Choosing Your Digital Safety Net: Compare Leading Backup and Recovery Solutions
October 8, 2025

Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026

Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026

Elevate your business with proactive IT Support Charleston WV. Secure, cloud-powered solutions & local expertise for seamless operations.
February 18, 2026
October 8, 2025
Backup and Recovery Solutions are the foundation that keeps your business running when technology fails. Data is your most valuable asset, and losing it can shut down operations in minutes. Top solutions like Veeam, Commvault, Druva, Rubrik, and Cohesity offer comprehensive protection for virtual, cloud, and SaaS environments.
The stakes have never been higher. Research shows that 69% of companies experienced at least one ransomware attack in the past year, while 74% of enterprises are not prepared for modern data risks. Your business faces constant threats from cyberattacks, hardware failures, human error, and natural disasters.
Modern backup is about cyber resilience. Today's solutions protect against ransomware with immutable backups, provide instant recovery, and integrate AI-powered threat detection. This shift from simple data copies to sophisticated defense systems can mean the difference between a minor disruption and a business-ending disaster.
I'm Steve Payerle, President of Next Level Technologies, and I've spent over 15 years helping businesses in Columbus, Ohio and Charleston, WV implement robust Backup and Recovery Solutions that protect against today's complex cyber threats. My team's extensive cybersecurity training has shown me how the right data protection strategy can save businesses from devastating losses.
