Don't Get Lost in the Forest: Mastering Active Directory Installation
January 9, 2026

Master cybersecurity compliance. Explore top Security Compliance Services for beginners to secure data, build trust, and prevent penalties.
February 25, 2026

Secure your dental practice from downtime & breaches. Discover expert IT services for dentists specializing in HIPAA, cybersecurity & dental software.
February 24, 2026

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
January 9, 2026
Active directory setup is the process of installing and configuring Microsoft's directory service to centrally manage users, computers, and resources across your Windows network. Here's the quick roadmap:
Essential Steps for Active Directory Setup:
What is Active Directory? Active Directory (AD) is Microsoft's directory service that acts as a centralized database for managing your network. It handles user authentication through the Kerberos protocol, controls resource access, and enables Single Sign-On (SSO) so employees log in once to access all network resources. For any business with more than a handful of computers, it's the backbone that keeps everything organized and secure.
Why Active Directory Matters for Network Management:
Without Active Directory, you're managing each computer individually—resetting passwords locally, installing software manually, and struggling to control who accesses what. With AD properly configured, you gain centralized control over your entire network from one location. You can enforce security policies across all machines, deploy software to hundreds of computers simultaneously, and ensure only authorized users access sensitive data.
The stakes are high. A poorly configured Active Directory can leave your business vulnerable to security breaches, make compliance audits nightmarish, and turn simple tasks like password resets into hour-long ordeals. Conversely, a well-designed AD environment streamlines IT operations, strengthens security, and scales effortlessly as your business grows.
I'm Steve Payerle, President of Next Level Technologies, and I've guided countless businesses through active directory setup and management since founding our company in 2009. Our team in Columbus, Ohio and Charleston, WV has the extensive cybersecurity training and technical experience to ensure your directory service is both secure and efficient.
Before we even touch a keyboard for the actual active directory setup, a crucial step is thorough planning. Think of it like building a house: you wouldn't start hammering nails without a blueprint, right? The same goes for your Active Directory. A well-thought-out design is essential for a cost-effective and successful deployment. This initial planning phase helps us align your IT infrastructure with your business needs, ensuring scalability and ease of management for years to come.
We always recommend taking the time to design your logical structure, including forest and domain planning. This involves considering how your organization's hierarchy, geographical locations, and administrative needs translate into the Active Directory structure. Microsoft provides excellent guidance on AD DS Design and Planning that we often leverage. We'll also establish clear naming conventions for your domains, organizational units (OUs), and objects. This seemingly small detail can make a huge difference in managing your environment as it grows. Planning for scalability from the outset is key; an Active Directory that works for 50 users today needs to gracefully handle 500 or 5,000 users tomorrow.
Our IT professionals in Columbus, Ohio, specialize in helping businesses align their IT design with their business structure. We'll work with you to ensure your Active Directory is not just a technical solution, but a strategic asset that supports your operational efficiency and growth.
Before diving into the installation, let's ensure your server is ready. Here's a list of prerequisites that are non-negotiable for a smooth active directory setup:
Meeting these prerequisites ensures that your server has the foundational elements necessary to host Active Directory Domain Services reliably.
Beyond the basic prerequisites, several key design considerations will influence the stability and performance of your Active Directory environment:
Once our planning is complete and all prerequisites are met, we move to the heart of the active directory setup: installing the Active Directory Domain Services (AD DS) role and promoting our server to a Domain Controller. This is where your server transforms into the central authority for your network.
There are primarily two modern methods for installing AD DS: using Server Manager (the graphical user interface, or GUI) or using Windows PowerShell (for command-line automation). It's worth noting that the traditional Active Directory Domain Services Installation Wizard (dcpromo.exe) is deprecated beginning in Windows Server 2012. We prefer Server Manager for smaller, one-off installations or for those less familiar with scripting, while PowerShell offers efficiency and repeatability for larger or complex deployments.
