From Tokens to Biometrics: Real-World Multi-Factor Authentication Examples
September 23, 2025

Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026

Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026

Find the best Remote IT Support Business for your small business. Learn how to define needs, evaluate providers, and secure your tech.
February 6, 2026
September 23, 2025
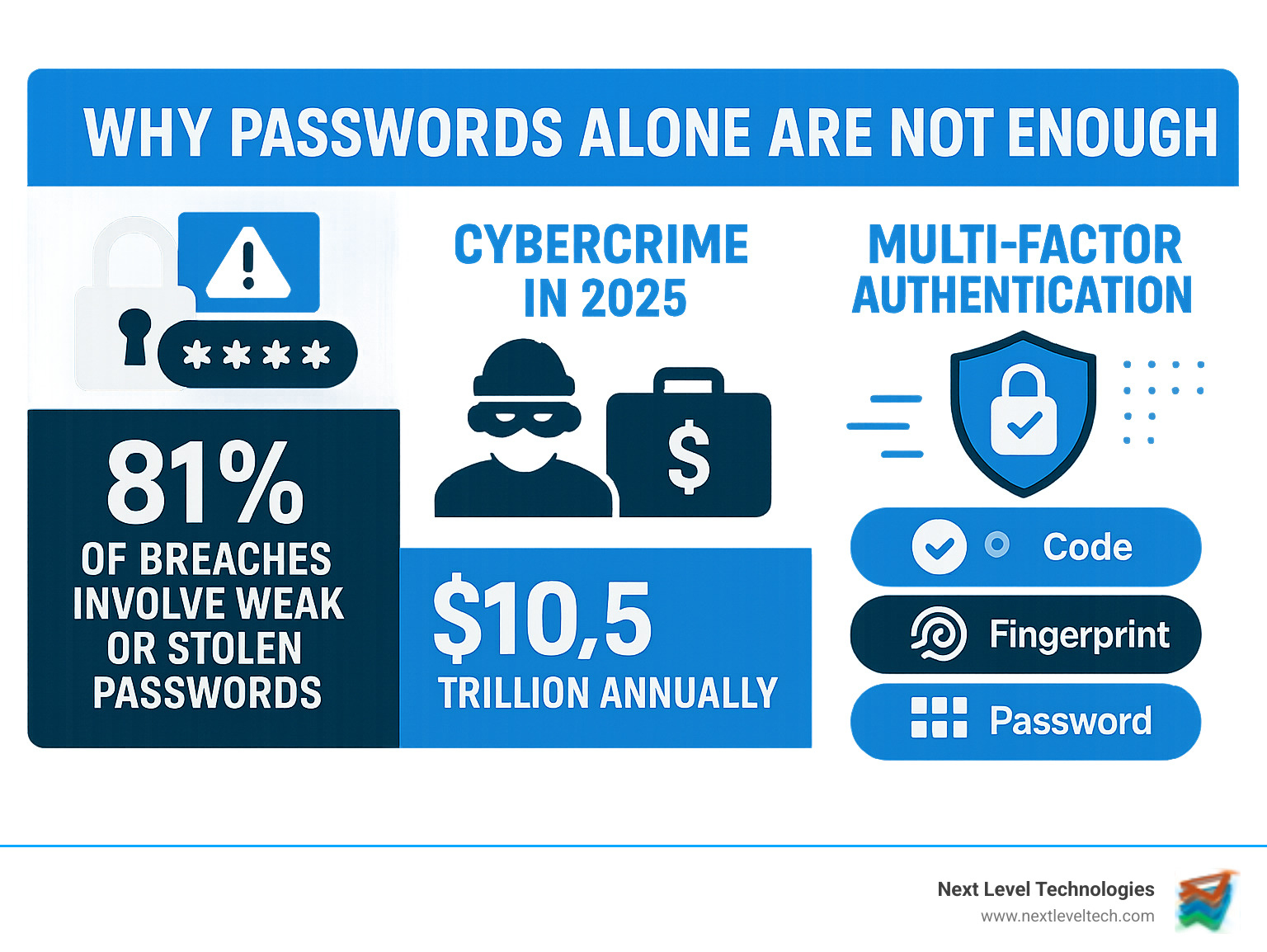
Multi factor authentication examples are everywhere in today's digital world, and for good reason. With cybercrime projected to cost companies a staggering $10.5 trillion annually by 2025, robust security is more critical than ever.
The reality is stark: passwords can be easily compromised through phishing, cracking, or brute force attacks. Relying on a single password is like using a paper lock on a bank vault. That's where multi-factor authentication (MFA) steps in as your digital bodyguard.
MFA requires users to provide two or more separate authentication factors from different categories: something you know, something you have, or something you are. This layered approach ensures that even if one factor is compromised, unauthorized users are stopped in their tracks.
