How to Ace Your SOC 2 Type 2 Assessment
July 28, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
July 28, 2025
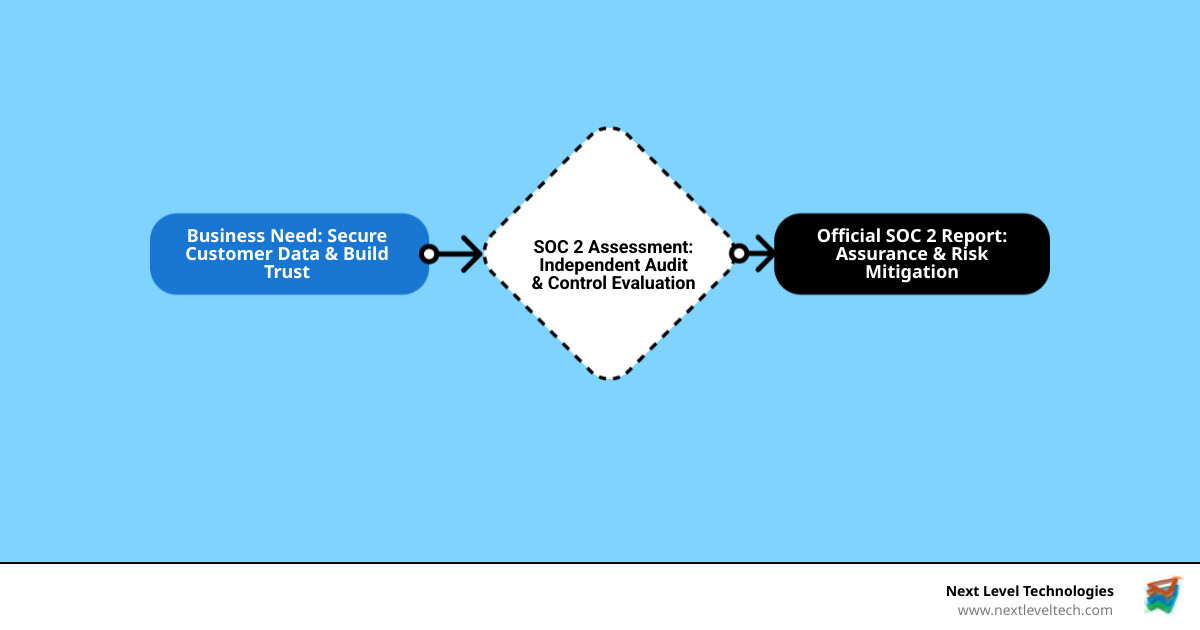
A soc 2 assessment can seem daunting, but it's a critical process for many organizations. At its core, a SOC 2 assessment is an independent audit of how well a service organization manages and protects customer data based on a framework developed by the American Institute of Certified Public Accountants (AICPA).
Here's a quick look at what a SOC 2 assessment covers:
With data breaches on the rise, customers demand proof that their information is safe. SOC 2 compliance isn't just about risk avoidance; it's about building trust and demonstrating a serious commitment to security.
As President of Next Level Technologies, I've seen how a successful soc 2 assessment transforms businesses. Our highly trained cybersecurity staff in Columbus, Ohio, and Charleston, WV, have the technical experience to help companies achieve and maintain this gold standard.
Handy soc 2 assessment terms:
The Trust Services Criteria (TSC) are the foundation of a soc 2 assessment. These are the five principles against which your organization's controls are measured.
While the Security criterion is mandatory for any SOC 2 report, the other four—Availability, Processing Integrity, Confidentiality, and Privacy—are selected based on your services and the data you handle.
Choosing the right TSCs is a critical first step that shapes your audit's scope. Including more relevant criteria provides a more complete security picture, giving clients greater peace of mind. Our team at Next Level Technologies, with locations in Columbus, Ohio, and Charleston, WV, offers Cybersecurity Compliance Services to guide you in selecting the criteria that best fit your organization.
