Choosing Your Shield: A Guide to Secure Remote Access Solutions
October 2, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
October 2, 2025
Effective remote work security solutions are a top priority for modern businesses. With many employees now in hybrid or fully remote roles, companies enjoy benefits like increased productivity but also face new, complex digital dangers. Protecting data and systems from these evolving threats is crucial for business continuity and trust.
To effectively secure your remote workforce, focus on these key areas:
At Next Level Technologies, our teams in Columbus, Ohio, and Charleston, WV, have extensive technical experience crafting robust remote work security solutions. We provide the comprehensive cybersecurity training and IT support needed to protect and propel your business forward.
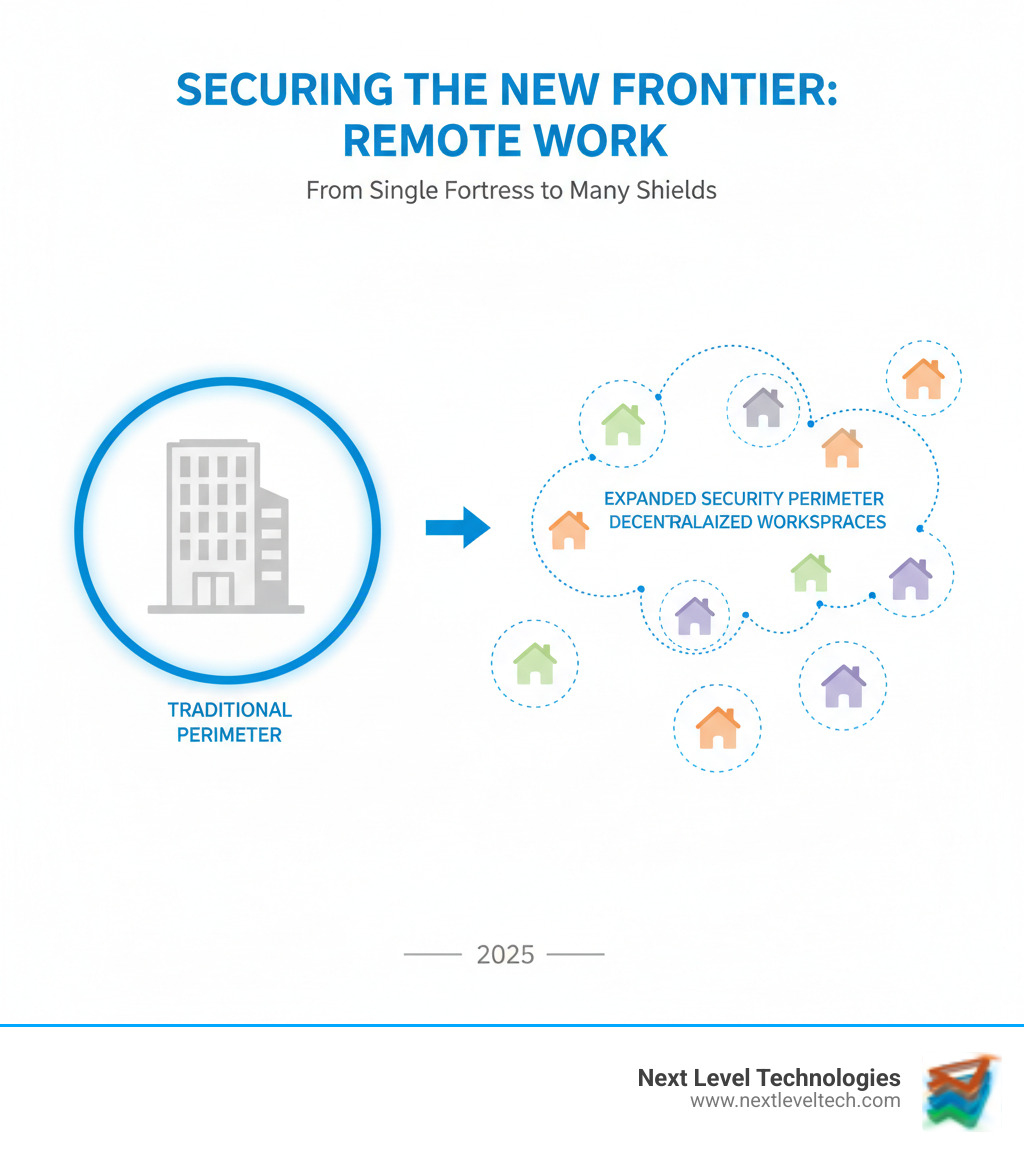
The shift to remote work has fundamentally changed cybersecurity. Protecting a single office is now the complex challenge of securing countless individual workspaces. The pandemic accelerated this shift, often forcing companies to prioritize operations over security. Cybercriminals took advantage, with CISA issuing warnings as phishing attacks surged.
