Unlocking Trust: AWS Security and Compliance Explained
January 19, 2026

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026

Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026

Protect your data. Learn how cloud backup services for business ensure recovery, continuity, and security for your enterprise.
March 3, 2026
January 19, 2026
AWS security and compliance is about protecting your business data in the cloud while meeting regulatory requirements.
At a glance:
With over 60% of business data now in the cloud, the stakes are high for mid-sized organizations. The cloud can give you enterprise-grade security without enterprise-level costs, but only if you understand how to use it correctly.
Many businesses still struggle with outdated technology and frequent downtime while facing pressure to protect customer data and avoid costly breaches. Cybercriminals increasingly target smaller organizations as "low-hanging fruit," and the average data breach now costs millions of dollars.
AWS built its platform with security as the top priority. Its infrastructure protects some of the world's most security-sensitive organizations, from global banks to government operations. But simply moving to AWS is not enough. You must configure the security tools properly and understand your responsibilities.
The foundation is the Shared Responsibility Model. AWS secures the infrastructure that runs the cloud, while you secure everything you put in or connect to that cloud. This division determines who handles what aspects of security and compliance.
This guide breaks AWS security and compliance into clear, actionable concepts. You will see which AWS services protect your data, how to meet industry regulations like HIPAA and PCI DSS, and why the shared responsibility model matters.
I'm Steve Payerle, President of Next Level Technologies. Since 2009, our teams in Columbus, Ohio and Charleston, WV have helped businesses implement secure, compliant cloud environments. Our staff’s extensive cybersecurity training and deep technical experience with aws security and compliance let us turn complex cloud security concepts into practical solutions for mid-sized businesses.
Related content about aws security and compliance:
Moving to the cloud means rethinking how security works. It is not a magic bullet that makes all your security worries disappear, but it does shift some of the heavy lifting to AWS. This critical concept is known as the Shared Responsibility Model, and it is the cornerstone of understanding AWS security and compliance. It clearly defines what AWS is responsible for and what remains your responsibility.
When we talk about AWS's responsibility, we are referring to the security of the cloud. Think of it like a landlord who secures the building, plumbing, and electricity, but is not responsible for what you put inside your apartment.
AWS protects the global infrastructure that powers all its services, including:
AWS continuously audits its environments and has been building this security and compliance framework since 2006. By simply choosing AWS, you inherit the best practices, policies, and operational processes of one of the world's leading security teams.

