Keep Your Books Safe: Simple Steps to Secure Your Accounting Network
August 20, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
August 20, 2025
Network security for accountants has become a business-critical priority as cyberattacks on accounting firms have skyrocketed by 300% since COVID-19 began. Your firm handles some of the most sensitive data imaginable - tax returns, payroll information, bank account details, and social security numbers - making you an attractive target for cybercriminals.
Here are the essential network security measures every accounting firm needs:
The consequences of inadequate security are severe. Data breaches can cost businesses an average of $4.2 million each, and accounting firms face additional risks including regulatory fines up to $100,000, loss of client trust, and potential lawsuits.
The reality is stark: 39% of UK businesses fell victim to cyber attacks last year, yet only 14% of small businesses have comprehensive security measures in place. Phishing attacks have increased by 50% in the past year, and sophisticated AI-powered threats are making traditional defenses obsolete.
As Steve Payerle, President of Next Level Technologies, I've spent over 15 years helping accounting firms in Columbus, Ohio and Charleston, WV implement robust network security for accountants solutions. Our team's extensive cybersecurity training and technical expertise have protected countless firms from the devastating impacts of cyber threats.
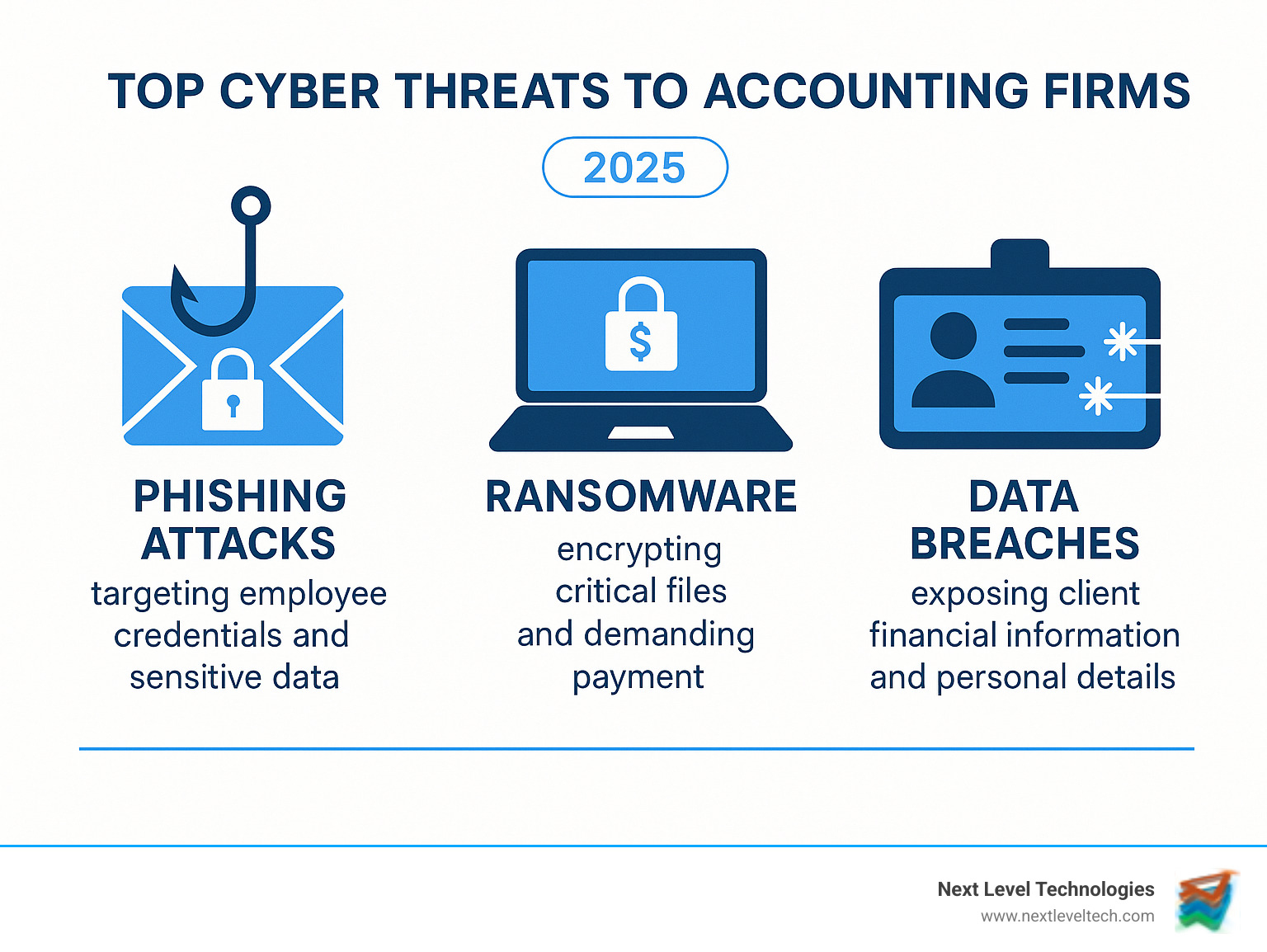
When we discuss network security for accountants, we're addressing the unique risks your firm faces. Unlike other businesses, your primary asset is a treasure trove of sensitive data—Social Security numbers, tax returns, payroll details, and corporate trade secrets—making you a prime target for hackers. Standard, off-the-shelf security simply isn't enough to protect this concentration of valuable information.
A breach can lead to devastating consequences beyond typical business disruptions, including severe regulatory penalties, massive financial loss, and irreparable harm to your reputation. The FTC Safeguards Rule, for example, mandates strict cybersecurity standards for firms like yours, with non-compliance fines reaching $100,000. At Next Level Technologies, our team's extensive cybersecurity training ensures we understand the nuances of IT Compliance for accountants, helping you meet and exceed these critical requirements.
Cyber threats are constantly evolving and becoming more targeted. Since COVID-19, attacks on accounting firms have surged by 300%, highlighting the industry's specific vulnerabilities.

