Navigating the Digital Minefield: A Guide to IT Risk Management and Compliance
January 27, 2026

Master Computer Hardware Solutions to boost business performance & security. Troubleshoot issues & plan smart upgrades.
January 28, 2026

Master IT risk management & compliance. Learn to identify, assess, mitigate, and monitor digital threats for business security.
January 27, 2026

Secure your future! Discover essential small business IT strategies, cybersecurity, and expert support to thrive in the digital age.
January 26, 2026
January 27, 2026
IT risk management is the systematic process of identifying, assessing, mitigating, and continuously monitoring risks to your organization's information technology systems and data. The goal is to protect your organization's ability to perform its mission by balancing the costs of protective measures against their potential impact, ultimately reducing risk to an acceptable level.
Key components of this process include:
In today's digital era, your reliance on IT systems makes risk management critical for protecting your entire operation. The stakes are high—the average cost of a data breach in the US reached $9.44 million in 2022.
Effective IT risk management helps you make informed decisions about your security budget, ensures compliance with regulations like HIPAA or FTC Safeguards, and can even uncover operational inefficiencies. It's both a shield and a tool for business improvement.
However, IT risk is a moving target. New threats emerge, and your business evolves. That's why risk management isn't a one-time project—it's an ongoing process that must adapt to the changing landscape.
I'm Steve Payerle, President of Next Level Technologies, and since founding our company in 2009, I've helped businesses across Ohio and West Virginia implement comprehensive IT risk management programs that protect their operations while enabling growth. Our team's extensive cybersecurity training and technical experience have shown us that the most successful organizations view IT risk management not as a burden, but as a strategic advantage.
Essential it risk management terms:
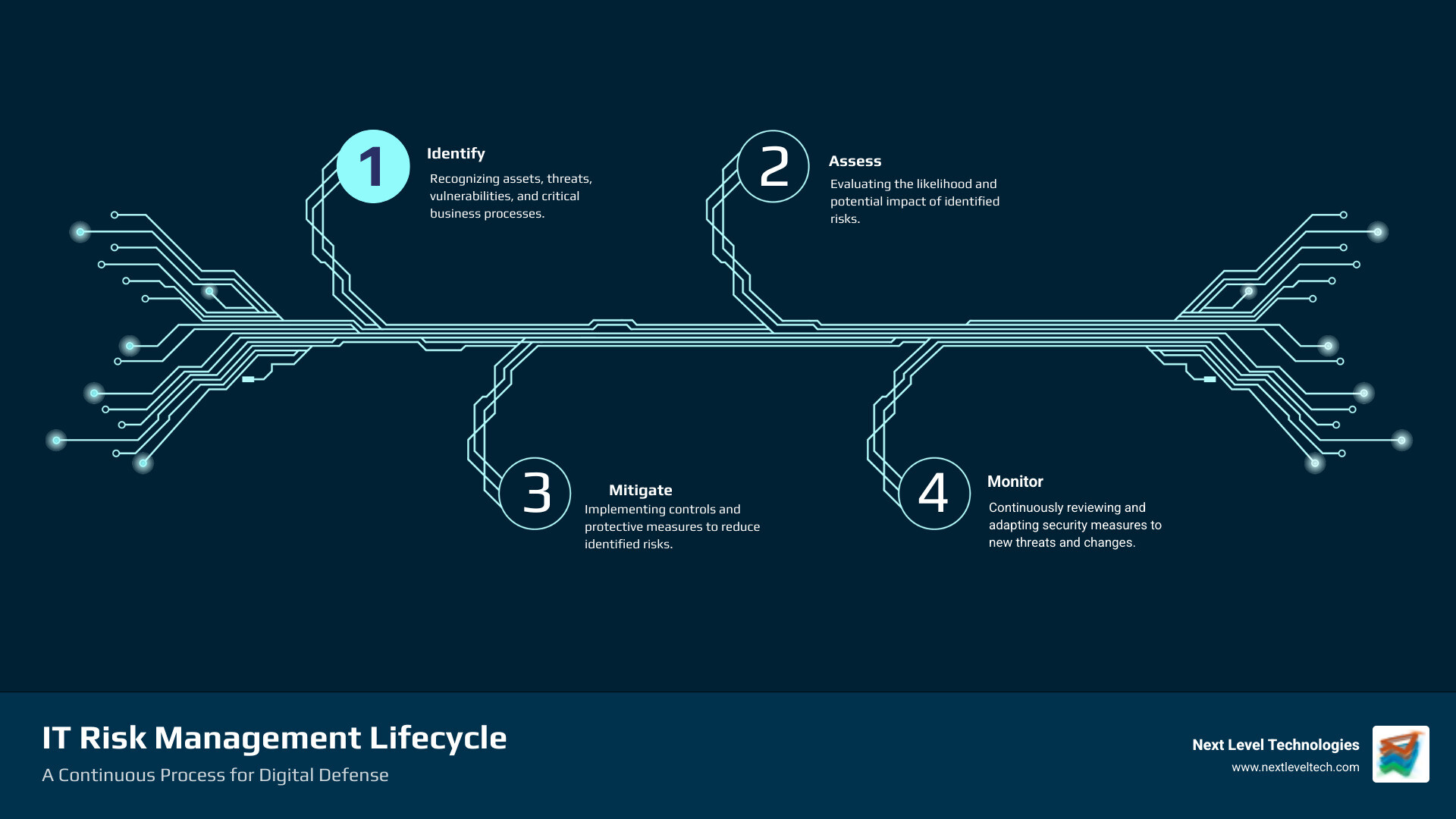
At its heart, IT risk management is a continuous, four-phase cycle designed to protect your organization's ability to operate. It's not a one-time fix but an ongoing process of identifying, assessing, and mitigating threats.