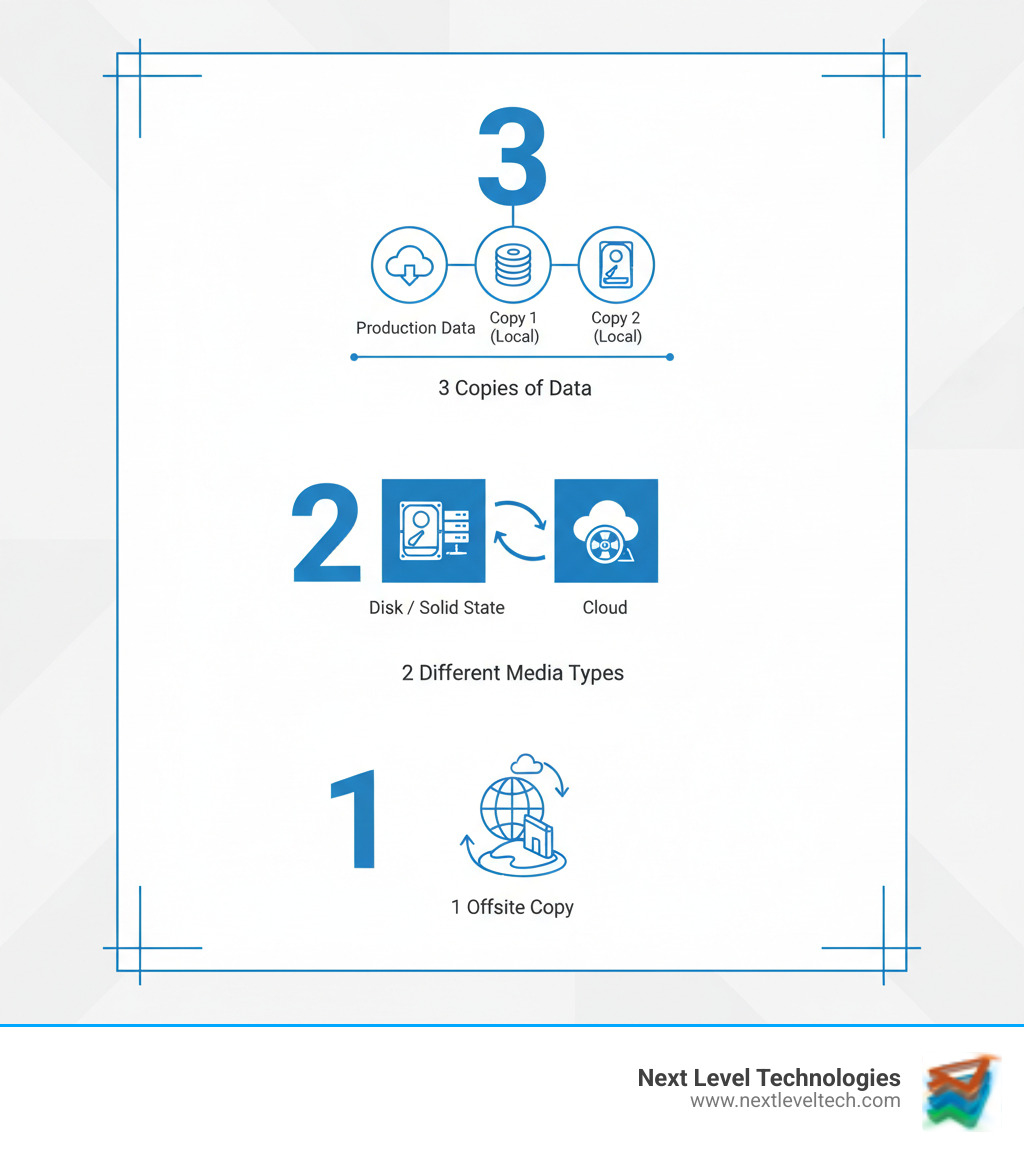
Think of Backup and Recovery Solutions as your business's insurance policy for data. They create copies of your critical information, so when disaster strikes—be it a simple file deletion or a ransomware attack—we can restore your operations quickly.
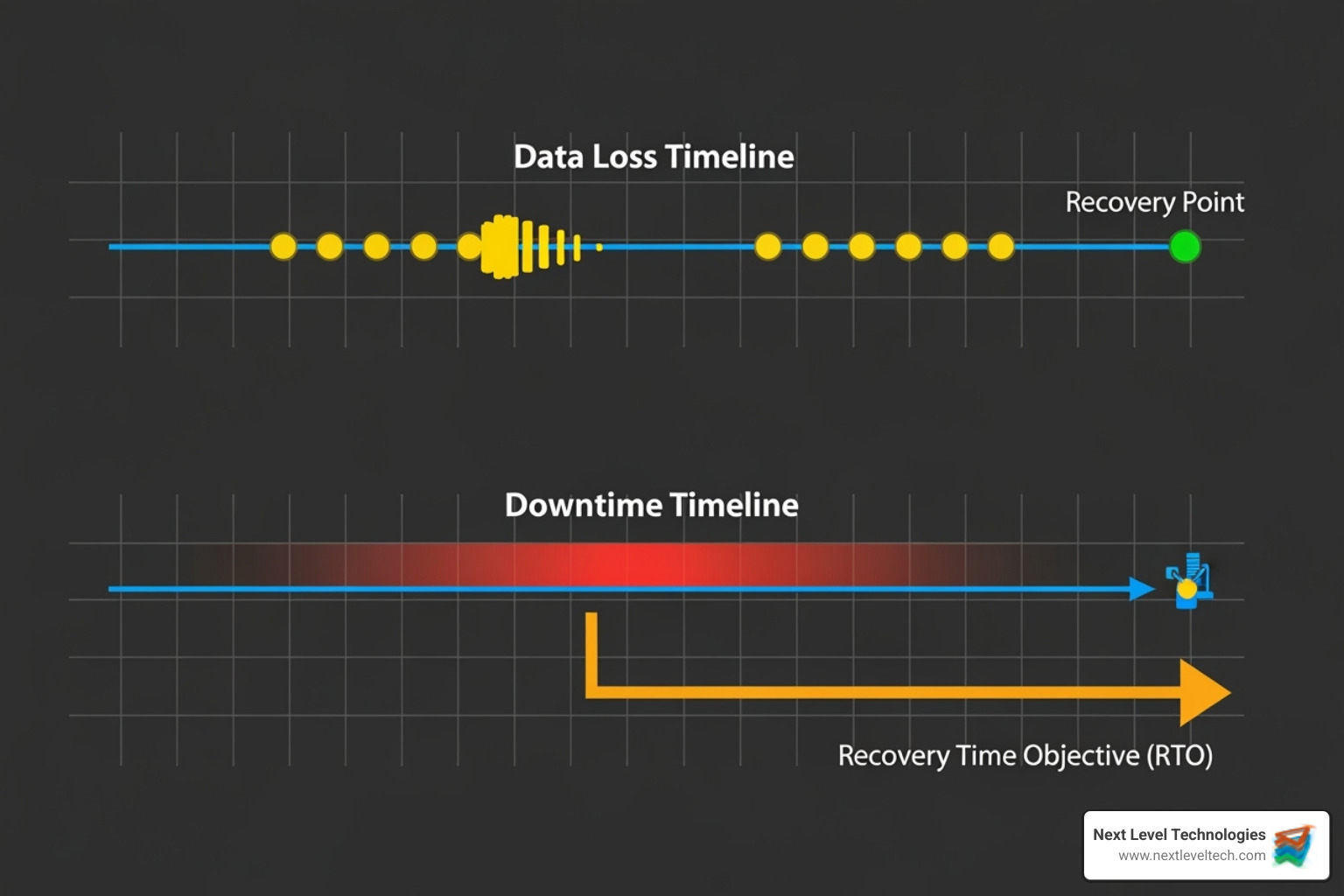
The foundation of a solid backup strategy involves two key concepts: Recovery Point Objective (RPO) and Recovery Time Objective (RTO). Your RPO defines how much data you can afford to lose, while your RTO determines how quickly you need to be back online. A business impact analysis helps set these objectives, and our team's extensive cybersecurity training has taught us that getting these numbers right is crucial for guiding your Backup and Recovery Solutions.
Choosing the right backup method is critical for a quick recovery. Here are the main approaches we use:
For more specific needs, file-level backup targets individual files, while application-aware backups work with databases and email servers to ensure data consistency. Our technical experience shows that combining multiple methods is often the best strategy. For more details, see more info about our backup services.
Effective Backup and Recovery Solutions must protect your entire mixed environment.
Our team's extensive cybersecurity training helps us manage complex hybrid cloud environments, ensuring no data falls through the cracks.
