Why Your Business Can't Afford to Ignore Compliance Gaps

Compliance Gap Analysis is the structured process of evaluating your organization's current policies, procedures, and security controls against specific regulatory requirements or industry standards—like HIPAA, PCI DSS, SOC 2, or ISO 27001—to identify where you fall short and what needs to be fixed.
Quick Answer: What You Need to Know
A Compliance Gap Analysis helps you:
- Identify specific areas where your practices don't meet regulatory standards
- Avoid costly fines and legal penalties by addressing issues before auditors find them
- Prioritize remediation based on risk severity and business impact
- Build stakeholder trust by demonstrating proactive compliance efforts
- Improve operational efficiency by streamlining processes and optimizing resources
Compliance requirements are a constantly moving target as new regulations, industry standards, and internal policies evolve in response to changing risks. For many small and mid-sized businesses, this creates a challenging landscape where small cracks in compliance practices can lead to significant issues impacting data security, customer trust, and your bottom line.
A compliance gap analysis reveals exactly where your organization stands today compared to where it needs to be. Rather than waiting for an audit to expose vulnerabilities, this proactive assessment gives us a clear roadmap for closing gaps before they result in breaches, fines, or reputational damage. It's not just about avoiding penalties—it's about building a more secure, efficient, and trustworthy organization.
The process involves comparing your current security controls, data handling procedures, and documentation against the specific requirements of regulations that apply to your industry. Whether you're handling cardholder data, protected health information, or simply want to demonstrate strong security practices to customers, a gap analysis identifies precisely where you need to improve and helps you allocate resources effectively.
I'm Steve Payerle, President of Next Level Technologies, and over the years I've helped businesses across Ohio and West Virginia strengthen their security posture through thorough Compliance Gap Analysis assessments. Our team's extensive cybersecurity training enables us to guide organizations through this critical process, turning compliance from a burden into a competitive advantage.
What is a Compliance Gap Analysis and Why is it Crucial?
