Networking's Fantastic Four: Understanding Hubs, Switches, Bridges, and Routers
November 7, 2025

Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026

Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026

Find the best Remote IT Support Business for your small business. Learn how to define needs, evaluate providers, and secure your tech.
February 6, 2026
November 7, 2025
Hubs switches bridges and routers are the four fundamental devices that connect computers and enable data to flow through your network and to the internet. While they may look similar—just boxes with blinking lights and cable ports—each serves a distinct purpose in how your business technology operates:
Understanding these differences is critical for mid-sized businesses. The wrong choice leads to slow networks, security vulnerabilities, and costly downtime. The right choice creates a foundation for efficiency, security, and growth.
As President of Next Level Technologies, I've spent over 15 years helping businesses in Columbus, Ohio and Charleston, WV build reliable network infrastructures using the right combination of hubs switches bridges and routers for their specific needs. Our team's extensive cybersecurity training ensures we not only connect your devices but protect them from modern threats.
Let's break down how each device works and when your business should use them.
Understanding how hubs switches bridges and routers work is like learning the evolution of transportation—from walking to flying. Each device represents a leap forward in network intelligence and capability. Let's explore how each one functions and why some have become relics while others power today's business networks.
A network hub is like a crowded room where everyone shouts, creating chaos. As the simplest device for connecting computers in a LAN, a hub operates at the Physical Layer (Layer 1) of the OSI model with zero intelligence. When data arrives at one port, the hub copies and broadcasts it to every other port, regardless of the intended recipient.
This broadcasting creates serious problems. Since all devices share one communication channel (half-duplex communication), only one can transmit at a time. If two devices send data simultaneously, their signals collide, forcing them to wait and retry, which slows down the entire network.
Second, all devices share the total bandwidth, so performance degrades as more devices are added. Third, hubs pose a massive security risk. Because every data packet is sent to every device, any computer can eavesdrop on all network traffic—a vulnerability our cybersecurity-trained team finds unacceptable.
For these reasons, hubs are legacy technology. Their low price is offset by poor performance and security, making them unsuitable for modern business networks.

The network bridge was the first smart solution to the congestion caused by hubs. Operating at the Data Link Layer (Layer 2), it introduced intelligence to networking. A bridge learns by examining the destination MAC address (a unique hardware ID) of each data frame. It builds a table to map which MAC addresses exist on which network segment.
This MAC address filtering allows for smart decisions. Traffic between devices on the same segment is kept local, while traffic destined for the other side is forwarded only to that segment. This selective forwarding creates smaller collision domains, dramatically improving performance by reducing unnecessary traffic.
Bridges were mainly used for network segmentation, connecting two LANs while keeping their traffic separate. While you won't find many standalone bridges today, they were the direct predecessor to switches.
If a hub shouts and a bridge is a doorman, a network switch is an efficient postal service delivering mail to specific addresses. A switch is a multi-port bridge with superior intelligence and performance. Like bridges, switches operate at the Data Link Layer (Layer 2).
When a device connects, the switch learns its MAC address and logs it in a MAC address table, creating a map of the network. When a data frame arrives, the switch uses its table to send the frame only to the destination port. This targeted data delivery eliminates broadcasting and wasted bandwidth.
Modern switches support full-duplex communication (sending and receiving data simultaneously) and provide dedicated bandwidth to each port. This means your network performance stays consistent even as you add more devices.
By creating a separate collision domain for each port, switches virtually eliminate data collisions. This reduces congestion, speeds up transfers, and improves security by preventing unauthorized eavesdropping.
At Next Level Technologies, we consider switches the backbone of every business network we design for clients in Columbus, Ohio, and Charleston, WV. Their performance and security benefits are non-negotiable for any serious business. You can learn more about how these devices compare at Difference between Hub, Switch and Router.

Routers connect different networks together. As the most sophisticated device of the group, a router operates at the Network Layer (Layer 3) of the OSI model. If a switch manages local city streets, the router is the highway system connecting your city to the world.
Routers use IP addresses (not MAC addresses) to direct data packets between networks. By examining a packet's destination IP address, a router intelligently determines the best path for it to travel. To make these decisions, routers use routing tables—dynamic maps of networks and the best routes to reach them. They can automatically find alternate paths if a connection fails.
