What the Heck is SOC 1 Compliance Anyway?
July 24, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
July 24, 2025
SOC 1 compliance is a framework that demonstrates your organization has proper internal controls over financial reporting when providing services that could impact your clients' financial statements. If you're a service organization like a payroll processor, data center, or SaaS provider, your clients may require you to obtain a SOC 1 report to prove your controls are working effectively.
Quick Answer: What You Need to Know About SOC 1 Compliance
Many business owners get confused by the technical jargon around SOC reports. The reality is simpler than it seems - if your service could affect how your clients report their finances, you probably need SOC 1 compliance to keep those clients happy and win new business.
As Steve Payerle, President of Next Level Technologies, I've helped numerous businesses in Columbus, Ohio and Charleston, WV steer SOC 1 compliance requirements while strengthening their IT infrastructure. Our team's extensive cybersecurity training and technical experience has shown us that proper IT controls are often the foundation of successful compliance efforts.
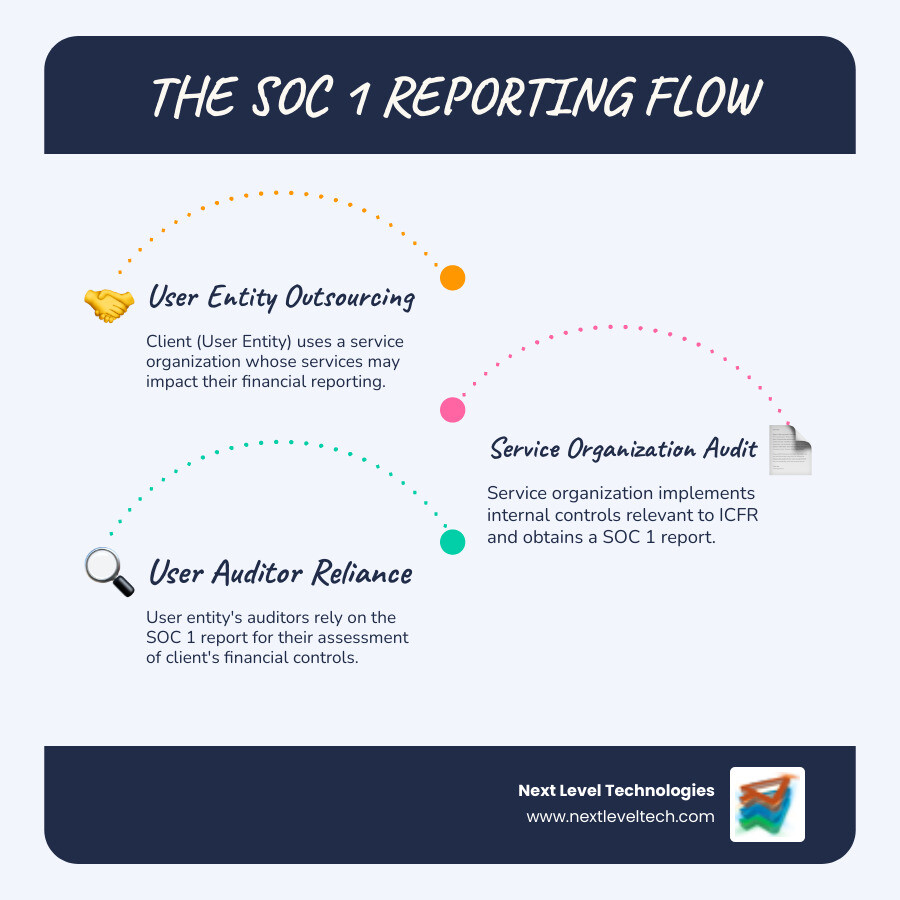
Imagine your company outsources payroll. When audit season arrives, how do you prove your payroll provider has controls to prevent errors on your financial statements? This is where SOC 1 compliance is essential.
SOC 1 (System and Organization Controls 1) is an independent audit report for service organizations. It examines whether a service provider has the right controls in place to handle your financial data properly, acting as a third-party validation of their processes.

The purpose of a SOC 1 report is risk mitigation. It provides assurance that a vendor's internal controls won't let errors slip through and affect your financial reporting. SOC 1 is the modern version of the former SAS 70 report, now governed by the Statement on Standards for Attestation Engagements (SSAE) No. 18, which evolves as business complexity grows.
If your services could impact a client's financial statements, you likely need SOC 1 compliance. This applies to:
The driving force is usually client demand. Clients need to satisfy their own auditors, and if they can't prove your controls are solid, they may find a new vendor.
Achieving SOC 1 compliance strengthens your business from the inside out.
According to PwC's Global Compliance Survey 2025, 77% of executives report negative impacts from compliance issues. A solid SOC 1 report helps you avoid this.
At Next Level Technologies, we've seen how strong IT controls form the foundation of successful compliance. Our team's extensive cybersecurity training and technical experience in Columbus, Ohio and Charleston, WV has helped many service organizations build the IT infrastructure needed to pass these audits.
