Future-Proof Your Business with the Best Compliance IT Solutions
November 18, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
November 18, 2025
Compliance IT solutions are specialized platforms that help organizations meet regulatory requirements, manage risk, and maintain security through automation. They centralize monitoring, policy management, and audit-ready reporting so teams can work from one reliable system instead of scattered spreadsheets.
Key areas covered by Compliance IT solutions include:
As businesses scale, ad-hoc processes break down. That is why thousands of companies now rely on dedicated platforms that streamline operations, reduce legal exposure, and build customer trust.
Without proper compliance IT solutions, your business is exposed to breaches, penalties, and downtime. The cost of non-compliance quickly exceeds the investment in the right tools.
I'm Steve Payerle, President of Next Level Technologies. For over 15 years, I've helped businesses in Columbus, Ohio and Charleston, WV implement Compliance IT solutions that protect their operations. Our team's extensive cybersecurity training and deep technical experience have guided hundreds of organizations through complex regulatory requirements.
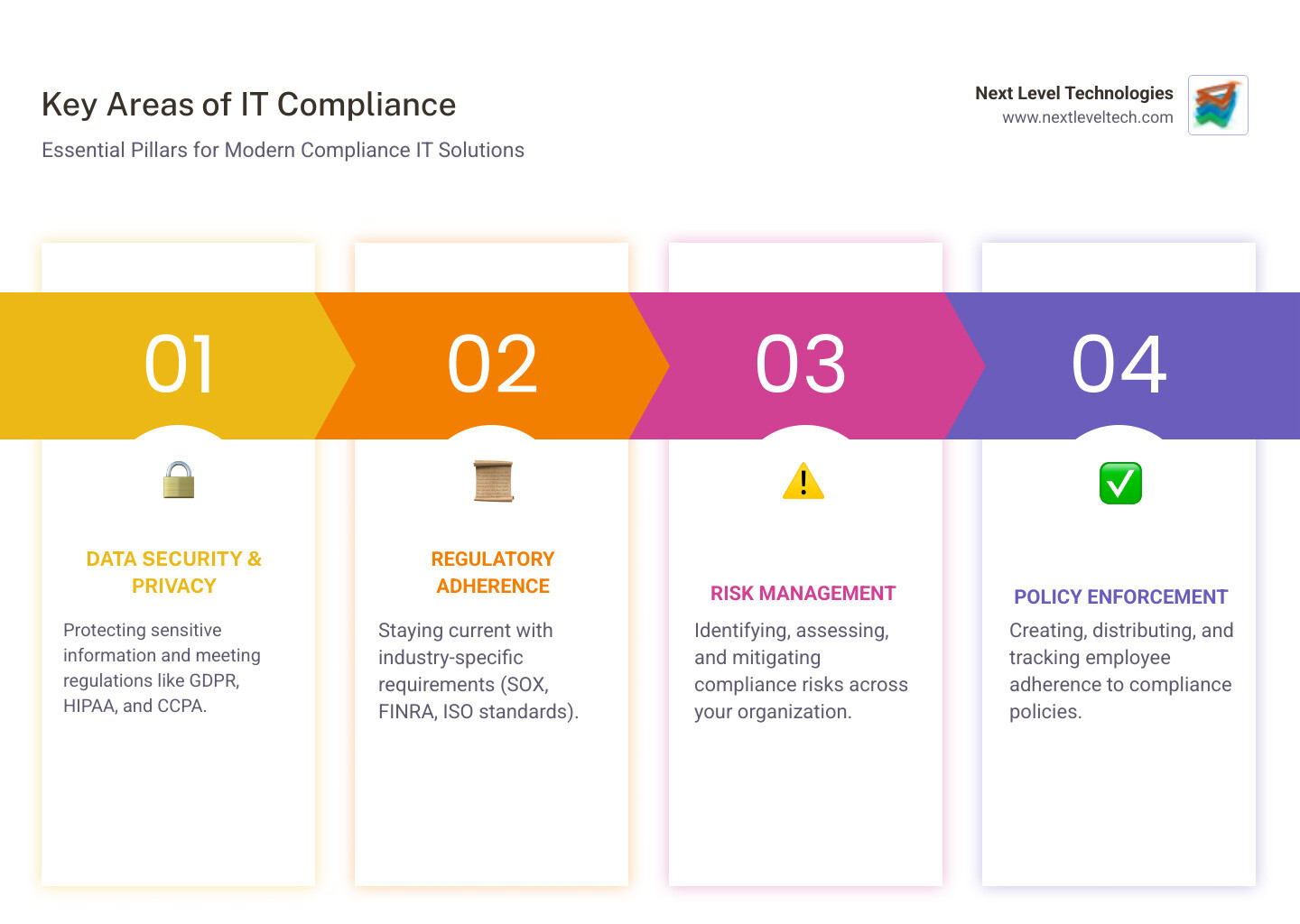
Modern Compliance IT solutions act as a command center for your organization's regulatory posture. They bring all compliance activities into one system, replacing scattered emails and spreadsheets with standardized, automated workflows.
