Secure IT Company Guide: Because Cybersecurity Isn't Optional
July 18, 2025

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026

Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026

Protect your data. Learn how cloud backup services for business ensure recovery, continuity, and security for your enterprise.
March 3, 2026
July 18, 2025
A secure it company is a specialized managed service provider focused on protecting businesses from cyber threats while maintaining their technology infrastructure. Going beyond basic IT support, they offer comprehensive cybersecurity solutions, including 24/7 threat monitoring, advanced security tools, compliance support (HIPAA, PCI DSS), data backup, and employee training.
The numbers tell a stark story. With 60% of cyber threats now coming from sources beyond traditional endpoints, businesses face an expanding attack surface that requires specialized expertise. For mid-sized businesses, partnering with a secure IT company isn't just about fixing problems—it's about preventing them. These providers offer the technical expertise and extensive cybersecurity training that most internal IT teams can't match.
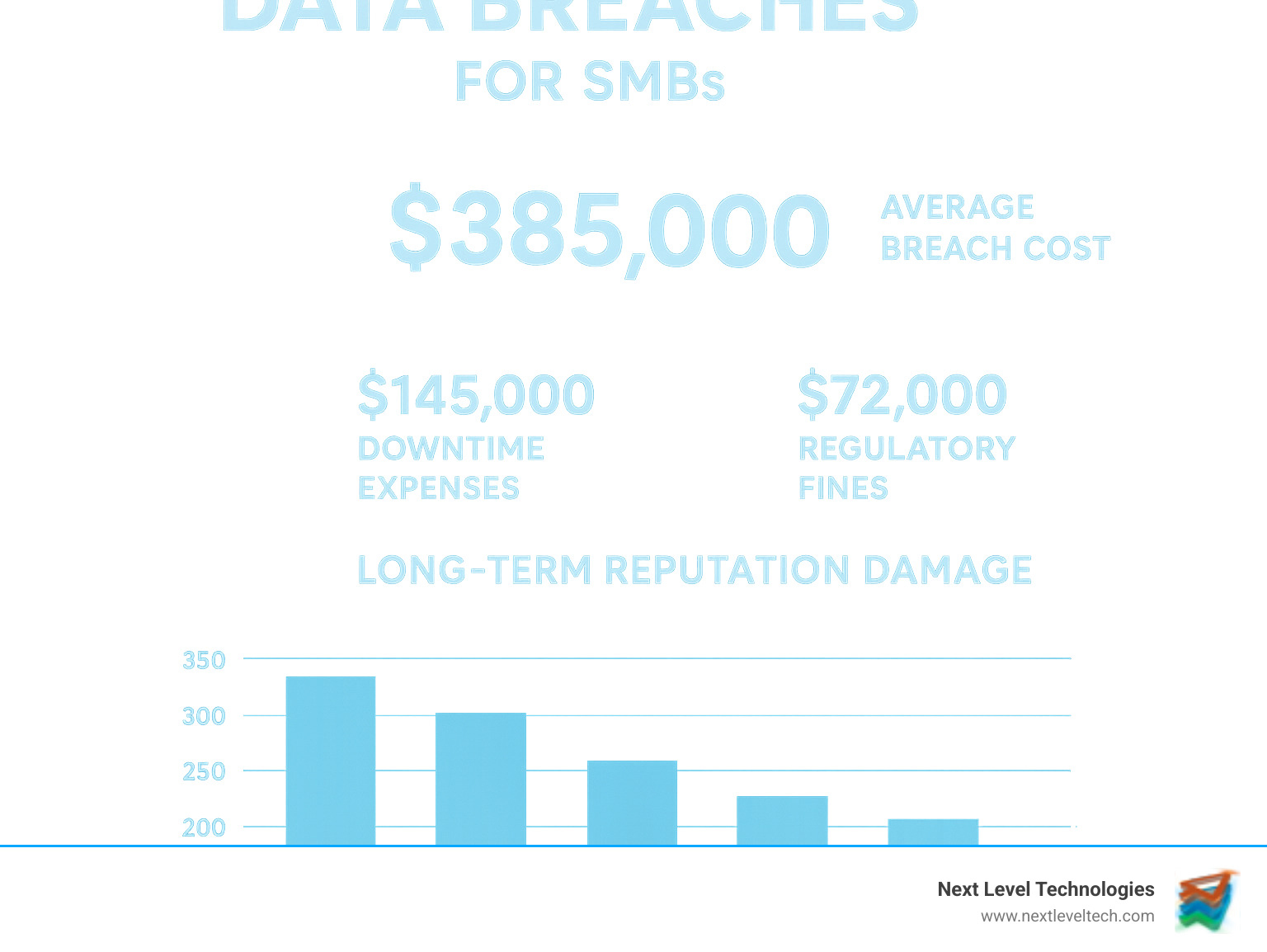
The stakes are higher than ever. Data breaches can cost millions in lost revenue, fines, and reputation damage, while the threat landscape grows more complex daily.
I'm Steve Payerle, President of Next Level Technologies. For over a decade, I've helped businesses in Columbus, Ohio, and Charleston, WV, understand what makes a secure it company effective. My team has seen how the right security partnership transforms a business from reactive firefighting to proactive protection.
Easy secure it company glossary:
Think of a secure it company as your business's digital bodyguard—always watching and ready to act. While a regular IT support company fixes problems after they happen, a secure it company focuses on stopping them before they start. Their primary mission is proactive defense. They constantly scan for threats, update security measures, and build stronger digital walls around your business. This approach to risk management ensures business continuity even when cyber criminals are working overtime. For a secure it company, security is a core function, woven into everything they do.
A secure it company focuses on threat mitigation through extensive cybersecurity training and technical expertise. Their teams study the latest attack methods to stay one step ahead, allowing them to spot potential problems that might slip past less specialized providers. Compliance adherence is another crucial area. Whether your business needs to follow HIPAA, PCI, or other regulations, a secure it company has the expertise to guide you. The best providers adopt Security by Design, building protection into every system from the ground up. This approach creates a true strategic partnership, where your provider is invested in your long-term success. For more details, see our post on IT Security Incident Management.
A secure it company serves a wide range of clients, but small and medium businesses (SMBs) are prime beneficiaries, gaining enterprise-level protection without the cost of a full internal security team. Industries with strict requirements, like government contractors, healthcare, finance, and legal firms, also rely on their specialized services. These businesses, whether in Columbus, OH, and Charleston, WV, or elsewhere, need protection that understands their unique challenges. Highly regulated industries particularly benefit because these providers have the technical experience to steer complex compliance requirements. At Next Level Technologies, our team's extensive cybersecurity training allows us to tailor our approach to businesses across all these sectors.