Modern Backup and Recovery Solutions offer powerful, precise recovery options. Unlimited versioning acts like a time machine, keeping every saved version of a file.
Granular recovery lets you pinpoint and restore exactly what you need—a single email, a specific database record, or a file version from last week—without restoring an entire system. Point-in-time recovery expands on this by allowing you to roll back entire systems to a precise moment before an incident occurred. Our technical experience in Columbus, Ohio and Charleston, WV has shown that these capabilities are vital for minimizing business disruption.
Today, your Backup and Recovery Solutions are your last line of defense against cyber threats. With 69% of companies facing a ransomware attack last year and 74% of businesses unprepared for modern data risks, the threat is real. It’s not just about restoring data; it’s about building a cyber resilience strategy that can withstand sophisticated attacks. At Next Level Technologies, our approach combines proactive defense with rapid recovery, ensuring your data is not just backed up, but truly protected.

Ransomware targets both your live data and your backups, so a strong Backup and Recovery Solution needs a specific playbook to fight back.
Our goal is always achieving 'minimum viability' for rapid recovery, getting your most critical systems back online as fast as possible. Our team, with its extensive cybersecurity training, creates streamlined recovery plans to get core operations for businesses in Columbus, OH, and Charleston, WV, running again in minutes, not days.
After a major cyberattack, advanced recovery techniques are often necessary.