At Next Level Technologies, our team has helped countless businesses in Columbus, Ohio, and Charleston, WV, implement effective multi factor authentication examples to protect their critical data. Through extensive cybersecurity training and hands-on experience, we've seen how proper MFA can be the difference between a secure business and a costly data breach.
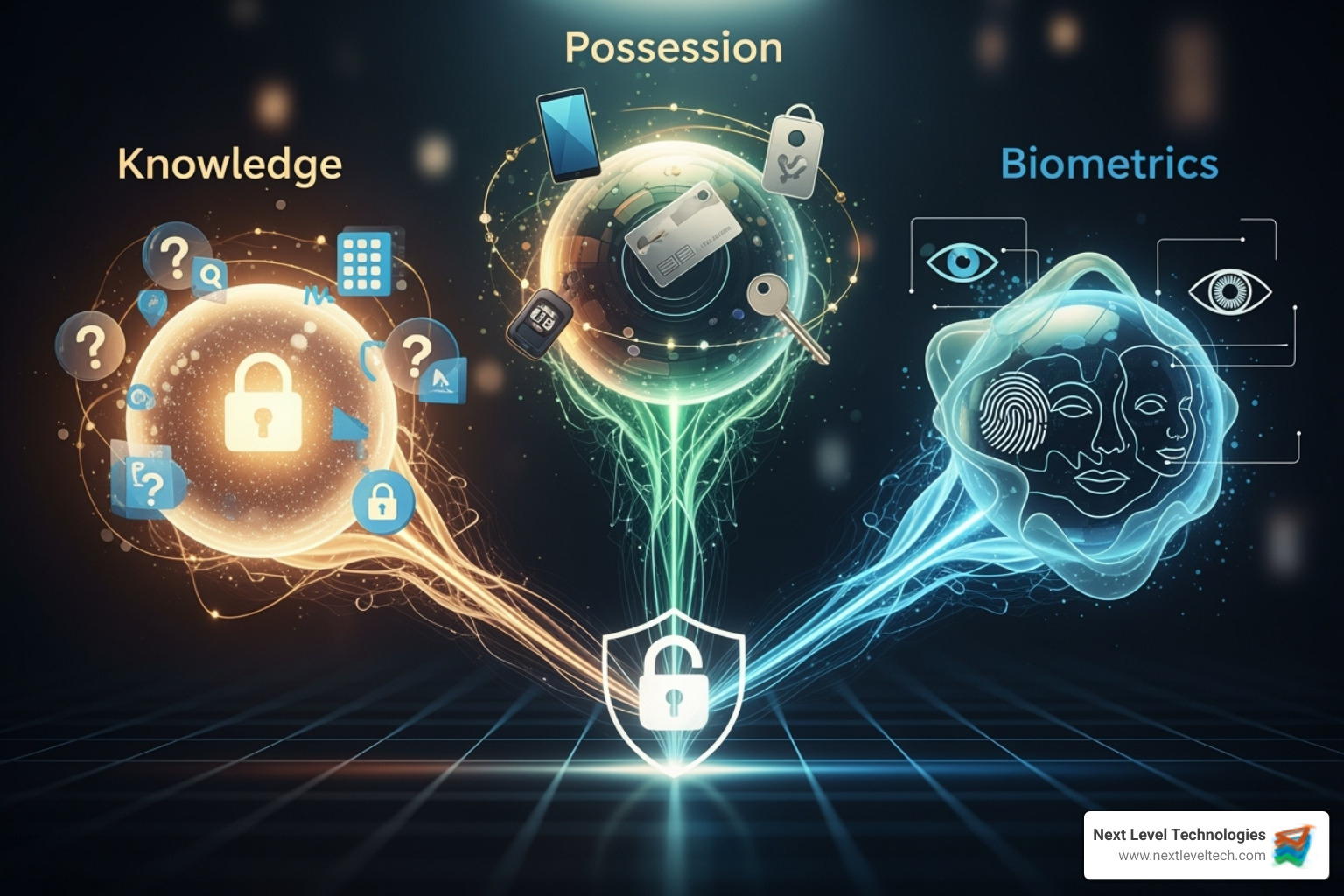
Effective multi factor authentication examples are built on three pillars of proof, creating a layered defense for your digital life. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) confirms that using at least two different types of authentication factors is key to real security. What is Multi-Factor Authentication?. At Next Level Technologies, our cybersecurity training has shown us that combining these pillars creates a nearly unbreachable defense.
This is information only you should know.
This involves a physical object in your possession.
This uses your unique biological traits for verification.
The power of MFA comes from combining these pillars. A stolen password is useless to a hacker who doesn't also have your fingerprint and your phone. This turns a single point of failure into multiple, strong security barriers.