A router's primary function is to connect different networks, such as your office LAN (using private IP addresses) to the internet (using a public IP address). It translates between them and manages data flow. The router typically serves as the gateway to the internet, which makes it the ideal place to implement security features like firewalls.
Routers also manage broadcast domains, preventing traffic from one network from flooding another, which is crucial for performance and scalability. Our team's extensive cybersecurity training ensures we treat routers as critical security checkpoints. We configure every device for our clients with strict firewall rules, access controls, and monitoring.

Understanding the distinctions between these devices is crucial for designing an efficient, secure network. Our team's extensive cybersecurity training emphasizes selecting the right hardware to protect your infrastructure by knowing what each device does—and what it doesn't do.
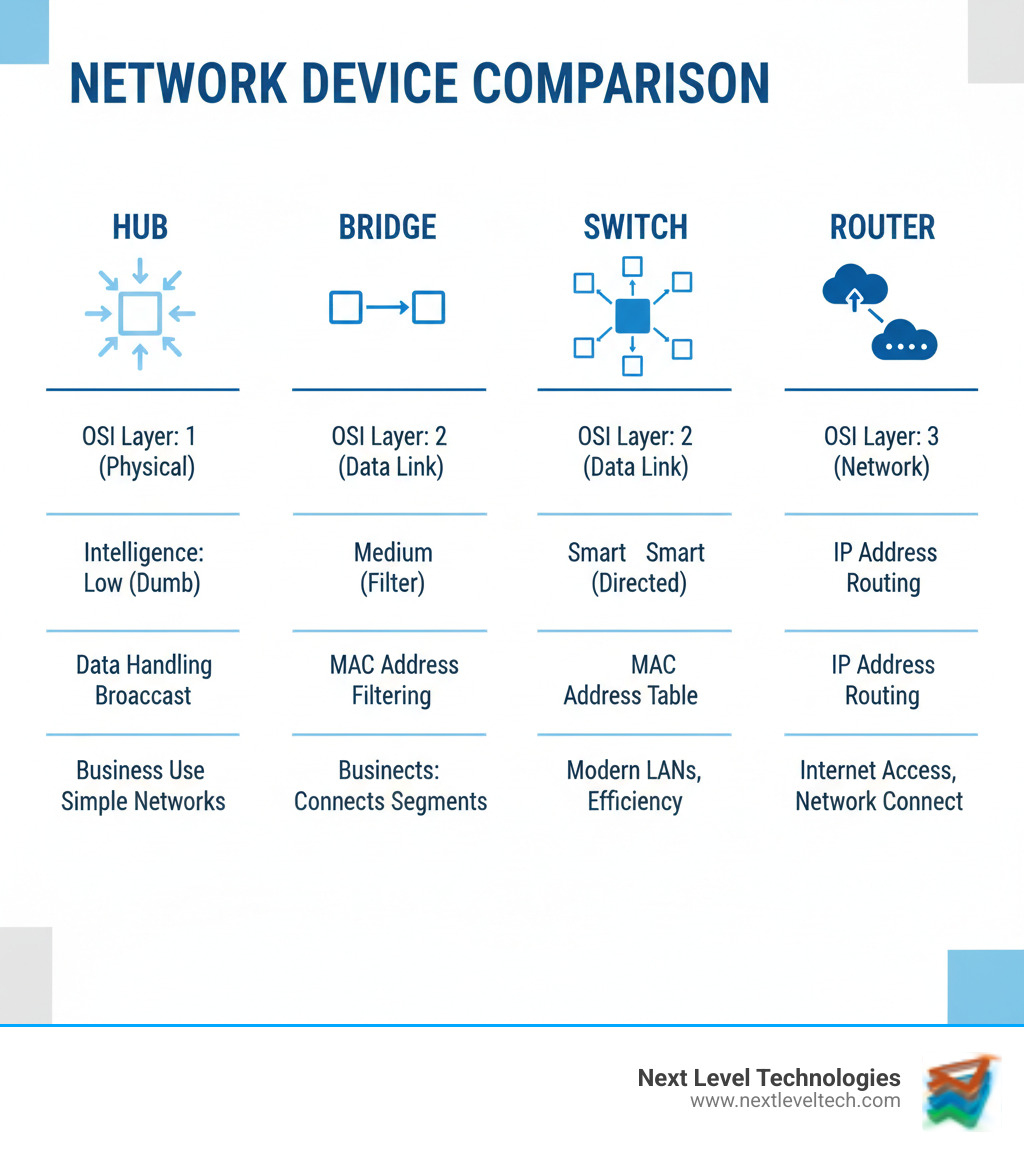
Comparing hubs, switches, bridges, and routers directly makes their distinct roles and evolutionary path from basic repetition to intelligent routing crystal clear:
| Feature | Hub | Bridge | Switch | Router |
|---|---|---|---|---|
| OSI Layer | Physical Layer (Layer 1) | Data Link Layer (Layer 2) | Data Link Layer (Layer 2) | Network Layer (Layer 3) |
| Data Handling Method | Broadcasts to all ports | Filters and forwards between segments | Targeted forwarding to specific port | Routes packets between different networks |
| Address Type Used | None (operates on electrical signals) | MAC Address | MAC Address | IP Address |
| Collision Domain | One large collision domain (all ports) | Divides collision domains (per segment) | Each port is a separate collision domain | Controls collision domains (within network) |
| Broadcast Domain | One large broadcast domain | One large broadcast domain | One large broadcast domain | Divides broadcast domains (between networks) |
| Intelligence | None (dumb repeater) | Basic (learns MACs) | High (learns MACs, dedicated paths) | Very High (learns IPs, routing tables, policies) |
| Typical Use Case | Obsolete, simple LANs (historical) | Connects 2 LAN segments, network segmentation | Connects devices within a LAN | Connects different networks (LAN to WAN/Internet) |
| Cost | Least expensive | More than hub, less than switch | More than bridge, less than router | Most expensive (due to advanced features) |
| Communication | Half-duplex | Half-duplex (typically) | Full-duplex | Full-duplex |
| Bandwidth | Shared among all ports | Shared per segment | Dedicated per port | Dedicated per port (for inter-network) |
This table shows a clear evolution from basic signal repetition (Hub) to genuine network intelligence (Router). Each step up brings better performance, security, and traffic management. You're not just paying for complexity; you're investing in an efficient and secure network foundation.
