Protecting Your Assets: A Guide to Cybersecurity in Financial Institutions
October 22, 2025

Master it service continuity management. Learn ITSCM objectives, components, and implementation to ensure business resilience and swift recovery.
March 9, 2026
Optimize IT spending & boost ROI with it cost management software. Gain visibility, cut waste, and drive strategic growth.
March 6, 2026

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
October 22, 2025
Cybersecurity for financial firms has become one of the most critical operational challenges of our time. Financial institutions are prime targets for sophisticated cybercriminals because they handle vast amounts of sensitive data and monetary assets. The stakes are incredibly high, with the consequences of a breach extending far beyond immediate financial loss to include regulatory fines, legal costs, and long-lasting reputational damage.
Key Components of Financial Cybersecurity:
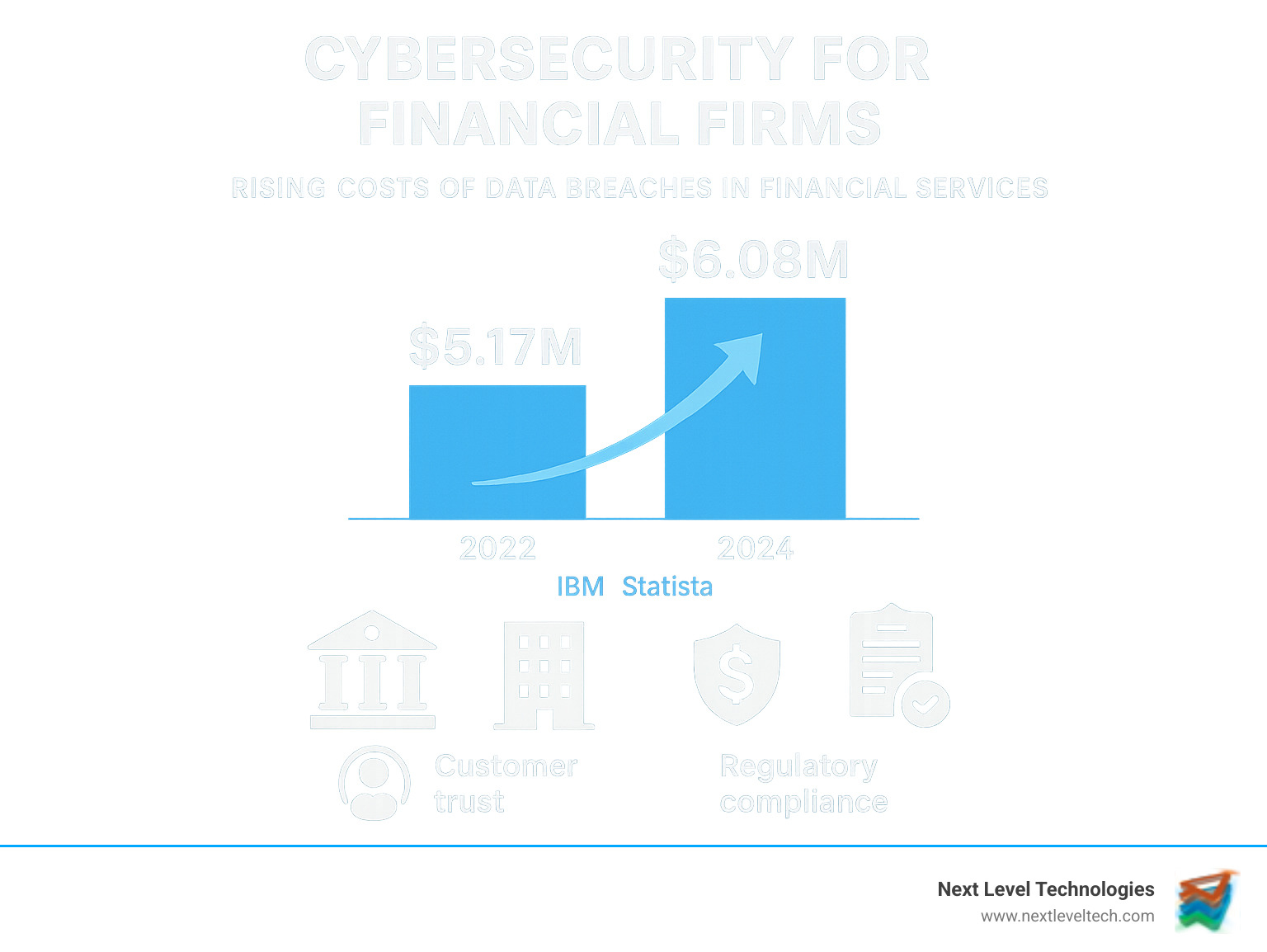
According to IBM's 2023 report, the finance and insurance industry saw the highest average cost of data breaches at $5.17 million per incident, a figure Statista reports has grown to $6.08 million USD.
