Keeping Your Apps Happy: The Lowdown on Incident Management
January 14, 2026

Unlock business growth with robust b2b it support. Prevent downtime, boost productivity, and secure your tech. Learn how to choose your ideal IT partner.
February 28, 2026

Secure your law firm's data, ensure compliance & boost efficiency with expert IT support for legal services. Protect your practice.
February 27, 2026

Master the challenges of an it support it career. Learn to become an IT support specialist, gain skills, and advance your tech journey.
February 26, 2026
January 14, 2026
Application incident management is the end-to-end process of detecting, responding to, and resolving unplanned interruptions or service degradations in your business applications. It's how your team handles everything from a slow login page to a complete system outage—minimizing downtime, protecting your reputation, and keeping customers happy.
Quick Definition:
Your applications are the focal point of business performance and customer satisfaction. When they go down or slow to a crawl, the impact is immediate and costly. Beyond the direct financial hit, you risk damaging customer relationships, losing competitive ground, and facing potential compliance issues—especially in regulated industries like finance and healthcare.
Think about it: a single outage doesn't just stop revenue. It creates a cascade of problems. Your support team gets flooded with calls. Customers take to social media. Your team scrambles without clear direction. And if you're in healthcare, patient care could be at risk.
The good news? Organizations with a solid incident management process can cut their Mean Time To Resolve (MTTR) by over 80 percent. They minimize user impact, coordinate faster responses, and most importantly—they learn from each incident to prevent it from happening again.
I'm Steve Payerle, President of Next Level Technologies in Columbus, Ohio and Charleston, WV, where we've helped dozens of mid-sized businesses build robust Application incident management processes that keep their systems running smoothly. Our team's extensive cybersecurity training and hands-on experience mean we've seen every type of incident—and know exactly how to respond.
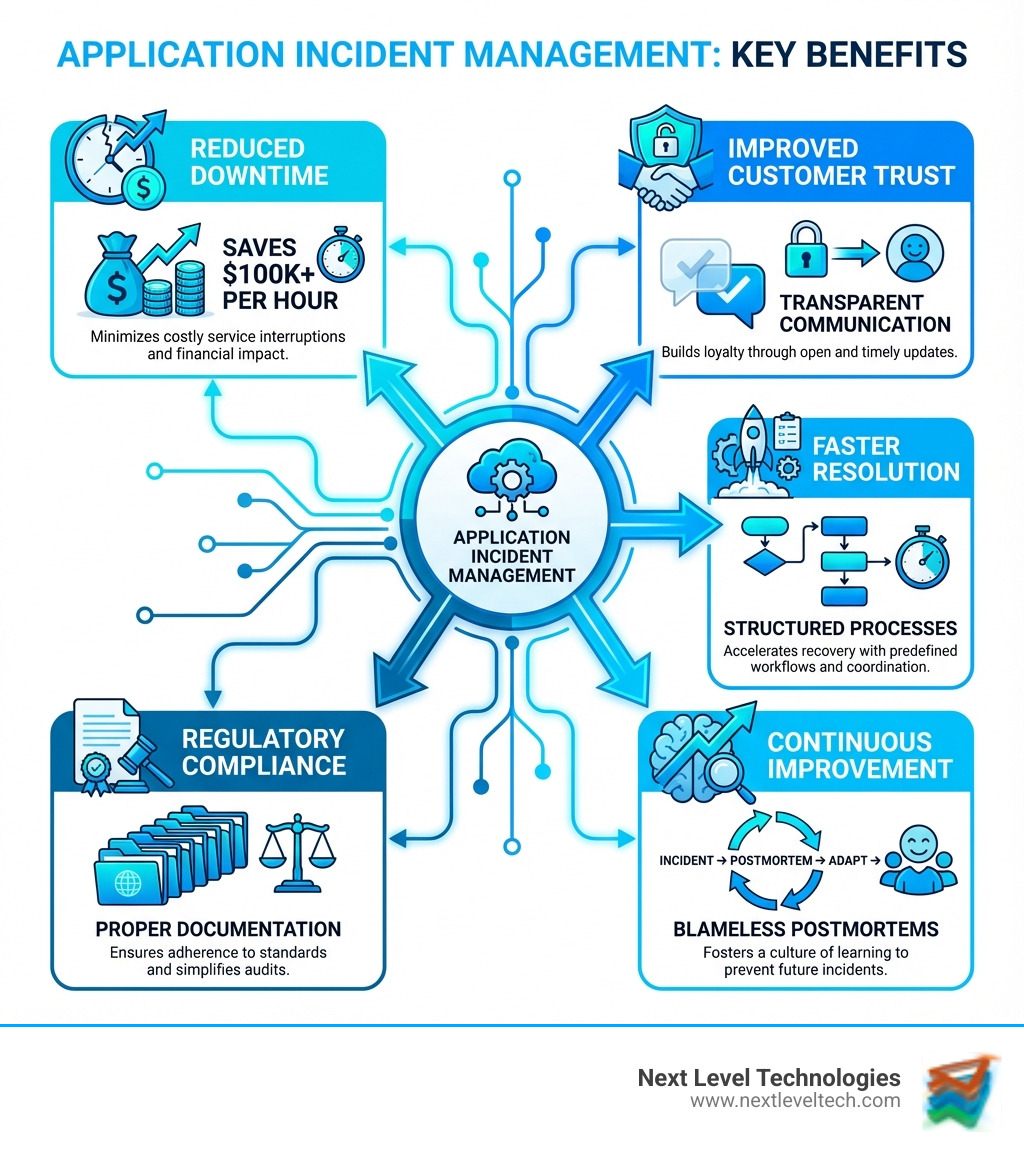
Effective Application incident management isn't just about putting out fires; it's about having a well-rehearsed plan to tackle any unexpected blaze, big or small. The incident lifecycle provides this structured response, guiding your team from the moment a problem appears until it's fully resolved and lessons are learned. Our goal is always to minimize disruption and ensure your Business Continuity IT Solutions remain strong, even when things go sideways.