While AWS handles the "of the cloud" part, you, as the customer, are responsible for security in the cloud. To continue the analogy, the landlord secures the building, but you are responsible for locking your apartment door and securing your valuables.
Your responsibilities in the Shared Responsibility Model include:
Understanding this division is key. It ensures you know exactly where your efforts must be focused to create a secure environment. Our teams in Columbus and Charleston apply extensive cybersecurity training and hands-on AWS experience to help clients design architectures that meet their side of this model.
For more insights, explore our guide on Cloud IT Security. You can also dig deeper into the specifics of the model by reading more about the Shared Responsibility Model.
AWS does not just provide a secure infrastructure; it also offers a suite of tools and services to help you meet your security and compliance objectives. Our highly trained technicians, with extensive cybersecurity training and deep technical experience, are adept at configuring these tools for maximum protection, ensuring your business in Columbus, Ohio, Worthington, Ohio, or Charleston, WV benefits from enterprise-grade security.
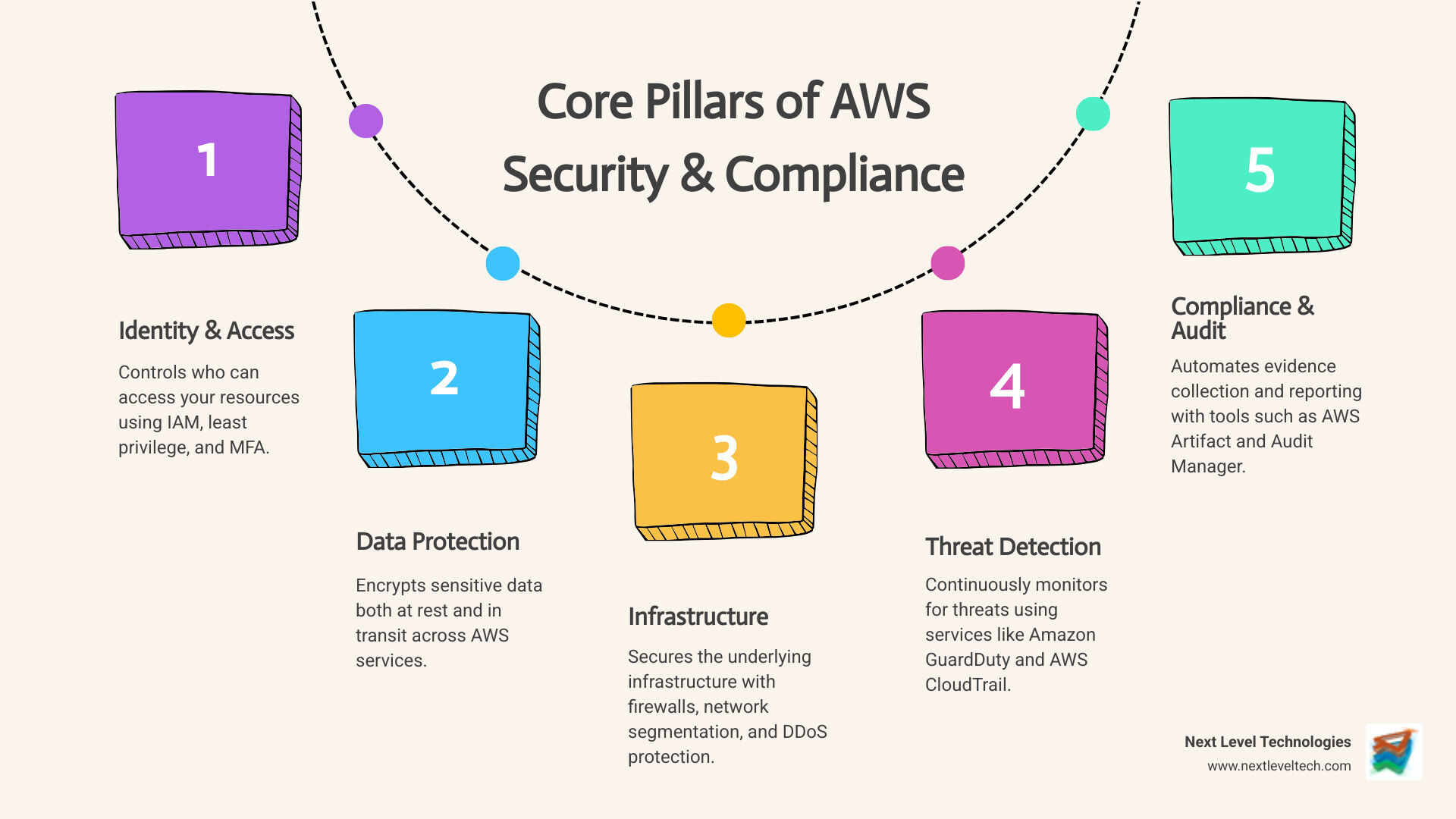
The first line of defense for any cloud environment is controlling who can access your resources and what they can do. AWS Identity and Access Management (IAM) is the foundational service for this. IAM lets you manage user permissions, define roles, and create policies that govern access to AWS services and resources.
At Next Level Technologies, we emphasize the principle of least privilege when configuring IAM. Users get only the permissions they need to perform their job functions. Combined with Multi-Factor Authentication (MFA), which adds an extra layer of security beyond just a password, IAM becomes a strong guardian for your AWS environment. Our team helps you implement MFA across critical accounts, significantly reducing the risk of unauthorized access. For a deeper dive, see our Multi-Factor Authentication Benefits Complete Guide.
Even with robust access controls, threats can emerge. Continuous monitoring and proactive threat detection are vital. AWS offers services that act as always-on security guards, identifying potential risks before they escalate.
By integrating these services, our cybersecurity-trained staff helps clients build a proactive security posture and respond quickly to issues. This continuous monitoring is a critical component of effective Threat Modeling and Risk Analysis.

