly.
Securing BYOD versus corporate devices requires different approaches. We have full control over company devices. For personal devices (BYOD), we use mobile device management and clear policies to enforce security standards before granting access. Our Advanced Threat Protection Solutions article explores these measures in detail.
Passwords alone are not enough; they can be stolen or cracked. Multi-Factor Authentication (MFA) is the solution. MFA requires two or more credentials to prove identity. Even if an attacker steals a password, they can't get in without the second factor, like a code sent to a phone.
This simple, effective method dramatically reduces unauthorized access. After a password, a user might use a code from a text, a push notification, or a fingerprint to verify their identity. Many compliance frameworks like HIPAA and PCI-DSS now require MFA. The technology is user-friendly and familiar to most people from personal banking or social media. For businesses looking to implement MFA, cloud-based solutions offer the easiest deployment path.
Security isn't 'set it and forget it.' Continuous monitoring and management are essential for long-term protection.
Access logs and anomaly detection help spot problems early. We track who accesses what and when, using automated systems to flag unusual patterns—like logins from a new country at 3 AM—for immediate investigation.
Real-time monitoring provides constant network visibility. Our cybersecurity-trained team can spot and respond to suspicious activity, often stopping attacks before they cause damage.
Privileged Access Management (PAM) secures high-value accounts like those of administrators. We use just-in-time access, session recording, and extra oversight to protect these prime targets.
Incident response planning is crucial because incidents can still happen. A clear, tested plan for containment, elimination, and recovery can mean the difference between a minor issue and a disaster, as our experience with IT Security Incident Management shows.

Traditional network security is like a medieval castle: once you're past the outer walls, you can roam freely inside. This outdated approach is no longer enough.
Zero Trust flips this model, operating on the principle of "never trust, always verify" (see NIST SP 800-207 Zero Trust Architecture). Every user, device, and connection must continuously prove it is trustworthy to gain access.
This shift isn't just theoretical. Our team at Next Level Technologies has seen how this approach transforms security for businesses across Columbus, Ohio, and Charleston, West Virginia. With our extensive cybersecurity training, we've helped dozens of companies move beyond the outdated "castle-and-moat" mentality.
Zero Trust Network Access (ZTNA) makes this practical for secure remote access. Unlike VPNs that grant broad access, ZTNA provides granular access, giving users entry only to specific applications they need, after meeting security requirements.
The principle of least-privilege access is simple: only grant access to what is necessary. This ensures that if an attacker compromises a user's credentials, they cannot explore your entire infrastructure.
Micro-segmentation complements this by creating separate, locked zones for each application. This limits lateral movement risk, a major flaw in traditional VPNs.
Crucially, ZTNA creates a reduced attack surface. Applications become invisible to unauthorized users, hiding them from attackers.
The numbers speak for themselves: more than 80% of surveyed companies plan to implement a zero trust model. This isn't just a trend - it's the future of cybersecurity. For businesses looking to modernize their security approach, our guide on Cloud Security Best Practices provides additional insights into implementing these frameworks effectively.
Understanding the practical differences between ZTNA and traditional VPNs helps clarify why this shift matters so much for your business:
| Feature | Traditional VPNs | Zero Trust Network Access (ZTNA) |
|---|---|---|
| Security Model | "Trust, but verify" (once inside, mostly trusted) | "Never trust, always verify" (continuous verification) |
| Access Level | Broad network access (like a key to the whole building) | Granular, application-specific access (key to one specific room) |
| Attack Surface | Large (entire network exposed if VPN is breached) | Small (only specific applications are exposed to the user) |
| User Experience | Often clunky, requires client software, can be slow | Seamless, often clientless or lightweight agent, faster |
| Scalability | Can be challenging, requires VPN concentrators | Highly scalable, cloud-native architecture |
| Visibility | Limited visibility into post-connection activity | Detailed, real-time visibility into user-to-application flow |
ZTNA not only improves security but also the user experience, providing faster access for remote workers and greater visibility for IT teams.
Technology alone isn't enough. The most sophisticated secure remote access systems can fail due to human error, which is why a strong cybersecurity culture is as important as the right tools. Our people are both our strongest defense and our greatest vulnerability.

A sobering 20% of workers received no IT guidance when shifting to remote work. We can't expect employees to make good security decisions without proper training.
Phishing awareness training is a top priority. With the average attack costing $1.6 million, it's not optional. Regular training should teach employees to spot red flags like poor grammar, urgent language, and mismatched links.