While remote work can boost productivity by 35-40%, it creates a daunting security landscape. Here are the primary challenges:
Insecure home networks are a major vulnerability. Unlike corporate offices, home networks often use basic routers with weak security, making them easy targets for cyber threats.
The BYOD (Bring Your Own Device) challenge adds complexity. When employees use personal devices for work, IT teams lose visibility and control. These unmanaged devices may lack corporate security software, requiring sophisticated remote work security solutions.
Phishing attacks have exploded. Phishing, vishing, and smishing attacks prey on isolated remote workers. The average attack costs businesses $1.6 million.
Data leakage is a major concern. Employees might accidentally share confidential data through personal email or unapproved cloud services, putting critical information at risk.
Shadow IT emerges when employees use unapproved tools. While convenient, these apps can create significant security gaps and compliance issues.
Physical security risks include unattended laptops, sensitive documents visible on video calls, and accidental access by family members.
Compliance issues are more complex. Ensuring compliance with regulations like HIPAA or PCI DSS across many home offices requires robust security frameworks.
Perhaps most challenging of all is human error, which accounts for over 90% of incidents. The best technology can be undermined by one employee clicking a malicious link.
According to Forbes' Remote Work Statistics And Trends In 2024, 12.7% of full-time employees work remotely, and 28.2% are in hybrid models. These figures represent a new normal that demands proactive, comprehensive remote work security solutions.

While these challenges are significant, they are manageable. The right combination of technology, policies, and training can create a secure remote environment. The key is to rethink security from the ground up, not just deploy more software.
Securing a remote workforce requires a layered, holistic strategy. No single tool is enough; effective remote work security solutions integrate multiple technologies to protect data, devices, and access points.
At Next Level Technologies, our extensively trained cybersecurity teams in Columbus, Ohio, and Charleston, WV, know that robust security is about enabling business continuity. Our technical experts build the right combination of tools to keep your team productive and secure. Learn more about our Cybersecurity Services.

The first challenge is ensuring only the right people access your systems.
Virtual Private Networks (VPNs) create an encrypted tunnel between a remote device and the company network. While essential, VPNs are just one piece of a larger strategy. We help implement comprehensive Secure Remote Access Solutions.
Virtual Desktop Infrastructure (VDI) keeps all data on company servers. Employees access a virtual desktop, so no sensitive data is stored on their local device. This is ideal for preventing data loss from stolen or compromised endpoints.
Zero Trust Network Access (ZTNA) operates on the principle of "trust nobody, verify everything." Unlike VPNs, ZTNA grants access on a per-request, per-application basis, creating a more granular security model.
Identity and Access Management (IAM) systems verify user identities and control permissions. Features like Single Sign-On (SSO) improve user experience, while Role-Based Access Control (RBAC) enforces the principle of least privilege, giving employees access only to the resources they need.
Remote endpoints are outposts of your business network and need serious protection.
Endpoint Detection and Response (EDR) solutions continuously monitor endpoints for suspicious activity. They detect threats that bypass traditional defenses and enable rapid response, acting like a security detective on every device.
Mobile Device Management (MDM) is crucial for managing smartphones and tablets. MDM allows IT to enforce security policies, manage apps, and remotely wipe corporate data from lost or stolen devices.
Antivirus and anti-malware software remains essential. Disk encryption protects data on stolen devices, and patch management is critical for closing vulnerabilities that hackers exploit.
Securing BYOD policies must balance security with employee privacy. This can involve creating secure work containers on personal devices. Our IT Security Solutions for Small and Mid-Sized Companies help steer this complexity.
Protecting information in cloud applications requires specialized tools.
Cloud Access Security Brokers (CASB) act as intermediaries between users and cloud services. They enforce security policies, provide visibility, and prevent data leakage across all cloud applications.
Data Loss Prevention (DLP) solutions identify and prevent the unauthorized sharing of sensitive information. Cloud data encryption provides another layer of protection by scrambling data.
Secure cloud storage involves using enterprise-grade platforms with strong access controls and audit trails. Backup and disaster recovery planning is also essential to ensure business continuity after an incident like a ransomware attack.
The key is integrating these systems seamlessly. For more insights, see our Cloud Security Best Practices guide. Our cybersecurity teams have extensive training in these technologies and excel at creating comprehensive strategies that protect your business without hindering productivity.
