Don't Get Hacked! Columbus Cybersecurity Providers You Can Trust
July 31, 2025

Get top-tier IT Support Worthington OH. Boost efficiency, secure data, and grow your business with expert managed IT services.
February 3, 2026

Unlock innovation & cut costs with expert Open Source managed services. Boost security, efficiency, and compliance for your business.
February 2, 2026
Compare IT Service Management Tools. Learn key features, benefits, and how AI can transform your IT operations for peak efficiency.
January 30, 2026
July 31, 2025
When seeking Columbus cybersecurity services, it's crucial to look for a provider with a proven track record and deep expertise. Top partners specialize in holistic cybersecurity, offering services like cloud security, 24x7 monitoring, digital forensics, and compliance consulting. Many leverage extensive experience from military or federal backgrounds and hold advanced degrees, ensuring they bring a sophisticated, attacker-focused mindset to your defense.
Protecting your business is no longer an option—it's a necessity. The need for robust Columbus cybersecurity services has never been more urgent. Just recently, the City of Columbus itself faced a significant cyberattack. A foreign threat actor attempted to disrupt the city’s IT infrastructure, leading to some data being accessed and posted on the dark web. This incident serves as a stark reminder that no organization, regardless of size, is immune to sophisticated cyber threats. For businesses in Columbus, proactive cybersecurity is vital. This comprehensive guide will help you understand the landscape of cyber threats and choose the right cybersecurity partner.
I’m Steve Payerle, President of Next Level Technologies. With my team, I've built a dynamic technology services and cybersecurity company in Columbus, Ohio, and Charleston, WV, offering top-tier Columbus cybersecurity services and managed IT solutions. Our experienced staff has extensive cybersecurity training and technical expertise, ensuring your business stays safe and productive.
Hey there, fellow business owners! If you're running a business in Columbus, you know our city is a hub of innovation and growth. But just like in any busy digital landscape, there's another side to the coin: cyber threats. These days, businesses like yours, from the smallest startup to the biggest enterprise, face a constant stream of digital dangers. We're talking about clever foreign threat actors, sneaky ransomware, and frustrating data breaches that can really throw a wrench in your day. Phishing scams, which often look like super legitimate emails, are still tricking even the savviest employees into giving away important info or accidentally downloading nasty malware.
The financial hit from these cyber incidents can be truly massive. It’s not just about the immediate costs of fixing things up. You also have to consider lost work time, potential legal bills, fines from regulators, and, perhaps most painfully, a damaged reputation. When trust goes down, so can your customer base and, ultimately, your revenue. That’s why it’s so incredibly important to understand these common cybersecurity threats and how expert managed IT services, like the Columbus cybersecurity services we offer, can really help you stay safe. For a deeper dive into these dangers, check out our guide on 5 Common Cybersecurity Threats To Small Businesses And How Managed IT Services Can Help.
Just imagine the headache the City of Columbus experienced when its IT infrastructure was hit! This wasn't some minor glitch; it was a foreign cyber threat actor trying to mess with the city's systems. Even though internet access was quickly cut off, some data still managed to slip out and end up on the dark web. The city's tech team, working hand-in-hand with federal authorities, had to work tirelessly to sort it out, even offering credit monitoring to affected folks. This incident is a huge reminder that no one is truly immune, and having a solid plan for when things go wrong is absolutely essential.
It’s not just government entities feeling the heat. We've seen national incidents that ripple right here in Ohio. Take the data breach at DISA Global Solutions, which affected over 3 million people. What's scary is that it went unnoticed for quite a while, showing just how vital continuous monitoring and quick detection truly are. Even big players like T-Mobile have faced consequences, settling a data breach for a staggering $350 million. That's a pretty clear sign that cutting corners on security can be incredibly expensive.
And let’s talk about healthcare for a moment. This sector is a major target, with an alarming 41.2% of third-party data breaches in 2024 hitting healthcare organizations. Why? Because protected health information (PHI) is incredibly valuable to cybercriminals on the dark web. If your business ever faces a breach, knowing what to do is critical. You'll want to get cybersecurity experts involved ASAP for incident response, notify any affected parties, and really beef up your defenses. For individuals, a great first step is to Obtain a free copy of your credit report to keep an eye on things. Learning How To Protect Your Data From Ransomware is also a must-do in today's world.