As the volume and sophistication of cyber threats increase, financial institutions must evolve from reactive security to proactive, comprehensive cybersecurity programs. I'm Steve Payerle, President of Next Level Technologies. From our offices in Columbus, Ohio and Charleston, WV, I've spent over a decade helping financial institutions build robust defenses. My team's extensive cybersecurity training and technical experience have shown that effective protection requires deep industry knowledge and a full understanding of the evolving threat landscape.
Basic cybersecurity for financial firms terms:
For any financial institution, cybersecurity for financial firms is the foundation upon which trust, reputation, and operational resilience are built. You handle the most sensitive data imaginable—financial records, social security numbers, and investment portfolios—along with direct monetary assets. A single failure can trigger a devastating domino effect, including reputational damage, operational disruptions, and a loss of customer trust.
Adding to this pressure, financial institutions face intense regulatory scrutiny from multiple agencies. Understanding IT Compliance is not just about checking boxes; it's about building a fortress to protect your entire business.
The average cost of a data breach in finance recently climbed to $6.08 million USD globally, according to Statista's global cost of breach statistics. These figures, however, don't capture the full story. They omit the cascading costs of regulatory fines, lengthy legal battles, and customer churn that follows when people lose faith in your security. A major cyberattack can even shake confidence in the entire financial system, creating ripple effects across markets.
In my years helping financial institutions from our Columbus, Ohio and Charleston, WV offices, I've seen how a single incident can threaten a thriving business's survival.
Cybercriminals target financial institutions for a simple reason: that's where the money and high-value data are. These are not amateur attacks. Financial firms face threats from organized cybercrime syndicates, hacktivist groups making political statements, and nation-state actors seeking to destabilize markets.
The potential for direct financial gain is a powerful lure. Why steal credit card numbers when you can potentially access wire transfer systems? Our team's extensive cybersecurity training has shown us that these threats are evolving faster than ever. The Top 3 Cyber Threats Facing the Finance Industry are constantly morphing into more sophisticated variants. If you're in financial services, you are a priority target. The question isn't if you'll be attacked, but when.
The cyber threat landscape for financial institutions is dangerously complex. From our work with clients across Columbus, Ohio and Charleston, WV, we see a dramatic shift in the volume and sophistication of attacks. Cybersecurity for financial firms must now defend against an ever-expanding range of threats.

Electronic Crime (eCrime) continues to rise, with a staggering 76% increase in victims named on eCrime leak sites in 2023 compared to 2022. This highlights how data-theft extortion has become a primary criminal enterprise. Supply chain attacks have also changed the game, as a single compromised vendor can create a domino effect. Your security is only as strong as your weakest third-party connection, making third-party vendor risk a pressing concern.
External threats are constantly evolving with new, sophisticated variations.
Our team's extensive cybersecurity training confirms that defending against these threats requires Advanced Threat Protection Solutions that can adapt to new attack methods.
While external threats get headlines, internal risks can be just as damaging. Insider threats, whether malicious or accidental, are challenging because they originate from individuals with legitimate access. Recent reports show that 84% of companies suffered an identity-related breach, often from compromised credentials.
Third-party risk management is a major weakness for many, with 65% of organizations identifying it as their weakest security link. Cloud misconfigurations, such as publicly accessible storage buckets, are another leading cause of data breaches. The reality of weak vendor security means that maintaining consistent standards across your supply chain is a significant challenge. This is why we specialize in helping financial service providers, including our work with Cybersecurity Services for Accountants, to mitigate these complex risks.
Effective cybersecurity for financial firms requires a multi-layered defense, much like a medieval fortress. The most effective strategies combine several proven approaches. The Zero Trust model, which operates on the principle "never trust, always verify," has become the gold standard, requiring continuous verification for every user and device. This is often combined with a data-centric security approach, which protects sensitive information wherever it resides, and continuous monitoring to create a robust shield around your most valuable assets.
Our team's extensive cybersecurity training has shown that every strong security program rests on five pillars. Missing one can leave dangerous gaps.
From our offices in Columbus, Ohio and Charleston, WV, we've helped financial institutions strengthen these areas. For more details, see our guide on IT Security for Banks.
Identity has become the new security perimeter. You must verify and control every person and device accessing your systems.
Our technical team's experience shows these IAM components are most effective when integrated into a comprehensive strategy, as outlined in the FFIEC's guidance on Authentication and Access to Financial Institution Services and Systems.
