Schooling IT Compliance: Ensuring Success in Education
June 13, 2025

Unlock innovation & cut costs with expert Open Source managed services. Boost security, efficiency, and compliance for your business.
February 2, 2026
Compare IT Service Management Tools. Learn key features, benefits, and how AI can transform your IT operations for peak efficiency.
January 30, 2026
Unlock efficiency with service management software. Streamline operations, boost customer satisfaction, and transform your business.
January 29, 2026
June 13, 2025
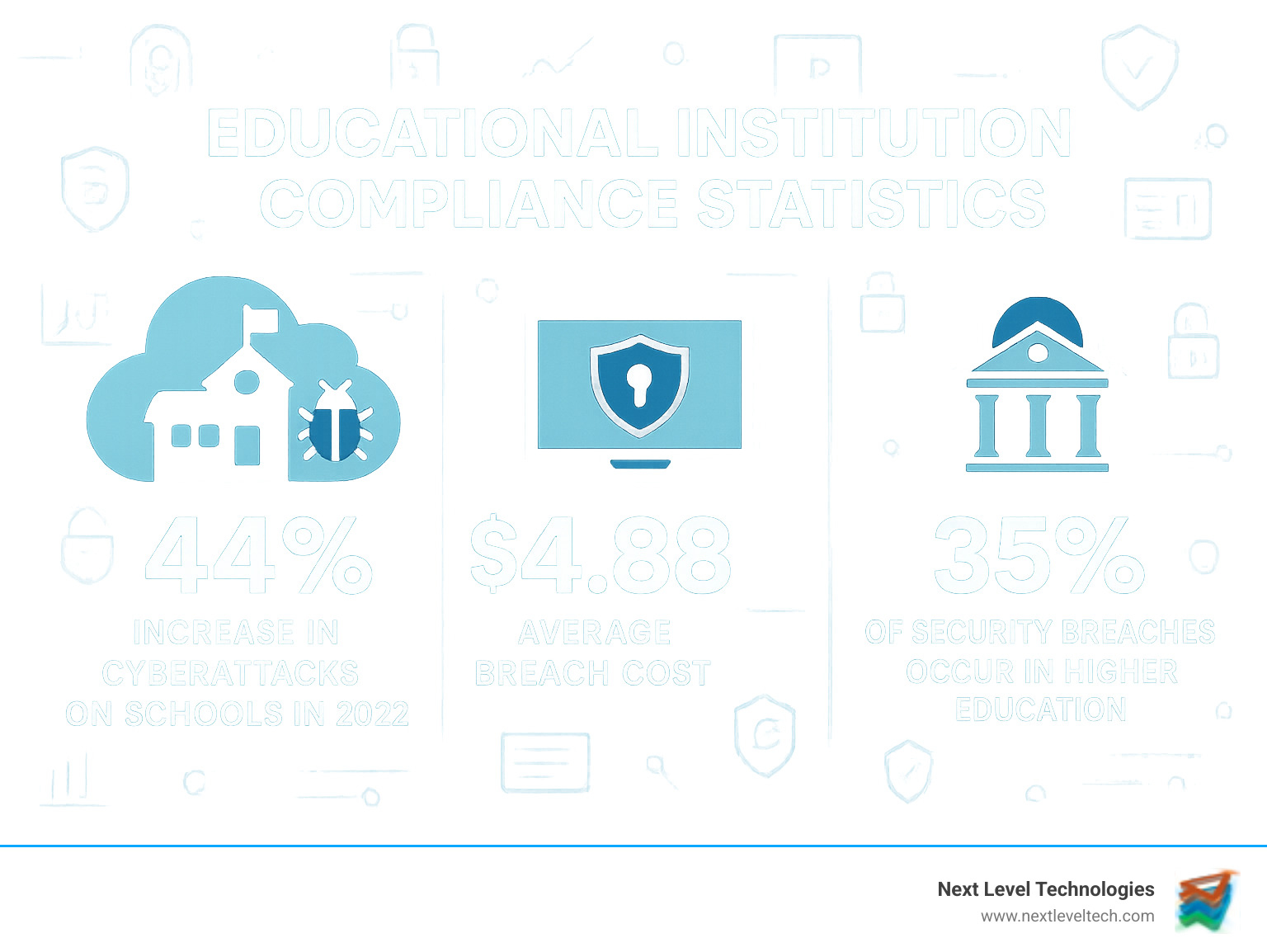
IT compliance for education refers to the policies, technologies, and practices educational institutions must implement to protect sensitive data and meet regulatory requirements. With cyberattacks against schools surging by 44% in 2022, educational institutions have become prime targets for hackers seeking valuable student information.
