Navigating Change: Your SOC 2 Management Playbook
August 22, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
August 22, 2025
SOC2 change management is the systematic process for modifying IT infrastructure, software, and procedures while maintaining security and compliance for a SOC 2 audit. Without it, organizations risk vulnerabilities, system disruptions, or failing their audit entirely.
Key components include:
A robust SOC 2 change management process prevents system downtime and security issues by ensuring every modification is planned, tested, and documented. This creates the audit trail auditors need and protects your business from costly disruptions. Ineffective change management can lead to unauthorized deployments, security breaches, and compliance failures. When done right, it becomes a shield against operational chaos and a way to demonstrate trust.
I'm Steve Payerle, President of Next Level Technologies. With over 15 years of experience, I've helped businesses across Columbus, Ohio, and Charleston, WV, implement effective soc2 change management frameworks. Our team's extensive cybersecurity training and technical experience allow us to guide companies through complex compliance requirements, balancing operational efficiency with security demands.
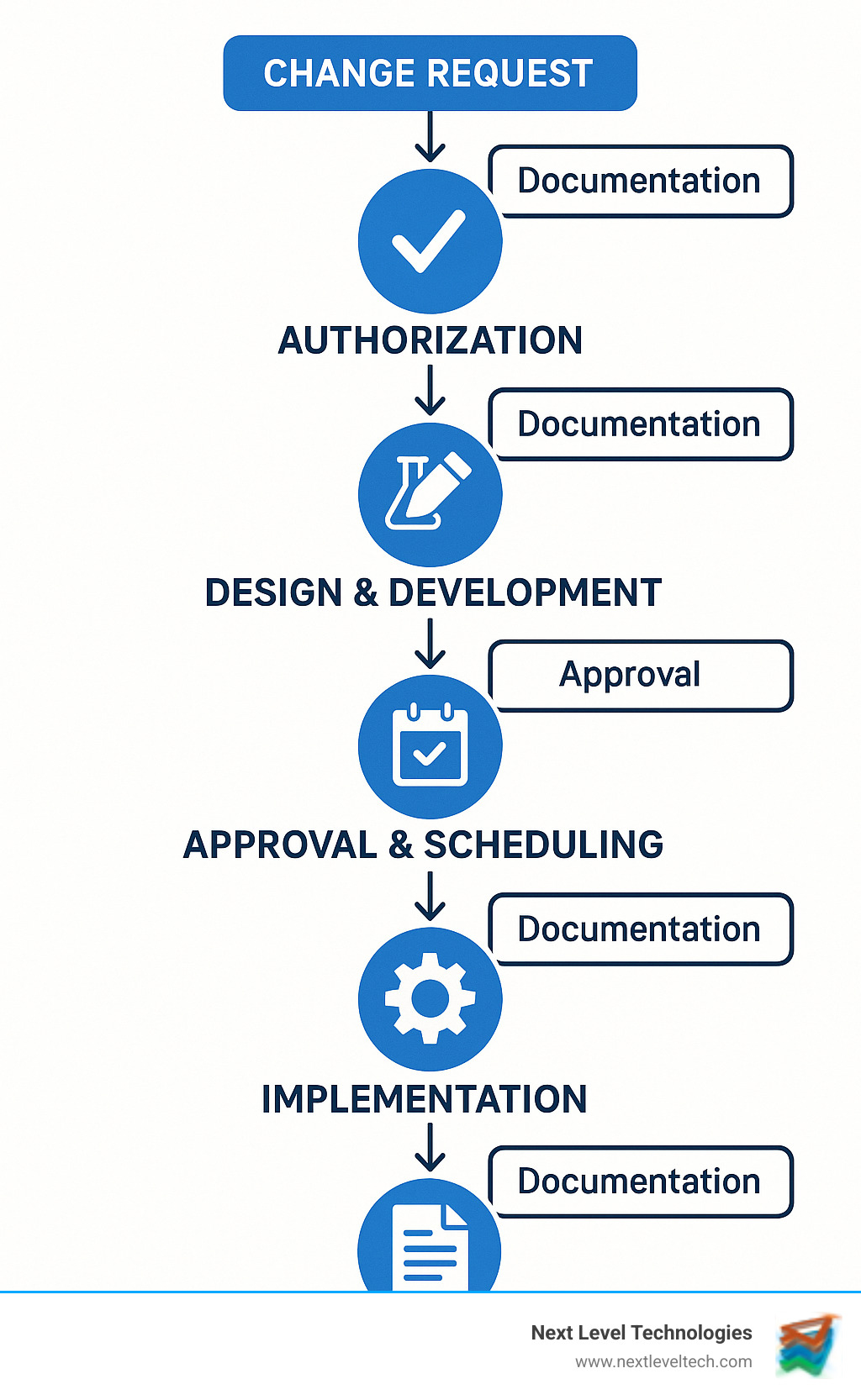
Soc2 change management vocabulary:
When your business relies on customer trust, you must prove that constant IT evolution—software updates, security patches, server upgrades—doesn't put their data at risk. The American Institute of Certified Public Accountants (AICPA) provides the SOC 2 framework as a roadmap for demonstrating responsible data handling across five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Soc2 change management is not optional; it's a core component of Common Criteria 8 (CC8). Auditors will scrutinize how you manage changes to your infrastructure, software, procedures, and data, seeking proof that every modification improves risk mitigation and maintains system stability.
For details, see the SOC 2 Common Criteria related to Change Management (CC8). For broader context, we've also covered more information about IT Compliance.
Think of soc2 change management as a safety net for your IT environment. It's a systematic process ensuring every change—no matter how small—goes through proper channels. This process covers the full spectrum of modifications:
The goal is to allow only controlled modifications, preventing unauthorized changes that introduce security vulnerabilities or system failures. A solid change management process acts as a gatekeeper, ensuring only approved, tested changes reach production.