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes network functions into seven layers. A device's operating layer determines its capabilities. You can explore this concept in more depth at Switches, Hubs, Bridges, and Routers Explained.
Hubs operate at the Physical Layer (Layer 1). They deal only with electrical signals, regenerating them across all ports without any intelligence.
Bridges and switches operate at the Data Link Layer (Layer 2). This layer handles device-to-device communication on the same network using MAC addresses. Switches are essentially advanced, multi-port bridges that use MAC addresses to make smart forwarding decisions.
Routers work at the Network Layer (Layer 3), which handles packet delivery across different networks. Routers use IP addresses and routing tables to determine the best path for data to travel between networks, even if they are of different types.
Our experience helping businesses in Columbus, Ohio, and Charleston, WV, confirms that understanding these layers helps clarify why you need the right device for the right job.
The evolution from hubs to routers is a story of increasing data-handling intelligence.
Hubs use a 'broadcast everything' approach. This creates a single large collision domain, where simultaneous transmissions cause collisions and slow the network. Performance degrades as more devices are added due to shared bandwidth.
Switches introduced targeted data delivery. By learning MAC addresses, a switch sends data only to the recipient's port. This creates a separate collision domain for each port, eliminating collisions and providing dedicated bandwidth.
Routers provide the highest level of intelligence. They manage traffic between networks using IP addresses to make best-path routing decisions. Critically, they control broadcast domains, preventing traffic from one network from flooding another, which is essential for scalability.
This progression from broadcasting to best-path selection is why hubs are obsolete; their inefficiency and security flaws are unacceptable in modern business. Our team's extensive cybersecurity training focuses on configuring switches and routers to protect your business while optimizing performance.
Modern business-grade switches and routers offer more than basic connectivity; they have features that impact your security, performance, and growth. For businesses from Columbus, Ohio, to Charleston, WV, understanding these capabilities is key to making smart IT investments.
Your router does far more than simply pass data between your office and the internet. Modern business routers are powerful network management tools that protect your data, prioritize critical communications, and adapt to changing network conditions. Here's what you should expect from a quality business router:
Built-in Firewalls act as your network's front door security guard. They inspect all network traffic, blocking suspicious data before it causes harm. Our cybersecurity-trained team configures firewalls with custom policies to meet specific client security and compliance needs.