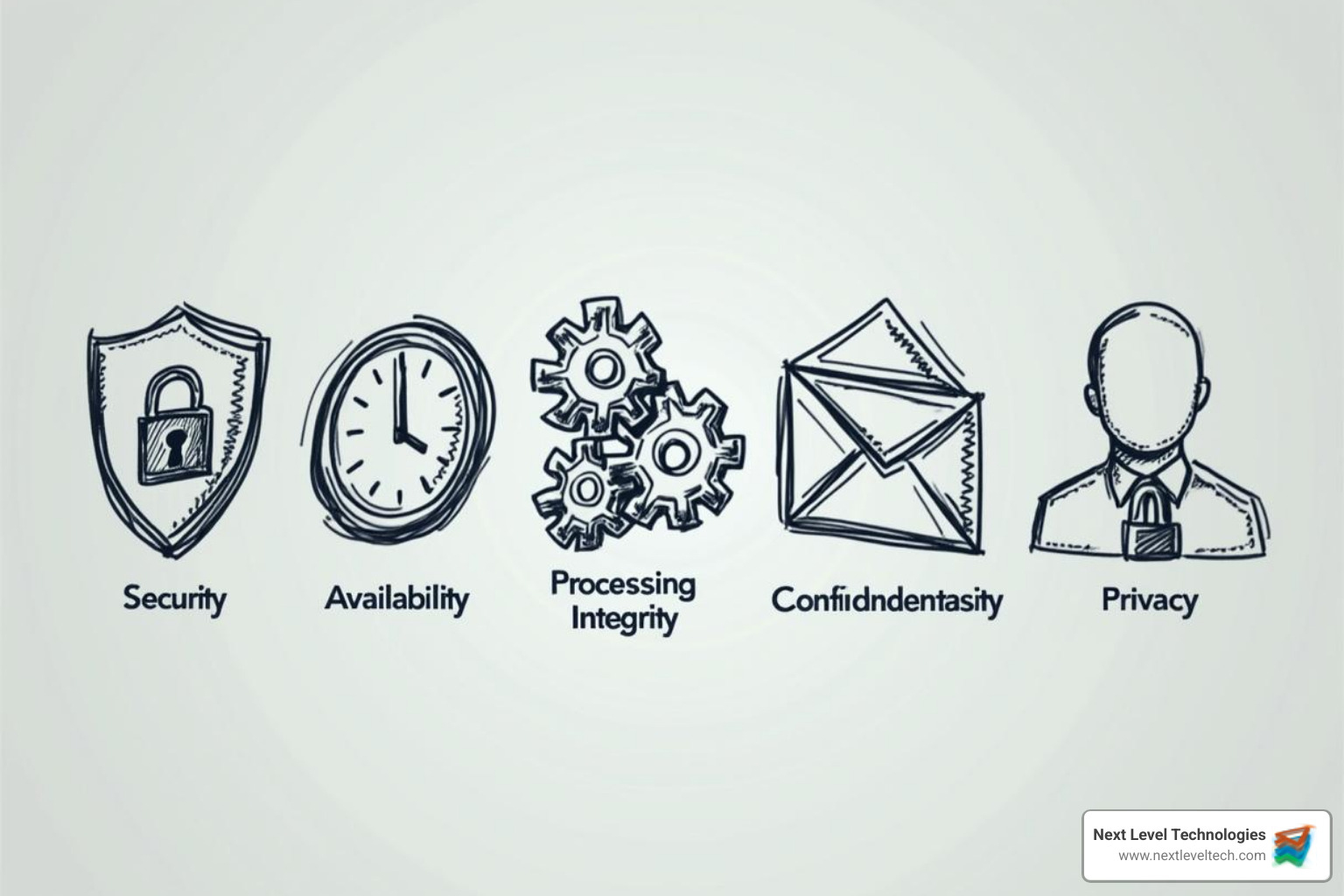
Let's unpack each pillar:
The Security criterion, or Common Criteria, is the core of every SOC 2 report. It focuses on protecting systems and data from unauthorized access, both digital and physical. It addresses whether your systems are protected against unauthorized use and access.
This pillar covers protective measures such as:
Our team's extensive cybersecurity training ensures these controls are not just implemented but are robust and effective. We also offer Advanced Threat Protection Solutions to further bolster your defenses.
This criterion ensures your systems and data are available for operation and use as committed or agreed. It's about minimizing downtime and having solid plans for unexpected disruptions.
Key components include:
We help you build resilient systems, incorporating powerful Cloud Security Best Practices to ensure your services are always available.
Processing Integrity ensures your system processes data completely, accurately, and on time as authorized. It confirms that data is handled reliably within your systems. This criterion doesn't guarantee the accuracy of data upon input, but rather that the system processes it as intended.
Controls often involve:
Our IT Security Policy Compliance services help you enforce rules that protect your data processing integrity.
Confidentiality is about protecting sensitive information (e.g., business plans, intellectual property) from unauthorized access or disclosure. Special controls are needed to safeguard this type of data.
Key controls include:
Our Secure Remote Access Solutions are designed with confidentiality in mind, protecting your sensitive data wherever it's accessed.
The Privacy criterion governs how your organization collects, uses, retains, discloses, and disposes of Personally Identifiable Information (PII) in conformity with your privacy notice and the Generally Accepted Privacy Principles (GAPP).
Controls usually include:
Protecting personal data is a fundamental responsibility. At Next Level Technologies, our highly trained cybersecurity staff helps organizations steer data privacy complexities. Learn more about frameworks like HIPAA in our article: Is Your Data Truly Secure The Shocking Truth About HIPAA Compliance.
A soc 2 assessment journey is a manageable process with the right guidance. It involves careful audit preparation, gap analysis, and remediation, often streamlined with compliance automation tools.

Before the official audit, we strongly recommend a soc 2 assessment readiness assessment. This proactive step identifies your organization's preparedness, saving time, money, and stress.