Quick Guide to IT Compliance for Education:- Core Regulations: FERPA (student records), COPPA (children's privacy), HIPAA (health data)- Key Requirements: Secure data storage, access controls, consent management, breach reporting- Protected Data: Student PII, health records, financial information, research data- Consequences of Non-Compliance: Loss of federal funding, legal penalties, reputational damage- Essential Safeguards: Encryption, MFA, staff training, vendor management, incident response
Educational institutions face unique compliance challenges because they manage diverse data types across complex networks while maintaining an open learning environment. From K-12 schools to universities, the stakes are high—a single ransomware attack has forced institutions to pay up to $100,000 in ransom.
I'm Steve Payerle, President of Next Level Technologies, and I've guided dozens of educational institutions through IT compliance for education challenges with our specialized teams in Columbus, Ohio and Charleston, WV who possess extensive cybersecurity training specifically for the education sector.
IT compliance for education terms made easy:- IT compliance assessments- IT compliance certifications- IT compliance monitoring
IT compliance for education isn't just about checking regulatory boxes—it's about creating a shield around sensitive information students, parents, and staff entrust to schools. It serves two critical functions: managing risk and aligning with regulations while maintaining open, collaborative learning environments.
This balancing act applies across the entire educational landscape: K-12 schools, colleges and universities, vocational schools, online learning platforms, and third-party vendors. Each must steer regulations like FERPA (protecting student records), COPPA (safeguarding children's online privacy), HIPAA (covering student health information), and potentially GDPR for institutions with European students.
Non-compliance with FERPA can cut off the federal funding many institutions rely on. Your reputation is also on the line—parents and students increasingly consider data security when choosing schools.
The threat landscape is more dangerous than ever. Educational institutions have become prime targets for ransomware attacks, with devastating consequences. Lincoln College in Illinois paid nearly $100,000 in ransom after a cyberattack in 2021 and ultimately closed its doors after 157 years.
This isn't surprising when you consider the education sector has experienced a 44% increase in cyberattacks in recent years. Our cybersecurity experts in Columbus and Charleston have seen how proper compliance measures can prevent disaster.
The consequences of getting compliance wrong are severe: loss of funding, regulatory fines, lawsuits, breach notification costs, operational disruption, and long-term reputation damage.
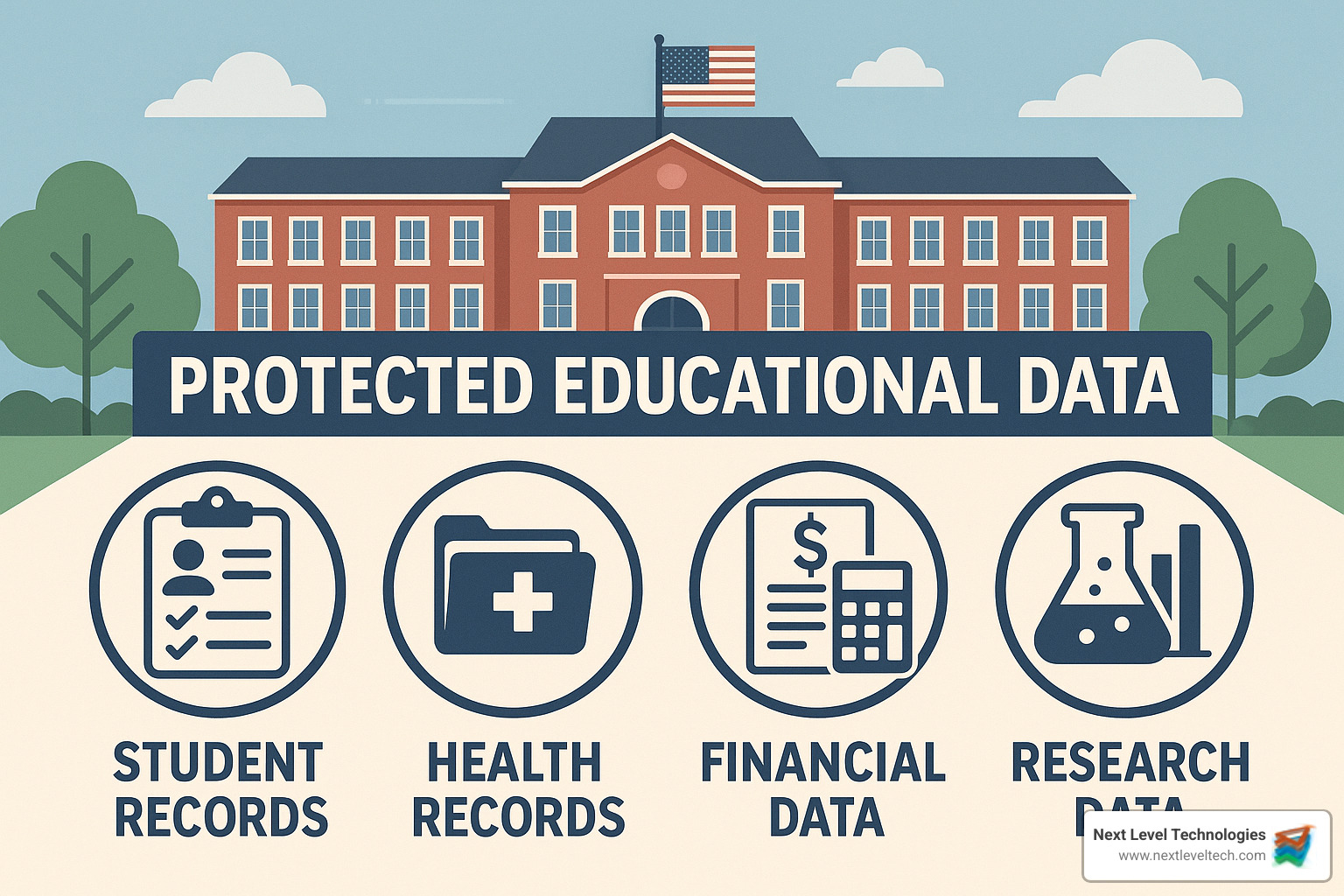
Student Personally Identifiable Information (PII) includes names, Social Security numbers, addresses, birth information, parent details, student ID numbers and login credentials.