Auditors focus on soc2 change management because it's tangible proof of your security commitment. A well-implemented process is foundational to your security program.

Building a soc2 change management process isn't just about ticking compliance boxes—it's about creating a safety net that protects your business from costly mistakes. The foundation of a compliant process rests on a complete change lifecycle, which requires meticulous documentation, proper authorization, thorough testing, formal approval, and strict segregation of duties.
Our team at Next Level Technologies has seen these components work together to prevent chaos. To see how change management fits into a broader strategy, explore our insights on IT Security Policy Compliance.
Every change should follow a predictable journey to prevent surprises that can bring down systems and compromise data.
In a SOC 2 audit, if you can't prove it, it didn't happen. Documentation provides your audit trail and a roadmap for consistent operations.
This documentation ecosystem creates the comprehensive audit trail that soc2 change management requires, building transparency and accountability into every change.
Building a soc2 change management framework can be a streamlined process. We've helped countless businesses in Columbus, Ohio, and Charleston, WV, transform chaotic change processes into compliant systems that make their lives easier. The secret is creating a framework that protects your business and feels natural to use.
Our team's extensive cybersecurity training and technical experience have taught us that the best compliance programs aren't a burden. For comprehensive support, explore our Cybersecurity Compliance Services.

Here is the proven approach we use to build a soc2 change management process from the ground up:
Sometimes, urgent changes are necessary to restore service or fix a critical vulnerability. SOC 2 allows for this but requires a controlled, documented approach.
Having clear processes for high-pressure situations demonstrates the operational maturity that auditors and customers expect.
A well-designed soc2 change management process naturally strengthens all five Trust Services Criteria (TSC), creating layers of protection. Think of it as ensuring every adjustment to your complex security system is carefully planned, tested, and verified. For organizations looking to evaluate their current posture, we offer comprehensive IT Compliance Assessments to identify gaps.