Strong password policies are a cornerstone of security. Encourage using password managers to create and store complex, unique passwords for every account, eliminating weak password risks.
For public Wi-Fi safety, education is key. Train employees to avoid sensitive work on unsecured networks. The Secure Remote Access guide from the FTC provides excellent guidance on these practices.
Finally, create a culture where reporting incidents is encouraged. Employees must feel safe reporting suspicious activity, as a quick report can prevent a major disaster.
Compliance is about protecting customer trust and your reputation, not just avoiding fines. Your secure remote access strategy must consider industry-specific regulations.
Compliance is an ongoing commitment that must be built into your remote access strategy.
Choosing the right solution can feel overwhelming, but a systematic approach simplifies it.
Start by assessing your specific business needs: number of remote workers, required applications, device types (personal, corporate, IoT), and resources.
Scalability is crucial. Your solution must grow with your business. Cloud-based solutions are often more adaptable than hardware-based systems.
In a cost-benefit analysis, proper secure remote access pays for itself through productivity gains and reduced risk of costly breaches. Prevention is always cheaper than recovery.
Integration capabilities are vital. The solution must work with your existing systems. An experienced partner is invaluable here.
Vendor support isn't just about fixing problems. The right partner brings extensive cybersecurity training and technical expertise to guide complex decisions. At Next Level Technologies, our team's deep security background helps businesses in Columbus, Ohio, and Charleston, West Virginia, implement solutions that actually work in the real world.
For a comprehensive overview of available options, check out our detailed guide on Secure Remote Access Solutions.
Over my 15 years helping businesses in Columbus, Ohio, and Charleston, West Virginia implement secure remote access solutions, I've noticed the same questions come up again and again. Let me share the most common ones and the answers my team and I have developed through our extensive cybersecurity training and real-world experience.
The safest method is a multi-layered strategy combining Zero Trust principles (ZTNA), strong endpoint security, mandatory Multi-Factor Authentication (MFA), and continuous monitoring. Relying on a single technology like a VPN is no longer enough. A layered approach ensures that if one defense fails, others are in place to stop threats before they cause damage. Each layer verifies access requests and monitors activity to maintain security.
No, and this is a common misconception. A VPN encrypts traffic but typically grants broad network access. If a user's credentials are compromised, an attacker has wide access to your network, allowing them to move laterally. Modern threats require a more granular approach like ZTNA, which grants access on a per-application basis, severely limiting the potential damage from a single breach. That's why our team always recommends moving beyond basic VPN solutions.
Securing IoT devices like smart sensors and cameras presents unique challenges. They require a specific strategy:
Recognizing that IoT devices need a different approach is key. Our team's extensive cybersecurity training helps us design the right IoT security solution for your business.
The message is clear: secure remote access is essential for modern business. The secure office perimeter is gone, replaced by a distributed workforce where every remote employee is a potential entry point for cyber threats.
Traditional security, especially old-school VPNs, is no longer enough. Cybercriminals have evolved, and they actively target remote workers, exploiting outdated defenses.
We've learned that endpoint security is the new perimeter. Every device is a gateway, requiring foundational security like device hardening and encryption. Multi-Factor Authentication is also a simple, powerful tool to stop unauthorized access.
Most importantly, the future is Zero Trust. This framework shifts security from 'trust but verify' to 'never trust, always verify.' Every connection is continuously authenticated, creating a much stronger security foundation.
A proactive security posture prevents threats rather than just reacting to them. This requires continuous monitoring and regular team training. Since over 90% of incidents involve human error, investing in people is as crucial as technology.
At Next Level Technologies, our team brings extensive cybersecurity training and years of hands-on experience to help businesses steer these complex challenges. Our highly-trained experts in Columbus, Ohio, and Charleston, West Virginia, have seen how the right security framework can transform a vulnerable business into a fortress that cybercriminals simply can't crack.
We understand that every business is different, which is why we don't believe in one-size-fits-all solutions. Whether you're a small medical practice worried about HIPAA compliance or a growing manufacturing company with remote workers across multiple states, we tailor our approach to fit your specific needs and budget.
Don't wait for a security incident to force your hand. The cost of prevention is always lower than the cost of recovery. Protect your business with comprehensive Managed IT Services and IT Support from Next Level Technologies, and let's build a security strategy that grows with your business while keeping your data—and your peace of mind—secure.
Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
