Protecting Your Business Data: More Than Just a Firewall
November 11, 2025

Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026

Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026

Find the best Remote IT Support Business for your small business. Learn how to define needs, evaluate providers, and secure your tech.
February 6, 2026
November 11, 2025
Data protection and security is the practice of safeguarding sensitive information from loss, corruption, and unauthorized access. Many businesses believe a firewall is enough protection. It's not. A single vulnerability—a misconfigured system, an untrained employee, or outdated software—can expose your most valuable asset and lead to devastating consequences.
Critical Statistics:
True data protection and security requires a layered approach combining people, processes, and technology. You need reliable backup systems, employees who can spot threats, and policies that protect data throughout its lifecycle. The regulatory landscape (GDPR, CCPA, HIPAA) adds another layer of complexity, where non-compliance can shut down your business.
With the right strategy, you can protect your data, maintain compliance, and focus on growth. I'm Steve Payerle, President of Next Level Technologies. For over 15 years, I've helped businesses in Columbus, Ohio, and Charleston, WV, implement effective data protection and security strategies. Our highly trained cybersecurity team has a proven track record of preventing breaches and recovering from disasters through proactive monitoring and expert guidance.
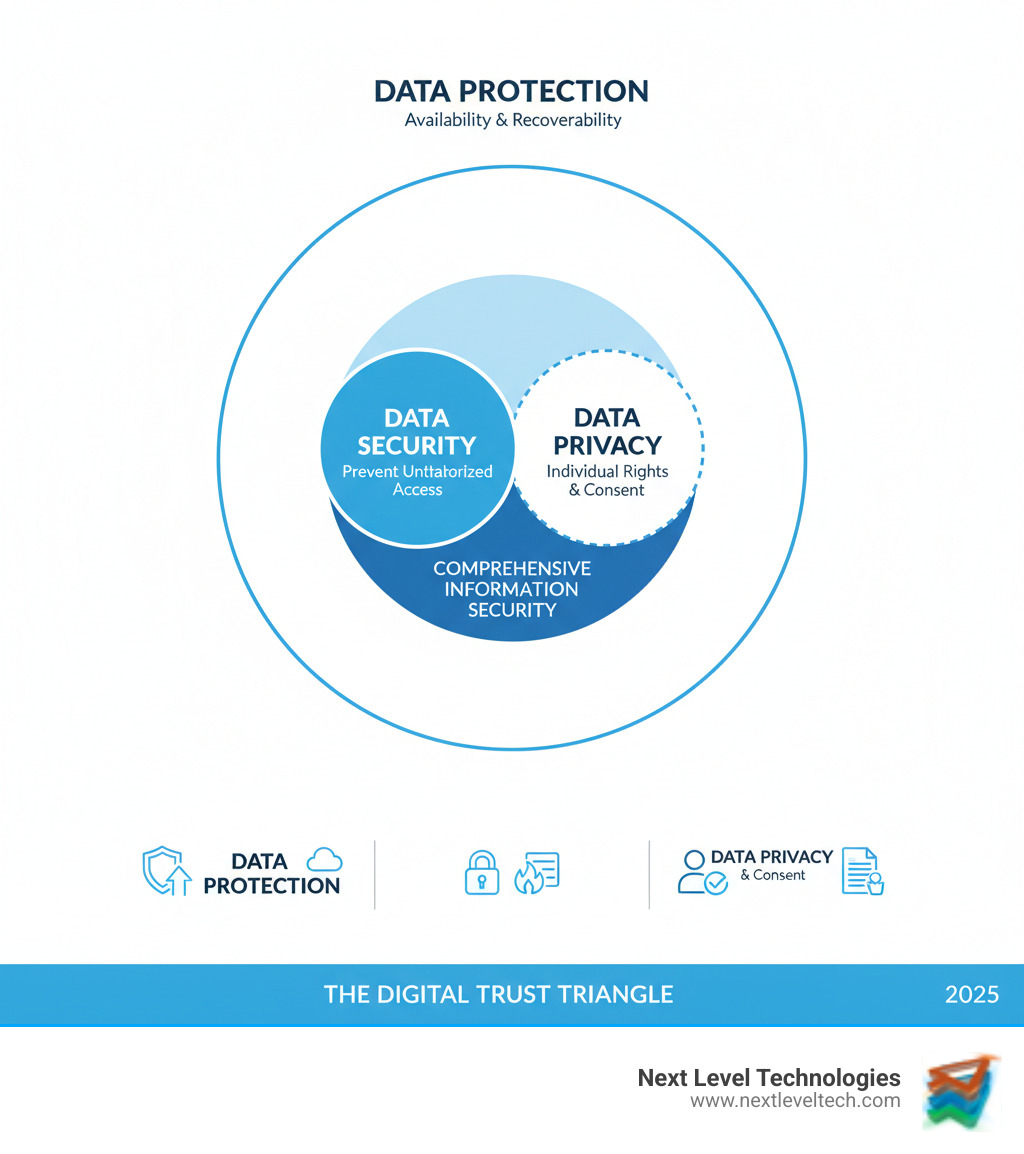
While often used interchangeably, data protection, security, and privacy are distinct concepts that form the foundation of a comprehensive information security strategy. Understanding their unique roles is the first step toward building an effective defense for your business.
| Attribute | Data Protection | Data Security | Data Privacy |
|---|---|---|---|
| Definition | Safeguarding information from loss or corruption, ensuring its availability. | Protecting data from unauthorized access, theft, or alteration. | An individual's right to control how their personal data is collected, used, and shared. |
| Scope | Broad: Encompasses security, privacy, availability, backups, and disaster recovery. | Narrow: A subset of data protection focused on preventing breaches. | A subset of both, focused on individual rights and compliance. |
| Primary Goal | Ensure data availability, integrity, and recoverability. | Prevent unauthorized access and safeguard confidentiality (CIA triad). | Grant individuals control over their personal information and govern data access policies. |
| Key Techniques | Backups, replication, disaster recovery (DRaaS), data lifecycle management. | Encryption, access controls (MFA), firewalls, antivirus, SIEM, data loss prevention (DLP). | Consent management, data minimization, anonymization, data subject access requests, privacy policies. |
Data protection is your business's comprehensive strategy to ensure data remains available, accurate, and usable—no matter what. It addresses threats beyond malicious actors, such as accidental deletions, server crashes, or natural disasters. Through business continuity and disaster recovery (BCDR) planning, data protection ensures you can get back to business quickly after an incident. The stakes are high: the average cost of a data breach reached USD 4.45 million in 2023. Beyond the financial hit, reputation damage and regulatory requirements can cripple a business. A solid data protection plan is the difference between a minor inconvenience and a company-ending catastrophe.
Data security and data privacy are key components of data protection. Data security focuses on preventing unauthorized access with technical controls like firewalls, encryption, and strong authentication. It asks: "How do we keep threats out?"
Data privacy, in contrast, focuses on individual rights and responsible data collection policies. It establishes rules for what data you collect, why you collect it, and who can see it. It asks: "Do we have permission to use this data, and are we using it responsibly?" For example, security ensures only authorized staff can access a customer database, while privacy ensures they use that data only for legitimate, consented purposes. Our extensively trained team in Columbus, OH, and Charleston, WV, helps businesses implement both, ensuring you are technically secure, compliant, and respectful of individual rights.
Effective data protection and security is like building a fortress with multiple layers of defense. This approach starts with foundational principles and builds up to practical, everyday actions that protect your business.
Every solid security strategy is built on the CIA Triad: Confidentiality, Integrity, and Availability.
Beyond the triad, a risk-based approach helps focus protection efforts where they matter most, ensuring security measures are appropriate for the risks you face, as noted in the ICO's A guide to data security.
Transform principles into practice with these essential steps:
For small businesses, start with these five practices:
Protecting your data isn't just about stopping hackers; it's about complying with a complex web of laws. Failure to do so is a major business risk that requires clear data handling policies and, for many, a dedicated Data Protection Officer (DPO).