A top secure it company uses a layered defense, like a medieval castle with multiple walls of protection. Our team at Next Level Technologies combines cutting-edge technology with continuous threat intelligence and 24/7 monitoring to stay ahead of the ever-changing cybersecurity landscape.
A solid security strategy starts with robust threat management. Our cybersecurity-trained staff brings years of technical experience to implement these essential services:
Beyond the foundation, a leading secure it company offers advanced solutions. Our extensive cybersecurity training enables us to handle sophisticated challenges:
Technology alone isn't enough; human error can undermine the best systems. That's why we focus heavily on the human element:
Finding the right secure it company is a critical business decision that requires careful vetting. You're not just hiring a vendor; you're building a long-term partnership. Choose right, and you'll gain peace of mind knowing your business is protected by proven technical expertise.
Dig deeper than website promises. Look for years in business, as longevity often indicates reliability. Industry certifications among staff represent proven knowledge from hundreds of hours of training. At Next Level Technologies, our team's extensive cybersecurity training ensures we're ready for emerging threats. Case studies and client testimonials provide real-world proof of their capabilities. Finally, ensure the staff has deep technical experience to handle complex challenges. For context, see this archived resource on foundational network security principles.
What separates the pros from the pretenders is their approach and technology. Look for a proactive versus reactive approach—do they hunt for threats or just fix broken systems? Modern security relies on AI and automation to detect threats in seconds, not hours. Integrated security platforms (XDR) unify security data across your entire environment for a complete view. The gold standard is a Zero Trust architecture, which assumes no user or device is automatically trusted. A commitment to avoiding vendor lock-in also shows they prioritize your needs. Find More info about Cloud IT Security on our site.
The cybersecurity world changes daily, and your partner must be agile. They need to adapt to evolving threats and update your defenses immediately. Staying current with regulations is also crucial to avoid hefty fines. Your provider should offer scalable solutions that grow with your business and customized service plans that fit your unique challenges and budget. Our team in Columbus, Ohio, and Charleston, WV, understands that adaptability is essential for keeping your business safe. For practical guidance, check out our 10 Cybersecurity Tips for Small Businesses.