This centralized approach powers key functions: policy development to create and approve internal guidelines, control monitoring to verify adherence, and workflow automation to route approvals and escalations. When issues arise, case management tracks them through resolution. This shift from manual to automated processes improves consistency and speed.
For a deeper dive, check our guide on Understanding the Basics of IT Compliance.
This is where Compliance IT solutions excel. Instead of periodic reviews, modern platforms continuously scan your environment for vulnerabilities. Through real-time monitoring and vulnerability scanning, they surface weaknesses in systems and applications.
Built-in prioritization helps teams focus on the highest-impact risks. When an issue needs action, mitigation workflows guide remediation and verify closure. Our team at Next Level Technologies, with extensive cybersecurity training, emphasizes that understanding your risk posture is essential for business resilience.
Learn more about our approach with IT Compliance Assessments.
Managing policies without a central system leads to confusion. Modern Compliance IT solutions fix this with end-to-end control. Policy creation tools and templates speed drafting and approvals. Version control ensures only current documents are in use.
After approval, dissemination features distribute policies automatically. Employee attestation confirms understanding and creates an auditable trail. All materials live in secure document storage, the single source of truth for compliance documentation.
For guidance, dig into IT Security Policy Compliance.
Audits become predictable instead of stressful with the right platform.
Audit trail logging records key actions for review. Evidence collection pulls required data automatically. Customizable dashboards show compliance status in real time, while automated reporting produces auditor-ready packets in minutes. With our extensive technical experience in Columbus, Ohio and Charleston, WV, we've seen this visibility turn compliance into a strategic asset.
For more insights, visit IT Compliance Monitoring.
Regulations and threats evolve constantly. Artificial intelligence and automation help organizations keep pace.
AI makes Compliance IT solutions faster and more accurate. Algorithms scan millions of data points to spot anomalies humans might miss. Machine learning models improve over time, and predictive analytics highlight potential issues before they escalate.
The results are fewer manual errors and major efficiency gains. The enterprise governance, risk, and compliance (EGRC) market continues to grow exponentially because these tools deliver measurable value. At Next Level Technologies, our team's extensive cybersecurity training shows how AI turns compliance into a proactive capability.
Staying current with regulations no longer has to be manual. AI-enabled Compliance IT solutions monitor regulatory bodies and trusted sources around the clock.
Always-on horizon scanning flags proposed and new rules. Automated impact analysis maps changes to your policies and controls so you know what to update and when. This is especially valuable for organizations operating across states or industries in Columbus, Ohio and Charleston, WV.
Natural Language Processing (NLP) interprets legal text, extracts obligations, and converts them into actionable tasks. Our Cybersecurity Compliance Services leverage these capabilities to help clients adapt quickly.
Compliance programs include repetitive, error-prone tasks. Automation reduces risk and saves time.
Automated evidence gathering collects logs and artifacts from multiple systems. Workflow triggers launch the right processes for events like onboarding or system changes.
Regular user access reviews flag excessive or stale permissions, a common source of incidents. AI-driven data reconciliation spots discrepancies that indicate gaps. Our team's extensive cybersecurity training and technical experience inform these controls, which are core to our Managed Cybersecurity Services.

Choosing the right Compliance IT solutions starts with defining your needs. Identify regulatory obligations, process pain points, and resource gaps. Are spreadsheets slowing audits? Is policy tracking inconsistent? Clarity here drives good selection.
Key considerations include:
For small businesses, our Beginner's Guide for Small Business Success offers practical advice.
A frequent decision is whether to adopt a unified platform or a set of specialized tools.