The incident lifecycle can be broken down into three crucial stages: Detection, Classification, and Alerting; Triage, Response, and Resolution; and finally, Communication and Post-Incident Review. Each stage plays a vital role in ensuring a swift and coordinated response, which is key to minimizing the financial impact of downtime and maintaining customer trust.
This is where the alarm bells first ring. An incident can't be resolved if it's not detected! Modern organizations rely heavily on automated monitoring systems to continuously observe application performance, user experience, and underlying infrastructure. These systems are designed to identify anomalies or deviations from normal behavior.
However, not all alerts are created equal. A good alerting mechanism should be:
Once an incident is detected, it needs to be classified. This involves assigning predefined data fields and event tags to the incident, which helps in grouping similar issues and identifying patterns. For example, categorizing an incident as 'Network' with a subcategory of 'Network Outage'. This classification feeds into the prioritization matrix, where we weigh the incident's impact (how many users or systems are affected) against its urgency (how quickly it needs to be resolved). A critical incident might affect many users and require immediate attention, while a low-priority incident might only affect a single internal staff member with no user interruption. This structured approach helps us leverage data to proactively identify and address potential incidents before they escalate, ensuring our resources are always focused on the most critical issues.
With an incident detected, classified, and prioritized, it's time for action. Triage is the initial assessment to determine the scope and immediate steps. This often involves assigning the incident to the appropriate team or individual based on routing and escalation policies.
The response phase then kicks in, starting with an initial diagnosis. Our teams, backed by extensive cybersecurity training, will investigate and diagnose the issue. This is where the magic of problem-solving happens, but it's important to remember a key principle: mitigation over root cause. When an application is down or severely degraded, our first priority is to restore service and minimize user impact. This might involve applying a quick fix, such as rolling back a recent code change or switching to a backup system. The deeper root cause analysis can—and often should—wait until service is restored. Having generic mitigations ready to go can significantly speed up recovery and keep our customers happier.
Once a fix is applied and service is restored, the incident can be closed. For a deeper dive into these processes, check out our IT Incident Management Complete Guide.
An incident isn't truly over until everyone who needs to know, knows, and everyone has learned from the experience. Communication during an incident is paramount, both internally and externally. Internally, seamless collaboration between departments is essential. Externally, transparent and active communication builds trust. We use status pages (like McGill's System Status page) and regular updates to keep users and stakeholders informed, even if it's just to say, "We're aware and working on it."
After the dust settles, the most valuable part of the lifecycle begins: the post-incident review (PIR), often called a postmortem. This detailed review identifies the root cause, contributing factors, and, most importantly, the lessons learned. The key here is a blameless culture. Instead of pointing fingers, we focus on improving systems, procedures, and training. This approach encourages open reporting and ensures that individuals feel safe sharing what happened, allowing us to address systemic issues and prevent similar incidents in the future. Corrective action items are then identified from these postmortems and integrated into our team's backlog, driving continuous improvement in our Application incident management processes.
Behind every successful incident response is a well-oiled team. It’s not just about technical prowess; it’s about clear roles, shared understanding, and a culture that fosters learning over blame. At Next Level Technologies in Columbus, OH and Charleston, WV, we believe a strong team, equipped with extensive cybersecurity training, is your best defense.