Here are some of the most prevalent threats:
These threats underscore why understanding the Top 3 Cyber Threats Facing the Finance Industry is vital. Your firm's security is only as strong as its weakest link.
The consequences of a breach are catastrophic, extending far beyond immediate financial costs.
While understanding your Cyber Insurance Risk Assessment is important, prevention is key. The fallout from a single breach can be enough to put a firm out of business.
Think of network security for accountants as a multi-layered fortress protecting your most valuable asset: client data. A single lock isn't enough, and a proactive, layered defense is necessary to withstand sophisticated attacks.
At Next Level Technologies, our team's extensive cybersecurity training has helped accounting firms in Columbus, Ohio, and Charleston, WV, build these digital fortresses. We focus on implementing the right combination of technical controls that work together seamlessly. Our Cyber Security Services create a balanced defense strategy custom to your firm's operations.

A strong security foundation is critical for network security for accountants. These are the non-negotiable basics:
Remote work has expanded the security perimeter, making robust access controls for network security for accountants more important than ever.
A comprehensive backup and recovery plan is your ultimate safety net against data loss from hardware failure, disasters, or ransomware.
Effective network security for accountants requires these measures to work together as a cohesive system, protecting your firm without hindering operations.
A sobering truth: 82% of data breaches involve a human element. This isn't due to carelessness, but because cybercriminals are masters at exploiting human trust. Even with the best technology, your security is incomplete without well-trained employees, making them the cornerstone of effective network security for accountants.

Your employees are the gatekeepers of your digital fortress. With the right knowledge, they transform from a potential vulnerability into your strongest defense. At Next Level Technologies, our extensively trained cybersecurity team helps accounting practices in Columbus, Ohio, and Charleston, WV, empower their staff. As noted in Empowering employees with cybersecurity knowledge, trained staff can be the difference between a thwarted attack and a catastrophic breach.
Building a security-aware culture requires ongoing commitment.
Clear, written policies are the operating manual for your firm's security.
Cybersecurity isn't a one-and-done project; it's an ongoing process. The threat landscape evolves constantly, so your defenses must too. For network security for accountants, staying ahead means being proactive and performing regular check-ups, much like a thorough IT Internal Audit keeps your operations in order.
Keeping software updated is one of the most critical cybersecurity steps. Cybercriminals exploit outdated, unpatched software to gain access to sensitive data.
This includes keeping your Operating Systems (OS), software applications (accounting software, Microsoft Office), and security software (antivirus, firewalls) constantly updated with the latest security fixes and threat definitions. Even network hardware like routers needs firmware updates.
Manually updating everything is tedious and prone to error. Automated patch management ensures updates are applied promptly, while vulnerability scanning proactively identifies weaknesses. At Next Level Technologies, our highly-trained staff in Columbus, OH, and Charleston, WV, handle this through our Managed IT Services, taking this burden off your plate so you can focus on clients.
Regular audits are like a health check-up for your digital fortress, helping you find weaknesses before hackers do.
Network security for accountants requires ongoing attention, not a one-time fix. We recommend a tiered review schedule:
While major cloud platforms invest heavily in security, they operate on a shared responsibility model.
If your user-side settings are weak, your data can be compromised even if the cloud provider's infrastructure is solid. At Next Level Technologies, our team's extensive cybersecurity training helps clients implement Cloud Security Best Practices to properly secure their data.
Many small firms worry about the cost of robust network security for accountants, but the reality is that the cost of a breach is far greater than the cost of prevention. A single incident can lead to devastating fines, lawsuits, and reputational damage that could close your firm. Cybercriminals often target smaller businesses because they are perceived as easier targets.
The good news is that strong security is affordable and accessible.
The world of cybersecurity is a complex, constantly shifting landscape. For accounting firms, where protecting client data and trust is paramount, managing these challenges in-house can divert focus from your core mission. This is where partnering with an expert provides immense value.
At Next Level Technologies, we understand the unique regulatory and security challenges accounting firms face. Our mission is to simplify and secure your digital operations. Our highly-trained staff brings extensive cybersecurity training and deep technical experience from years of protecting sensitive financial data for businesses like yours in Columbus, Ohio, and Charleston, WV.
We offer comprehensive Managed IT Services and IT Support custom to accounting professionals. We proactively manage your IT infrastructure—from firewalls and encryption to backups and compliance—to ensure your network security for accountants is a robust digital fortress. This frees you to focus on what you do best: serving your clients, knowing their data is in safe, expert hands.
Don't leave your firm's reputation to chance. Partner with a team that has the expertise to protect your data, safeguard client trust, and secure your future.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