At its core, a Compliance Gap Analysis is a structured evaluation that compares your organization's current policies, procedures, and practices against specific regulatory standards. Think of it as taking a snapshot of "where you are now" and holding it up against "where you need to be." This strategic review helps pinpoint disparities, or "gaps," that could expose your business to risk.
This process is vital for ensuring legal adherence and fulfilling internal policies. It plays a foundational role in an organization's Governance, Risk, and Compliance (GRC) strategy, serving as both a diagnostic device and a planning tool to proactively address deficiencies.

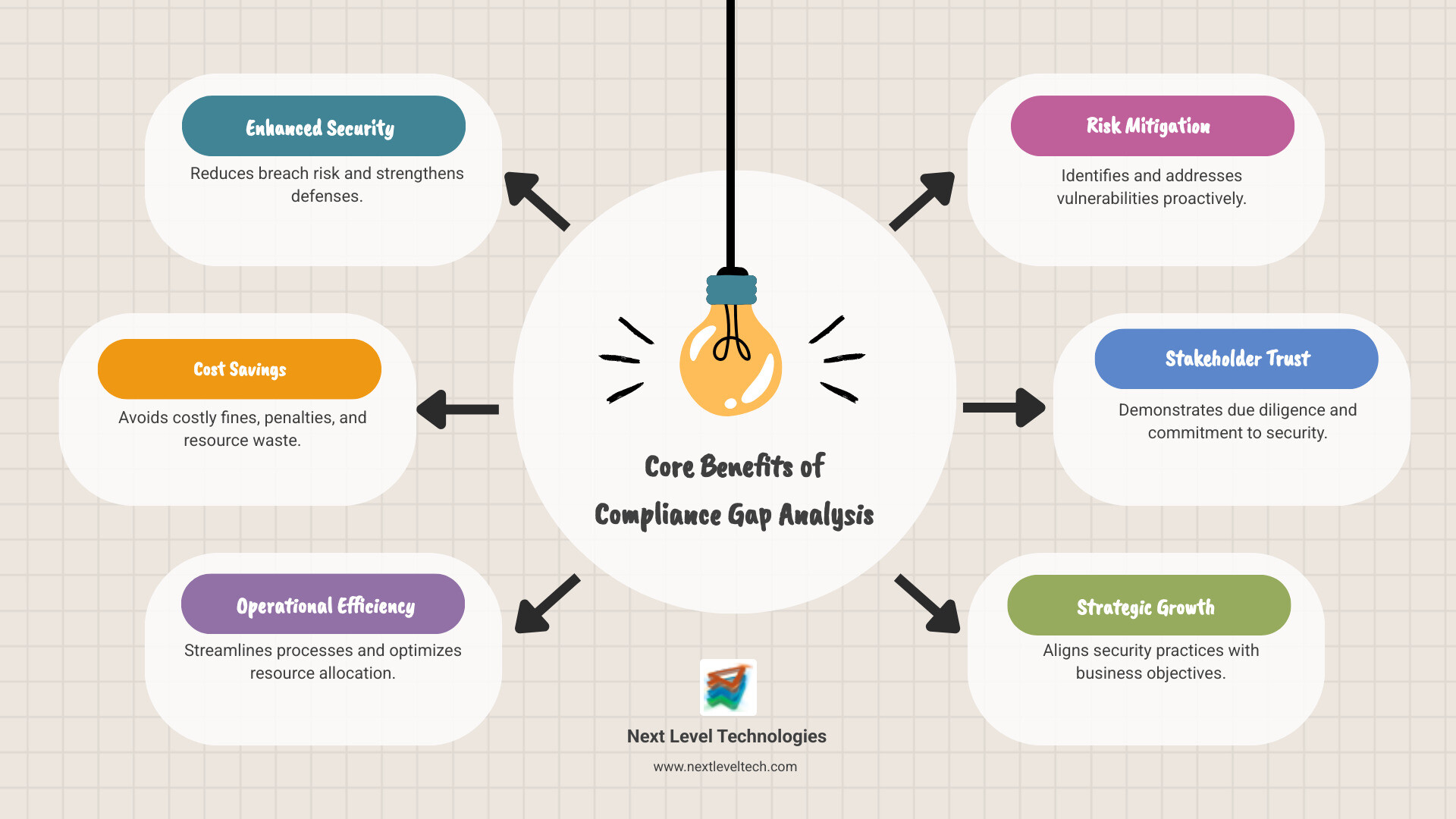
The Primary Benefits of a Compliance Gap Analysis
Conducting a thorough Compliance Gap Analysis offers advantages that extend far beyond simply avoiding fines. Here's how it benefits organizations like yours in Ohio and West Virginia:
- Improved Security Posture: By revealing where practices don’t meet regulatory standards, a gap analysis allows for targeted improvements. This proactive approach minimizes financial, legal, and reputational risks and strengthens your overall security.
- Cost Savings: A gap analysis identifies precise areas needing attention, which helps optimize spending on necessary upgrades and avoid redundant investments. Early detection of compliance risks can prevent costly breaches, fines, and legal battles.
- Operational Efficiency: Identifying and streamlining compliance processes leads to more efficient operations. Addressing inefficiencies and redundant controls improves workflows and resource allocation, boosting productivity.
- Optimized Resource Allocation: A gap analysis enables you to allocate the right resources—people, technologies, and investments—for compliance tasks, ensuring efforts are focused on the most impactful areas.
- Improved Reputation: Demonstrating a proactive commitment to compliance and data security builds trust with customers, partners, and auditors. This transparency can improve your market standing and provide a competitive edge.
- Proactive Risk Management: A gap analysis is a critical tool for understanding risks and weaknesses in advance. It allows you to make intentional decisions about improvements, reducing surprises and ensuring you're prepared for disruptions.
- Strategic Growth: Aligning compliance efforts with business goals supports strategic growth. By ensuring adherence to standards, you can confidently pursue new markets and partnerships, knowing your compliance foundation is solid.