Effective change management directly supports each of the Trust Services Criteria. This is what we see in action daily when working with our clients across Columbus, Ohio, and Charleston, WV.
| Trust Services Criteria | How Change Management Contributes |
|---|---|
| Security | - Prevents Unauthorized Changes: Strict authorization and approval processes ensure only approved changes are made. |
| - Mitigates Vulnerabilities: Secure design, development, and testing processes identify and remediate security flaws before deployment. | |
| - Maintains Baseline Configurations: Ensures systems adhere to hardened security standards. | |
| Availability | - Minimizes Downtime: Thorough testing and rollback plans reduce the risk of changes causing service disruptions. |
| - Ensures System Resilience: Changes are designed and tested to ensure the system can recover from failures and maintain accessibility. | |
| - Supports Business Continuity: Well-managed changes prevent outages that could impact critical business functions. | |
| Processing Integrity | - Ensures Accuracy and Completeness: Changes to data processing systems (e.g., new algorithms, data migrations) are tested to ensure data remains accurate, complete, and timely. |
| - Maintains Authorization: Controls ensure that changes to processing logic are authorized and align with business objectives. | |
| Confidentiality | - Protects Sensitive Information: Changes to data handling, storage, or access controls are managed to ensure confidential data is not exposed or compromised. |
| - Data Sanitization: Procedures for sanitizing data when moving between environments (e.g., production to test) prevent confidential information from being inadvertently used or exposed. | |
| Privacy | - Ensures Data Privacy Compliance: Changes impacting personal information are designed and tested to comply with privacy policies and regulations (e.g., GDPR, CCPA). |
| - "Privacy by Design": Proactively considers privacy issues during the design and development phases of any system or process change, rather than as an afterthought. | |
| - Protects Personal Information: Controls ensure personal data is handled securely throughout the change lifecycle, from development to deployment. |
As the table shows, proper change management is integral to Security by preventing unauthorized changes and mitigating vulnerabilities. It supports Availability through rigorous testing and rollback planning. For Processing Integrity, it ensures data remains accurate during system updates. Finally, it upholds Confidentiality and Privacy by carefully managing any change that touches sensitive or personal information.
After years of helping businesses, our team has learned to spot the warning signs of a failing change management process before they become major incidents.

The good news is these problems are fixable. With our technical experience and cybersecurity training, we help organizations in Columbus and Charleston identify and resolve these issues before they become audit findings.
Our team at Next Level Technologies has guided countless businesses in Columbus, Ohio, and Charleston, WV, through their soc2 change management journey. Based on our extensive cybersecurity training and technical experience, here are the answers to the most common questions we encounter.
A Change Advisory Board (CAB) is a cross-functional group that reviews and approves proposed changes. While SOC 2 does not explicitly require a "CAB," it does require a formal, documented approval process where changes are authorized by appropriate personnel. A CAB is simply one effective way to meet this requirement, especially for high-impact changes.
For smaller organizations, this function might be fulfilled by a designated approver or a small senior team. The key is that the approval function is formal, documented, and consistently followed.
This is a common concern for small teams where the same person may need to both develop and deploy a change. SOC 2 allows for this if you implement "compensating controls" that focus on detection and review.
These approaches, combined with solid documentation, demonstrate effective control to auditors, even with a lean team.
Though often used interchangeably, these terms have distinct meanings.
Think of change control as one critical stop on the broader change management highway. Auditors examine your entire soc2 change management framework, not just the approval gate.
Building and maintaining a soc2 change management framework doesn't have to be a solo effort. For many businesses, implementing these processes can feel overwhelming while juggling daily operations. When done right, however, a robust change management process becomes the foundation for continuous compliance and a stronger security posture, reducing downtime and building customer confidence.
At Next Level Technologies, we've guided countless businesses in Columbus, Ohio, and Charleston, WV, through this journey. Our team brings extensive cybersecurity training and deep technical experience to every engagement. We understand what auditors look for and, more importantly, how to build processes that work for your team, not against them.
We don't just hand you a policy document. We work alongside your team to implement change management processes that fit your culture, help select the right tools, and train your people effectively. Our goal is to make compliance manageable and sustainable.
Ready to build a soc2 change management framework that protects your business and impresses auditors? Explore our comprehensive Managed IT Services to see how we can partner with you to secure your operations.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