Beyond identity and detective controls, protecting your core infrastructure and data is essential. AWS provides services to fortify your network and safeguard sensitive information.
For network protection, AWS offers:
For data protection, AWS offers strong encryption and key management:
Our approach to Data Protection and Security on AWS focuses on layered defense, including:
Meeting regulatory requirements and maintaining compliance can feel daunting. AWS simplifies this by adhering to numerous global standards and providing tools to help you prove your own compliance. This is where our team's deep understanding of AWS security and compliance, backed by extensive cybersecurity training and real-world technical experience, truly benefits businesses in Columbus, Worthington, and Charleston.
AWS supports 143 security standards and compliance certifications, more than any other major cloud provider. This includes:
By operating in an accredited AWS environment, you can reduce the scope and cost of your own audits. You effectively "inherit" AWS controls for the "security of the cloud," and focus your compliance efforts on your applications and data. To dive deeper into these controls, see the AWS Risk and Compliance whitepaper.
Many industries face unique regulatory requirements. AWS provides the tools and architectural guidance to help you meet them, and our engineers apply their specialized cybersecurity training to implement those designs correctly.
Examples include:
Being able to demonstrate compliance is as important as achieving it. AWS provides services that streamline auditing and reporting, turning manual, periodic tasks into automated, ongoing functions.
By leveraging these tools, our cybersecurity-focused teams help clients in Ohio and West Virginia maintain transparent, auditable cloud environments. This automation is a key part of robust Cybersecurity Audit and Compliance Solutions.
For small and mid-sized businesses (SMBs), the path to strong cloud security and compliance can seem overwhelming. The good news is that AWS offers enterprise-grade security capabilities without enterprise-level costs, provided you plan carefully and configure services correctly.
Our teams in Columbus, Worthington, and Charleston specialize in helping SMBs apply AWS securely, drawing on extensive cybersecurity training and hands-on implementation experience.
Many SMBs question whether cloud security is truly better than traditional on-premises setups. In practice, AWS often provides a stronger security posture than most organizations can achieve alone.
| Feature | On-Premises Security | AWS Cloud Security |
|---|---|---|
| Upfront Cost | High (hardware, software, infrastructure) | Low (pay-as-you-go, no large capital expenditure) |
| Maintenance | High (physical upkeep, patching, upgrades) | Lower (AWS manages infrastructure; you manage "in the cloud") |
| Physical Security | Dependent on your facility's capabilities | World-class, multi-layered (AWS data centers) |
| Scalability | Difficult and costly to scale up or down | Highly elastic, scales on demand |
| Compliance Burden | You own all controls and audits | Shared responsibility (AWS handles "of the cloud") |
With AWS, you remove the need to manage facilities and hardware, freeing your IT staff to focus on higher-value work. You also benefit from a 24/7 global security team monitoring the infrastructure, something typically out of reach for SMB budgets.
Cybercriminals increasingly view SMBs as easy targets because many lack advanced security controls. Compliance is not only about avoiding fines; it is also about building trust with customers, partners, and regulators.
Strong AWS security and compliance practices help you:
Cyber insurance can provide a financial safety net but does not replace solid security and compliance. Our team delivers comprehensive IT Security Solutions for Small and Mid-Sized Companies that combine technical controls with strategy.
While AWS offers powerful tools, misconfigurations remain a leading cause of cloud breaches. For SMBs with lean IT teams, the complexity of security settings can be a real risk.
Our cybersecurity-trained engineers and technicians help you:
By leveraging our managed services, you gain a dedicated team of cloud security professionals who act as an extension of your business. We keep your AWS environment secure and compliant so you can focus on core operations. Learn more about How Managed IT Services Help Small Businesses with Regulatory Compliance.
The most critical first step for securing an AWS account is to secure your root user account. This account has unrestricted access to all your AWS resources, so it is a prime target for attackers. You should:
Our teams in Columbus and Charleston routinely help clients harden root accounts as part of initial onboarding, drawing on extensive cybersecurity training to avoid common mistakes.
No. Using AWS does not automatically make your business compliant with regulations like HIPAA, PCI DSS, or GDPR. This ties back directly to the Shared Responsibility Model.
AWS provides an infrastructure that is compliant with these standards (security of the cloud). You are still responsible for configuring your applications, data, and access controls in a compliant manner (security in the cloud). AWS offers tools and guidance, but achieving and maintaining compliance requires your active participation and correct configuration.
In many respects, AWS security is superior to traditional on-premises solutions, especially for SMBs and mid-sized organizations:
With the right configuration and ongoing management by an experienced partner, AWS often delivers a more robust, scalable, and cost-effective security posture than typical on-premises environments.
Achieving robust AWS security and compliance is not a one-time project; it is an ongoing commitment. It requires a clear understanding of the Shared Responsibility Model, correct configuration of powerful AWS services, and constant vigilance against evolving threats.
For businesses in Columbus, Worthington, and Charleston, navigating this landscape can be complex. At Next Level Technologies, our teams bring extensive cybersecurity training and deep technical experience to every AWS environment we design, implement, and manage. We focus on:
This lets you focus on your core business while we help keep your cloud infrastructure secure and compliant.
Ready to take your cloud security to the next level? Explore our Managed IT Services and IT Support to see how we can help.
Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