Now that you understand the three pillars, let's look at real-world multi factor authentication examples. At Next Level Technologies, our cybersecurity-trained team in Columbus, Ohio, and Charleston, WV, regularly implements these methods. Through years of hands-on experience, we've learned that the best MFA balances rock-solid security with user convenience. The key is knowing which method to use and when.
This is often the first multi factor authentication example people encounter. After entering your password, a one-time code is sent to your phone or email. You enter this code to log in.
These apps are the secure, modern version of the old bank tokens. You scan a QR code to link an account, and the app generates a new six-digit code every 30 seconds, even when offline.
This is one of the easiest methods. Instead of typing a code, you get a notification asking, "Is this you trying to log in?" and simply tap "Approve" or "Deny."
Using your unique traits like a fingerprint or face is a fast and convenient way to authenticate. Most modern smartphones and laptops include fingerprint scanners and facial recognition (like Face ID).

For maximum security, physical devices like YubiKeys are the gold standard. They plug into a USB port or connect via NFC and use advanced cryptography to prove your identity.
This method uses geofencing and IP address verification to create an invisible security perimeter. It analyzes where a login attempt is coming from and flags anything unusual.
This advanced method analyzes how you interact with your device. It looks at your unique keystroke dynamics (typing rhythm) and mouse movement patterns.
These are physical cards with an embedded microchip that stores cryptographic keys. Users insert the card into a reader and often enter a PIN to authenticate.
The multi factor authentication examples covered are powerful, but modern cybersecurity demands smarter solutions. At Next Level Technologies, our extensive cybersecurity training and real-world implementation show that attackers constantly evolve. This is where adaptive MFA and artificial intelligence (AI) create an intelligent, dynamic security system.
Adaptive MFA, or risk-based authentication, adjusts security requirements based on the risk of each login attempt. Instead of always requiring two factors, it analyzes the context.
A login from your usual office in Columbus, Ohio, on a trusted device might only require a password. But an attempt from an unfamiliar network in another country at 3 AM would trigger a demand for more proof. The system assesses risk signals like device history, location, network, and time of day. When it detects high risk, it triggers step-up authentication, requiring an additional factor. This reduces user friction during low-risk activities while enforcing strong security when needed. Our experts in Charleston, WV, and Columbus, OH, have seen this approach improve both security and user satisfaction. You can learn about Adaptive Multi-Factor Authentication solutions to see how they can transform your security.
AI and machine learning are the brains behind adaptive MFA. These systems learn and adapt over time.
Through our hands-on experience, we've seen these AI-powered systems become dynamic, learning defenses that are invaluable in modern cybersecurity.
Creating an effective MFA strategy isn't about randomly picking multi factor authentication examples. It's about building a security framework that works for your business. At Next Level Technologies, our extensive cybersecurity training and hands-on experience help businesses in Columbus, OH, and Charleston, WV, develop strategies that protect data without frustrating employees. The key is balancing security with practicality.
Choosing the right MFA is like choosing the right lock. Your choice should depend on several factors:
Once you've chosen your methods, successful implementation is critical. This is where our highly trained staff makes a difference.
Our cybersecurity-trained staff at Next Level Technologies often helps businesses in Columbus, Ohio, and Charleston, WV, by answering common questions about multi factor authentication examples. Here are the most frequent ones:
While often used interchangeably, there's a key difference. Two-Factor Authentication (2FA) requires exactly two authentication factors. Multi-Factor Authentication (MFA) requires two or more factors.
Essentially, all 2FA is a type of MFA, but MFA can include three or more factors for even greater security. We recommend thinking in terms of MFA for more flexible and scalable security.
While MFA makes unauthorized access significantly harder, no system is 100% foolproof. Our cybersecurity training emphasizes being realistic about threats. Attackers can use sophisticated techniques like real-time phishing, social engineering, or SIM swapping to try and bypass MFA.
However, these attacks are complex and often target weaker MFA methods or human error. The goal of MFA is to make attacking your systems so difficult and costly that criminals move on to easier targets. Strong MFA methods, like hardware keys, are extremely difficult to bypass.
Not necessarily. Modern systems are smarter than the old "enter a code every time" approach. Features like trusted devices and "remember me" functionality reduce MFA prompts on your regular devices.
Adaptive MFA is even more intelligent, assessing risk factors like your location and device. It may only prompt for MFA when a login attempt seems suspicious. The frequency depends on the system's policy and the sensitivity of the data being protected.
The key takeaway from these multi factor authentication examples is simple: passwords alone are no longer enough. The old approach to security is an open invitation to cybercriminals. Just as you use multiple locks to protect your home, your digital life deserves the same thoughtful, layered protection.
The methods we've explored, from SMS codes to hardware tokens, create a fortress around your digital identity. Each layer makes it exponentially harder for attackers to succeed, even if they steal a password.
At Next Level Technologies, our highly trained staff in Columbus, OH, and Charleston, WV, have seen how proper MFA transforms a business's security. Through extensive cybersecurity training and real-world experience, we help organizations build robust, multi-layered defenses. This isn't just about compliance; it's a proactive IT strategy that protects your most valuable assets.
Modern MFA, especially with adaptive authentication, can be both stronger and more convenient. Don't wait to become another cybercrime statistic. The investment in MFA today is minor compared to the cost of a data breach tomorrow.
Ready to move beyond passwords and secure your digital future? Protect your business with our comprehensive Managed IT Services and let our team build the layered defense your business deserves.
Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026
Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