Cyber threats are constantly changing, but some bad actors just keep showing up. Here’s a peek at what businesses in Columbus are up against:
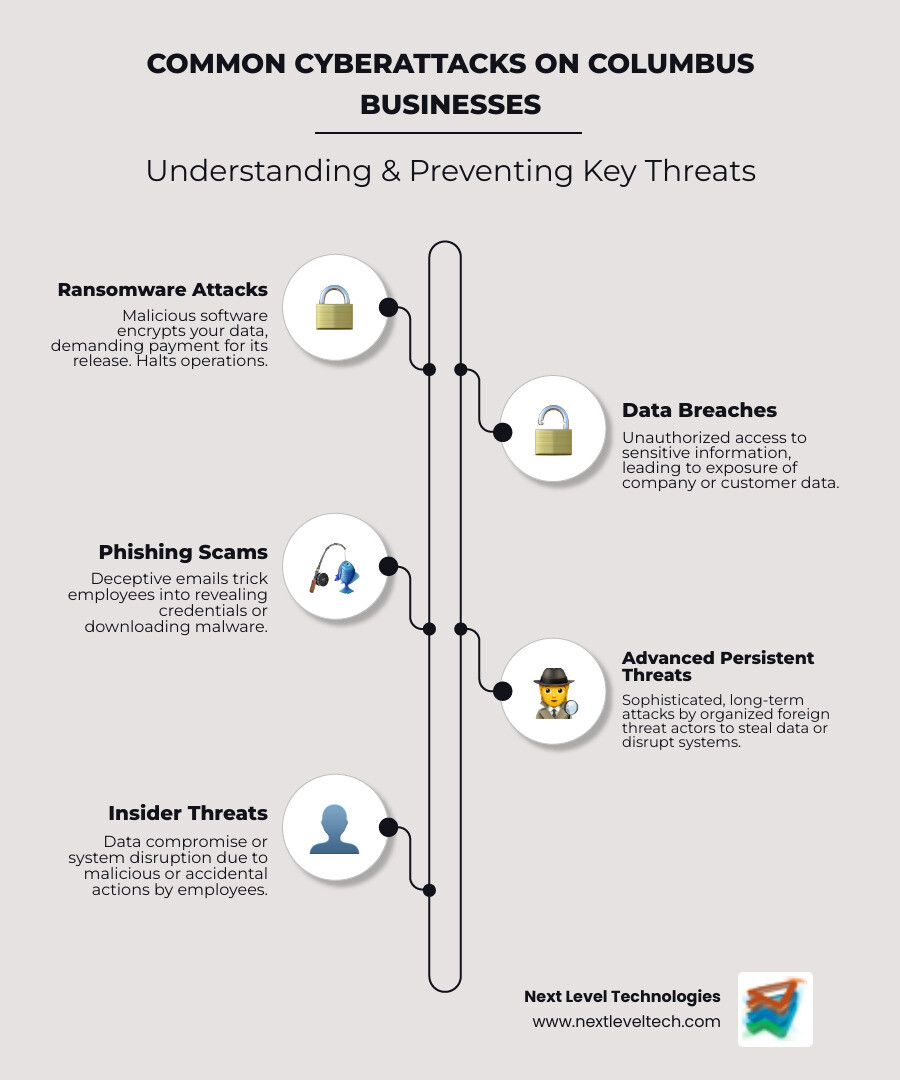
First up, Ransomware. This nasty software locks up your data and demands money to release it. These attacks are on the rise, hitting businesses of all sizes – even micro-businesses and small businesses that might not even realize they’ve been breached until it’s too late.
Then there are Data Breaches and Exfiltration. Beyond just ransomware, cybercriminals are always looking to steal sensitive information. This includes things like personally identifiable information (PII) and protected health information (PHI), which they often sell on the dark web.
You also have to watch out for Phishing and Social Engineering. These are clever tricks designed to manipulate people into giving up confidential information or doing something that compromises security. They exploit human error, which is often the weakest link in any cybersecurity chain.
Finally, don't forget about Insider Threats. While not as common, threats from within your own organization – whether someone acts maliciously or just makes an accidental mistake – can lead to serious data loss or system compromises.
