Hardware Security: Your Unbreakable Digital Shield
September 3, 2025

Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026

Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026

Protect your data. Learn how cloud backup services for business ensure recovery, continuity, and security for your enterprise.
March 3, 2026
September 3, 2025
Computer security hardware solutions are physical devices designed to protect your business systems at the foundational level, below the operating system where software-based threats can't reach. These solutions range from network appliances like firewalls to endpoint hardware like Trusted Platform Modules (TPMs) and specialized Hardware Security Modules (HSMs).
The urgency for hardware-based security has never been greater. A recent study revealed that 63% of organizations encountered at least one data breach resulting from hardware security vulnerabilities in the previous year. As one cybersecurity expert puts it: "Hardware-based cybersecurity isn't merely an option—it's imperative."
Unlike software that can be bypassed by attacks targeting firmware or system-level vulnerabilities, hardware security creates an immutable root of trust that protects your entire technology stack from the ground up.
I'm Steve Payerle, President of Next Level Technologies. Over the past 15 years, my team's extensive cybersecurity training has helped hundreds of businesses implement computer security hardware solutions as part of comprehensive managed IT strategies. We've seen that the most resilient businesses combine both hardware and software defenses to create an unbreakable digital shield.
Simple guide to computer security hardware solutions terms:
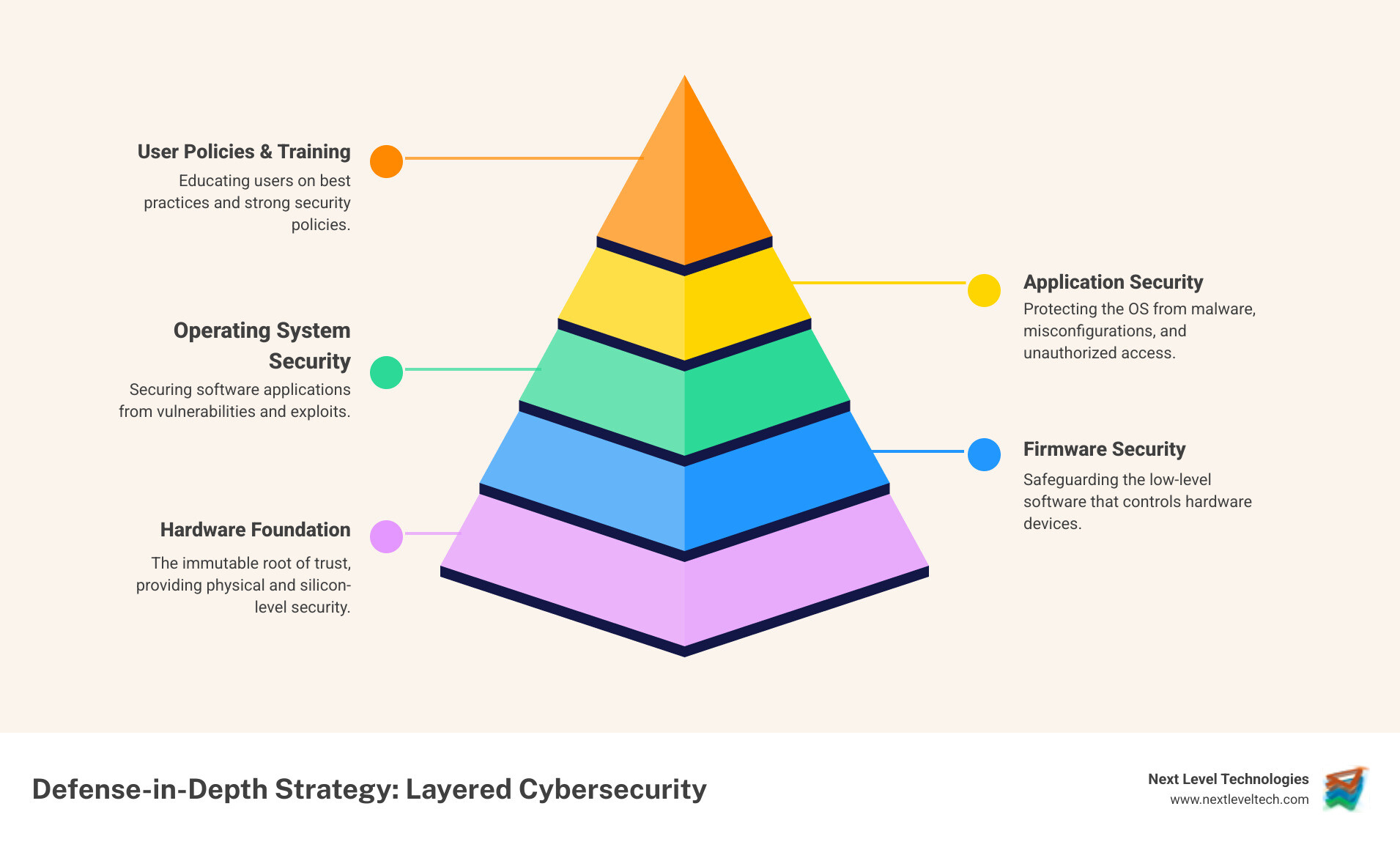
Imagine your business security as a fortress. Software-based security includes guards at the gates, while hardware-based security is the stone foundation itself. Both are essential for a defense-in-depth strategy, but a compromised foundation makes the best guards useless.
Hardware-based cybersecurity operates at the physical layer, built into silicon chips and specialized devices. It exists before your computer even loads its operating system. In contrast, software-based cybersecurity like antivirus programs runs on top of the OS, meaning it can only protect what it can "see" after the system is already running.
Computer security hardware solutions offer unique advantages. Tamper resistance means devices are physically designed to detect unauthorized access. Performance benefits occur because dedicated hardware can handle demanding tasks like encryption without slowing down your main systems. Most importantly, hardware provides isolation from software vulnerabilities, remaining protected even if attackers bypass your software defenses.