During a readiness assessment, our highly trained cybersecurity staff will help you:
A professional readiness assessment typically ranges from $10,000 to $17,000. This upfront investment is minor compared to the potential cost of a qualified audit report or failing to meet client expectations. Our team in Columbus, Ohio, and Charleston, WV, leverages extensive technical experience to offer IT Compliance Assessments that make this phase smooth and insightful.
A key decision is choosing between a Type I or Type II report, which impacts the audit's scope, timeline, and level of assurance.
| Feature | SOC 2 Type I | SOC 2 Type II |
|---|---|---|
| Audit Window | A snapshot in time | Over a period (typically 3-12 months) |
| Control Testing | Assesses if controls are designed well | Assesses both if controls are designed well AND if they work effectively over time |
| Timeline | Generally faster to get | Requires a monitoring period, so it takes longer |
| Level of Assurance | Provides assurance on control design only | Provides a higher level of assurance on both control design and operational effectiveness |
Most customers now prefer a SOC 2 Type II report. While a Type I is faster, it only shows your controls' design at one point in time. A Type II report proves your controls work effectively over a period, making it the gold standard for demonstrating ongoing security commitment. We recommend aiming for a Type II, as it offers greater assurance and opens more business opportunities. A shorter 3-month review period is an option for those on a tighter schedule.
Once you are ready, an independent third-party auditor conducts the official soc 2 assessment:
The entire journey, from preparation to receiving the report, generally takes six months to a year. It's a significant undertaking that our team, with its extensive cybersecurity training and IT Internal Audit expertise, can help you steer successfully.
Your SOC 2 report is a powerful statement that serves as independent validation of your commitment to data security. It offers a competitive advantage, streamlines vendor management, mitigates risks, and builds confidence in your services.

While not legally mandatory like HIPAA or GDPR, SOC 2 compliance has become an essential requirement for service organizations that store, process, or transmit customer data. This includes:
Why is it so important?
Our Managed IT Services Help Small Businesses With Regulatory Compliance, including preparing for and maintaining SOC 2 compliance.
It's helpful to understand how SOC 2 compares to other common frameworks:
SOC 1 vs. SOC 2:
SOC 2 vs. ISO 27001:
While both aim to improve security, their approaches differ. Many organizations pursue both, as they are complementary. Our expertise can help you steer various compliance requirements, as detailed in Understanding IT Compliance Requirements For Different Industries.
A soc 2 assessment is an attestation, not a pass/fail certification. The auditor provides an objective opinion on your security posture based on AICPA standards.
Instead of a "fail," the report will contain one of four opinions:
Receiving anything other than an unqualified opinion means you'll need to remediate the identified issues and likely undergo another audit. The goal is always to achieve an unqualified opinion to provide the highest level of assurance.
It's normal to have questions when navigating a soc 2 assessment. Our team, with its deep technical experience and extensive cybersecurity training, has guided countless businesses through the process. Here are some of the most common questions we hear.
A soc 2 assessment must be performed by an independent Certified Public Accountant (CPA) or CPA firm accredited by the American Institute of CPAs (AICPA). This independence is crucial for an unbiased and credible report. When selecting a firm, ensure they have the proper licensing, a deep knowledge of the SOC framework, and relevant industry expertise.
A SOC 2 report is generally considered valid for 12 months. To maintain continuous compliance and assure clients of your ongoing commitment to security, you'll need to undergo annual audits. For periods between audits, a bridge letter can be issued. This is a formal statement from management that "bridges" the gap from your last report date, extending the assurance for new clients. Our IT Compliance Monitoring services help you stay ahead of these ongoing requirements.
The entire soc 2 assessment process, from preparation to the final report, typically takes between six months to a year. The timeline can vary based on your organization's current security maturity, system complexity, and internal efficiency.
The process generally includes:
Compliance automation platforms can significantly accelerate this timeline, potentially cutting the total time in half by streamlining tasks like evidence collection and risk management. Our highly trained cybersecurity staff leverages their expertise to make this complex journey manageable for you.
A soc 2 assessment is more than a compliance checkbox; it's a strategic investment in your business. It demonstrates your commitment to data security, builds confidence, and sets you apart. This isn't a one-time task but an ongoing journey toward continuous security improvement.
At Next Level Technologies, we've walked this path with many businesses. Our team of highly trained cybersecurity staff, based in Columbus, Ohio, and Charleston, WV, are ready to be your trusted guides. With extensive technical experience and cybersecurity training, they are experts at navigating the SOC 2 landscape.
We'll be with you from the initial readiness assessment to implementing controls and guiding you through the audit. We pride ourselves on offering comprehensive Managed IT Services and IT Support, helping businesses of all sizes achieve and maintain SOC 2 compliance.
Let's team up. Our goal isn't just to help you get a soc 2 assessment report; it's to help you ace it, strengthening your reputation as a secure and dependable service provider. Together, we'll reach the next level of security and trust for your business.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