The numbers don't lie: cyberattacks are WAY up. The traditional security methods that worked yesterday simply aren't enough to win against today's sophisticated attackers. We really encourage every business to take a good look at their cybersecurity practices and put strong measures in place. To get you started, we’ve put together 10 Cybersecurity Tips For Small Businesses.
In the face of these escalating threats, businesses in Columbus need to shift from a reactive stance to a proactive one. Waiting for an incident to occur before taking action is like waiting for your house to catch fire before installing smoke detectors. Proactive security, on the other hand, involves anticipating and neutralizing threats before they can cause damage. This is where comprehensive Columbus cybersecurity services come into play.
A Managed Security Service Provider (MSSP) plays a crucial role in building a robust security framework for your business. Unlike traditional IT service providers, MSSPs specialize exclusively in cybersecurity, offering deep expertise and continuous protection. They provide custom security solutions custom to your unique needs, ensuring that your digital assets are safeguarded 24/7 through continuous monitoring and rapid response capabilities.
One of the cornerstones of modern cybersecurity is Managed Detection and Response (MDR). This service goes beyond traditional antivirus solutions, offering real-time threat hunting and continuous monitoring of your IT environment.
For businesses looking for comprehensive protection, managed cybersecurity services offer a full suite of solutions to keep you safe.
Knowing your weaknesses is the first step to becoming strong. Vulnerability assessments and penetration testing are critical services that help businesses identify security gaps before attackers do.
These services are crucial components of effective IT incident management and help ensure your systems are robust. Additionally, for businesses that develop their own software, secure code review helps identify vulnerabilities at the application level.
Navigating the complex world of regulatory compliance can be daunting, but it's non-negotiable for many businesses in Columbus. Our Columbus cybersecurity services can help you meet various industry and government regulations, ensuring you avoid hefty fines and maintain trust.
For comprehensive IT compliance solutions and specialized cybersecurity compliance services, partnering with experts is essential.
Choosing the right Columbus cybersecurity services provider is one of the most critical decisions your business will make. It's not just about finding a vendor; it's about forging a partnership with a team that understands your unique needs and can adapt to the changing threat landscape.
When vetting potential providers, we encourage you to ask the right questions. Look beyond flashy marketing and dig into their experience, methodologies, and commitment to client success. A true partner will integrate seamlessly with your team, offering strategic guidance and personalized support, rather than a one-size-fits-all solution. This partnership approach is what we believe sets us apart from many IT service providers in Columbus, Ohio.
Experience matters, especially in cybersecurity. Look for providers with a long track record of dedicated service in the field, with some of the most established firms having over two or three decades of proven expertise. This longevity indicates stability and a deep understanding of the industry's evolution.
Beyond years in business, scrutinize the team's technical experience and extensive cybersecurity training. Top-tier providers often highlight teams with extensive military or federal government experience, bringing a unique understanding of an "attacker's mindset" and high-stakes operations. It's also common for a high percentage of their team to hold advanced degrees in cybersecurity, showcasing a commitment to cutting-edge knowledge. This level of expertise provides invaluable insights into complex compliance and security challenges.
We at Next Level Technologies pride ourselves on our experienced staff, who possess extensive cybersecurity training and technical expertise. We believe that a highly skilled team is your best defense against sophisticated cyber threats. Look for providers who specialize in your industry (e.g., healthcare, finance, aerospace), as they will have a deeper understanding of your specific regulatory requirements and common threats. Our cybersecurity services are designed with this in mind, ensuring a team with the right skills is always on your side.
A truly effective cybersecurity partner doesn't just react to breaches; they actively work to prevent them.
While many cybersecurity services can be delivered remotely, having a local partner for your Columbus cybersecurity services offers distinct advantages.
We often hear some great questions from businesses like yours here in Columbus when it comes to cybersecurity. It’s a big topic, and it’s natural to have a few head-scratchers! Let’s clear up some common points together.
This is a fantastic question, and it's one that causes a bit of confusion for many. Think of it this way:
A Managed Service Provider (MSP) is like your trusted general practitioner for all things IT. They manage your entire technology ecosystem, from keeping your computers running smoothly to handling network issues and making sure your systems are up-to-running. They’re there for your everyday IT needs, keeping everything humming along.