Integrated platforms provide a single source of truth, reduce data silos, and deliver cross-functional visibility. They can be more cost-effective over time but may have higher upfront costs and a steeper learning curve, with some vendor dependence.
Standalone tools can be quicker to deploy for specific needs and may cost less initially. The trade-offs are fragmented data, integration overhead, and managing multiple vendors. A modular platform can bridge both approaches by letting you start small and add capabilities.
Compliance needs differ by industry. Choose solutions that map to your frameworks and terminology.
Our teams in Charleston, WV and Columbus, Ohio bring extensive cybersecurity training and technical experience to tailor solutions that fit your sector.
Explore industry requirements in our article on Understanding IT Compliance Requirements for Different Industries and get healthcare-specific insights on HIPAA Compliance.
Beyond platform type and industry fit, focus on fundamentals:
Our experience in Columbus, Ohio and Charleston, WV shows these elements drive long-term success. For more strategies, explore Top strategies IT service providers use to guarantee your data privacy and compliance.
Compliance is more than avoiding penalties; the right Compliance IT solutions improve daily operations. Embedded controls lead to better forecasting, stronger risk management, and a clear competitive edge.
This is especially important for small and mid-sized organizations, where a single incident can be costly. Strong practices open doors to customers and markets that require proof of security and compliance. Our teams in Columbus, Ohio and Charleston, WV apply extensive cybersecurity training and technical experience to turn compliance into tangible business value.
Learn more with our guide to IT Security Solutions for Small and Mid-Sized Companies.
Your security posture depends on consistent, measurable controls.

Modern platforms provide a consolidated risk view so teams can prioritize action. Proactive mitigation uses alerts and workflows to address issues early. Built-in incident response documents steps and owners. Core controls like data encryption and access controls protect sensitive information at rest and in transit. Centralizing these capabilities increases visibility and confidence.
For a comprehensive look at securing your IT environment, see our IT Security Services Ultimate Guide.
Certifications such as SOC 2 or ISO 27001 signal mature security and compliance programs. Compliance IT solutions support audit readiness by organizing documentation and evidence the way auditors expect.
Many platforms include framework mapping to align controls to SOC 2, ISO 27001, and more. After certification, continuous monitoring maintains control effectiveness. Evidence management captures proof automatically so you stay audit-ready. Our teams in Columbus, Ohio and Charleston, WV combine technical experience with extensive cybersecurity training to guide clients from preparation to ongoing compliance.
Start your journey with our guide on SOC 2 Assessment and explore more about IT Compliance Certifications.
When discussing Compliance IT solutions, a few questions come up often. Here are concise answers.
GRC (Governance, Risk, and Compliance) is the overall strategy that ensures operations are governed, risks are managed, and obligations are met. Platforms unify these areas for a holistic view.
Compliance software focuses on meeting specific regulations like HIPAA or GDPR. It can be standalone or part of a GRC suite. As we tell clients in Columbus, Ohio and Charleston, WV: GRC is the house; compliance software is a key room or its foundation.
Modern Compliance IT solutions include capabilities built for privacy.
These features support Privacy by Design and help demonstrate protection of personal data. Our team's extensive cybersecurity training ensures we implement these controls effectively.
Yes. Small businesses face the same risks with fewer resources. Right-sized, scalable Compliance IT solutions reduce manual work, help avoid costly fines, and build customer trust.
Our teams in Columbus, Ohio and Charleston, WV implement practical, affordable solutions for SMBs, leveraging deep technical experience and extensive cybersecurity training.
Learn more in our article: How Managed IT Services Help Small Businesses with Regulatory Compliance.
We've shown how Compliance IT solutions go beyond avoiding penalties to strengthen operations, protect assets, and build trust. The future is integrated, intelligent, and proactive.
Implementing and maintaining these capabilities is challenging. The right partner accelerates success.
At Next Level Technologies, we bring 15+ years of experience helping organizations in Columbus, Ohio and Charleston, WV deploy effective Compliance IT solutions. Our team's extensive cybersecurity training and technical experience mean we do more than install software—we align solutions to your risks, regulations, and goals.
We've guided hundreds of organizations through HIPAA, SOC 2, and more. We listen first, then design a plan that fits your reality, whether you are starting your program or scaling it.
Let us handle compliance and cybersecurity complexities so you can focus on growth.
Ready to build a more secure, compliant future? Partner with us for your managed IT services and support and get a dedicated team in your corner.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