Partnering with a secure it company is a strategic investment that delivers tangible business advantages. Every dollar spent on proactive cybersecurity can save thousands in breach costs, downtime, and lost productivity. Businesses that invest in security see measurable returns through improved efficiency and reduced risk.
The most immediate benefit is a dramatically improved security posture. With 24/7 protection, a team of experts watches over your systems around the clock. This leads to drastically reduced threat dwell time—the critical window between when a threat enters your system and when it's neutralized. Our team's extensive cybersecurity training allows us to shrink this window from hours to seconds. This directly minimizes the risk of data breaches. You also gain access to specialized skills and technical experience that would be too costly to hire in-house. We provide comprehensive Cybersecurity Services in Columbus that bring enterprise-level protection to organizations of all sizes.
A secure it company also boosts your operational efficiency. Reduced downtime from proactive monitoring means less lost productivity and revenue. You'll see lowered capital expenditure on security tools, as you leverage your partner's infrastructure instead of buying your own. Predictable monthly costs make budgeting easier by eliminating surprise repair bills. Most importantly, it frees up your internal staff to focus on core business goals instead of putting out security fires. The automation of security tasks like patching and updates saves countless hours and reduces the risk of human error, allowing you to focus on growing your business.
After years of working with clients across Columbus, Ohio and Charleston, WV, I've heard the same questions from businesses considering a secure it company. Here are the straight answers you deserve.
The cost depends on your specific needs. Key factors include the size and complexity of your business and the scope of services required. A small firm has different needs than a large company with multiple locations. Most providers offer service tiers, often with per-user or per-device pricing. At Next Level Technologies, we create custom packages so you only pay for what you need. While there is an upfront investment, the cost of inaction—a data breach, fines, and downtime—is almost always far greater. It's about investing in your business's future and peace of mind.
Absolutely. This co-managed IT model is a popular and effective approach. A secure it company can augment your internal staff by handling specialized, time-consuming cybersecurity tasks like 24/7 monitoring, threat hunting, and compliance management. This collaboration allows your team, who knows your business inside and out, to focus on daily support and strategic initiatives while we bring specialized security expertise to the table. We fill the skill gaps your team may have in complex areas like cloud security or specific compliance frameworks, providing them with strategic support.
Taking the first step is simple and starts with a conversation. We begin with a free, no-obligation initial consultation to understand your business, IT setup, and biggest concerns. From there, we typically recommend a comprehensive risk assessment and vulnerability scan to get a clear, honest picture of your current security posture. This network assessment gives us a baseline to identify immediate concerns. Finally, we work with you to develop a security roadmap—a clear, step-by-step plan with recommended solutions and realistic timelines. Our team's extensive cybersecurity training and technical experience mean we can translate complex concepts into practical business decisions. Ready to start? Our Managed Cybersecurity Services are designed to guide you through this process seamlessly.

Think of cybersecurity not as an expense, but as your business's secret weapon. When you partner with a secure it company, you're investing in confidence, growth, and the freedom to focus on your goals. At Next Level Technologies, we've seen businesses in Columbus, Ohio, and Charleston, WV, transform from worrying about threats to pursuing new opportunities with confidence.
A proactive stance on security is smart business. It means recognizing that threats are a matter of when, not if. By making security your strongest asset, you create a stable foundation for sustainable growth and gain invaluable peace of mind. When you know your digital assets are protected by professionals with extensive cybersecurity training and technical experience, you can focus your energy on innovation and customer service.
Future-proofing your business means having a strategic partner who understands the evolving threat landscape. Ready to take the next step? Exploring comprehensive Managed IT Services and IT Support is the critical move toward achieving true peace of mind and turning your biggest concern into your greatest competitive advantage.
Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