Traditional "castle-and-moat" security is obsolete for a distributed workforce. As our cybersecurity teams in Columbus, Ohio, and Charleston, WV, know, the perimeter has vanished. Modern remote work security solutions require smarter frameworks like Zero Trust and SASE.
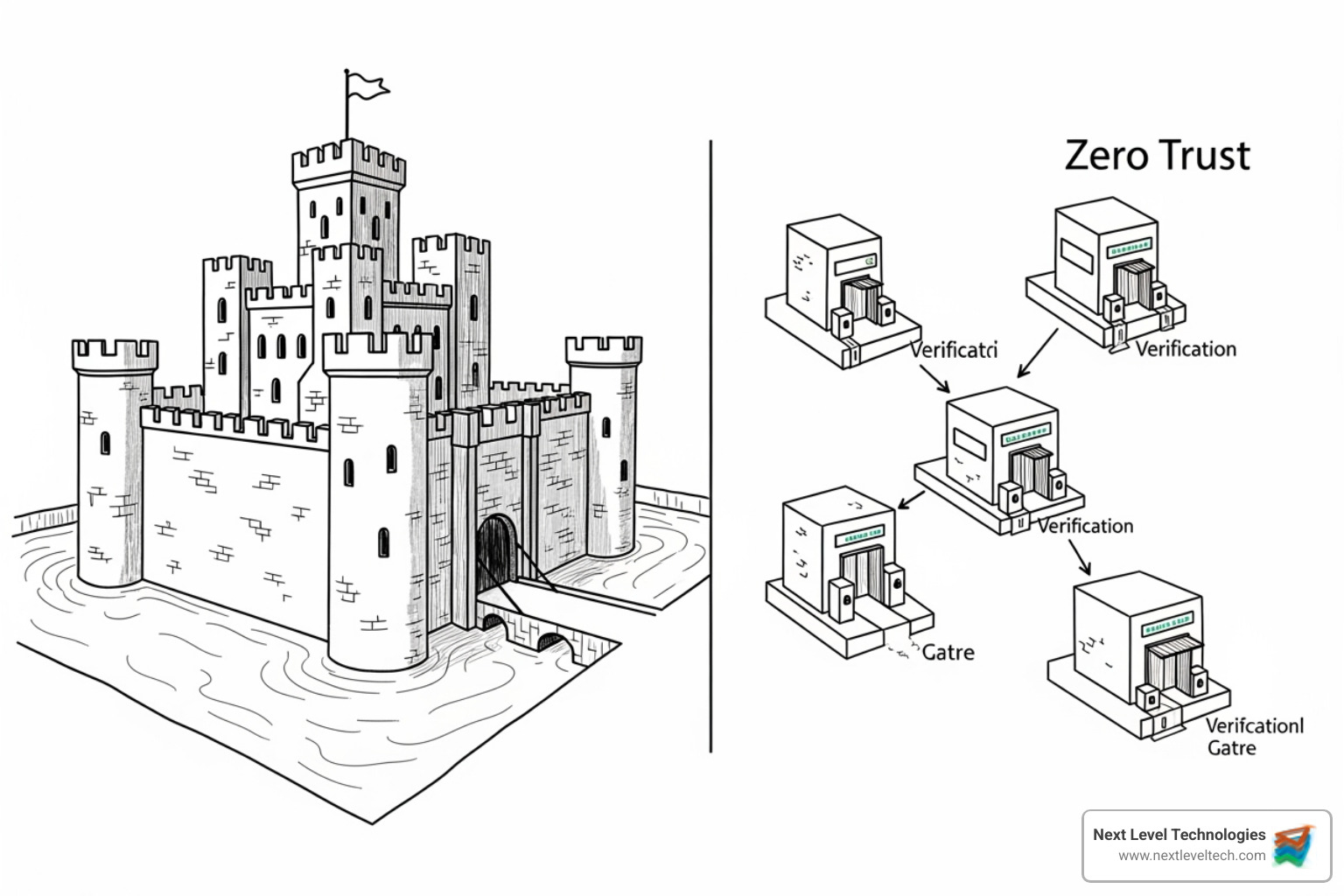
Zero Trust operates on a simple principle: trust no one, verify everyone. Every access request is scrutinized, regardless of user location. It enforces the principle of least privilege, ensuring users only get the access they need. This is achieved through micro-segmentation and continuous verification. If a device is compromised, Zero Trust limits the attacker's ability to move laterally across the network, containing the threat.