Educational records include grades, transcripts, attendance records, disciplinary actions, special education documentation, and counseling notes.
Health records in educational settings include immunization records, medical conditions, mental health information, disability documentation, and health insurance details.
Financial data spans tuition payments, financial aid applications, scholarship information, parent financial details, and payment card information.
Research data at colleges and universities includes human subject research, proprietary findings, grant information, intellectual property, and research participant details.
Navigating the maze of regulations affecting schools can feel overwhelming. Let's break down the key laws and standards you need to know:
FERPA (Family Educational Rights and Privacy Act) serves as the cornerstone of educational privacy, giving parents and eligible students control over educational records. Our Columbus team often reminds clients that FERPA violations can directly impact federal funding.
COPPA (Children's Online Privacy Protection Act) protects students under 13 using online services, requiring parental consent before collecting personal information.
HIPAA (Health Insurance Portability and Accountability Act) applies to campus health centers and medical facilities. Our Charleston, WV specialists have helped numerous school clinics implement proper safeguards.
GLBA (Gramm-Leach-Bliley Act) applies if your institution has a financial aid office handling financial data.
PCI DSS (Payment Card Industry Data Security Standard) applies whenever you process credit card payments for tuition, campus stores, or events.
FISMA (Federal Information Security Modernization Act) affects institutions receiving certain types of federal funding.
NIST 800-171 governs the protection of Controlled Unclassified Information in non-federal systems.
GDPR (General Data Protection Regulation) applies if you have international students from the EU.
State Privacy Laws add another layer of complexity, creating a patchwork of requirements that vary by location.
| Regulation | Primary Focus | Key Requirements | Penalties for Non-Compliance |
|---|---|---|---|
| FERPA | Student educational records | Consent for disclosure, access rights, annual notification | Loss of federal funding |
| COPPA | Online privacy of children under 13 | Parental consent, privacy policies, data minimization | FTC fines up to $43,280 per violation |
| HIPAA | Health information | Security safeguards, privacy practices, breach notification | Fines up to $1.5 million per violation category annually |
| GLBA | Financial information | Written security plan, risk assessment, safeguards | Fines up to $100,000 per violation |
| PCI DSS | Payment card data | Network security, access controls, monitoring, testing | Fines from $5,000 to $100,000 per month |
FERPA forms the foundation of IT compliance for education in the United States. Its requirements directly impact your IT systems:
Access Rights require systems to quickly produce complete student records when requested (within 45 days).