When you're exploring SOC 1 compliance for your business, you'll quickly find there are two main types of reports to choose from: Type 1 and Type 2. Think of it like choosing between a snapshot and a movie - both tell a story, but one gives you a much richer picture over time.
Both types of SOC 1 reports are issued by a Certified Public Accountant (CPA) firm as official attestation reports. Each report includes the auditor's opinion, management's assertion about their controls, detailed control objectives, and the results of any testing performed. These aren't public documents - they're confidential reports typically shared only with your clients (user entities) and their auditors, often under a Non-Disclosure Agreement because of the sensitive financial information they contain.
Here's something important to remember: your SOC 1 report has a shelf life. It's generally valid for 12 months from the date it's issued. To keep your compliance current and avoid any gaps in coverage, you'll want to start planning your next audit before the current report expires. Sometimes, if there's a short gap between reports, your auditor might issue a bridge letter - essentially a brief statement confirming that nothing material changed in your control environment during that short period (usually three months or less).
A SOC 1 Type 1 report is like taking a detailed photograph of your control environment on a specific date. The auditor examines whether your controls are properly designed and suitable for achieving their intended objectives - but they don't test whether those controls actually work in practice over time.
This type of report focuses on answering one key question: "If these controls were operating as designed, would they effectively address the risks they're supposed to handle?" It's essentially a readiness assessment that many organizations use as their first step into SOC 1 compliance.
The Type 1 audit process is typically faster and less complex than its Type 2 counterpart. Most well-prepared organizations can complete a Type 1 audit in 2-4 months. This makes it an attractive option for companies that need to demonstrate they have proper controls in place quickly, or for those who want to identify and fix any gaps before committing to the more extensive Type 2 process.
However, there's a trade-off for this speed and simplicity: lower assurance. While a Type 1 report shows you have good controls on paper, it doesn't prove they're working effectively day-to-day. It's like having blueprints for a secure building - they might look perfect, but you haven't actually tested whether the building can withstand real-world challenges.
If Type 1 is a snapshot, then a SOC 1 Type 2 report is a comprehensive documentary. This report evaluates not just whether your controls are well-designed, but also whether they're operating effectively over an extended period - typically 6 to 12 months.
During a Type 2 audit, the auditor doesn't just look at your control documentation. They collect evidence of how your controls actually functioned throughout the entire review period. They might examine logs, interview staff multiple times, observe processes in action, and test samples of transactions from different months to ensure consistency.
This extended observation period is why Type 2 audits typically take 6-12 months to complete from start to finish. The auditor needs time to observe your controls in action across different scenarios and time periods.
The payoff for this additional time and effort is higher assurance and significantly more value to your clients. User entities and their financial auditors strongly prefer Type 2 reports because they demonstrate that your controls don't just look good on paper - they actually work consistently over time. For many larger clients, a Type 2 report isn't just preferred; it's required.
At Next Level Technologies, our team's extensive cybersecurity training has shown us that the Type 2 process, while more demanding, often reveals important insights about how IT controls perform under real-world conditions. This makes it the gold standard for organizations serious about SOC 1 compliance.
| Feature | SOC 1 Type 1 Report | SOC 1 Type 2 Report |
|---|---|---|
| Report Focus | Design of controls and suitability | Design of controls and operating effectiveness |
| Timeframe | As of a specific date (a "snapshot") | Over a period of time (typically 6-12 months) |
| Level of Assurance | Lower; confirms controls are designed well | Higher; confirms controls are designed well AND are working effectively over time |
| Typical Use Case | Initial audit; internal assessment; demonstrating readiness; for clients with less stringent requirements | Ongoing compliance; for clients requiring high assurance; preferred by financial auditors |
The choice between Type 1 and Type 2 often comes down to your specific business needs, client requirements, and timeline. Many organizations start with Type 1 to establish their foundation, then move to Type 2 for ongoing compliance and maximum client confidence.
Achieving SOC 1 compliance requires planning and dedication, but the process is manageable when broken down. At Next Level Technologies, our team's extensive cybersecurity training and technical expertise helps businesses strengthen the critical IT General Controls (ITGCs) that are often pivotal for a successful SOC 1 audit.

The audit is handled by a CPA firm that evaluates two main areas: your IT General Controls (system access, change management, operations monitoring) and your Business Process Controls (procedures for handling client financial data). The goal is to build a culture of continuous monitoring where strong controls become second nature.
Preparing for your first SOC 1 audit involves several key steps:
SOC 1 compliance is an ongoing commitment, not a one-time project.
The world of SOC reports can sometimes feel like a confusing alphabet soup. While we've deep-dived into SOC 1 compliance, it's important to understand how it differs from its cousins, SOC 2 and SOC 3, so you can choose the right report for your specific needs. The numbers (1, 2, 3) don't indicate a hierarchy or that one is "better" than another; they simply represent different focuses and audiences.

Think of it this way: financial controls versus security controls. That's the main difference between SOC 1 and SOC 2. The report audience and report distribution also vary significantly, which affects how you can use each report in your business.
At Next Level Technologies, our extensive cybersecurity training and technical experience means we often help businesses in Columbus, Ohio and Charleston, WV understand which report they actually need. It's not uncommon for companies to think they need one type when they actually need another - or sometimes both!