Our team's extensive cybersecurity training has shown us that businesses with both layers of protection are far more resilient. Each makes the other more effective.
| Feature | Hardware-Based Security | Software-Based Security |
|---|---|---|
| Primary Focus | Physical isolation, tamper-resistance, protects below-OS | Protects OS/applications, flexible configuration |
| Layer of Operation | Physical, firmware, boot process | Operating system, application, network layer |
| Vulnerability | Physical attacks, supply chain compromises, side-channel | Malware, exploits, zero-days, requires regular updates |
| Performance | Can offer performance boosts by offloading tasks | Can consume system resources |
| Flexibility | Less flexible, requires physical changes | Highly flexible, easily updated/configured |
| Root of Trust | Creates an immutable, foundational trust | Relies on the underlying hardware's integrity |
Today's cyber criminals are targeting your foundation. Below-OS attacks are a fundamental shift, injecting malicious code into your device's firmware before the operating system even starts. Your computer boots up trusting this corrupted code, and your antivirus software, which relies on the OS, never even sees the threat.
Advanced rootkits embed themselves so deeply in firmware that they become nearly invisible to traditional software tools. Supply chain vulnerabilities add another risk, as malicious components can be introduced during manufacturing. Once a compromised device is in your office, no amount of software can fix its untrustworthy foundation. Furthermore, software cannot prevent physical tampering or side-channel attacks that analyze power consumption to steal encryption keys.
Even the best antivirus software struggles with zero-day attacks—brand new threats that don't match known patterns. The cybersecurity professionals at Next Level Technologies have seen these evolving threats impact businesses in Columbus, Ohio, and Charleston, WV. The solution isn't to abandon software, but to build a more complete defense.
A root of trust is the one component in your security system you can absolutely count on to be uncompromised. Silicon-level security provides this by building security features directly into processor chips, where they cannot be altered by software.
The secure boot process acts as a security checkpoint at startup, cryptographically verifying the digital signature of each piece of code before it loads. If anything is amiss, the system won't start. This verification happens in isolated execution environments that remain separate and secure even if the main OS is compromised. This reliable device identity, or immutable identity, becomes the foundation upon which all other security layers are built, creating a far more resilient security posture.