The financial industry operates under intense regulatory scrutiny. Cybersecurity for financial firms is not just about fending off hackers—it's about meeting the strict expectations of multiple regulatory bodies. Our team's extensive cybersecurity training has shown that compliance is about building a foundation of trust with customers.The most effective approach involves proactive risk management and fostering a security-aware culture where everyone, from the board down, understands their role in protecting data.

The regulatory landscape can feel overwhelming, but several key frameworks provide a roadmap.
Our technically experienced staff helps firms steer these rules as part of our Cybersecurity Compliance Services.
Compliance is the starting point, but true security goes beyond the minimums. Based on our experience, these practices make the biggest difference:
These practices are key components of effective IT Security Incident Management.
The cybersecurity landscape moves incredibly fast, and cybersecurity for financial firms requires looking ahead to prepare for emerging threats. Cybercriminals are constantly upgrading their toolkits with AI-driven attacks, and future technologies like quantum computing could one day break today's encryption. Proactive preparation, including regular tabletop exercises to simulate cyber incidents, is no longer optional.
Artificial Intelligence is a double-edged sword. It offers powerful defensive tools but also arms cybercriminals with new weapons.
The Artificial Intelligence Risk Management Framework (AI RMF 1.0) offers guidance for navigating these risks. Our team's extensive cybersecurity training helps clients strategically invest in technology to keep pace.
No matter how strong your defenses are, you must assume an incident will eventually occur. A solid Incident Response Plan (IRP) is therefore absolutely critical.
Your IRP should be a well-rehearsed drill with clear steps for containment and eradication—stopping an attack's spread and removing the threat. The recovery phase focuses on restoring systems and data from clean backups to ensure business continuity. After the event, a thorough post-incident analysis is crucial to learn from the attack and strengthen your defenses.
Financial institutions also face strict regulatory notification requirements, such as those in the Computer-Security Incident Notification Final Rule, which mandate reporting significant incidents within specific timeframes. Regular practice and expert partnership can make all the difference. This is where IT Outsourcing for Banks can be invaluable, providing specialized knowledge and resources when you need them most.
Financial institutions are prime targets because they are a one-stop shop for cybercriminals. Cybersecurity for financial firms is critical because these organizations hold a unique combination of direct monetary assets and vast amounts of sensitive personal data like social security numbers and bank account details. This information can be used for direct theft, complex fraud, or sold on the dark web, offering attackers a high return on investment. The interconnected nature of the financial system also means a single breach can have widespread ripple effects, making it an attractive target.
A Zero Trust security model operates on the principle of "never trust, always verify." It discards the old idea of a trusted internal network and instead assumes that any user or device could be compromised. Every single access request is rigorously verified, regardless of its origin. This is crucial for banks because it prevents lateral movement by attackers. If one endpoint is breached, the attacker cannot easily move through the network. This approach minimizes the potential damage of a breach and helps meet strict regulatory compliance standards.
Robust cybersecurity is achievable for smaller institutions without a massive budget. The key is smart resource allocation and focusing on high-impact foundational controls like multi-factor authentication, regular backups, and strong access policies. Cloud-based security services also offer enterprise-grade tools on a subscription basis, making them more affordable.
However, the most effective strategy is often partnering with a specialized Managed Security Service Provider (MSSP). Our extensive cybersecurity training and technical experience allow us to provide smaller institutions access to highly trained experts and advanced security tools. From our offices in Columbus and Charleston, we help community banks and credit unions implement top-tier cybersecurity for financial firms at a fraction of the cost of building an in-house team.
The journey of cybersecurity for financial firms is a continuous process, not a final destination. In today's interconnected world, robust cybersecurity is a fundamental business necessity that underpins customer trust, reputation, and financial stability. The cost of a breach can exceed $6 million, and the regulatory landscape demands constant vigilance. The clear takeaway is that financial institutions must adopt a proactive, comprehensive defense strategy.
At Next Level Technologies, we understand these challenges because we steer them with our clients daily. From our offices in Columbus, Ohio, and Charleston, WV, our highly trained staff brings extensive cybersecurity training and technical experience to every partnership. We have seen how the right expertise can transform a firm's security posture.
Whether you are a large bank or a community credit union, the principles are the same: protect your assets by staying ahead of threats, continuously adapting your defenses, and implementing best practices. It's about building layered defenses and having an incident response plan ready for when an attack occurs.
The cybersecurity landscape will keep evolving, but with the right approach and expertise, your financial institution can thrive securely.
Don't leave your firm's security to chance. Let our team help you build the fortress-like defenses your institution deserves. Get expert Managed IT Services and Support and take the first step toward true peace of mind.
Master it service continuity management. Learn ITSCM objectives, components, and implementation to ensure business resilience and swift recovery.
March 9, 2026
Optimize IT spending & boost ROI with it cost management software. Gain visibility, cut waste, and drive strategic growth.
March 6, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