Consent Rules generally require written permission before sharing personally identifiable information from educational records.
Audit Logs are essential for proving compliance by maintaining detailed records of who accessed what information and when.
Encryption isn't specifically mandated by FERPA, but it's considered a best practice for protecting sensitive data.
Annual Notices must be sent to parents and eligible students about their FERPA rights.
Directory Information can be disclosed without consent if you've given proper public notice.
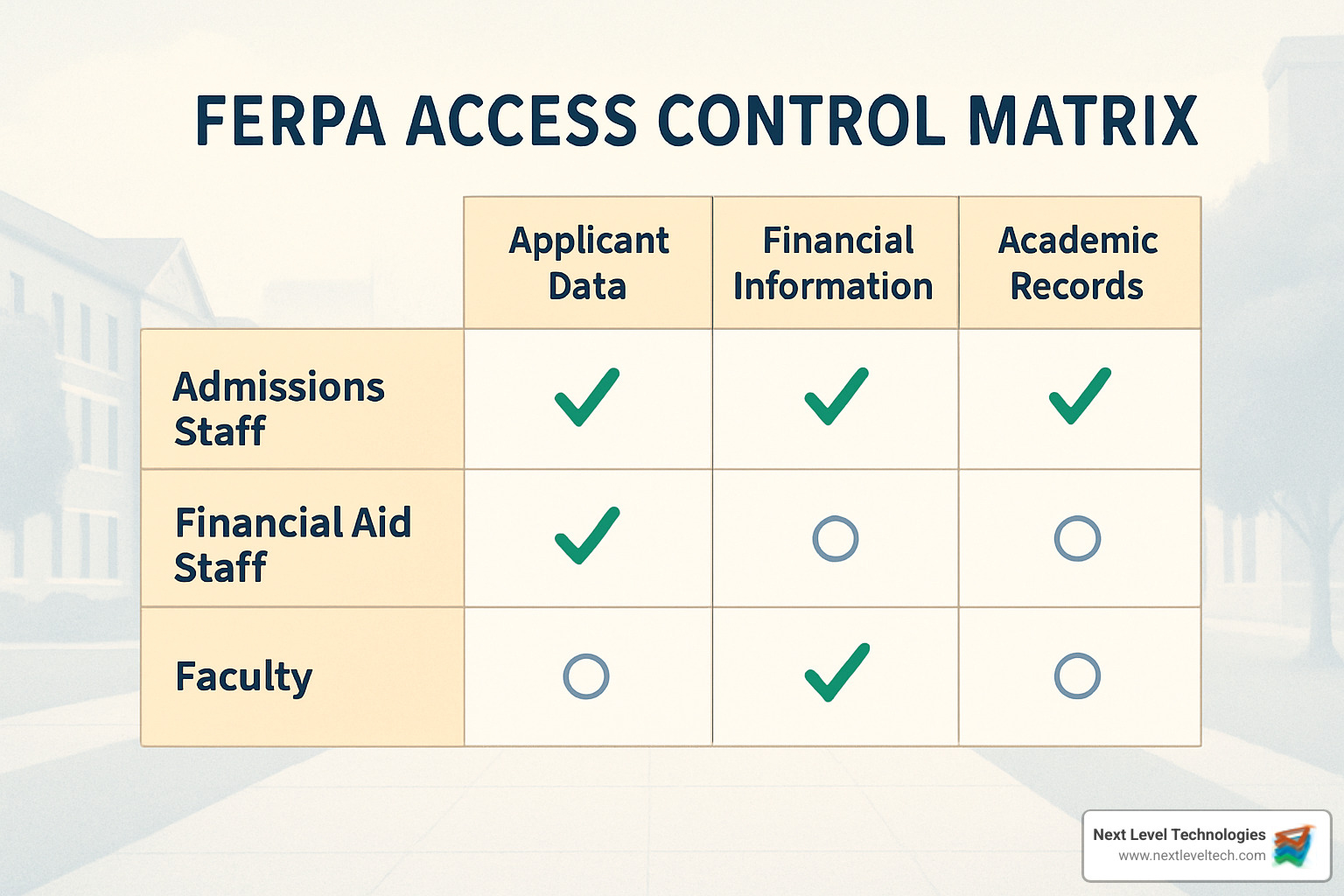
Many schools face additional requirements based on the services they provide:
Health Clinics and Medical Services bring HIPAA into the picture, requiring additional safeguards for protected health information.