Now, a Managed Security Service Provider (MSSP) is a specialist. They focus exclusively on cybersecurity. While your MSP might offer some basic security features, an MSSP dives deep into protecting your business from the changing world of cyber threats. This means they bring dedicated, deep expertise in things like advanced threat detection, rapid incident response, navigating complex compliance rules, and offering continuous, specialized security monitoring. When you choose an MSSP, you're getting access to a team with extensive cybersecurity training and specialized threat intelligence, going far beyond what a general IT provider can typically offer. They live and breathe cybersecurity, providing that next level of protection.
The cost of Columbus cybersecurity services for a small business isn't a one-size-fits-all answer, much like buying a car. It really depends on what you need and how much protection you’re looking for.
Several factors play a role in determining the price. For example, the size and complexity of your business – how many employees you have, how many devices are connected, and how intricate your network is – will impact the scope of services needed. Also, the level of service you choose matters. You might opt for basic endpoint protection and firewalls, or you might need fully managed 24/7 monitoring with advanced threat hunting and a dedicated security operations center (SOC). Finally, any specific services you require, like help with compliance (HIPAA or SOC 2), penetration testing, or employee training, will also factor into the overall cost.
Most reputable providers in Columbus, including us at Next Level Technologies, offer custom quotes after an initial risk assessment. This helps us understand your unique vulnerabilities and needs, so we can create a custom solution that provides the best value and protection for your budget. While cybersecurity is certainly an investment, remember to weigh it against the potential financial losses, reputational damage, and legal fees that can come from a devastating cyberattack. Proactive cybersecurity is almost always more cost-effective than trying to recover from a breach.
This is such a crucial question, and the answer is simple: your employees are often your strongest, or unfortunately, your weakest, link in cybersecurity! Employee training and awareness play a monumental role in strengthening your organization's defenses.
Think of your team as your first line of defense. Proper training helps them recognize common cyber threats like tricky phishing emails, social engineering tactics (where attackers try to manipulate people), and suspicious links or attachments. A well-informed team can spot these dangers before they compromise your systems.
Training also reinforces safe practices. This includes vital habits like using strong, unique passwords for different accounts, always enabling multi-factor authentication (MFA) whenever possible, securely handling sensitive data, and knowing when and how to report anything suspicious right away.
A significant number of data breaches happen because of human error. Comprehensive training reduces human error by giving your staff the knowledge and skills to identify and prevent potential threats. Regular training helps create a security-aware culture within your organization. When everyone understands their role in protecting company assets, you build a much stronger defense. Even the most advanced technical security measures can be bypassed by a single click from an unsuspecting employee. Investing in continuous cybersecurity education for your team is truly one of the most effective ways to significantly reduce your risk of a breach.
Our digital world truly offers amazing opportunities, but for businesses here in Columbus, it also comes with some serious risks. We've seen how sophisticated cyber threats have grown, from the City of Columbus cyberattack to the widespread impact of ransomware and data breaches. This really highlights just how critical robust Columbus cybersecurity services have become. Having a proactive strategy, one that blends advanced technology with skilled human expertise, isn't just a nice-to-have anymore. It's truly essential for your business to survive and thrive.
That's why choosing the right partner is so incredibly important. You're not just looking for a vendor; you're seeking a team that genuinely understands your unique needs. Look for a provider with deep technical expertise, extensive cybersecurity training, and a proven track record. They should be proactive in defending your systems and rapid in their response if an incident occurs. A true partner will understand the ins and outs of our local business environment and can provide custom, comprehensive solutions that fit just right.
At Next Level Technologies, we're dedicated to being that trusted partner for businesses just like yours. With our main hub right here in Columbus, Ohio, and strong roots in Charleston, WV, and Worthington, OH, we offer a full suite of managed IT services and specialized cybersecurity solutions. Our goal is to safeguard your operations, keeping your data and systems secure. Our experienced staff boasts extensive cybersecurity training and the technical expertise needed to protect what matters most to you. We're proud to serve businesses of all sizes, including those vital industries that larger providers sometimes overlook, ensuring everyone has access to top-tier cybersecurity.
Don't wait to become the next headline. Take charge of your cybersecurity today and give your business the protection it deserves.
Contact Next Level Technologies for expert Managed IT Services And IT Support.
Get top-tier IT Support Worthington OH. Boost efficiency, secure data, and grow your business with expert managed IT services.
February 3, 2026
Unlock innovation & cut costs with expert Open Source managed services. Boost security, efficiency, and compliance for your business.
February 2, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