The timing of a Compliance Gap Analysis is crucial for its effectiveness. While many organizations see it as a one-off task, there are several optimal times to perform this assessment:
- Implementing New Regulations: When new laws or industry standards emerge (e.g., updates to HIPAA or PCI DSS), a gap analysis is essential to understand how your current practices measure up against the new requirements.
- Preparing for an Audit: Conducting a gap analysis before a formal audit (like a SOC 2 attestation) allows you to proactively identify and address deficiencies. This ensures you're audit-ready and increases the likelihood of a successful outcome.
- Post-Security Incident: After a data breach, a gap analysis can help identify the underlying weaknesses that contributed to the event, allowing for targeted improvements to prevent future occurrences.
- Major Organizational Changes: Mergers, acquisitions, or significant changes in business operations (like launching new services or adopting new technologies) necessitate a fresh look at compliance to ensure alignment with all relevant standards.
- Annual or Bi-annual Schedule: For continuous compliance, it’s best practice to establish a routine schedule for gap analyses. This ensures compliance remains a continuous process, not a one-time event, and helps maintain a strong compliance posture.
Its Role in a Broader Compliance Program
A Compliance Gap Analysis isn't just a standalone exercise; it's an essential component of a robust compliance program, serving as the foundation for your entire strategy.
- Foundation for Compliance Efforts: Whether starting a new compliance initiative or maintaining existing adherence, the gap analysis provides the initial roadmap. It helps you understand the current state, identify where you fall short, and set the course for corrective action.
- Roadmap for Improvements: The findings from a gap analysis directly inform the development of a remediation plan. This plan becomes your actionable roadmap, outlining specific steps, timelines, and responsibilities to close identified gaps.
- Demonstrating Due Diligence: Regularly conducting and acting upon gap analyses demonstrates a commitment to due diligence. This is crucial for satisfying regulatory bodies, reassuring customers, and proving to stakeholders that your organization takes compliance seriously.
- Continuous Compliance Cycle: Compliance is not a destination but a journey. The gap analysis feeds into a continuous cycle of assessment, remediation, monitoring, and re-assessment. Regular gap assessments help maintain your compliance standing and adapt to evolving regulatory landscapes.
The 6-Step Process for a Successful Compliance Gap Analysis
Navigating compliance complexities can feel like a maze, but a structured approach provides a clear path. Our team at Next Level Technologies, with our extensive cybersecurity training, guides businesses in Ohio and West Virginia through a proven 6-step process for a successful Compliance Gap Analysis. This actionable roadmap takes you from initial assessment to effective remediation, involving key stakeholders every step of the way.
Step 1: Define the Scope and Objectives
This initial step clarifies the purpose and sets clear targets for the compliance review. We need to know exactly what we're looking for before we dive in.
- Applicable Regulations: We identify all relevant regulatory requirements and industry standards for your business, such as HIPAA, PCI DSS, SOC 2, or ISO 27001. For our clients in Ohio and West Virginia, we cover all federal and state-specific mandates.
- Business Units Involved: We pinpoint which departments, teams, or functions will be part of the assessment to ensure no critical areas are missed.
- IT Systems: We list all IT systems, applications, and infrastructure that store, process, or transmit data relevant to the chosen regulations.
- Processes & People: We define the specific workflows, policies, and personnel whose actions impact compliance, from data entry to employee training.
- Setting Clear Targets: We establish measurable goals for the analysis. Are we aiming for full compliance, preparing for an audit, or assessing our current maturity level? Clear objectives guide the entire process.
Step 2: Assess the Current State
With the scope defined, we capture the current compliance landscape by diving deep into your existing environment.
- Data Collection: We gather all relevant information, including existing policies, procedures, contracts, system configurations, and past audit reports.
- Reviewing Policies & Procedures: We carefully examine your documented policies and operational procedures to understand what's supposed to be happening.
- Interviewing Stakeholders: We engage key personnel across departments. These interviews provide invaluable insights into day-to-day practices and undocumented processes, helping us understand what's actually happening.