Payment Portals and Financial Services trigger both PCI DSS and GLBA requirements for handling sensitive financial data.
Research Grants and Academic Research may require compliance with FISMA or NIST 800-171 for federal research funding.
Freedom of Information Act (FOIA) creates a balancing act for public institutions between transparency and protecting private student information.
Americans with Disabilities Act (ADA) requirements intersect with privacy concerns when handling accommodation documentation.
Creating an IT environment that meets IT compliance for education requirements isn't just about checking boxes—it's about building a secure foundation that protects sensitive data while supporting your educational mission.
Everything starts with a thorough risk assessment—your blueprint for compliance. Our teams in Columbus and Charleston have conducted dozens of these assessments, often finding hidden pockets of sensitive data or unexpected access points.
Zero-trust architecture forms your security foundation by verifying every user and device attempting to access resources—regardless of location. This is particularly valuable for schools with multiple campuses, remote learning programs, and diverse user populations.
Encryption protects information both when it's stored and when it's moving across networks. When one of our Charleston clients experienced a network breach, their properly encrypted student records remained completely secure.
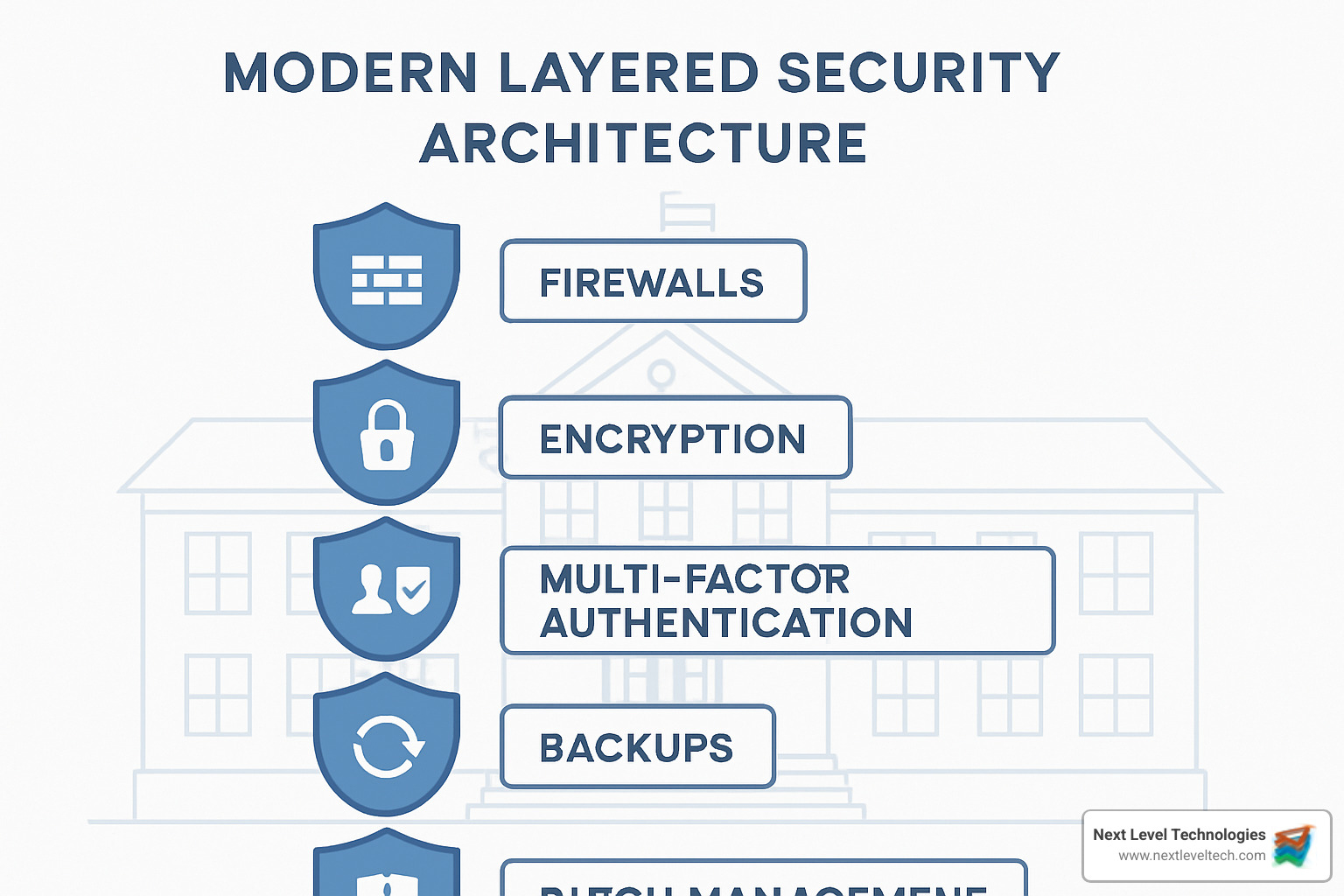
Multi-factor authentication (MFA) adds an essential security layer by requiring users to provide two or more verification factors. After implementing MFA at a Columbus school district, unauthorized access attempts dropped by 98% in the first year.