SOC 1 compliance is all about Internal Controls over Financial Reporting (ICFR). If your service could mess up your client's financial statements, this is your report. It's designed specifically for service organizations whose services have a direct impact on their clients' financial statements.
The purpose is straightforward: to assure user entities and their financial auditors that your controls over financial data processing are rock solid. When a payroll company processes employee wages or a loan servicing company handles payment processing, these activities directly affect their clients' books.
The intended audience for SOC 1 reports is primarily user entities and their CPA firms (the "user auditors"). These are the folks who need to know that your financial controls won't cause problems during their own financial audits.
Report distribution is tightly controlled. SOC 1 reports are restricted use reports, meaning they're private documents shared only with specific, authorized parties. You'll typically sign NDAs before sharing these reports because they contain sensitive information about your internal controls.
SOC 2 reports take a completely different angle. Instead of worrying about financial reporting, they focus on how well you protect and handle customer data. These reports evaluate controls based on the Trust Services Criteria, which cover five key areas.
Security is the foundation - it's required for all SOC 2 reports and covers protection against unauthorized access. Availability ensures your system works when it's supposed to work. Processing integrity means your system processes data completely, accurately, and on time. Confidentiality protects information that's supposed to stay secret. Privacy ensures personal information is handled properly throughout its entire lifecycle.
The broader audience for SOC 2 reports includes potential customers, regulators, business partners, and internal management. If you're a SaaS provider or cloud service company, customers will often ask for your SOC 2 report before they'll trust you with their data.
Like SOC 1, SOC 2 reports are typically restricted use and shared under NDA due to the detailed and sensitive information they contain about your controls. Here's something important to remember: you don't need a SOC 1 report before getting a SOC 2. They address different concerns and can be pursued independently or at the same time if your business needs both.
SOC 3 reports are like the marketing-friendly version of SOC 2. They evaluate the same Trust Services Criteria as SOC 2, but they're designed for public consumption. Think of it as a high-level summary that gives people confidence without revealing your secret sauce.
The purpose is to provide general assurance about your security and operational controls without the detailed, sensitive information found in a SOC 2 report. It's perfect for companies that want to publicly demonstrate their commitment to security.
SOC 3 reports are general use reports, which means they can be freely distributed. Many companies use them as a marketing tool - you've probably seen "SOC 3 certified" badges on websites. Unlike SOC 1 or SOC 2 reports, SOC 3 reports don't include detailed descriptions of tests or results, making them safe for public consumption.
The decision usually comes down to this: if your service directly affects your client's financial statements, SOC 1 compliance is your go-to. If you handle customer data and need to prove strong security controls, SOC 2 is likely what you need. If you want a public badge of honor for your security efforts, SOC 3 is the winner.
Many organizations, especially in the IT and cloud service space, find themselves needing both SOC 1 and SOC 2 reports to satisfy different client requirements. It might seem like overkill, but different clients care about different things - some worry about their financial audits, others worry about data breaches.
We've taken quite a journey together through SOC 1 compliance, haven't we? From understanding what it actually means to breaking down the differences between Type 1 and Type 2 reports, exploring the audit process, and comparing it with other SOC reports - you now have the roadmap to steer this complex but essential business requirement.
Here's the bottom line: SOC 1 compliance is fundamentally about trust. When your clients outsource critical financial processes to you, they need confidence that you're handling their data with the same care they would. A SOC 1 report provides that formal assurance, demonstrating that your internal controls over financial reporting are not just adequate, but genuinely effective.
The secret sauce to successful SOC 1 compliance often comes down to having rock-solid IT controls in place. This is where the rubber meets the road, and frankly, where many organizations stumble. Your IT General Controls (ITGCs) form the backbone of your entire compliance framework - from access management and change controls to system monitoring and data backup procedures.
At Next Level Technologies, our team's extensive cybersecurity training and deep technical expertise has shown us time and again how critical these IT foundations are. Whether we're working with businesses in Columbus, Ohio or Charleston, WV, we see the same pattern: organizations with strong IT infrastructure find their compliance journey much smoother and more cost-effective.
Think about it - if your systems aren't properly secured, if your access controls are loose, or if your change management processes are informal, you're setting yourself up for audit findings and potentially costly remediation efforts. But when your IT house is in order, compliance becomes a natural extension of good business practices rather than a scramble to meet requirements.
The beauty of partnering with a managed IT services provider is that compliance support becomes woven into your everyday operations. Instead of treating SOC 1 compliance as an annual fire drill, you're building and maintaining the controls continuously. This approach not only makes audits less stressful but often results in operational improvements that benefit your entire organization.
Whether you're gearing up for your first SOC 1 audit or looking to streamline your ongoing compliance efforts, success starts with a solid foundation. When your IT controls are properly designed, documented, and maintained, everything else falls into place more naturally.
Ready to strengthen your IT foundation for compliance success? Let's work together to make your SOC 1 compliance journey as smooth and successful as possible.
Strengthen your IT controls for compliance with our Managed IT Services
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