- Technical Control Testing: Leveraging our extensive cybersecurity training, our team performs technical assessments like vulnerability scans, penetration testing, and configuration reviews to verify the effectiveness of security controls. For guidance, we often refer to resources like the Security Self-Assessment Guide for Information Technology Systems.
- Documenting Existing Controls: We compile a comprehensive record of all current controls, noting their effectiveness and alignment with your policies.
Step 3: Identify and Document the Gaps
Here, we compare your current state against the required state to find the "gaps" in your Compliance Gap Analysis.
- Comparing Current State to Requirements: We systematically cross-reference your current practices and controls against each requirement of the chosen regulatory frameworks.
- Pinpointing Deficiencies: Any area where your current state doesn't meet the required standard is identified as a gap, such as missing controls, ineffective processes, or outdated policies.
- Logging Deviations: Each identified gap is carefully documented with a clear description, the specific requirement it violates, and its potential impact.
- Noting Risk Level: We assign an initial risk level (e.g., high, medium, low) to each gap based on its potential severity and likelihood of exploitation.
- Real-world Examples:
- For HIPAA compliance in a Charleston, WV, healthcare practice, a gap might be sending patient health information (PHI) via unencrypted email or improperly disposing of paper PHI records.
- For a Columbus, OH, firm aiming for PCI DSS compliance, gaps could include outdated firewalls or not enforcing multi-factor authentication (MFA) for administrative access to cardholder data.
- A tech startup preparing for SOC 2 attestation might have weak password policies or a missing incident response plan, which are definite control gaps.
This step involves strategically deciding which gaps to tackle first, as not all gaps are created equal.
A common point of confusion is the difference between a Compliance Gap Analysis and a risk assessment. While both are crucial, they have distinct focuses:
| Feature | Compliance Gap Analysis | Risk Assessment |
|---|
| Primary Goal | Identify disparities between current practices and required standards/regulations. | Identify threats, vulnerabilities, and their potential impact/likelihood. |
| Focus | Adherence to specific controls, policies, and regulatory mandates. | Evaluation of risk exposure (likelihood x impact) to assets. |
| Outcome | A list of missing or insufficient controls/practices to meet compliance. | A prioritized list of risks and recommended mitigation strategies. |
| "What if" | "What if we don't meet this regulation?" | "What if this threat exploits this vulnerability?" |
- Risk Matrix: We use a risk matrix to evaluate each gap, prioritizing based on potential impact (e.g., fines, data breach) and likelihood. High-risk gaps, like failing to encrypt sensitive data, are always a top priority.
- Assessing Business Impact: We consider how each gap could affect your business operations, finances, and customer trust. A weak data encryption policy for a SaaS company, for example, would be a high-risk gap.
- Likelihood of Exploitation: We evaluate the probability that a vulnerability linked to the gap could be exploited.
- Creating a Corrective Action Plan: For each prioritized gap, we develop a detailed remediation plan outlining specific actions, necessary resources (people, technology, budget), and a timeline.
- Assigning Ownership: Clear ownership is assigned for each remediation task to ensure accountability and drive progress.
- Setting Timelines: Realistic deadlines are established for each action item to keep the remediation process on track.
This step is about execution: actively working to close the identified gaps based on the remediation plan.
- Closing Identified Gaps: This involves the practical implementation of the corrective actions outlined in our plan.
- Implementing New Controls: We introduce new security controls, processes, or technologies where deficiencies were found, such as implementing AES-256 encryption and MFA to meet PCI DSS standards.
- Updating Policies: Existing policies and procedures are revised to align with compliance requirements and new controls, ensuring documentation reflects current best practices.
- Technical Improvements: This could involve upgrading software, patching systems, or implementing new security tools. Our team's technical experience is invaluable here, ensuring improvements are effective.
- Staff Training: A crucial part of remediation is training employees on new policies and security best practices. Well-trained staff are a powerful defense against common vulnerabilities like human error.