Regular backups and disaster recovery planning ensure you're prepared for the worst. When ransomware hit a small college in West Virginia, their comprehensive backup strategy allowed them to restore operations within 24 hours without paying the ransom.
Consistent patch management closes vulnerabilities before they can be exploited. Our Cybersecurity Solutions for Education include automated patch management that keeps systems current without overwhelming your IT staff.
Implementing IT compliance for education doesn't happen overnight. Here's a practical roadmap:
Establish a cross-functional compliance committee including IT, administration, faculty, and legal representatives.
Adopt a recognized framework like the NIST Cybersecurity Framework (CSF) as your foundation.
Conduct a comprehensive gap analysis to reveal where you stand and what needs fixing.
Develop clear, enforceable policies that are understandable to everyone—not just IT professionals.
Implement technical controls and provide staff and student training to ensure everyone understands their role.
Establish regular monitoring, measurement, and assessment for continuous improvement.
For more guidance, check out our detailed guide on IT Security Policy Compliance.
A secure architecture forms the technical backbone of IT compliance for education. Essential elements include:
Network segmentation protects your most sensitive systems by creating separate zones within your network, containing potential breaches and limiting lateral movement by attackers.
Endpoint protection secures individual devices that access your network through next-generation antivirus software, application whitelisting, and disk encryption.
Cloud configuration hardening prevents accidental exposure of sensitive student information through proper configuration, strong access controls, and regular security reviews.
Security Information and Event Management (SIEM) systems centralize logging and monitoring, giving you visibility across your entire environment.
Data Loss Prevention (DLP) tools identify sensitive information and prevent it from leaving your network through unauthorized channels.
A K-12 district we worked with in Ohio saw a 75% reduction in security incidents after adopting this architecture, with their IT director noting, "We're not just compliant on paper—we're genuinely more secure, and that's what matters most."
Keeping your school's data safe requires managing who can access what, ensuring your vendors follow the rules, and knowing exactly what to do if something goes wrong.
Access management is your school's security checkpoint. By implementing role-based access control (RBAC), you ensure teachers, administrators, students, and staff can only access the information they need to do their jobs. Just-in-time (JIT) privileged access provides temporary liftd permissions only when absolutely necessary.
"After implementing JIT access at our university, we reduced our potential attack surface dramatically," shared one IT director we worked with. "Over 85% of our administrative accounts no longer have standing privileges—they request access only when needed."
For vendor management, your compliance responsibility doesn't end when you outsource. Before signing any contract:
Our Charleston team recently helped a school district find through our vendor assessment process that their student information system provider was storing unencrypted student data in an offshore data center—a clear FERPA violation.
Even with the best prevention measures, breach management requires advance planning. Your incident response plan should define containment procedures, forensic investigation processes, and communication protocols that comply with regulatory requirements.
IT compliance for education requires ongoing vigilance. The education sector's dynamic environment, with students and faculty coming and going each semester, makes continuous monitoring especially important.
User activity logging forms the backbone of this monitoring, recording who accessed protected data, what they accessed, when it happened, where they connected from, and what actions they took.
Modern monitoring systems can actively look for suspicious patterns through anomaly detection, which uses machine learning to understand normal behavior and alert you when something unusual happens.