Ready to build a robust defense system for your IT? Explore our IT Risk Management Solutions.
Think of risk assessment as your reconnaissance mission. Before you can defend, you need to know what you're up against. This critical component of IT risk management provides a snapshot of assessed risks at specific points in time, forming the foundation for ongoing risk management.
Our methodology for conducting an IT risk assessment typically involves these primary steps:
This systematic approach ensures we don't miss anything. For a deeper dive into identifying and analyzing potential weaknesses, check out our guide on Threat Modeling and Risk Analysis. You can also refer to NIST's Guide for Conducting Risk Assessments.
Once we've identified and assessed the risks, it's time to act. Risk mitigation involves prioritizing and implementing risk-reducing measures to bring risk to an acceptable level, balancing protection costs with your mission.
There are several strategies we can employ for risk mitigation:
| Strategy | Description -| Risk Acceptance | Acknowledging a risk and deciding not to take any action, often because the cost of mitigation outweighs the potential impact. -| Risk Avoidance | Eliminating the risk by ceasing the activity that causes it. For example, discontinuing a service or not adopting a new technology. -| Risk Transference | Shifting the risk to a third party, such as through insurance or outsourcing specific functions. -| Risk Mitigation | Implementing controls and countermeasures to reduce the likelihood or impact of a risk. This is the most common strategy. -
After choosing a strategy, we implement controls, which can be technical (firewalls), administrative (policies), or physical (locks). The goal is to reduce residual risk—the risk remaining after controls are applied—to an acceptable level.
Effective IT risk management isn't just an IT department task; it's a core business function. By integrating risk management into your overall strategy, you can make your business more resilient, efficient, and prepared for the future. This approach helps streamline operations, enables better-informed decisions, and shifts your posture from reactive to proactive.
At Next Level Technologies, our team's deep technical experience helps businesses in Ohio and West Virginia integrate IT risk into their larger organizational framework, turning security into a strategic advantage. Learn more about our approach with our Cybersecurity Audit and Compliance Solutions.
For enterprises, IT risk management is a critical component of a broader Enterprise Risk Management (ERM) framework. The increasing frequency and sophistication of cybersecurity attacks mean that IT risks must be considered alongside financial, operational, and legal risks.
Integrating IT risk management with ERM provides a holistic view of all business risks, ensuring that technology-related threats are understood in the context of your overall business objectives. Using tools like ICT risk registers, we can translate technical risks into business-relevant terms, facilitating better decision-making at the executive level. This approach is detailed in NIST's publication on Integrating Cybersecurity and Enterprise Risk Management (ERM).
One of the most effective ways to manage IT risk is to build security in from the ground up. Integrating security into the Systems Development Life Cycle (SDLC) means addressing potential vulnerabilities at every stage, from design to deployment and maintenance. This "security by design" approach is far more cost-effective than fixing issues after a system is live.
By making security an integral part of the SDLC, we ensure that new systems and applications are resilient against threats from day one. For more detailed guidance on this, consult NIST's publication on Security Considerations in the System Development Life Cycle.
Navigating the complexities of IT risk management can be challenging. Fortunately, various frameworks and standards provide a structured approach to help organizations systematically identify, assess, and mitigate risks. These guidelines serve as best practices and benchmarks for demonstrating compliance and a commitment to robust security.
Our team at Next Level Technologies leverages these resources, combined with our extensive cybersecurity training and technical experience, to provide custom solutions for businesses in Ohio and West Virginia. Adopting a recognized framework also aids in your Cybersecurity Compliance Services journey.
Here are some of the most widely recognized frameworks:
Organizations often blend elements from multiple frameworks to create a custom approach. For more details on the NIST RMF, you can refer to their Risk Management Framework for Information Systems and Organizations.
While essential, it's important to recognize the limitations of any risk management strategy. One common criticism is the subjectivity inherent in many assessments, particularly when estimating the likelihood and impact of threats. Furthermore, IT risk management can sometimes overlook the human factor, as human error or negligence can circumvent even the most robust technical controls.
Despite these limitations, a structured approach to IT risk management remains the most effective way to address digital threats. Our role at Next Level Technologies is to apply these methodologies with a pragmatic understanding of their nuances, using our technical expertise to minimize subjectivity and provide the clearest possible picture of your risk landscape.
We often hear similar questions from businesses in Charleston, WV, and Columbus, OH, about IT risk management. Here are some quick answers:
Think of cybersecurity as a key part of the broader field of IT risk management.
Effective IT risk management is achievable for any size business. The key is to be smart and strategic:
A risk register is a central document used to track all identified risks. It's crucial for effective IT risk management because it:
Essentially, it's the master plan for your risk management strategy.
The digital landscape is complex and ever-changing, a true minefield for businesses trying to focus on growth and innovation. Navigating these challenges—from sophisticated cyber threats to stringent regulatory requirements—demands not just technology, but deep expertise and a proactive, strategic approach to IT risk management.
At Next Level Technologies, we understand these demands intimately. Our team, comprised of highly trained staff with extensive cybersecurity training and technical experience, is dedicated to helping businesses throughout Ohio and West Virginia (including Columbus and Charleston) protect their operations, achieve compliance, and optimize their IT infrastructure.
We don't just react to problems; we help you build a resilient, secure foundation. Our approach involves:
Your mission is our priority. Let us be your trusted partner in securing your digital future, allowing you to focus on what you do best—growing your business.
Ready to take your IT security to the next level? Visit us at https://www.nextleveltech.com to learn how we can help.
Master Computer Hardware Solutions to boost business performance & security. Troubleshoot issues & plan smart upgrades.
January 28, 2026
Secure your future! Discover essential small business IT strategies, cybersecurity, and expert support to thrive in the digital age.
January 26, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