Step 6: Monitor, Report, and Repeat
Compliance is an ongoing commitment. This final step establishes the framework for continuous improvement and sustained adherence.
- Continuous Monitoring: We set up processes for ongoing monitoring of controls to ensure they remain effective and that new gaps don't emerge as your business evolves.
- Regular Reviews: We periodically conduct internal reviews to check the status of remediation efforts and the overall compliance posture, such as annual or bi-annual checks for SOC 2.
- Verifying New Controls: We ensure that all newly implemented controls are working as intended and effectively closing the identified gaps.
- Reporting Progress to Leadership: Regular reports are provided to management, detailing progress, remaining risks, and any new challenges to maintain buy-in for compliance initiatives.
- Adapting to Regulatory Changes: The regulatory landscape is constantly shifting. We stay vigilant for new regulations and adapt our compliance program accordingly, initiating a new gap analysis cycle when needed.
Leveraging Technology and Best Practices
In today’s digital world, relying solely on manual processes for Compliance Gap Analysis can be like trying to catch smoke with a net—frustrating and largely ineffective. We believe in moving beyond cumbersome spreadsheets to harness the power of technology, combined with the invaluable insights of expert human judgment, to make this process efficient and actionable.
How Technology and Automation Improve a Compliance Gap Analysis
The manual approach to compliance gap analysis is notoriously time-consuming and resource-intensive. It often involves endless spreadsheets, manual scanning of regulatory websites, and laborious testing. This is where technology steps in to be our superhero.
- Automated Data Collection: Automation platforms can integrate with your existing systems to automatically collect evidence and data, significantly reducing the time spent on repetitive, labor-intensive tasks.
- Real-time Monitoring: Instead of periodic checks, automated tools provide continuous monitoring of your systems and processes, offering real-time visibility into your compliance posture.
- Pre-built Framework Templates: Modern compliance software comes with pre-authored frameworks and control mappings for standards like SOC 2, ISO 27001, HIPAA, and PCI DSS. This eliminates the need for manual compilation and mapping, speeding up Step 1 (Defining Scope) and Step 3 (Identifying Gaps).
- Streamlined Reporting: Automation can quickly generate comprehensive reports, dashboards, and audit trails, making it easier to track progress, report to stakeholders, and prepare for audits.
- AI-powered Remediation Guidance: Some advanced platforms offer AI-powered guidance for remediation, helping to prioritize high-risk gaps and suggest specific actions, making Step 4 (Prioritizing Gaps) much more efficient.
- Reducing Human Error: By automating comparisons and data collection, technology minimizes the risk of human error that can plague manual assessments, leading to more accurate and reliable results.
Organizations lacking the knowledgeable personnel and resources required for a manual approach often turn to automation to simplify and accelerate their Compliance Gap Analysis process.
Common Pitfalls and How to Avoid Them
Even with the best intentions, organizations can stumble during a Compliance Gap Analysis. Recognizing these common pitfalls allows us to steer clear of them.
- Treating it as a One-Time Project: Compliance is dynamic. Viewing the analysis as a "check-the-box" activity means you'll quickly fall behind. Avoid this by scheduling regular, recurring gap analyses (annually or bi-annually) and integrating it into a continuous compliance program.
- Lack of Stakeholder Buy-in: Without support from leadership and engagement from various departments, remediation efforts can stall. Avoid this by involving key stakeholders from the outset, communicating the benefits of compliance, and ensuring clear ownership for tasks.
- Analysis Paralysis: Getting bogged down in endless data collection or over-analyzing minor issues can prevent action. Avoid this by setting clear objectives, prioritizing gaps based on risk, and focusing on actionable improvements rather than perfection.
- Forgetting to Reassess Assumptions: As your organization grows or changes, the initial assumptions about critical functions or risks might become outdated. Avoid this by regularly reviewing and updating your business impact analysis (BIA) and risk assessments, especially after significant organizational changes.