Three major regulations shape the global landscape:
Our cybersecurity team has extensive training across these and other compliance frameworks, like PCI-DSS for payment data, and can help businesses in Columbus, OH, and Charleston, WV, determine which regulations apply to them.
Ignoring data protection and security regulations can be financially catastrophic. The consequences are severe and immediate:
Compliance isn't just about avoiding fines; it's about protecting your business's stability and reputation. Our teams in Columbus, Ohio, and Charleston, WV, have deep compliance expertise to guide you safely through this minefield.
The cyber threat landscape is constantly evolving, so your defenses must too. Building a modern fortress requires assembling the right tools and staying ahead of emerging trends in data protection and security.

These tools form the layers of your defense strategy:
Our team in Columbus, Ohio, and Charleston, WV, has extensive experience implementing these technologies. To learn more, IBM offers free resources to expand your skills with free security tutorials.
Stay ahead of what's next:
Our highly trained staff stays current on these trends to ensure your defenses are always prepared for the next threat.
Business owners often have pressing questions about data protection and security. Here are straightforward answers to the most common ones we hear.
While all business data has value, certain types carry higher risk and are governed by specific laws. You must prioritize protecting:
Our cybersecurity team in Columbus, Ohio, and Charleston, WV, has extensive training in classifying and protecting all these data types.
Building a plan is a step-by-step process. Start with a solid foundation and build from there:
Before you invest in any security tool, you must answer one question: What data do you have, and where is it? You cannot protect what you don't know exists. The first step is to conduct a data inventory and classification. This process involves identifying all the data your organization collects and stores, categorizing it by sensitivity (e.g., public, confidential, restricted), and mapping its location across servers, cloud services, and employee devices. This foundational knowledge allows you to make informed, prioritized decisions about your data protection and security strategy. Our extensively trained cybersecurity staff can guide you through this critical first step.
We've covered the essentials of data protection and security, from core principles and best practices to navigating complex regulations. The message is clear: protecting your data requires a holistic strategy, proactive defenses, and strict compliance.
You started your business to pursue your passion, not to become a cybersecurity expert. Managing this complexity shouldn't be a second full-time job. That's where Next Level Technologies steps in. For over 15 years, our highly trained cybersecurity team has protected businesses like yours in Columbus, Ohio, and Charleston, WV. We understand your challenges and are here to provide peace of mind.
We become an extension of your team, handling risk assessments, implementing custom technologies, and training your staff. We manage the 24/7 monitoring, threat intelligence, and compliance so you can focus on growth. The cost of a breach—averaging $4.45 million plus reputational damage—is too high to ignore. Protecting your business isn't optional; it's essential.
Ready to take data protection and security seriously without it taking over your life? Get comprehensive managed IT services and support and let our experts build a resilient digital fortress around your most valuable assets.
Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026
Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