Regular compliance scans proactively check your systems against current requirements. We recommend monthly scans for critical systems, quarterly scans for everything else, and additional checks after significant infrastructure changes.
Dashboard reporting helps make monitoring data meaningful to different stakeholders, from board members who want a simple status overview to IT teams who need detailed technical information.
As the Verizon Data Breach Investigations Report consistently shows, social engineering remains one of the top causes of data breaches in education, so monitoring should include metrics on phishing simulation performance and security awareness training completion rates.
Despite your best prevention efforts, breaches can still happen. Having a well-rehearsed breach response playbook ensures your institution can respond effectively while meeting regulatory requirements.
When containment is your first priority, quickly identify affected systems and data, preserve digital evidence, and activate your incident response team using pre-established communication channels.
The forensic investigation determines how the breach happened, when it started, and exactly what information was compromised. This investigation must be thorough and well-documented to inform both recovery efforts and compliance obligations.
Legal considerations should never be an afterthought. Immediately notify legal counsel to determine which regulations apply and what your notification obligations might be.
Your communication strategy should include templates for internal communications, external messages for students and parents, and formal notifications for regulatory bodies.
During remediation and recovery, address the vulnerability that led to the breach before restoring systems. Educational institutions should pay special attention to the 45-day FERPA window for responding to record requests, which doesn't pause during a breach.
For more information on preparing for and responding to security incidents while maintaining compliance, check out our guides to IT Compliance Assessments and IT Compliance Monitoring.
Creating a robust IT compliance for education program requires equipping your people with the knowledge and skills they need to protect sensitive data every day.
Security awareness training is where it all begins. Our approach isn't about boring compliance videos—we create engaging, role-specific training that resonates with administrators, faculty, staff, and students alike.
"The scenarios in your training actually reflected situations we face daily," shared a principal from a Columbus school district. "For the first time, our staff understood why following proper protocols matters when handling student records."
Our cybersecurity experts develop customized simulations that mirror real educational environments—like handling a parent's request for records or spotting sophisticated phishing emails.
Tabletop exercises bring together key stakeholders to work through realistic incident scenarios without the pressure of an actual breach. We recommend conducting these exercises annually, using scenarios based on actual incidents in the education sector.

Compliance automation software can dramatically reduce the administrative burden of maintaining compliance by streamlining policy distribution, tracking training completion, monitoring systems for configuration issues, generating audit-ready reports, and alerting you to potential compliance gaps.
Identity and Access Management (IAM) platforms provide the critical foundation for controlling who can access what information, enabling automated provisioning as roles change, strengthening security with multi-factor authentication, improving user experience through single sign-on, maintaining detailed access logs, and facilitating regular access reviews.
Technical controls alone won't ensure IT compliance for education. The most secure schools and universities have built cultures where protecting data is simply "how we do things here."
Leadership buy-in sets the tone for the entire institution. When presidents, superintendents, and principals demonstrate that security matters, people notice.
Cross-departmental teams break down silos that often hinder effective compliance. These collaborative groups should include voices from IT, student affairs, academic departments, HR, legal counsel, and administration.
Periodic reviews keep your compliance program fresh and effective. We help institutions establish regular cadences for reviewing policies and procedures—annually at minimum, but also after organizational changes, when new regulations emerge, or following security incidents.
Formal certifications provide educational institutions with structured frameworks for IT compliance for education while demonstrating their commitment to protecting sensitive data.
SOC 2 certification focuses on controls relevant to security, availability, processing integrity, confidentiality, and privacy—valuable for institutions that provide services to other organizations or handle particularly sensitive research data.
ISO 27001 provides an internationally recognized framework for information security management, particularly valuable for institutions with international programs or students.
GLBA Safeguards compliance is mandatory for educational institutions that provide financial services, including processing student loans.
Regardless of which certifications you pursue, audit readiness should be an ongoing priority through current documentation, regular control testing, prompt addressing of weaknesses, evidence preservation, and staff preparation.
By combining the right tools, effective training, and a commitment to continuous improvement, educational institutions can build sustainable IT compliance for education programs that protect sensitive data while supporting their educational mission.
IT Compliance CertificationsUnderstanding IT Compliance Requirements for Different Industries
When schools fail to maintain IT compliance for education, the consequences can be severe:
Financial penalties hit hardest. FERPA violations can result in the complete loss of federal funding—a devastating blow for most institutions. Beyond FERPA, HIPAA violations can cost up to $1.5 million per violation category annually, while GLBA non-compliance carries potential $100,000 penalties per violation. State privacy laws add another layer of financial risk.