SASE (Secure Access Service Edge) is a complementary, cloud-native architecture that converges networking and security into a single cloud-delivered service. It brings security to the user, wherever they are, instead of backhauling traffic to a central office. SASE combines key technologies like SD-WAN, Secure Web Gateway, CASB, Zero Trust Network Access, and Firewall as a Service. This ensures consistent security and better performance for remote users.
Here's how these approaches compare to traditional security:
| Feature | Traditional Security | Zero Trust | SASE |
|---|---|---|---|
| Principle | Trust internal, distrust external | Never trust, always verify | Converged networking & security at the edge |
| Architecture | Perimeter-based, data center-centric | Identity- and context-driven, micro-segmented | Cloud-native, globally distributed points of presence |
| Access Model | VPN for full network access | Least privilege, application-specific access (ZTNA) | Least privilege, ZTNA integrated with network optimization |
| Benefits for Remote Work | Limited, relies on users connecting to HQ | Improved security, limits breach impact | Optimal performance, consistent security, simplified management |
Zero Trust and SASE are becoming essential. Zero Trust provides the "verify everything" philosophy, while SASE provides the cloud-native infrastructure to implement it efficiently. Our extensively trained cybersecurity teams understand this isn't an either-or choice. The most effective remote work security solutions blend elements of both to create a robust and practical security posture for the modern hybrid workplace.
Even the most sophisticated remote work security solutions can fail with a single click. The human element is often the most vulnerable point, with over 90% of cybersecurity incidents tracing back to human error. In remote settings, this vulnerability is amplified.

Attackers don't need to break down the door if they can trick an employee into opening it. This was evident when phishing attacks surged by 500% at the start of the pandemic, targeting newly remote workers who were often operating without their usual office security net.
Cybersecurity awareness training is a frontline defense. It teaches your team to recognize the red flags of phishing emails, such as suspicious senders, urgent language, and malicious links. A key rule is to verify suspicious requests before clicking.
Social engineering extends beyond email to vishing (voice) and smishing (SMS). Attackers pose as trusted figures to manipulate employees. Training helps your team recognize and resist these psychological tactics.
Strong password policies, managed through a password manager, are another critical foundation. Your acceptable use policies must also be updated for remote work, providing clear guidelines on using personal devices and securing home networks.
A clear, accessible incident response plan is vital. Employees must know who to contact and what to do when they suspect an issue. As the Cyber Kill Chain framework illustrates, early detection and response are critical to mitigating damage.
At Next Level Technologies, our extensively trained cybersecurity teams in Columbus, Ohio, and Charleston, WV, know that technology is only as strong as its users. We don't just implement remote work security solutions; we empower your workforce with continuous education. Our experts translate complex threats into practical guidance, making security a team-wide responsibility where every employee is a key defender.
It's normal to have questions when securing a remote workforce. Here are some of the most common concerns we hear, along with our expert insights.
Effective remote work security solutions offer more than just protection; they provide significant business benefits:
Multi-Factor Authentication (MFA) is one of the most impactful steps you can take. It requires users to provide two or more verification factors to gain access, dramatically improving security. Even if a password is stolen—a factor in 81% of breaches—MFA prevents unauthorized access. It is a cornerstone of a Zero Trust security model.
MFA combines verification methods from different categories:
Modern MFA is user-friendly, often involving a simple push notification to a phone. Enforcing MFA across all critical systems is a foundational best practice for any robust remote work security solutions, offering a monumental security return on a small implementation effort.
Collaboration tools like Teams and Slack are vital for remote work but also present security risks. A multi-pronged approach is needed to secure them effectively:
Remote work is here to stay, offering flexibility and productivity but also introducing new digital dangers. From insecure home networks and BYOD risks to phishing attacks and cloud data protection, navigating this new normal requires a proactive, comprehensive plan built on strong remote work security solutions.
This guide covered the essentials for building that plan: creating a digital fortress with access controls like ZTNA and VDI, protecting every endpoint with EDR and MDM, and securing cloud data with DLP. We explored modern frameworks like Zero Trust and SASE that shift security to a "never trust, always verify" model. Finally, we highlighted the critical human element, where employee training and clear policies are your most essential defenses.
At Next Level Technologies, we know every business is unique. We partner with you to understand your specific needs and craft customized remote work security solutions. Our extensively trained cybersecurity teams in Columbus, Ohio, and Charleston, WV, bring deep technical experience and a passion for staying ahead of threats. We design and implement strategies that protect your assets, ensure compliance, and empower your team to work securely and confidently from anywhere.
Don't let the complexities of remote work security feel overwhelming. Let us help you build your digital fortress so you can focus on what you do best – growing your business.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