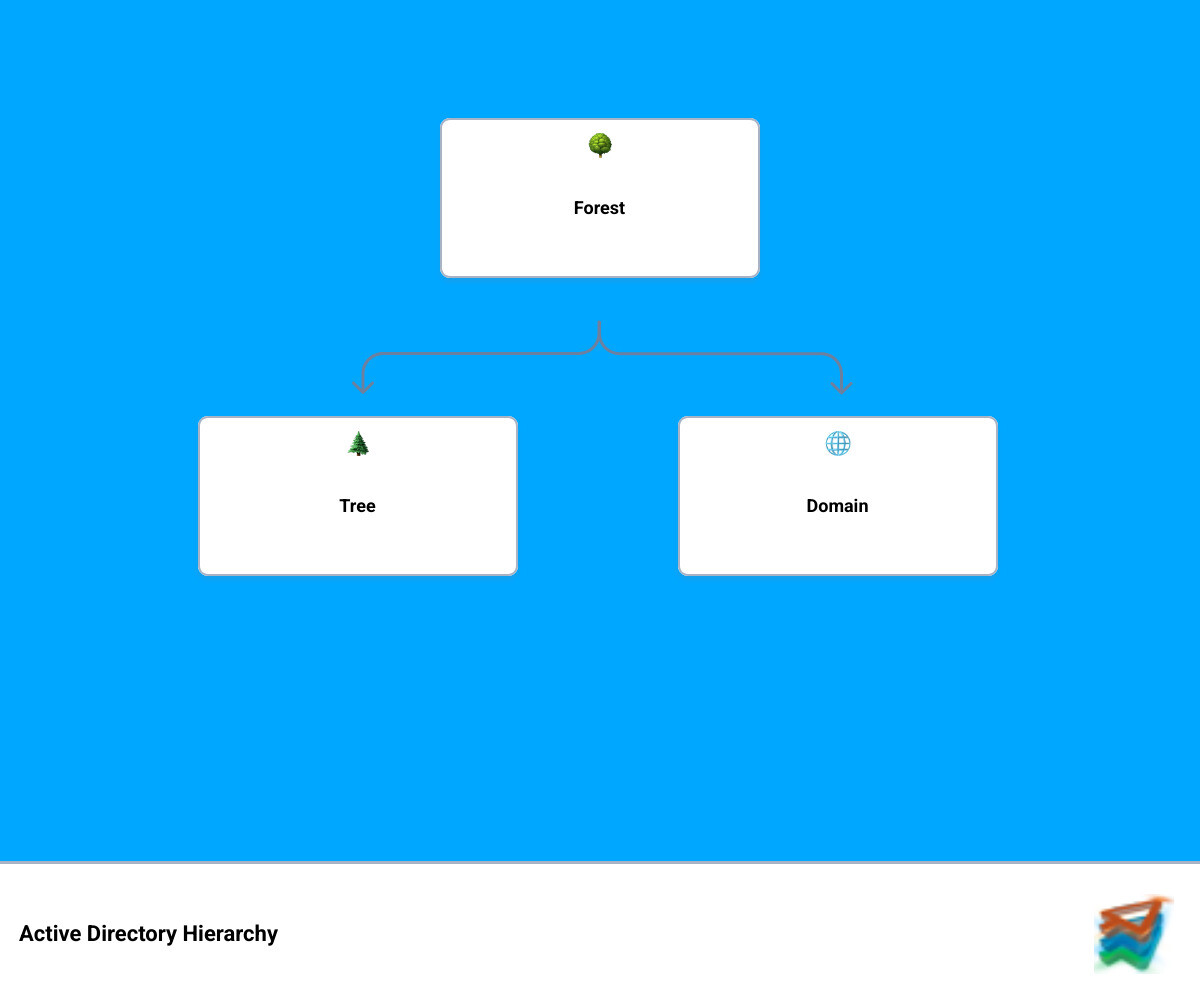
The goal here is typically to create a new forest, which is the top-level container in Active Directory, encompassing one or more domains. This creates a completely new, independent Active Directory environment. You can find detailed installation instructions on Microsoft Learn, which we'll summarize below.
For many, the graphical interface of Server Manager offers a straightforward path to active directory setup. Here’s how we guide our clients through it:

Now that the role is installed, we need to promote the server to a Domain Controller:
Congratulations! You’ve just completed a foundational part of your active directory setup.
For those who love efficiency, automation, and repeatability—or for our experienced IT support teams managing multiple deployments—Windows PowerShell is the tool of choice for active directory setup. The benefits of automation are immense: reduced human error, faster deployments, and consistent configurations across your infrastructure.
Here’s a breakdown of the PowerShell approach:
Install the AD DS Role: We start by installing the Active Directory Domain Services role using the Install-WindowsFeature cmdlet:
Install-WindowsFeature -Name AD-Domain-Services -IncludeManagementTools -RestartThe -IncludeManagementTools parameter ensures that the necessary GUI tools like Active Directory Users and Computers are also installed, and -Restart will reboot the server if required.
Promote to a New Forest: After the role is installed, we use cmdlets from the ADDSDeployment module to promote the server. To create a new forest, we use Install-ADDSForest:
# Define variables for domain name and DSRM password$DomainName = "yourcompany.local"$DSRMPassword = ConvertTo-SecureString "YourStrongDSRMPassword!" -AsPlainText -Force# Install a new AD DS ForestInstall-ADDSForest ` -DomainName $DomainName ` -InstallDNS:$true ` -NoRebootOnCompletion:$false ` -DomainMode "Win2016" ` # Or Win2019, Win2022 depending on your target FL -ForestMode "Win2016" ` # Or Win2019, Win2022 -LogPath "C:\Windows\NTDS" ` -SysvolPath "C:\Windows\SYSVOL" ` -DatabasePath "C:\Windows\NTDS" ` -Credential (Get-Credential) ` # Prompts for Domain Administrator credentials -SafeModeAdministratorPassword $DSRMPasswordConvertTo-SecureString for the DSRM password. For production environments, we often use Get-Credential to securely prompt for credentials or retrieve them from a secure vault, rather than hardcoding them. This is a best practice for security, especially important given the rising number of cyberattacks targeting small to medium-sized businesses.Test-ADDSForestInstallation to perform prerequisite checks, ensuring our environment is ready and avoiding potential issues during deployment. This is a preferred method for our experienced IT support teams in Columbus, Ohio, and Charleston, WV, as it allows for efficient and error-free deployments.This automated approach is particularly powerful for large-scale deployments or for building repeatable lab environments for learning and testing.