Legal consequences include lawsuits from affected students and parents, potentially escalating to class action litigation for larger breaches. Defense costs alone can strain budgets, not to mention potential settlements.
Operational disruption creates significant challenges. Schools may face mandatory remediation requirements, increased regulatory scrutiny, surprise audits, and even system shutdowns during investigations.
Reputational damage may be most costly long-term. Our cybersecurity experts have witnessed how quickly trust erodes after a compliance failure becomes public. One private school client in Columbus experienced a 12% drop in applications following a relatively minor data breach.
Keeping policies current is essential to IT compliance for education:
Annual comprehensive reviews ensure alignment with current regulations, institutional practices, evolving technologies, and the changing threat landscape.
Trigger-based reviews should occur when new education privacy regulations emerge, when you make significant changes to IT infrastructure or services, following any security incident, during major organizational restructuring, or when adopting new educational technologies.
Continuous monitoring between formal reviews helps track regulatory changes, collect feedback on policy effectiveness, document implementation challenges, and log improvement suggestions.
Diverse stakeholder involvement improves policy quality. "When we included representatives from IT, legal, academic affairs, and student services, we found blind spots in our policies that no single department had recognized," shared a college administrator we work with in West Virginia.
Vendor management represents one of the trickiest aspects of IT compliance for education. Key contract elements include:
Data protection requirements that explicitly require vendors to protect data according to all applicable education privacy laws, prohibit them from using institutional data beyond providing the contracted service, mandate encryption, and require data minimization.
Security measures should be clearly defined, including minimum security standards, regular security assessments, prompt patching, and security training for vendor staff.
Breach notification terms should define what constitutes a security incident, establish specific notification timeframes (typically 24-72 hours), detail required content of breach notifications, and outline cooperation requirements for investigation.
Verification through compliance certifications provides ongoing assurance. Specify required certifications like SOC 2 or ISO 27001, set frequency requirements for renewal, and reserve the right to request and review documentation.
Audit rights allow you to verify vendor security and compliance. Define the scope and frequency of permitted audits and require vendor cooperation.
Contract end provisions should require secure return or destruction of data, establish timeframes for this process, and mandate certification of destruction.
Subcontractor management terms should require approval for subcontractors, ensure all security and compliance obligations flow down to them, and hold the primary vendor responsible for subcontractor compliance.
Navigating the complex landscape of IT compliance for education requires expertise, diligence, and a commitment to continuous improvement. Throughout this guide, we've seen how educational institutions face unique challenges in balancing open learning environments with strict data protection requirements.
The stakes couldn't be higher. From losing federal funding to suffering reputational damage that affects enrollment for years, the consequences of non-compliance are severe. Yet with the right approach, compliance becomes more than just checking regulatory boxes—it transforms into a strategic advantage that demonstrates your commitment to student privacy and institutional integrity.
Here at Next Level Technologies, our teams in Columbus, Ohio and Charleston, WV bring specialized cybersecurity expertise custom specifically to the education sector. Our specialists undergo extensive training in educational compliance requirements and stay current with evolving threats and regulations.
"Working with Next Level Technologies transformed compliance from a constant worry to a structured program we can confidently manage," one university CIO told us after implementing our recommendations.
We've guided dozens of educational institutions—from small K-12 schools to major universities—through every step of their compliance journey. Our approach is comprehensive yet practical:
What makes our approach different is that we understand every educational institution has its own unique needs, constraints, and priorities. That's why we develop customized compliance programs rather than one-size-fits-all solutions. Our managed IT services provide ongoing support, ensuring your compliance posture remains strong even as regulations and technologies evolve.
To learn more about how Next Level Technologies can support your IT compliance for education needs, visit our managed IT services page or contact our education specialists today.
In today's threat landscape, compliance isn't just about avoiding penalties—it's about protecting your institution's mission, reputation, and the students you serve. Let us help you transform compliance from a challenge into a strength.
Unlock innovation & cut costs with expert Open Source managed services. Boost security, efficiency, and compliance for your business.
February 2, 2026
Compare IT Service Management Tools. Learn key features, benefits, and how AI can transform your IT operations for peak efficiency.
January 30, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