Computer security hardware solutions provide multiple layers of defense for your digital infrastructure. These are not passive gadgets but active digital guards working around the clock. At Next Level Technologies, our extensively trained cybersecurity professionals have deployed these solutions for businesses in Columbus, Ohio and Charleston, WV, demonstrating how the right hardware prevents devastating breaches. Understanding these tools is crucial for building a solid IT Infrastructure for Small Business.
Your network perimeter requires robust protection. Network security hardware creates multiple checkpoints for all data entering or leaving your systems.
These dedicated appliances are also essential components of any comprehensive Hardware Backup Solutions strategy.
While network security protects the perimeter, endpoint hardware secures the devices your team uses daily, right down to the chip level.
If other hardware solutions are the guards, Hardware Security Modules (HSMs) are the vault for your most sensitive cryptographic keys. These are tamper-resistant physical devices designed for secure key management and cryptographic operations.
HSMs excel at cryptographic key management, handling the entire lifecycle of digital keys—generation, storage, and use—in a highly secure environment. They also perform digital signing to ensure the authenticity of software and transactions, and encryption offloading to free up server resources. Modern HSMs are crypto-agile, preparing for future threats like post-quantum cryptography, and provide a quantum-safe foundation for industries ranging from finance to government.

Implementing computer security hardware solutions requires careful planning and technical expertise. At Next Level Technologies, our team's extensive cybersecurity training has taught us that success lies in understanding how these tools fit into your specific business goals and technology ecosystem. Simply buying hardware is not enough; proper implementation is key.
Our experience serving businesses in Columbus, Ohio, and Charleston, WV, highlights several critical steps for a successful implementation:
Different industries face unique security challenges, and computer security hardware solutions provide custom protection that software alone cannot.
The cybersecurity landscape is constantly evolving, and the future of computer security hardware solutions is about creating smarter, more proactive systems. Through our extensive cybersecurity training at Next Level Technologies, we see a shift from reactive defenses to intelligent hardware that can predict and prevent attacks.
The next wave of hardware security is focused on staying ahead of sophisticated attackers.
Artificial intelligence is a double-edged sword in cybersecurity, making hardware-based AI security critical.
When it comes to computer security hardware solutions, we hear certain questions from business owners repeatedly. After 15 years of implementing these measures, our team at Next Level Technologies has developed extensive cybersecurity training to address these common concerns. Here are the answers to the most frequent questions we encounter.
A hardware firewall is a dedicated physical appliance that sits at the edge of your network, inspecting all incoming and outgoing traffic to protect every device connected to it. It offers robust, high-performance protection for the entire network. A software firewall is a program installed on an individual computer, protecting only that single device and using its processing power. Hardware firewalls provide a strong perimeter defense, while software firewalls offer endpoint-specific protection.
No single solution can stop every attack. However, computer security hardware solutions provide a critical foundational layer of protection that is extremely difficult for attackers to bypass, especially against threats that target firmware or operate below the OS. The most effective approach is a defense-in-depth strategy, layering hardware security with software protection, strong security policies, and employee training. Hardware security provides the unshakeable foundation that makes all other security measures more effective.
This is a common misconception. Hardware-based security is essential for businesses of all sizes. Most modern business computers already include Trusted Platform Modules (TPMs), a form of hardware security that simply needs to be properly configured. Furthermore, affordable solutions like hardware security keys and small business-grade hardware firewalls provide powerful protection against common threats like phishing and network intrusions. Cyber threats don't discriminate by company size, and our IT Support for Small Businesses helps make these enterprise-grade solutions accessible and affordable for everyone.
Computer security hardware solutions are not an IT expense; they are the unshakeable foundation of your business's digital infrastructure. From the silicon-level security in your chips to the dedicated firewalls at your network perimeter, these physical defenses provide a layer of protection that software alone cannot replicate, operating where traditional security tools can't reach.
However, owning the right hardware is only half the battle. Proper implementation and integration into a cohesive security strategy are critical. This is where our extensive cybersecurity training and hands-on experience make the difference. The team at Next Level Technologies doesn't just install devices; we configure them to provide maximum protection for your specific business needs.
We have helped hundreds of businesses in Columbus, Ohio, and Charleston, WV, build these unbreakable digital shields. Our cybersecurity professionals possess the deep technical expertise to assess your risks and implement the right mix of hardware and software solutions.
As threats grow more sophisticated, a strong defense is non-negotiable. With the right combination of hardware-based security and expert guidance, you can build a resilient security posture that keeps your business safe. Ready to take your cybersecurity to the next level? Contact us to learn more about our managed IT services and IT support and how we can help you build the digital shield your business deserves.
Create a strategic it plan for small business success. Learn to secure data, optimize tech, and future-proof your operations.
March 5, 2026
Unlock local deals on LSN.com! Learn to buy, sell, and navigate your local sales network safely. Support community commerce now.
March 4, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