Virtual Private Network (VPN) Support allows remote and traveling employees to securely access company resources. The router encrypts this traffic, protecting sensitive data from interception.
Quality of Service (QoS) allows you to prioritize critical traffic, like a video conference call over a large file download, ensuring important communications remain clear even when the network is busy.
Network Address Translation (NAT) allows multiple internal devices to share a single public IP address for internet access. This conserves IP addresses and adds a layer of security by hiding your internal network structure.
Dynamic Routing Protocols like RSVP-TE (Resource Reservation Protocol - Traffic Engineering) enable routers to automatically find the best data paths and adapt to network changes, much like a GPS rerouting around traffic.
These features make a router a comprehensive management and security platform, providing smart, secure connectivity that protects your business.
Making the right choice about hubs switches bridges and routers isn't just a technical decision—it's a business decision that affects your daily operations, security posture, and ability to scale. Our technical experience serving businesses across Ohio and West Virginia has taught us that the right network foundation prevents countless headaches down the road.
Small businesses and home offices typically start with a quality wireless router, which often includes a built-in switch and Wi-Fi. This single device handles internet access, internal traffic, and device connectivity in one package.
As your business grows, you'll likely need to add dedicated switches for more ports and better internal performance. Using switches for LAN segmentation (e.g., separating departments) improves both performance and security.
Connecting multiple locations, such as offices in both Columbus and Charleston, requires enterprise-grade routers to create secure connections and manage complex routing and security.
Why hubs are obsolete is worth emphasizing: they are too slow and insecure for any modern business. A switch is always the better, affordable choice.
Scalability considerations are crucial. Choosing quality switches and routers with room for growth ensures your network can evolve with your business. Our team at Next Level Technologies designs networks with this future growth in mind, ensuring your technology investment continues to pay dividends.
The foundation of any reliable business network combines the right switches for internal connectivity with sophisticated routers for internet access and inter-network communication. Understanding how these devices work together allows you to build infrastructure that's fast, secure, and ready for whatever your business needs next. Learn more about how we design and manage robust network infrastructures at our managed IT services and support page.
The main difference is their function and scope. A switch operates at Layer 2 to connect devices within a single local network (LAN) using MAC addresses. A router operates at Layer 3 to connect different networks together (like your LAN to the internet) using IP addresses.
A simple analogy: switches manage traffic within a building, while routers direct traffic between cities. Businesses need both for a functional network.
Hubs are obsolete for two main reasons: inefficiency and insecurity. By broadcasting all data to every connected device, they create massive network congestion and frequent data collisions, slowing performance to a crawl. This broadcasting also means any device on the hub can intercept all network traffic, a critical security flaw our cybersecurity-trained team advises against.
With affordable and vastly superior switches available, there is no reason to use a hub in a modern network.
Yes, most small business routers include a built-in multi-port switch. This allows you to connect several wired devices directly to the router for local communication, while the router component manages your internet connection. This integrated approach is convenient and cost-effective for smaller setups.
As your business grows, you will likely add dedicated switches to expand your network's capacity while your router continues managing internet connectivity. When we design networks for clients, we carefully evaluate whether an integrated router-switch combination meets their needs or if separate, more robust devices are warranted.
The partnership between switches and routers is the foundation of every modern network. While hubs and bridges are now historical footnotes, understanding the roles of switches and routers is essential.
Choosing the right devices is a critical business decision. An inefficient or insecure network leads to lost productivity, security vulnerabilities, and potential damage to your reputation. The right infrastructure is an investment in your company's stability and efficiency.
You don't have to make these decisions alone. At Next Level Technologies, we understand that a secure, high-performing network is your business's backbone. Serving clients from Columbus, Ohio, to Charleston, West Virginia, our team uses its deep technical knowledge and extensive cybersecurity training to design and implement robust network infrastructures that protect your data and support your operations.
Your network should be an asset that enables efficiency and growth, not a headache. This is the difference between simply owning devices and having a true network strategy.
Don't let outdated technology or improper network design hold your business back. Let's build a network that's ready for today's challenges and tomorrow's opportunities.
Build a better network with our managed IT services and support
Unlock digital excellence with expert computer hardware and networking services. Secure your business, boost productivity, and future-proof your IT.
February 11, 2026
Unlock predictable IT costs, always have the latest tech, and boost efficiency with Hardware as a Service. Transform your business today!
February 10, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