Inspired by emergency response frameworks like the Incident Command System (ICS), effective Application incident management teams adopt specific roles to maintain order during chaos. The "three Cs" of incident management are to Coordinate, Communicate, and Control, and these roles help us achieve that:
Each role has distinct responsibilities, preventing confusion and ensuring everyone knows their part when an incident strikes. This clear structure is vital when working under pressure.
Perhaps one of the most powerful tools in modern Application incident management is a blameless culture. When an incident occurs, it's easy to look for someone to blame. However, this only leads to fear of reporting and obscures the true, often systemic, issues.
A blameless culture, as championed by DevOps and SRE philosophies, shifts the focus from "who caused it?" to "what can we learn?" It encourages open reporting and transparency in postmortem analysis. By ensuring individuals can report incidents without fear of retribution, organizations can uncover the real contributing factors – be they process flaws, tool shortcomings, or training gaps. This approach helps us address systemic issues, make meaningful improvements, and ultimately prevent future incidents. Our team, with its extensive cybersecurity training, is committed to this philosophy, understanding that learning from failure is the fastest path to greater resilience.
The landscape of IT has evolved dramatically, and so too has Application incident management. While traditional ITIL (Information Technology Infrastructure Library) provided a foundational framework, modern approaches like DevOps and Site Reliability Engineering (SRE) have introduced new philosophies custom for today's agile, cloud-native environments.
A core tenet of DevOps and SRE is the "you build it, you run it" philosophy. This means the team that develops a service is also responsible for its operation and, crucially, for fixing it if it breaks. This approach fosters a deep sense of ownership and accountability, leading to more robust and resilient applications.
For teams running global services, agility and speed are paramount. Any downtime can affect thousands of organizations, not just one. DevOps teams focus on finding more efficient ways to build, test, and deploy software, which inherently requires addressing incidents quickly. This often involves a heavy reliance on automation for provisioning, incident prioritization, and even AI-enabled root-cause analysis tools.
This approach thrives in environments with microservices architectures and continuous integration/continuous deployment (CI/CD) pipelines, where rapid changes are common. The goal is to optimize system performance, accelerate resolution, and prevent future incidents. While ITIL still provides valuable frameworks for overall IT Service Management (ITSM), DevOps and SRE emphasize a more integrated, continuous improvement cycle for incident handling.
These two terms are often used interchangeably, but in IT, they serve distinct purposes. Understanding the difference is crucial for effective IT operations.
While distinct, incident and problem management are deeply intertwined. Every incident is a potential symptom of an underlying problem. Effective Application incident management relies on robust problem management to ensure that incidents don't keep happening.
In the world of digital services, relying solely on human intervention for Application incident management is like bringing a knife to a gunfight. Modern tools and automation are indispensable for streamlining detection, response, and resolution. Our Cybersecurity Services leverage these advanced capabilities to keep your applications secure and operational.
Automation is a game-changer in incident management. It reduces manual effort, speeds up response times, and ensures consistency. We're talking about sophisticated systems that can:
These automated capabilities not only streamline the process but also free up our human experts, particularly those with extensive cybersecurity training, to focus on the more complex, novel, or critical incidents that require nuanced judgment.
To truly improve our Application incident management processes, we need to measure them. Metrics provide objective insights into our performance and highlight areas for improvement. Here are some of the most important:
By consistently tracking these metrics, we can continuously refine our processes, demonstrate the value of our incident management efforts, and proactively address weaknesses in our systems.
We get a lot of questions about how to best manage application incidents. Here are some of the most common ones we hear from businesses in Columbus, OH and Charleston, WV:
Preparation is the cornerstone of effective Application incident management. It's not a question of if an incident will happen, but when. Organizations can prepare by:
These proactive steps build confidence and ensure a swift, coordinated response when an actual incident occurs.
The most important aspect of communication during an incident, both internally and externally, is clarity, consistency, and timeliness. When an application is down or struggling, anxiety runs high. Providing regular, honest updates—even if you don't have a full resolution yet—is crucial.
Customers want to know you're aware of the problem and actively working on it. Silence can be interpreted as indifference.
Alert fatigue is a significant challenge where responders become desensitized to constant notifications, leading to missed critical alerts. We overcome this by:
By making alerts more intelligent and relevant, we ensure our teams can respond effectively to genuine incidents.
In today's interconnected digital world, Application incident management is not just an IT function; it's a critical business imperative. From minimizing costly downtime (which can easily exceed $100,000 per hour for a single server) to safeguarding customer trust and ensuring regulatory compliance, a robust incident management strategy is foundational to modern organizational success.
We've explored the essential lifecycle, from the crucial stages of detection and resolution to the vital importance of communication and post-incident learning. We've highlighted how modern approaches like DevOps and SRE, with their "you build it, you run it" philosophy and focus on automation, are changing incident response. And we've emphasized the human element: building a skilled team, defining clear roles, and fostering a blameless culture where learning from incidents drives continuous improvement.
At Next Level Technologies, serving businesses in Columbus, OH, and Charleston, WV, we understand that effective Application incident management is a blend of proactive preparation, structured response, and continuous learning. Our team's extensive technical experience and deep cybersecurity training mean we're not just reacting to incidents; we're helping you build resilient systems and processes that prevent them.
Ready to stop fearing the next outage and start building a truly resilient application environment? Let us help you take your incident management to the next level. Explore our Managed IT Services and IT Support to see how we can keep your applications happy and your business thriving.
Unlock business growth with robust b2b it support. Prevent downtime, boost productivity, and secure your tech. Learn how to choose your ideal IT partner.
February 28, 2026
Secure your law firm's data, ensure compliance & boost efficiency with expert IT support for legal services. Protect your practice.
February 27, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