Once your Domain Controller is up and running, the active directory setup isn't quite finished. Now, it's time to verify the installation and begin configuring your directory to reflect your organization's structure and needs. This involves using tools like Active Directory Users and Computers and the Active Directory Administrative Center to build out your directory structure and manage network objects.
A well-structured Active Directory is a beautiful thing, making administration a breeze. Here's how we start populating your domain:
ra-service or autoenrollmentbind account might be created for certificate services integration, and added to the 'Cert Publishers' group, but never to the 'Protected Users Security Group' to avoid breaking LDAP Bind, as highlighted in some specialized integrations.For your Active Directory to function correctly, its network services—specifically DNS and DHCP—must be properly configured and integrated. They are the unsung heroes of your domain.
_ldap._tcp.dc._msdcs.yourdomain.local) are correctly registered in your DNS zone.yourcompany.local) and usually a reverse lookup zone to resolve IP addresses back to hostnames.Properly configured DNS and DHCP ensure that client computers can find and communicate with your Domain Controllers, authenticate users, and access domain resources seamlessly.
An active directory setup is not a "set it and forget it" task. In today's threat landscape, maintaining and securing your Active Directory environment is paramount. With cyberattacks becoming more sophisticated, especially against SMBs, neglecting AD security is like leaving your front door wide open. Our team, with extensive cybersecurity training, particularly our experts in Charleston, WV, understands the critical importance of these ongoing efforts.
Here are some best practices we implement and recommend:
By adopting these practices, we ensure your Active Directory remains a secure and reliable foundation for your business operations.
We often encounter common questions about Active Directory. Here are some of the most frequent ones:
A Domain Controller (DC) is a server with the Active Directory Domain Services (AD DS) server role installed that has specifically been promoted to a domain controller. Its primary role is to host a copy of the AD DS database (the NTDS.dit file), providing authentication and authorization services for users and computers within its domain.
You need a Domain Controller because it centralizes user authentication, manages access to network resources, and enforces security policies. Without it, you'd have to manage each computer and user individually, which quickly becomes unmanageable and insecure in a business environment. For redundancy and high availability, we always recommend having at least two Domain Controllers in your environment. If one DC fails, the other can seamlessly take over, preventing network downtime.
Absolutely! Setting up Active Directory in a home lab environment is an excellent way to learn and test your skills without impacting a production network. Many of our team members honed their skills this way.
To do this, you'll typically need:
There are many great resources available, including videos like How to Setup a Basic Home Lab Running Active Directory (Oracle VirtualBox), that can walk you through the process. It's a fantastic hands-on learning experience!
Think of it like this:
yourcompany.local would be a domain.So, a domain is a segment of your network managed by AD, while a forest is the overarching structure that contains all your domains, establishing a common foundation and trust relationships between them.
Mastering active directory setup is truly the foundation of a well-managed, secure, and scalable business network. We've walked through the critical steps, from meticulous planning and meeting prerequisites to the actual installation using Server Manager or PowerShell, and finally, the essential post-installation configurations of OUs, users, DNS, and DHCP. We've also emphasized the ongoing vigilance required to secure and maintain this vital component of your IT infrastructure.
A properly implemented and managed Active Directory streamlines operations, improves security through robust authentication and access control, and provides the scalability your business needs to grow. It simplifies tasks that would otherwise be complex and time-consuming, freeing up your team to focus on strategic initiatives.
For complex deployments, migrations, or ongoing maintenance, partnering with experienced IT professionals is often the smartest move. Our team at Next Level Technologies, with locations in Columbus, Ohio, and Charleston, WV, brings extensive cybersecurity training and technical expertise to ensure your Active Directory environment is not just functional, but optimized, secure, and aligned with your business objectives.
Don't get lost in the forest of complex configurations. Let us guide you to a clear, efficient, and secure Active Directory environment.
Master cybersecurity compliance. Explore top Security Compliance Services for beginners to secure data, build trust, and prevent penalties.
February 25, 2026
Secure your dental practice from downtime & breaches. Discover expert IT services for dentists specializing in HIPAA, cybersecurity & dental software.
February 24, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