Choosing the right Backup and Recovery Solution requires a careful assessment of your business needs. There is no one-size-fits-all answer. The decision depends on your Total Cost of Ownership (TCO), scalability requirements, performance needs, and your team's ability to manage complexity. Our extensive cybersecurity training has shown us that the best solution is the one that fits your operations perfectly.
| Feature | On-Premises | Cloud (BaaS) | Hybrid |
|---|---|---|---|
| Control | High | Lower (vendor managed) | Moderate to High |
| Cost Structure | High upfront CapEx, lower OpEx | Lower upfront OpEx, scalable subscription | Mix of CapEx and OpEx |
| Scalability | Limited by hardware | Highly scalable | Flexible (scale cloud as needed) |
| Performance | Fast local recovery | Varies with internet speed and vendor infra | Fast local recovery, cloud for DR |
| Maintenance | High (your responsibility) | Low (vendor responsibility) | Moderate (manage local, vendor manages cloud) |
| Ransomware Res. | Requires careful configuration (air-gapped) | Often built-in (immutability, air-gapped) | Combines best of both |
| Data Sovereignty | Full control | Depends on vendor's data center locations | Can be managed with local storage |
Security is the foundation of any good backup strategy. After years of helping businesses in Columbus, Ohio and Charleston, WV, I know that solutions designed with security first are the ones that save the day.
Our team's extensive cybersecurity training means we understand these complex requirements and can implement compliant solutions.
Today's Backup and Recovery Solutions offer incredible flexibility in how and where you store data.
The landscape of data protection is constantly evolving. The future of Backup and Recovery Solutions lies in leveraging automation and Artificial Intelligence (AI) to create smarter, more resilient systems that stay ahead of sophisticated cyber threats.
AI and automation are shifting data protection from reactive responses to proactive defense.
Backup and Recovery Solutions are the tools that make business continuity (BC) and disaster recovery (DR) plans a reality.
When designing a strategy for clients in Columbus, OH, and Charleston, WV, we focus on:
Here are answers to some of the most common questions we receive about Backup and Recovery Solutions.
Backup is the process of making a copy of your data and storing it safely. It's the spare key for your digital information.
Disaster Recovery (DR) is the complete, step-by-step plan to get your entire business running again after a major incident, like a cyberattack or natural disaster. A DR plan is the blueprint for rebuilding, and your backups are a critical component of that plan.
This depends on your Recovery Point Objective (RPO), which is the amount of data you can afford to lose. For critical data like sales transactions, you might need continuous or hourly backups. For less time-sensitive information, daily or weekly backups may suffice. Our team's technical experience helps determine the right RPO for your different data types and design a custom backup schedule.
Security depends on how a solution is configured and managed, not just its location. Both cloud and on-premises Backup and Recovery Solutions can be highly secure.
A well-designed solution with strong encryption, immutability, and strict access controls, monitored by experts with extensive cybersecurity training like our team at Next Level Technologies, provides robust security regardless of location.
As we've seen, data protection isn't just about technology—it's about building resilience into the foundation of your business. With 69% of companies experiencing ransomware attacks and 74% of enterprises unprepared for modern data risks, the question isn't if you'll face a data crisis, but if you'll be ready.
Backup and Recovery Solutions are your business continuity lifeline. When disaster strikes, a resilient data strategy allows you to keep serving customers and moving forward. Building this strategy requires understanding your unique RPO and RTO objectives, regulatory requirements, and growth plans.
The future belongs to businesses that accept proactive data protection. Modern solutions with AI-powered anomaly detection, immutable backups, and automated recovery testing actively defend against emerging threats.
For businesses in Columbus, OH, and Charleston, WV, this level of protection is within reach. At Next Level Technologies, our team's extensive cybersecurity training and technical experience allow us to craft custom data protection strategies that grow with your business. Our managed IT services provide enterprise-level protection without the complexity or cost.
Your data is irreplaceable. Don't leave its protection to chance.
Build your backup strategy with us and find what true data resilience looks like for your business.
Transform your IT! Discover how proactive IT support prevents issues, cuts costs, and secures your business for growth.
February 21, 2026
Discover the benefits of incident management to minimize costly downtime, boost customer trust, and ensure business continuity.
February 19, 2026
Next Level Technologies was founded to provide a better alternative to traditional computer repair and ‘break/fix’ services. Headquartered in Columbus, Ohio since 2009, the company has been helping it’s clients transform their organizations through smart, efficient, and surprisingly cost-effective IT solutions.