- Vague Remediation Plans: A plan that lacks specific actions, timelines, or assigned owners is destined to fail. Avoid this by creating robust, detailed action plans with clear steps, realistic deadlines, and named individuals responsible for each task.
Best Practices for an Actionable Analysis
To ensure your Compliance Gap Analysis is not just an academic exercise but a powerful tool for improvement, we adhere to several best practices:
- Involve Cross-Functional Teams: Compliance touches every part of your business. Engage IT, legal, HR, operations, and leadership to get a holistic view and foster collective responsibility.
- Engage Experts with Extensive Cybersecurity Training: Interpreting complex regulations and assessing technical controls requires specialized knowledge. Our team at Next Level Technologies, with our extensive cybersecurity training, brings the expertise needed to accurately identify gaps and recommend effective solutions for businesses in Ohio and West Virginia.
- Document Everything Carefully: From the initial scope to identified gaps, remediation plans, and monitoring results, thorough documentation is critical for accountability, audits, and future reference.
- Ensure Continuous Improvement: Compliance is an ongoing process. Use the gap analysis as a starting point for continuous monitoring, regular reviews, and adaptation to evolving regulatory landscapes and business needs.
- Prioritize with a Risk-Based Approach: Not all gaps are equal. Focus resources on high-risk, high-impact deficiencies first.
- Communicate Clearly: Ensure all stakeholders understand the findings, the remediation plan, and their roles in achieving compliance.
Frequently Asked Questions about Compliance Gap Analysis
How often should my organization conduct a compliance gap analysis?
We recommend that organizations conduct a Compliance Gap Analysis at least annually, and more frequently if certain events occur. For example, you should perform one when implementing new regulations, preparing for an audit, after a security incident, or during major organizational changes like mergers or acquisitions. Regular assessments, perhaps bi-annually, are key for continuous compliance and maintaining your security posture.
Who are the key stakeholders that should be involved in the process?
A successful Compliance Gap Analysis requires input from various parts of your organization. Key stakeholders typically include:
- Leadership/Management: For setting scope, providing resources, and prioritizing remediation.
- IT and Security Teams: For assessing technical controls, systems, and data security. Our team at Next Level Technologies often works directly with your IT staff, providing specialized insights.
- Legal and Compliance Officers: For interpreting regulatory requirements and ensuring legal adherence.
- Department Heads/Process Owners: For understanding day-to-day operations and specific departmental policies.
- HR: For policies related to employee training, access management, and data handling.
- Data Protection Officers (if applicable): For privacy-specific regulations like HIPAA or GDPR.
What is the difference between a compliance gap analysis and an audit?
While both involve evaluating your organization's practices, a Compliance Gap Analysis and an audit serve different purposes:
- Compliance Gap Analysis: This is a proactive, internal assessment designed to identify discrepancies between your current practices and required standards before an official audit. Its goal is to pinpoint weaknesses and create a roadmap for remediation, helping you get "audit-ready." It's about self-improvement.
- Audit: This is a formal, independent examination (often by a third party) to verify that your organization is compliant with specific regulations or standards. An audit assesses the effectiveness of your controls and processes at a specific point in time. It typically results in a formal report or attestation and can carry legal implications if non-compliance is found.
A gap analysis helps you prepare for an audit, making the audit process smoother and more likely to result in a positive outcome.
Conclusion
In an changing regulatory landscape, a Compliance Gap Analysis is more than just a defensive measure; it's a proactive strategy for long-term business resilience and growth. By systematically identifying where your practices fall short of requirements, prioritizing those gaps based on risk, and implementing targeted remediation plans, you're not just avoiding penalties—you're building a stronger, more secure, and more trustworthy organization.
At Next Level Technologies, we understand the unique challenges businesses in Ohio and West Virginia face. Our expertise in managed IT services and support, combined with our team's extensive cybersecurity training, positions us as your trusted partner in navigating compliance complexities. We're here to help you turn compliance from a burden into a competitive advantage, ensuring your business is not just compliant, but truly resilient.
Strengthen your compliance with our managed IT services and support






